Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Yesterday, Bryan Clark pointed out a new option on Verizon's privacy settings that gives new customers 30 days to opt out of a data sharing program that gives advertisers information on basically everything you're doing on your new iPhone (or any other smartphone).

NTFS? What is it? It stands for New Technology File System, but what does that mean? Well, it's the standard system for filing in Windows NT, including all later versions, up to the current Windows 7, but Mac users can take advantage of this file system, too. If you’re confused when it comes to your hard drive’s format, this guide will show you the way to get the most out of your system.
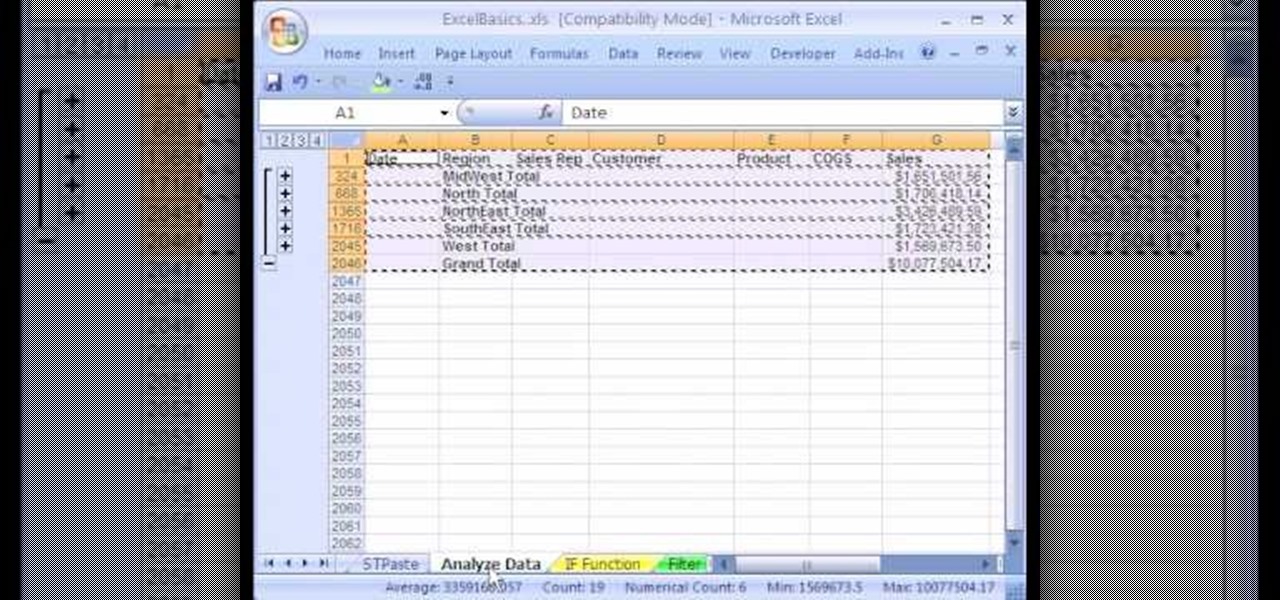
1. The following instruction describes how to generate sub totals in Microsoft Excel Sheet. 2. Take Region as a Primary column and Sales Rep as a Secondary Column. 3. First method to sort: Select a cell in Region and goto Data select A to Z. 4. Second method to sort: Select a cell in Region and Right click and select Sort A to Z 5. Then click a cell in Region and select Data->OutLine->SubTotal 6. In the SubTotal Window select 1.Each Change in: Region 2.Use function:Sum 3.Add subTotal to:Sales...

Need to sort a ton of data in Excel? Why waste time cutting and copying cells? In this tutorial, learn how make Microsoft Excel automatically sort columns or rows alphabetically.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

