One of the best parts of being an Android user is the countless awesome features. Many of these features are well-known and user-facing, like custom icon packs and launchers, but some get lost in the shuffle. Back at Google I/O 2016, Android Instant Apps were introduced to developers and enthusiasts. Since then, the feature has seen a wider rollout, but few users are aware of it.
The final developer version of iOS 11 was leaked a few days ago, but Apple quickly stopped signing it so nobody else could install it. With Apple's Sept. 12 event now over, the Golden Master (GM) version of iOS 11, the same version that will be released to everyone around Sept. 19, is available to install again — and anyone can get it.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.
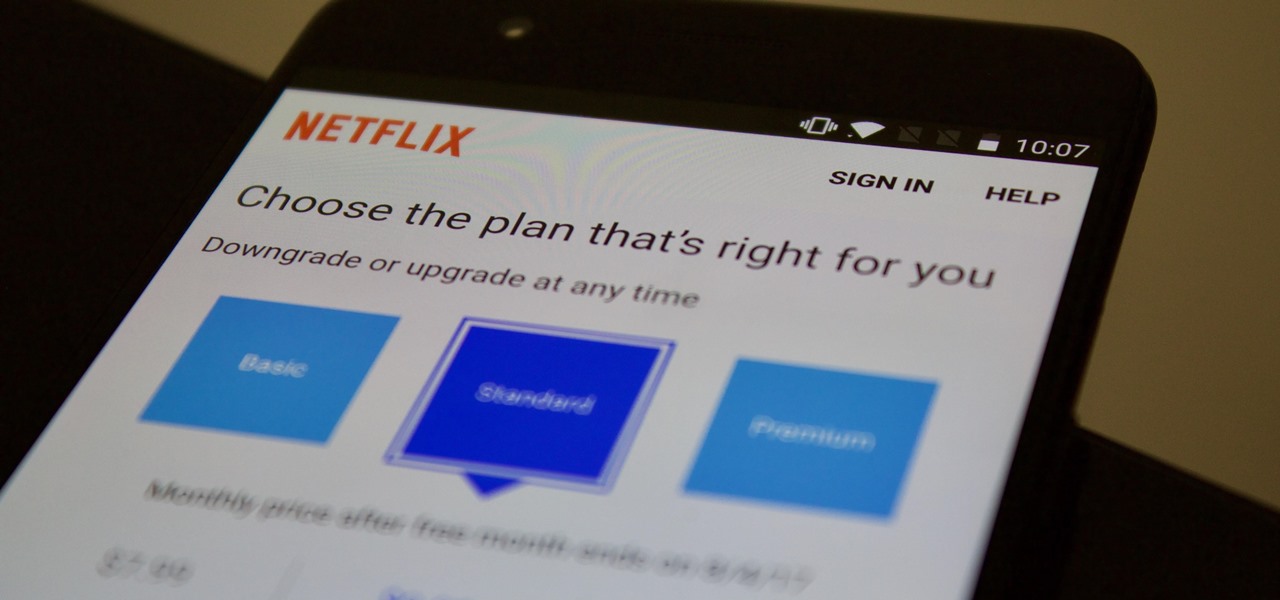
Netflix offers three different tiers of service. The good news is that no matter which subscription plan you choose, the available content is the same. Whether you choose the cheapest plan or the most expensive, you'll be able to watch any TV show or movie in Netflix's library. But there are other things to consider when choosing the plan that's right for you and your smartphone.
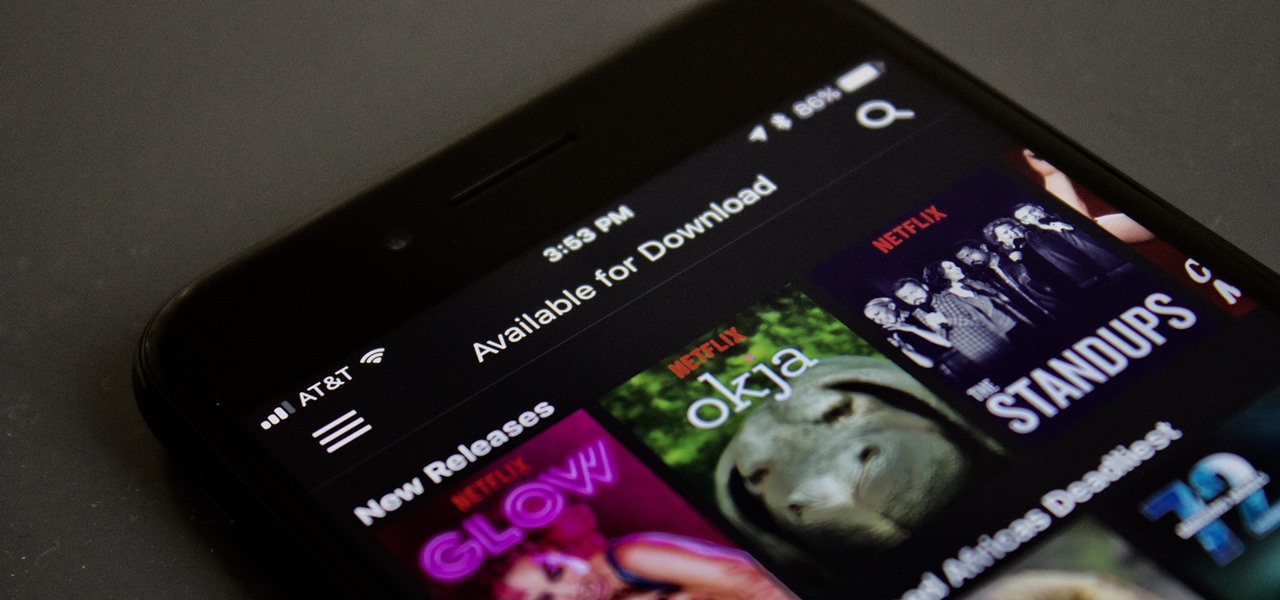
Netflix added the ability to download TV shows and movies on Android and iOS for offline binging back in Nov. 2016, and the process is the same as it is today. So if you anticipate having some downtime to catch up on Narcos or give Bright a try when you'll be away from a secure Wi-Fi connection, download videos onto your phone and save your data for more important things.

