The all new HTC One M8 is the latest Android flagship making the rounds through major carriers hoping to beckon your purchase. Coming in at about $200 for most carriers with a contract, it makes a good case for itself with its advanced features and solid price point—but, there's another way to buy the One, and it's not from your carrier.

You've probably seen someone in your family truss the turkey on Thanksgiving before roasting it, even if you don't recognize the word. To truss a bird or roast just means to wrap it up as compactly as possible before placing it in the oven, and it's usually done by tying it with string. Trussing a bird is a tradition that's been around for a long time, and a lot of home cooks do it religiously even if they don't know why. It's a highly debated topic with fierce supporters on both sides, but f...

As respectful as you may be, it's hard to resist looking through someone's iPhone when given the chance. You're not trying to snoop around, but it's just too easy to open up apps and read embarrassing emails or find scandalous Instagram follows. It's like looking through a digital diary riddled with deep, dark secrets.

Point-and-shoot cameras are practically extinct these days now that every new phone on the planet has a camera built right in. This makes the smartphone market highly competitive, because the camera specs and features are a big selling point.
You don't have to be in debt to receive annoying calls from unwanted numbers. You may love your grandma, but if she calls you three times a day to ask how to turn on the television, you might just want to push all of her calls to voicemail.

Lag has been a serious issue on Android devices since the very beginning. Even the Nexus 7's quad-core processor can't stop it from happening. That's because the pauses and long responses are coming straight from the Android OS itself, not the hardware.

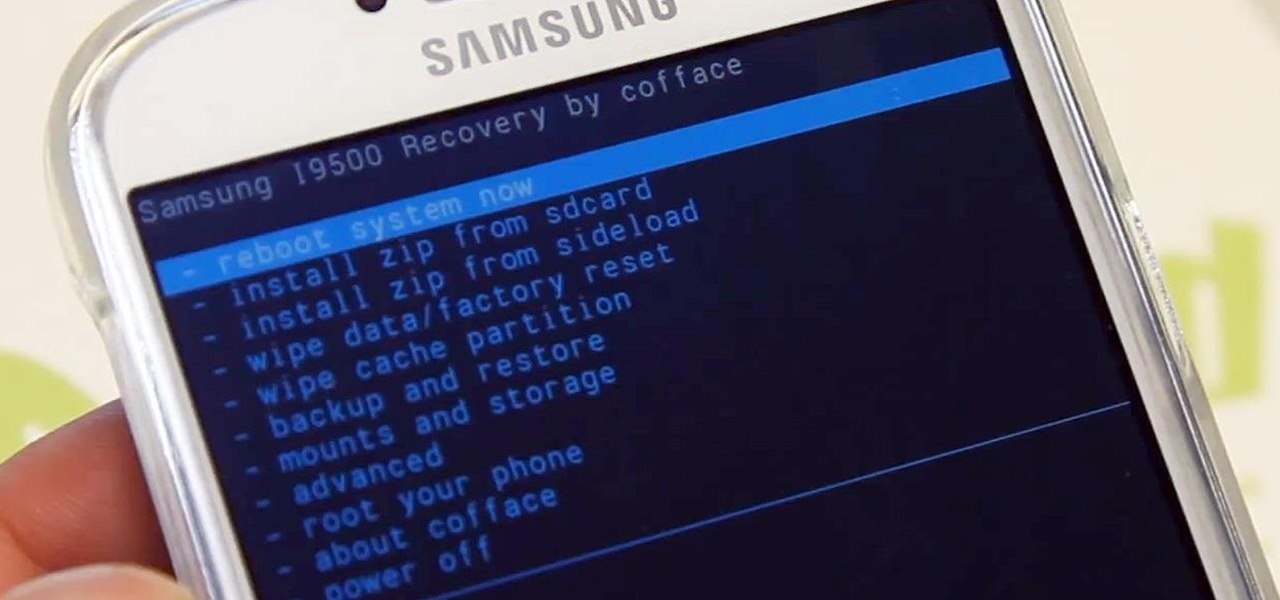
Ready to start rooting your Samsung Galaxy S4? For those of you with the GT-i9500 model GS4, this quick video will walk you through the entire rooting process using Odin and CWM.