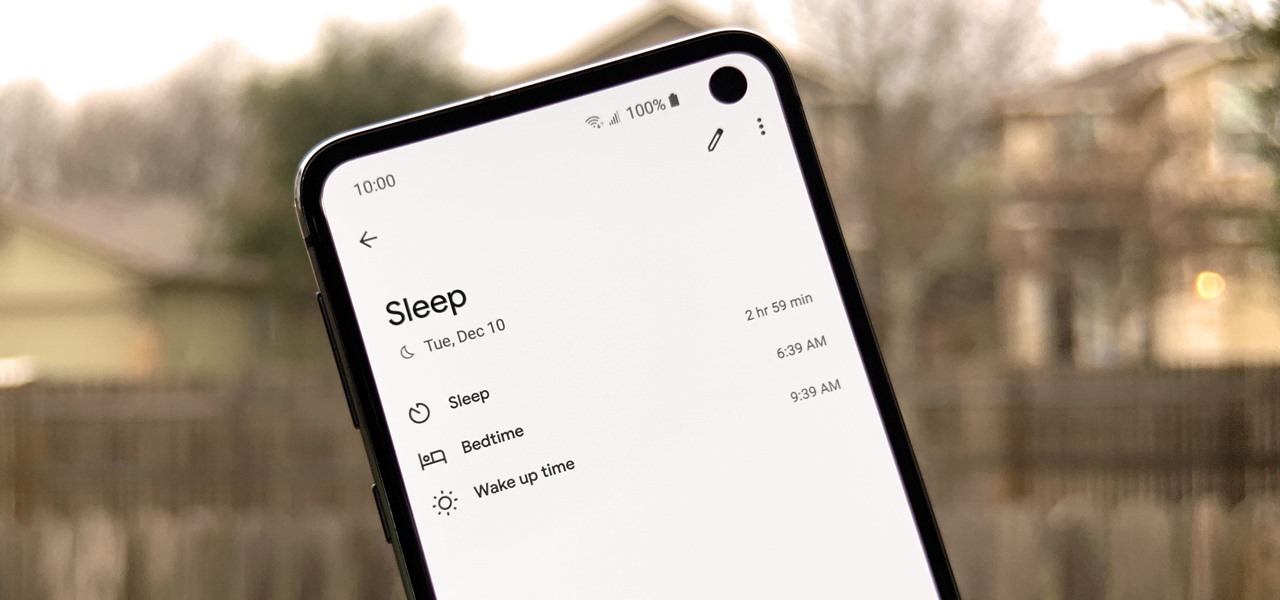
When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

Magic Leap is making it easier for developers to share their spatial computing experiments with other Magic Leap One users.

Sports technology company Form is testing the waters for augmented reality wearables with a product aimed at a very specific user group.

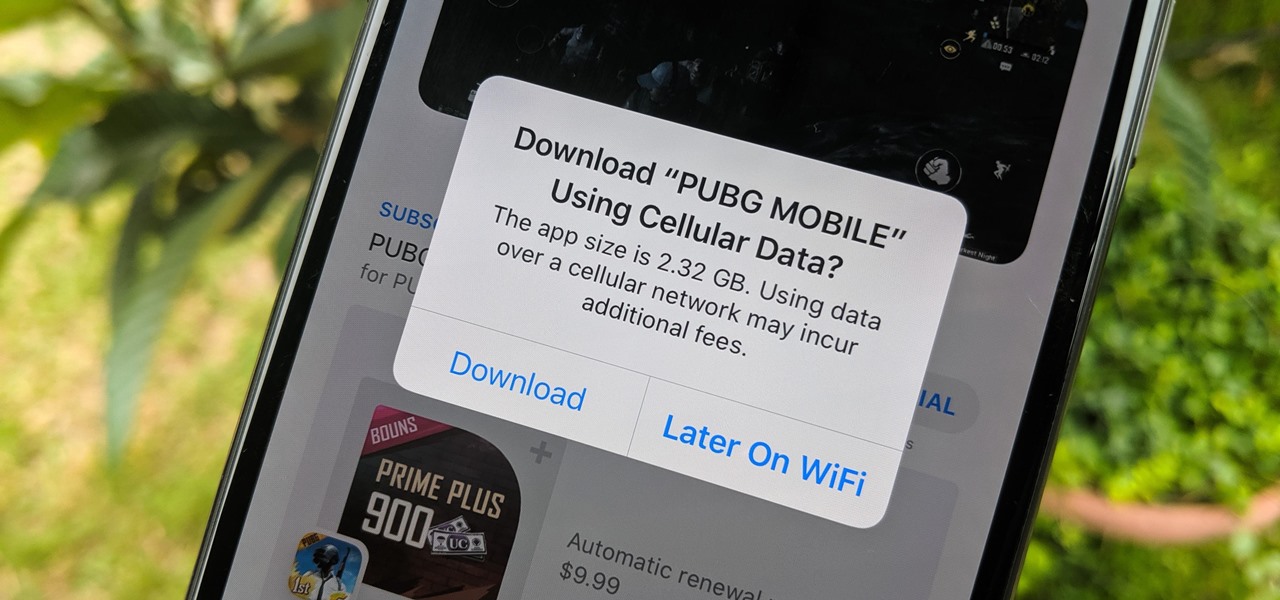
When there's a new game you want to play or app you need to use, but a Wi-Fi network isn't available, you can always download it over cellular data. If the size of the app is too large, however, you may not be able to on your iPhone. But that changes in iOS 13, which finally gives control over cellular data downloads in the App Store.