A pair of organizations recognized companies working in augmented reality for their innovative technologies over the past week. Meanwhile, another company used augmented reality for a sector that is overdue for a technology makeover, while another company has developed new camera modules that could usher in the next evolution of mobile AR.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

One thing that I got more and more excited about as we got closer and closer to the Microsoft Build 2017 developers conference was finally learning about the new Acer Windows Mixed Reality head-mounted displays (HMD). Brandon Bray, Principal Group Program Manager at Microsoft, had teased us a few weeks earlier at the Vision Summit event in Los Angeles, California, and said there would be a lot more information at Build. Fortunately for us, he was right.

Lyme is a growing threat as we move into warmer weather in the US. Researchers have said this year could be one of the worst for this tick-borne disease, as a skyrocketing mouse population and warmer temperatures increase the risk.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.

This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

Officials in Colorado are concerned as 61 cases of the mumps were reported so far this year, a significant increase in the prevalence of the contagious disease in the state.

Google has done it again—they've pushed another broken OTA update for the Nexus 6. Except this time, it almost completely softbricks your Nexus 6 instead of just screwing up Android Pay and SafetyNet. Apps are force-stopping left and right, making the phone practically unusable.

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.

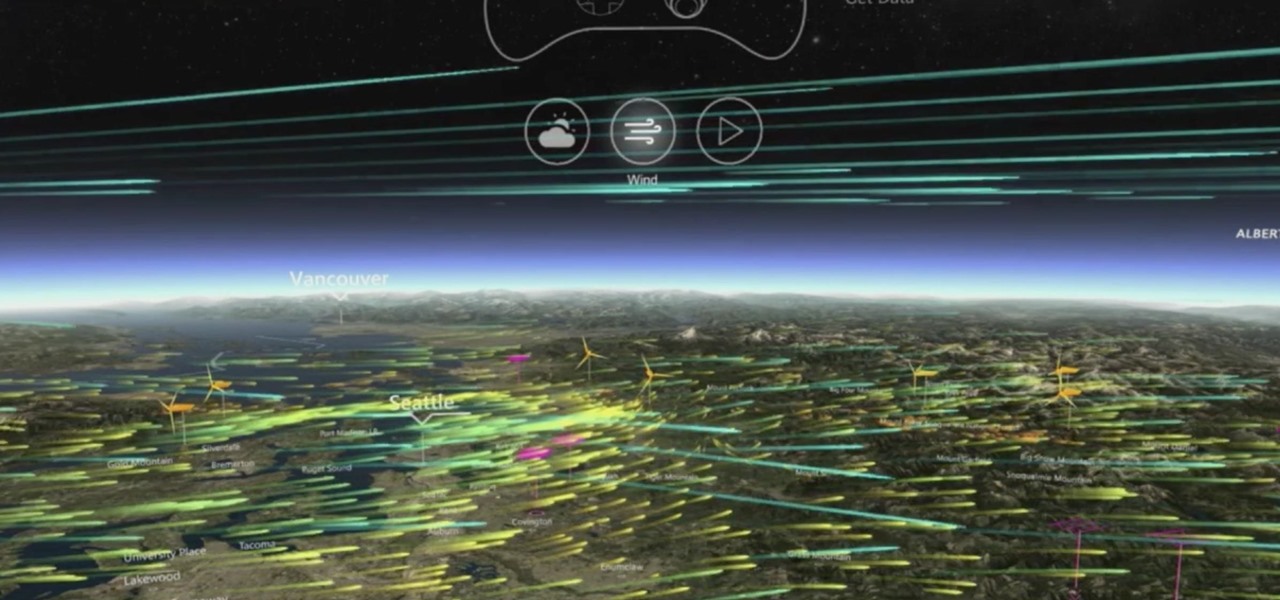
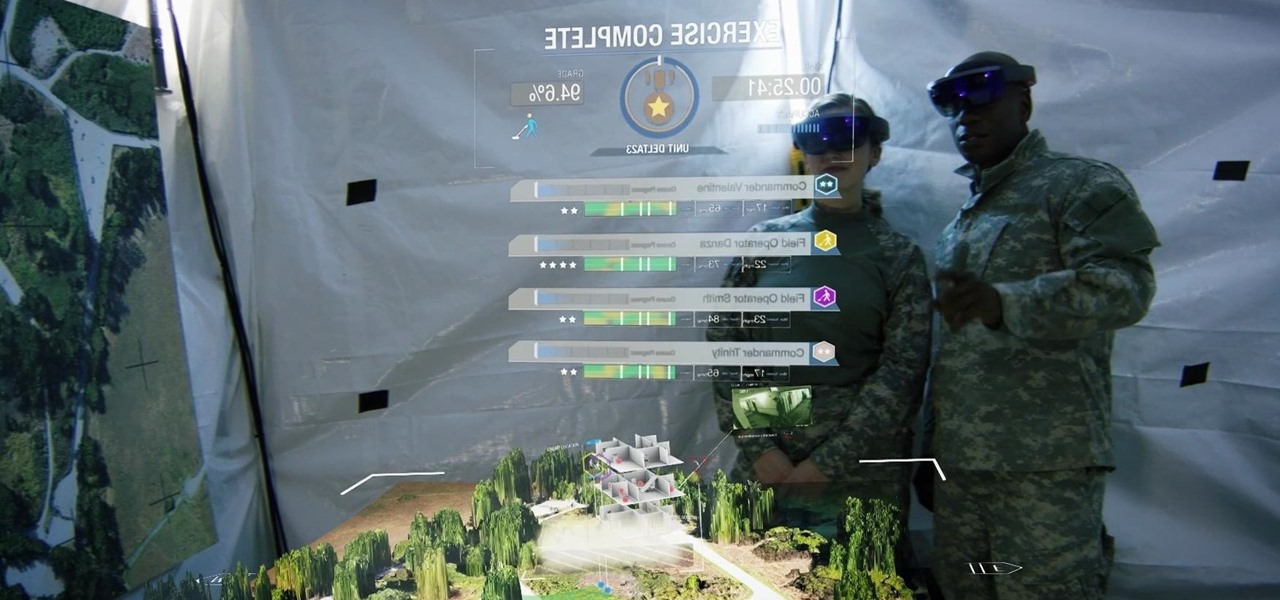
The limitless applications of 3D data visualization will enable a more efficient approach to many of life's problems. Each day, developers exploring this technology are finding new ways to solve these problems in mixed reality; 3D modeling, easier house management, spinal surgery, and forest fire management are just a few recent examples of ways 3D data visualization can benefit us all.

There's no question about it—Skype is one useful program, but has always been lacking in the mobile department. On your desktop, Skype works just fine and all of its options are available for usage. However, the same cannot be said for Android. On Android, you can't even change your status to "Away" or "Invisible."

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

Forget headphone jacks and "Courage." Look past the shiny Jet Black finish and beyond the minimized antenna lines. Sure, quad-LED flash and dual cameras are nice—but dual-SIM would've been much better.

Collecting Pokémon in Pokémon GO is only half the fun. Once you've reached Level 5, it's time to get your Pokémon ready to do battle with other Pokémon. This is where Gyms come in.

