Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

One of the coolest feature of the 3G iPhone is the high speed, always on, Internet connection. Having a constant connection to the Internet is pretty much a must have for any dot com mogul. The main problem with the iPhone is the screen is too small to do any serious Web surfing. Yes, it’s great for Twitter or checking up on emails but blogging from it is an exercise in frustration. Fortunately, there is a way to extend that 3G connection onto your laptop by turning your iPhone into a wireles...

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

Microsoft Excel is one of the most useful tools you can bring into your professional life. However, as useful as Excel is, it can also be difficult to learn on your own. The All-In-One Microsoft Excel Certification Training Bundle is an incredible tool that will take you from Excel beginner to Master for $33.99, on sale for 98% off.

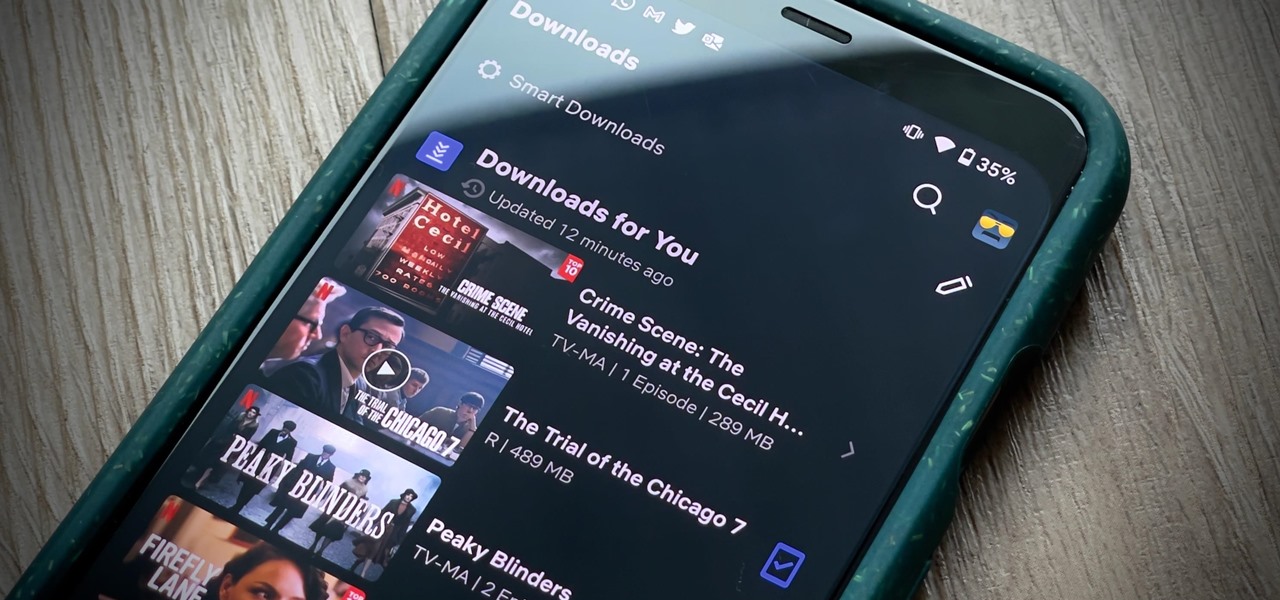
These days, there's more content than ever, and the sheer amount of titles out there can make picking something to watch seem near impossible. Netflix does provide suggestions based on content you've already viewed, which helps, and the company believes so much in its algorithms that it now gives you the option to auto-download videos on your devices based on your interests, no decisions required.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

It's no secret that more and more talented computer science gurus and programmers are turning toward high-paying careers in engineering. Today's engineers stand at the forefront of some of the world's most important and exciting technological innovations — ranging from self-driving cars and surgical robots to large-scale construction projects and even space exploration—and our reliance on these talented data-driven professionals is only going to grow in the coming years.

It can seem as though there's a virtually endless number of essential programming languages to choose from these days. And complicating matters even further for aspiring or even established programmers, developers, and hackers is the fact that most languages are a bit esoteric and suited for only a certain number of relatively finite tasks.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

In the not-so-distant past, cloud computing was thought of primarily in terms of online storage platforms. Now, however, massive cloud infrastructures are used by virtually every major business to reach clients, manage data, and deliver services.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

Since its original release as a spreadsheet program called Multiplan in 1982, Microsoft Excel has become the world's premier business software. If you think that it's only good for spreadsheets, you haven't been paying enough attention.

Whatever industry you're in, there's a decent chance you've had to work with Excel — that number-crunching powerhouse that drives the accounting departments of countless corporations across the globe.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

Just as predicted (but perhaps with less fanfare than usual), Apple has made the move of adding a depth sensor to the rear camera of its latest edition of the iPad Pro.