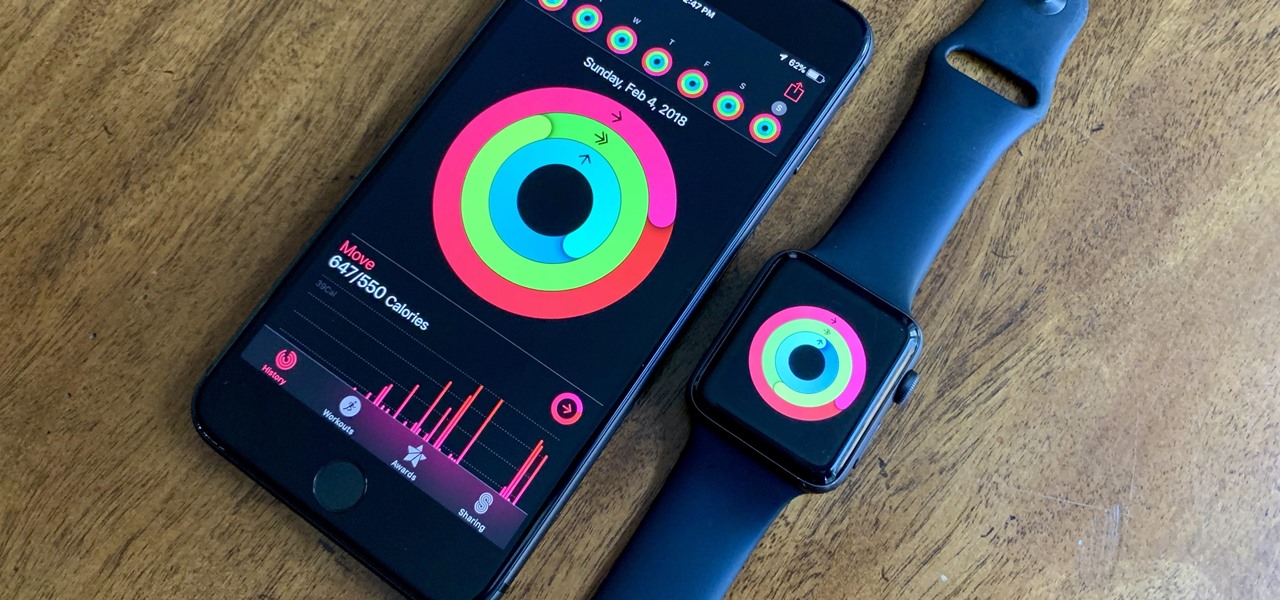
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

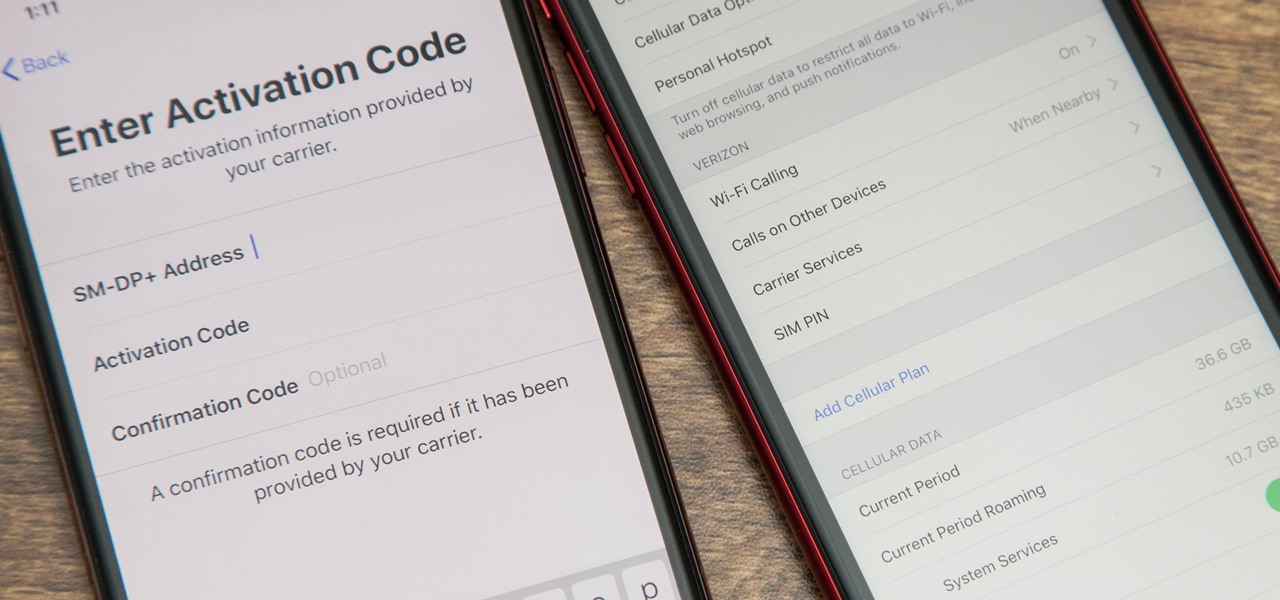
With an iPhone that includes a digital eSIM option aside its standard Nano-SIM card, you can have two cellular service accounts. One can be your primary line with your main wireless carrier, and the other can be from your main carrier or another provider. The eSIM account can be prepaid or postpaid as well as data-only, which is great for traveling. But which wireless providers support eSIM?