One of the biggest causes of smartphone battery drain is the mobile data connection—particularly if you live in an area with poor reception. But, chances are, you don't actually need this connection most of the time, because you're probably connected to Wi-Fi for a good chunk of the day, which uses far less battery life.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

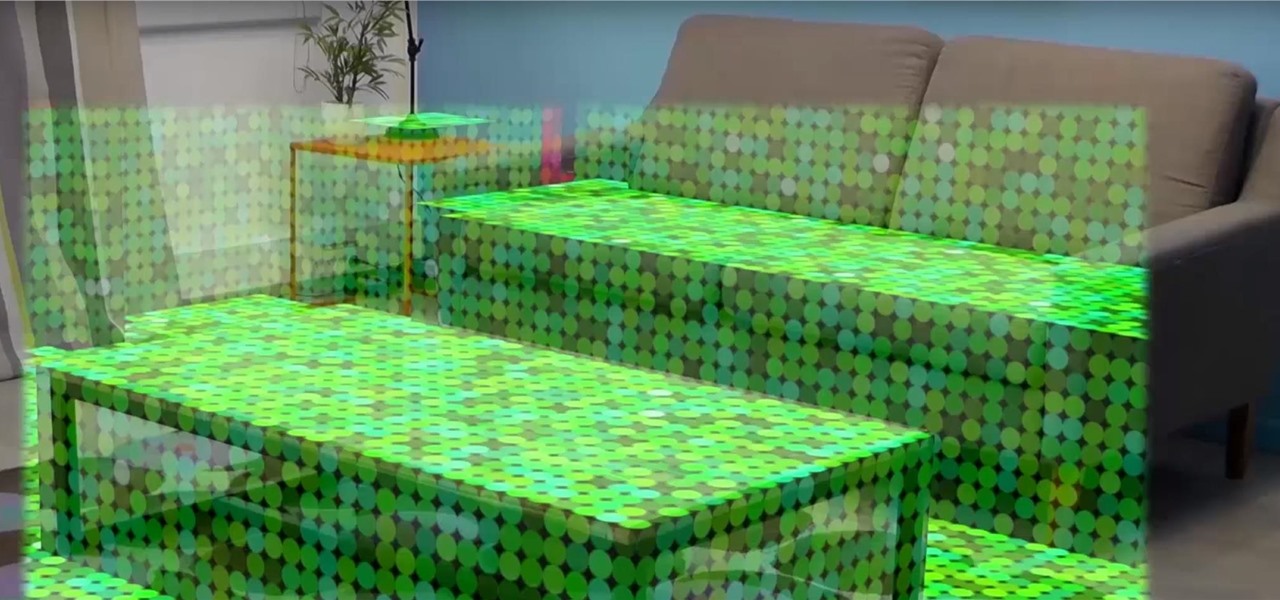
Once you've designed some holograms with HoloLens, you'll need to get them to interact with the environment. That's where Spatial Mapping comes in. There are five basic purposes for using HoloLens's Spatial Mapping with your app:

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

Android has a built-in browser called WebView that any app can use, which makes it easy for developers to display webpages without actually having to build an internet browser into their apps. But WebView is a stripped-down, bare bones browser with no ties to Android's default browser, Chrome, so none of your synced data like bookmarks, passwords, and history is available when an app is using WebView to display a page.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

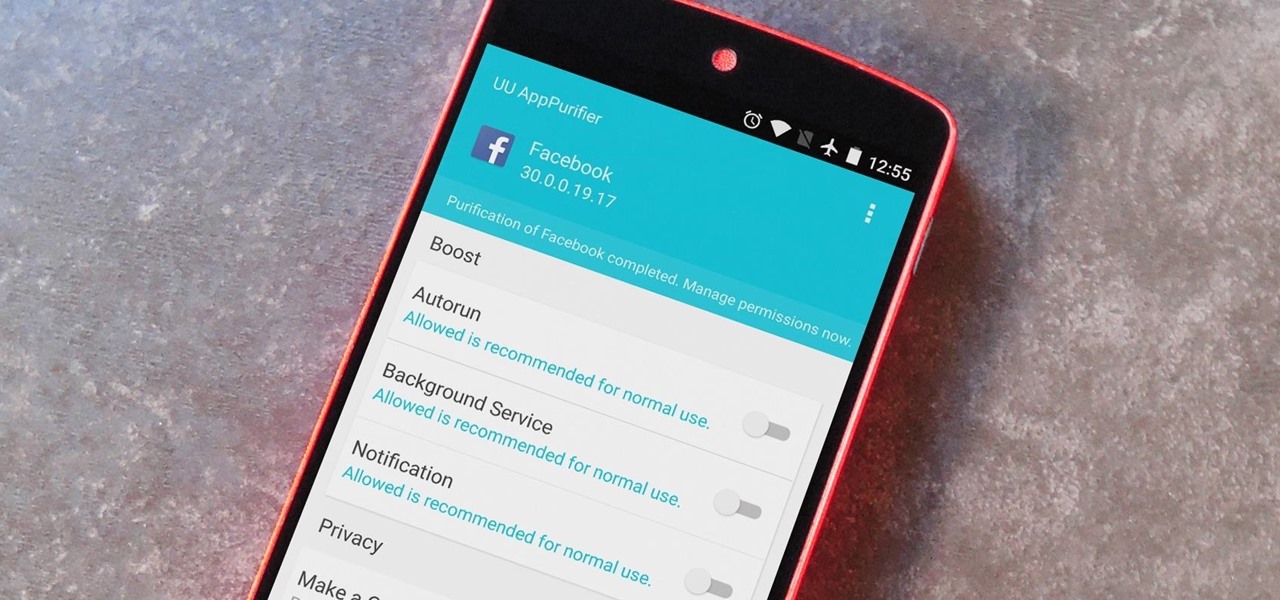
When it comes to app permissions, Android takes an "all or nothing" approach. You have no granular control over what data apps can access, so the only way to prevent an app from seeing your location or starting up on boot, for instance, is to not install the app in the first place.