Spotify launched an experimental feature in early-2018 called Spotify Voice, a voice assistant that lives right in the app. It lets you speak to quickly find and play your favorite songs, albums, artists, videos, and podcasts on the music streaming service. Although the feature was initially only available on iOS, it's been ported over to Android so that anyone can take advantage of it.

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

With its 3D engine being responsible for approximately 60% of augmented and virtual reality experiences, Unity is continuing to place a premium on tools that not only keep developers working in its development environment but also make their workflows easier.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Being an Android user and having friends who are in the Apple ecosystem does not need to be a pain. You can easily send high-quality videos to iPhone users, so don't feel handicapped without access to iMessage. Sending high-resolution videos to iOS users is easy with this fast video-sharing method.

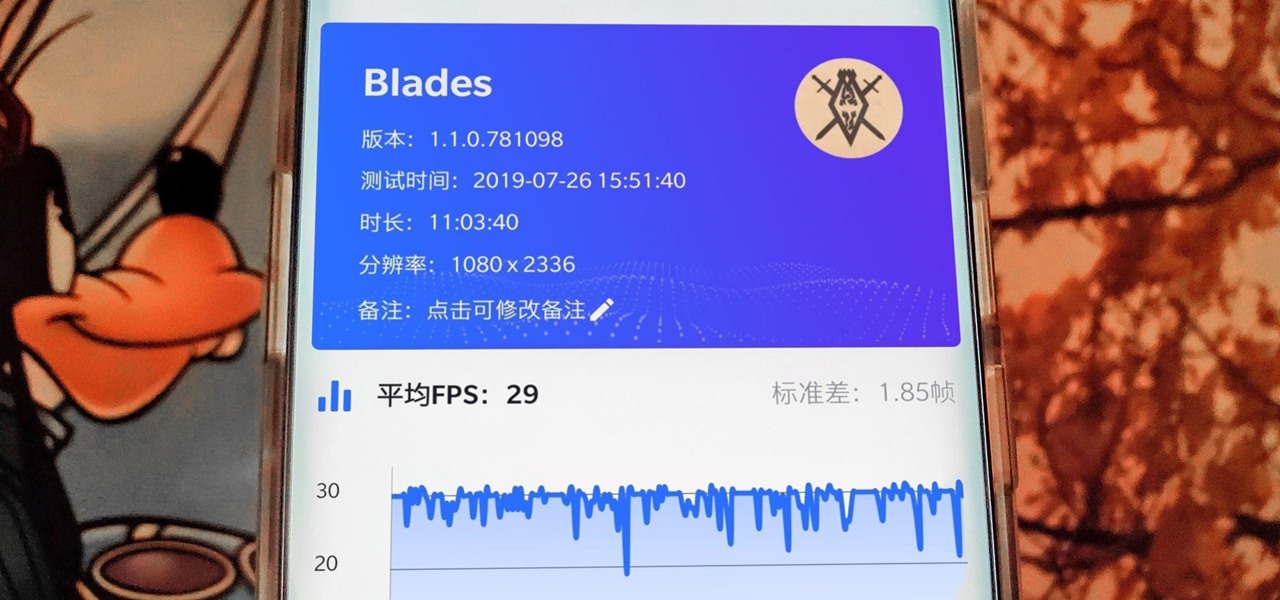
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