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Mozilla has created yet another browser for Android. Similar to Firefox Focus, Firefox Rocket was designed to address specific problems: limited internal storage and low data caps. However, in the process of solving these problems, they created one of the fastest browsers on the market.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

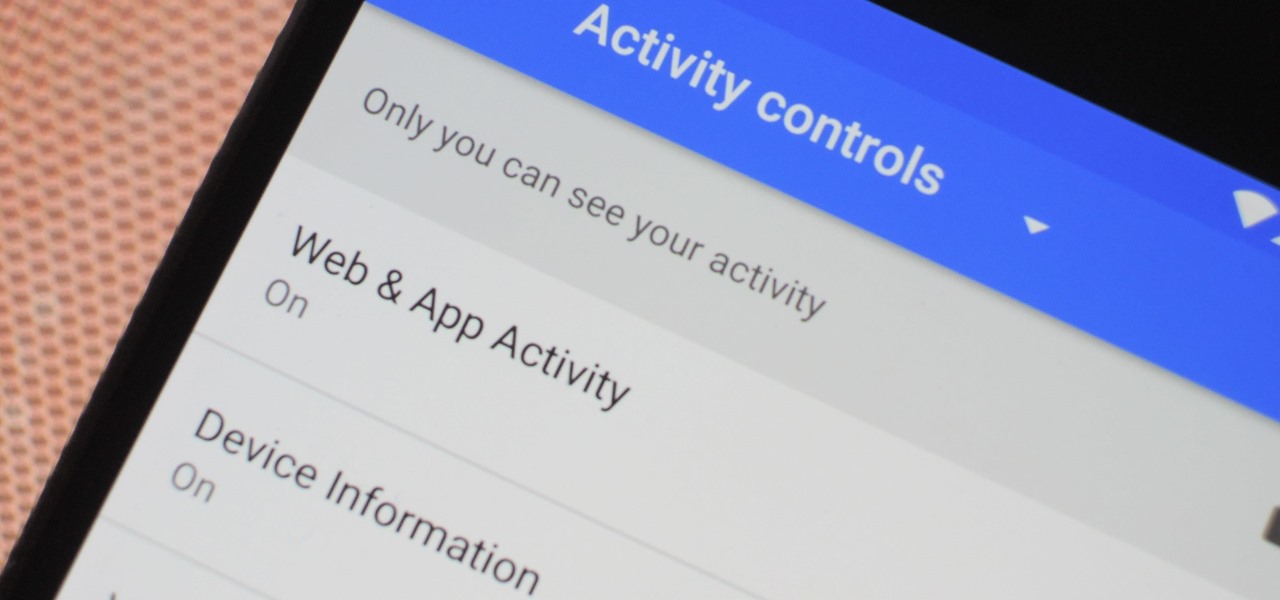
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

Tesla has confirmed the EV carmaker has begun to upload videos from models equipped with its latest flavor of Autopilot, as Tesla seeks to "fleet source" data to help improve its cars' machine learning capabilities.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