Many people ultimately remarry when their first marriage eds in divorce or had mistakes written all over it. The choices you made do affect you future relationships and it is up to notice these and correct those problems so it does not happen in your next committed relationship. Learning Reasons Why Your First Marriage Culminated in Divorce

Walking the streets at night can be uncomfortably dangerous. In 2010, there were 32,885 motor vehicle deaths in the United States. Of those, roughly 13%, or 4,280, were pedestrians. Two-thirds of those pedestrian deaths occurred at nighttime. Along with darkness, drivers also have to deal with rain and other harsh weather conditions. Combined, all of these factors can be very dangerous for anyone taking a walk at night. As it happens, pedestrian deaths are on the rise since 2009.

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

The final chapter of Christopher Nolan's Batman trilogy is here, The Dark Knight Rises, and if you're anything like me, it made you want to immediately don a cowl of your own and run around punching criminals. Don't forget though, one of the most awesome aspects of Batman is his never-ending supply of crazy gadgets. Unfortunately for most of us, we don't have a billion dollars, nor Morgan Freeman, so we'll just have to make do with some good old-fashioned DIY tricks. Read on for a rundown of ...

Thanks to the PlayStation 3 and Xbox 360, video games are constantly evolving to higher degrees of sophistication, with complex graphics, lifelike resemblances and storylines that create exciting experiences that relieve the tediousness of our everyday lives.

It's time to make some more room at the augmented reality cosmetics counter. This week, social media giant Pinterest unveiled "Try On," a virtual make-up visualization tool running on its Lens visual search tool.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

With each year that we anxiously await Apple's next big version of iOS, there comes the sad reality that the eldest iPhones will not continue to receive support. That's not the case with iOS 12, however, as the software is compatible with all iPhones currently running iOS 11, going back as far as the iPhone 5S.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

If you have an iPhone, you probably know that iOS 11 hasn't been the smoothest iOS version released, to put it lightly. We've seen bug after bug cripple the software's usability, many times within the Messages app. Now, yet another glitch has emerged to drive us crazy, one where just a simple Indian character can crash Messages as well as other third-party apps.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

It's not the bacteria itself that takes lives and limbs during invasive flesh-eating bacteria infections. It's the toxins secreted by the group A Streptococcus bacteria invading the body that causes the most damage.

US blood banks have assured the American public that they have the tools to prevent a Zika contamination, despite the rapid spread of the disease.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen burn-in.

Sleep lets our body processes rest and restores us for the next day, so a bad night's sleep can ruin the following twenty-four hours and even make us feel sick. Now, new research published in the journal Sleep cements the idea that loss of sleep actually leaves us vulnerable to sickness.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

