When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.

For those familiar with my old YouTube series, New in the Store, you will be excited to know that I am starting something very similar here on NextReality that's a bit more broad in scope. Have You Seen This? will take a look at HoloLens applications that are new in the Windows Store, as well as some that may not have gotten the attention they deserve.

When the "Just another day in the office at Magic Leap" video was released last year, it was called a mind-blowing, stunning, and breathtaking take on mixed reality gaming. It was a great presentation of what the technology could be, but not for a second did I think it was anything other than a concept video, and I'm not the only one who thought that. This was a goal to reach for mixed reality, not the reality.

You're all kale-d out, you've had it up to here with golden milk, and you're on the prowl for the next superfood. Well, get ready for some unicellular goodness: the next superfood is an algae named Spirulina, also known as Blue Majik. (Kudos to the marketing exec that came up with that, am I right?)

With the holidays over, a lot of people with shiny new Google Homes are getting their first chance to explore the new Google Assistant. Before the Google Home's release, the Assistant was only available for the Google Pixel and Pixel XL, or in a text-based form with Google Allo—but now it's gone mainstream.

The reviews for the Google Pixel phone have hit the web. There's a lot of praise, but not all are so positive. We've collected some of the best takes on the new devices from the top tech sites around.

Avocados aren't just having a moment—they're having an extended stay in the spotlight. From mainstays like guacamole to buzz-worthy variations of avocado toast, this silky green fruit is the Hulk of the food world right now. I, for one, welcome any avo-centric trend with open arms... and an open mouth, of course.

With Passover soon upon us, many Jews are dreading a week (or eight days for Conservative and Orthodox Jews) of making matzo, the staple of their diet. Matzo is also known as "the bread of affliction," and I'm pretty sure it's because by day three or so you're convinced that matzo is the 11th plague.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

This is a how to to change any user password on a windows 7 computer. If you forgot your password you can change any account password even if you are locked out of your account.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

How much you've actually spent and how much you think you've spent are usually two completely different results, and is especially true on Amazon when it's so easy to click and buy. You might think you've given Amazon a couple thousand over your lifetime, when the fact is that it's three or four times that amount.

In my household, we are frugal and somewhat picky eaters, so we have to be a little creative with the things we buy. We like to purchase items that can be used in multiple dishes to reduce cost—and because it's just more practical. Pancake mix is a favorite because it can be used in various dishes where any type of breading may be involved. To help inspire you, here are some of my favorite ways to use pancake batter at home.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

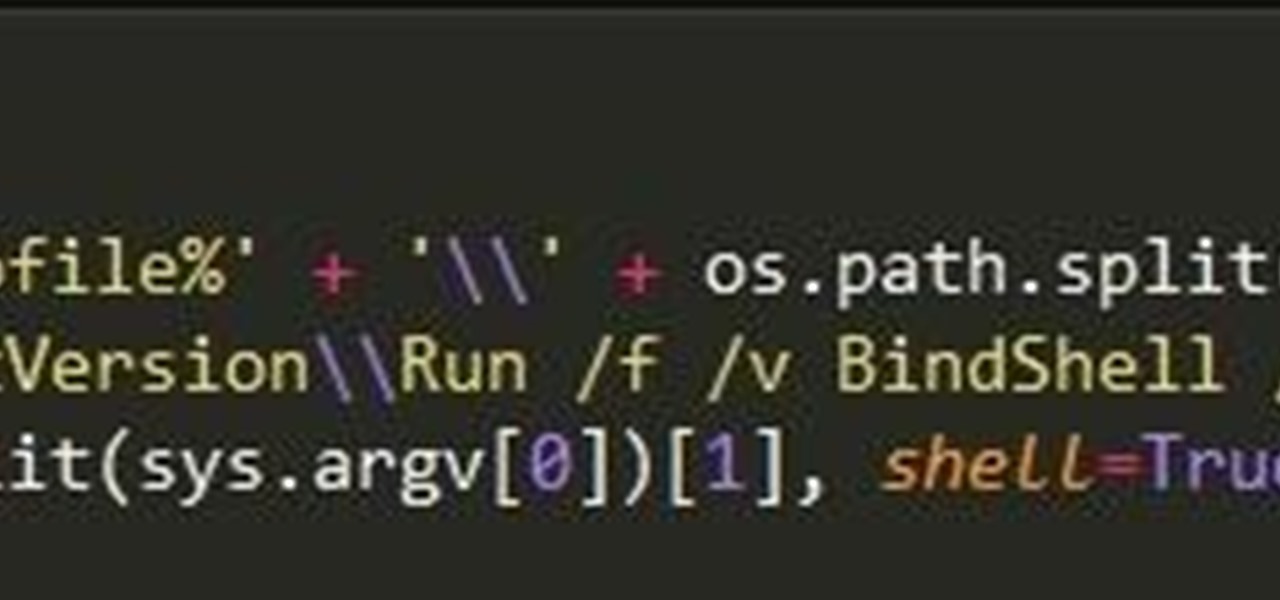
Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Hello friends. This is actually my first how to.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