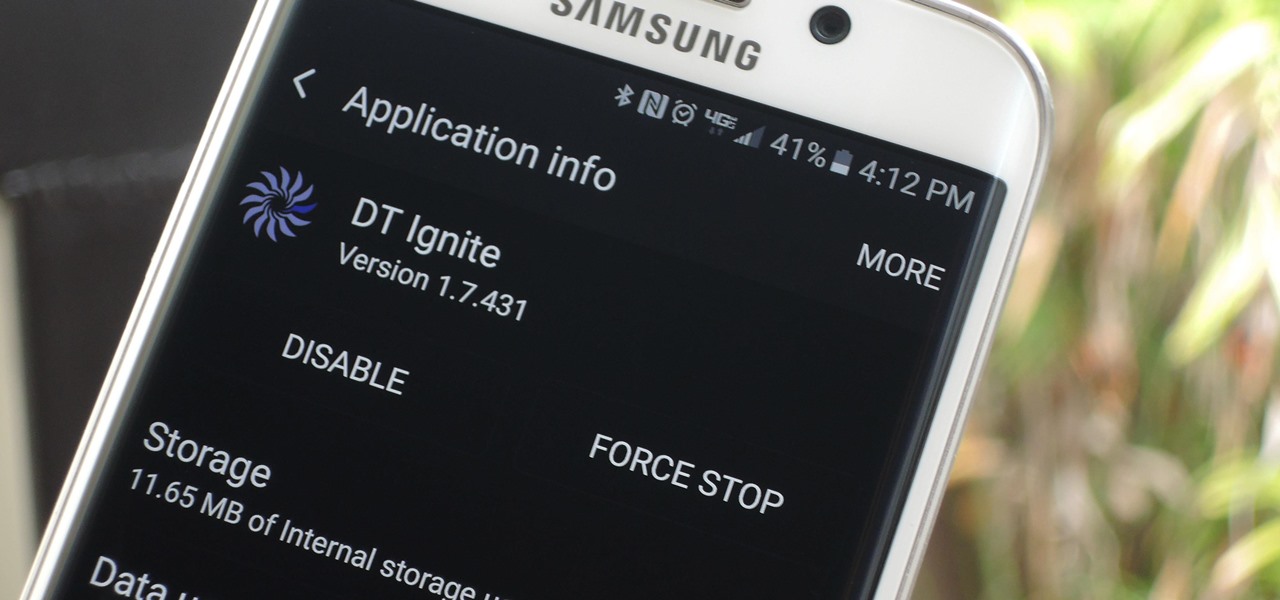
A few months ago, it was discovered that Verizon was installing an extremely shady app called "DT Ignite" on some of its smartphones—most notably, the Galaxy S7 and S7 Edge. The app, created by Digital Turbine, monitors your smartphone usage, then uses the data it collects to silently install "recommended" apps without notifying you.

Bluetooth 5 was announced and made officially available on December 7, 2016. It comes with a handful of improvements to speed, range, maximum device connectivity, and anti-interference from other nearby devices. While this might be great for those special few who use Bluetooth on a daily basis to send and receive (or steal) data, what about the average Joe?

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

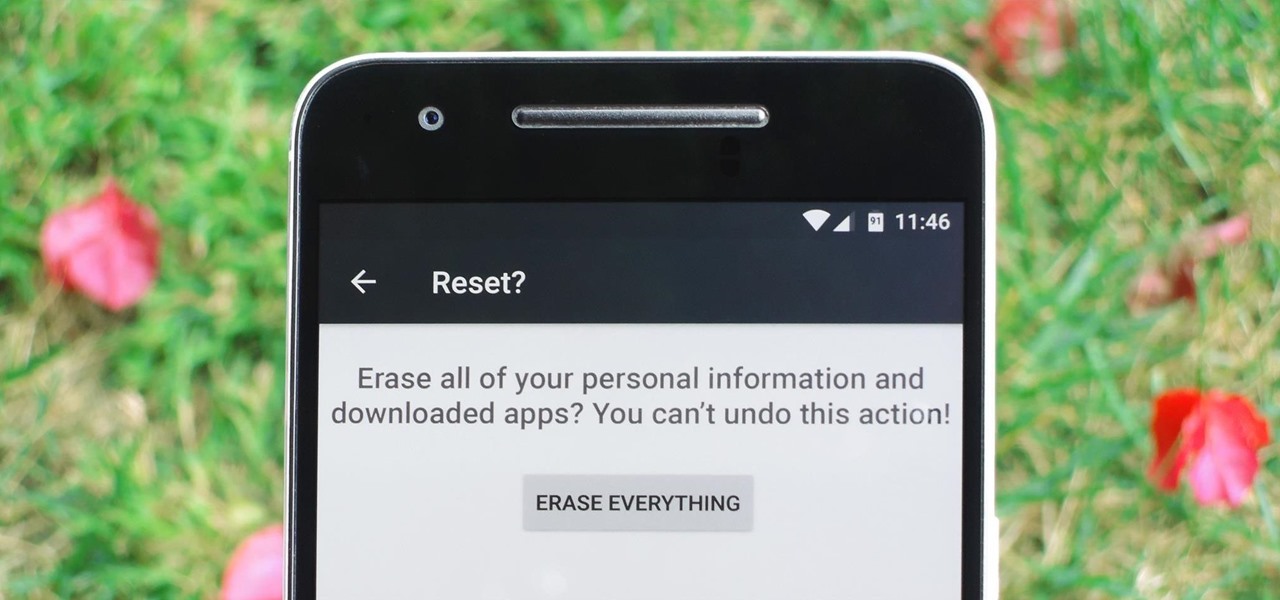
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.