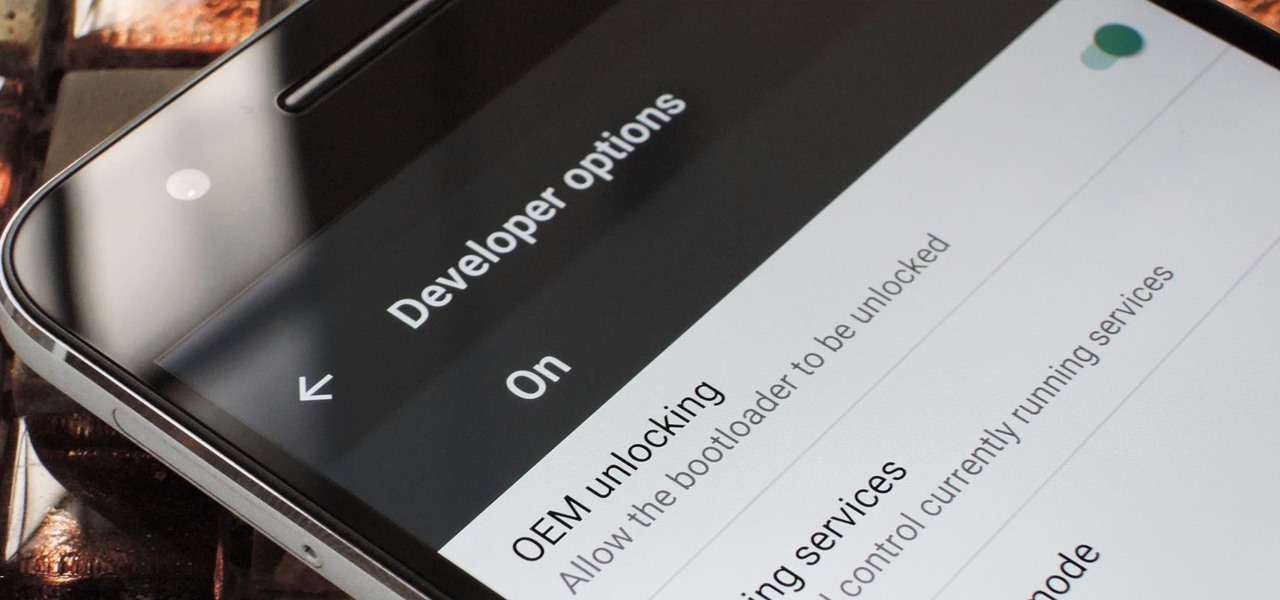
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Tomatoes are the perfect barometer for kitchen knives and knife skills. If you've ever watched an infomercial for a set of knives, you've surely seen the enthusiastic host waxing about how well the knives cut tomatoes. And if you've ever had your knives sharpened, you've most likely tested them out on a tomato.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Master Lock combination padlocks have been known to be vulnerable to an attack that reduces their 64,000 possible combinations down to 100. I've devised a new attack for cracking any Master combo lock that simplifies the process and reduces the amount of work down to only 8 combinations.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

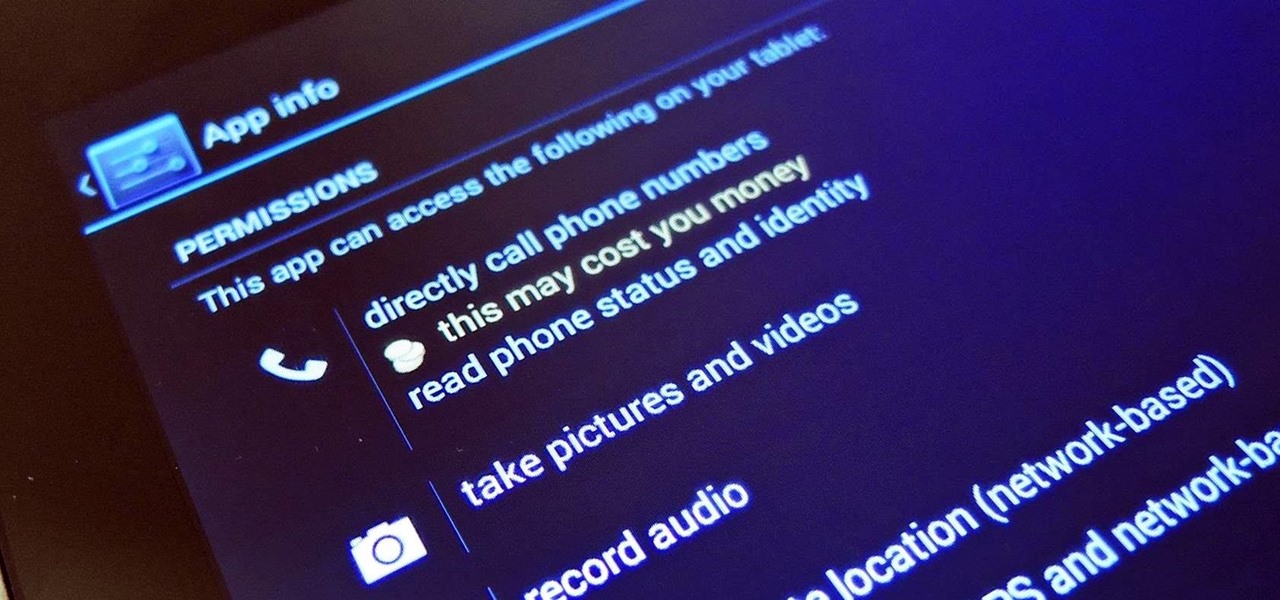
Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.