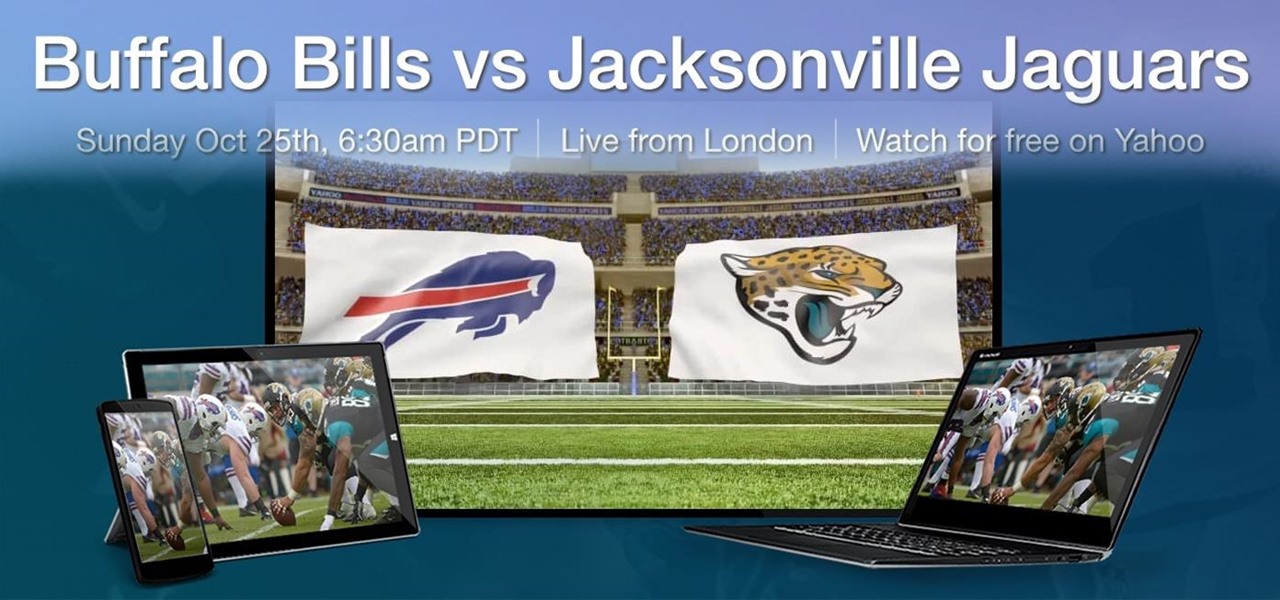
For a lot of would-be cord cutters, the lack of streaming local sports is the only hurdle that needs to be cleared before they can sever all ties with big cable. This is why it was a huge victory for us anti-cable folks when Yahoo announced that they would be hosting the first ever live-streaming NFL game this Sunday at 9:30 AM Eastern.

The standard way to make pasta requires a lot of water, and it takes a long time for that big pot of water to actually start boiling. For these reasons, as well as my hatred for washing large pots, I don't cook pasta at home very often—at least not the traditional way.

Butter is one of the most versatile ingredients in the world: its variety of uses range from brightening a morning piece of toast to finishing a beautiful rib-eye steak with decadent flair.

Let me start by saying something controversial: I despise the gluten-free fad. I think gluten is delicious (I go through at least two loaves of bread a week, with a healthy dose of pretzels and pasta in there as well), and I think many of the health myths surrounding gluten are either fabricated or hyperbolic.

Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

Being born with a sweet tooth and Japanese blood, my desire for dessert-style sushi is practically written into my DNA. At once delicious and adorable, these one-bite delights are the perfect way to conclude a meal. They're also a killer snack. Featured below are: 1) the Banana Nutella Nut Roll; 2) the Strawberry Kiwi Roll; 3) Mango and Sweet Rice Nigiri.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Welcome back, my hacker novitiates!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.