With all the stress that goes into booking flights and lodging, packing (and not forgetting) everything you'll need, finding pet sitters, and everything else that goes with a trip overseas, there's the added stress of staying connected while abroad.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

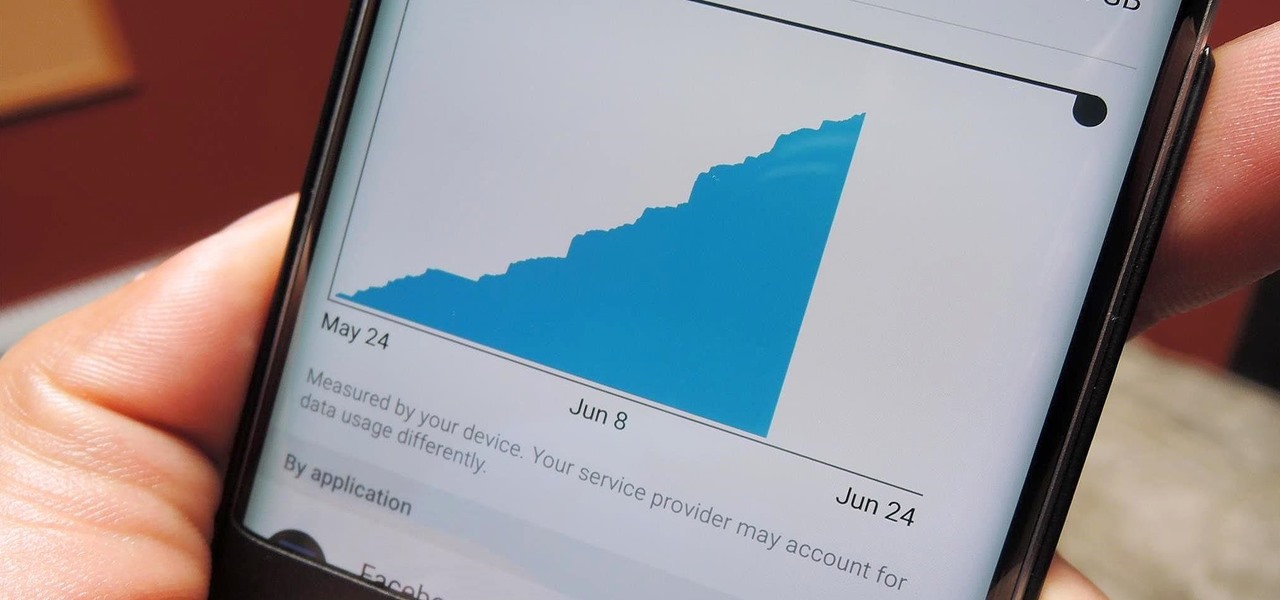
When you're not using your phone, it doesn't make much sense that it would be wasting power by maintaining an internet connection for the inside of your pocket or purse. Well, perhaps you need a little bit of intermittent data here and there so that apps can update themselves in the background and still post notifications, but it doesn't need to be constant.

T-Mobile continues to make waves in the U.S. wireless market behind CEO John Legere's UnCarrier program. At the latest installment in a series of industry-challenging announcements, Uncarrier 5.0 unveiled Test Drive. The new program is set to allow would-be customers to try out the "latest generation" iPhone for seven days on T-Mobile's network without any financial commitments.