Keeping your OnePlus One running smoothly can be taxing, especially if you spend most of your day looking for ways to tweak performance settings like me. Sometimes I get lucky and end up with a faster phone, but because I experiment so much, I often end up restoring it back to stock. This process can get old really quick, but when I started using the Bacon Root Toolkit from WugFresh, it became exponentially easier.

It's been a long-rumored feature, but today, VoIP calling has finally started rolling out to users of Google's Hangouts service. Essentially integrating Google Voice into the popular messaging platform, Google has given Android (as well as iOS) users an easy way to make calls without eating up their plan's minutes.

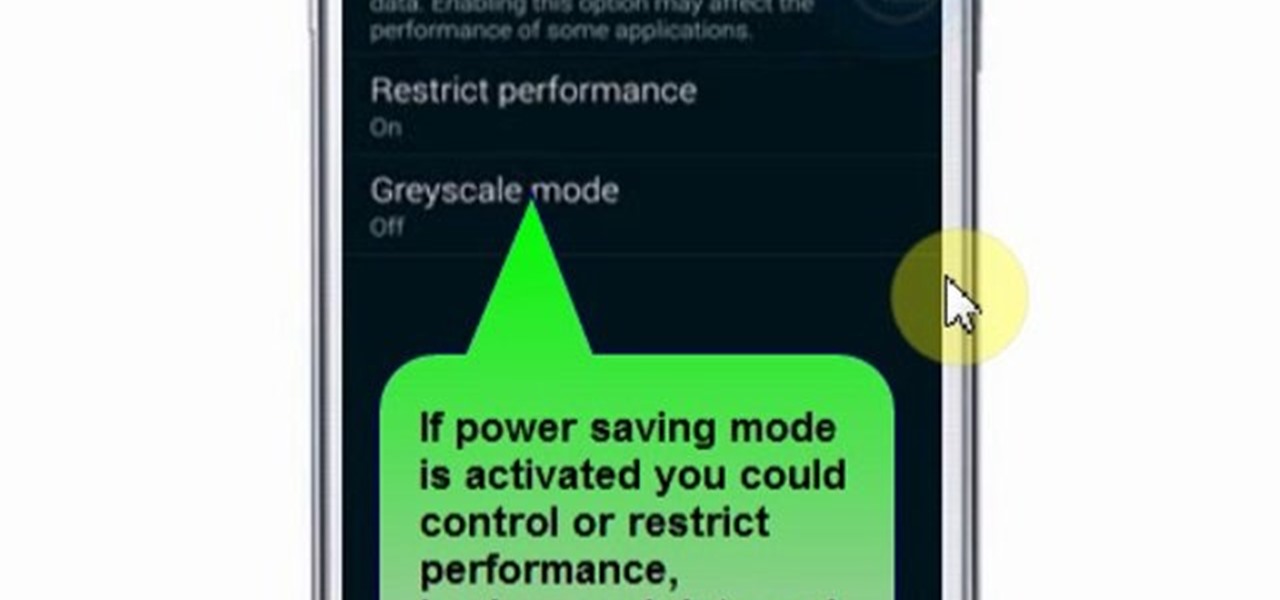
This video will show you how to set power saving mode in Samsung Galaxy S5 phone. Power saving mode will save or extend your battery life. So power saving mode will prevent unnecessary data usage. This mode will reduce screen brightness or turning off vibration and that will save your battery. This mode will control the display color which also saves battery. So this mode will save your internet connection usage and battery life. Follow the video.