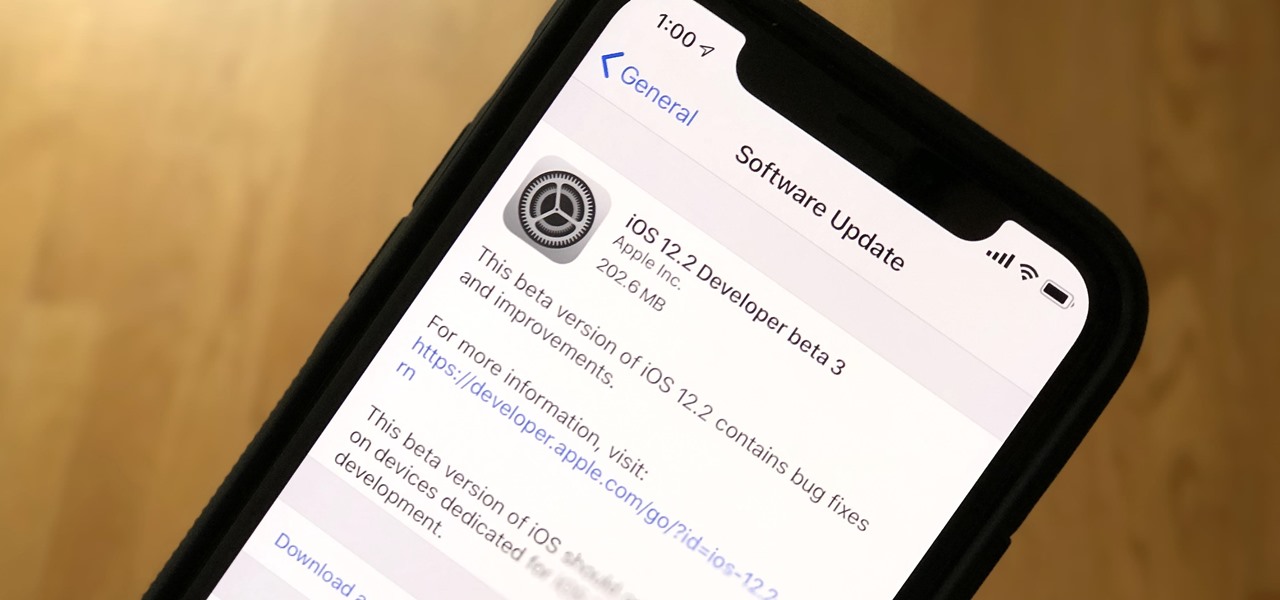
Apple just released the third iOS 12.2 developer beta Tuesday, Feb. 19, fifteen days after the release of iOS 12.2 developer beta 2. Beta 3 fixes an issue with the lock screen, and reintroduces Group FaceTime to beta testers. Overall, iOS 12.2 hosts a wealth of new features as well as bug and security patches.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

Niantic's most successful app, Pokémon GO, has become the first app to integrate the company's Real World Platform, the developer's AR cloud technology that enables multiplayer AR, persistent content, and occlusion with physical objects.

By now, you've probably already seen Andy Serkis and his performance capture demo for Magic Leap. And sure, marrying motion capture acting and augmented reality sounds compelling, but how does it really work as an experience?

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

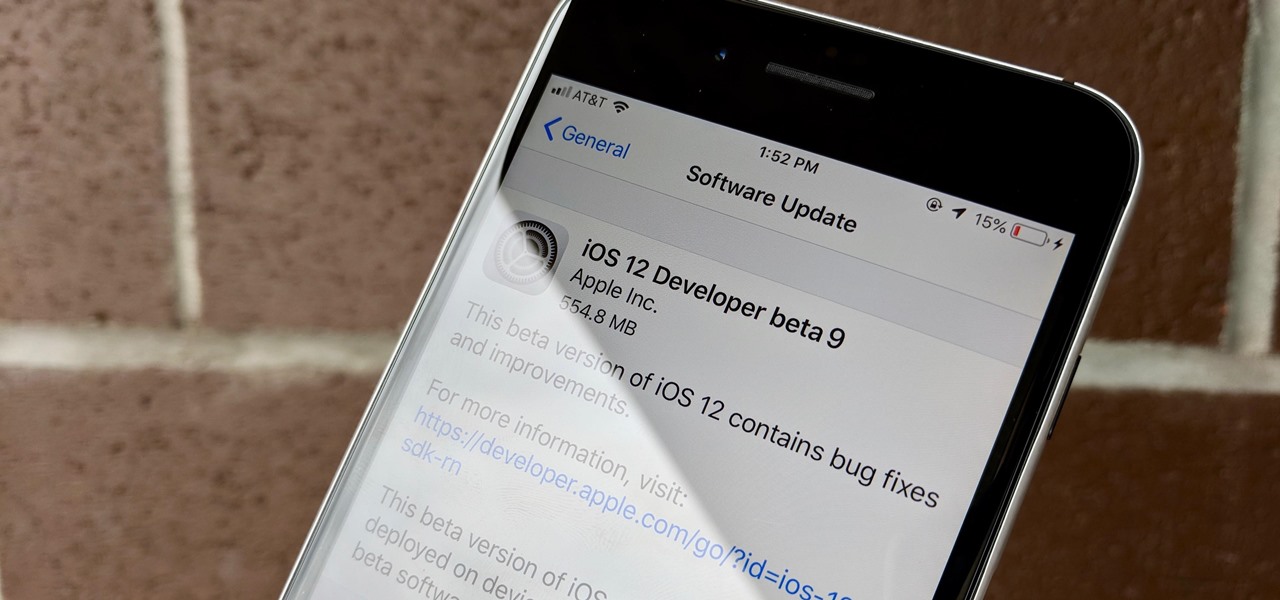
Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.

Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

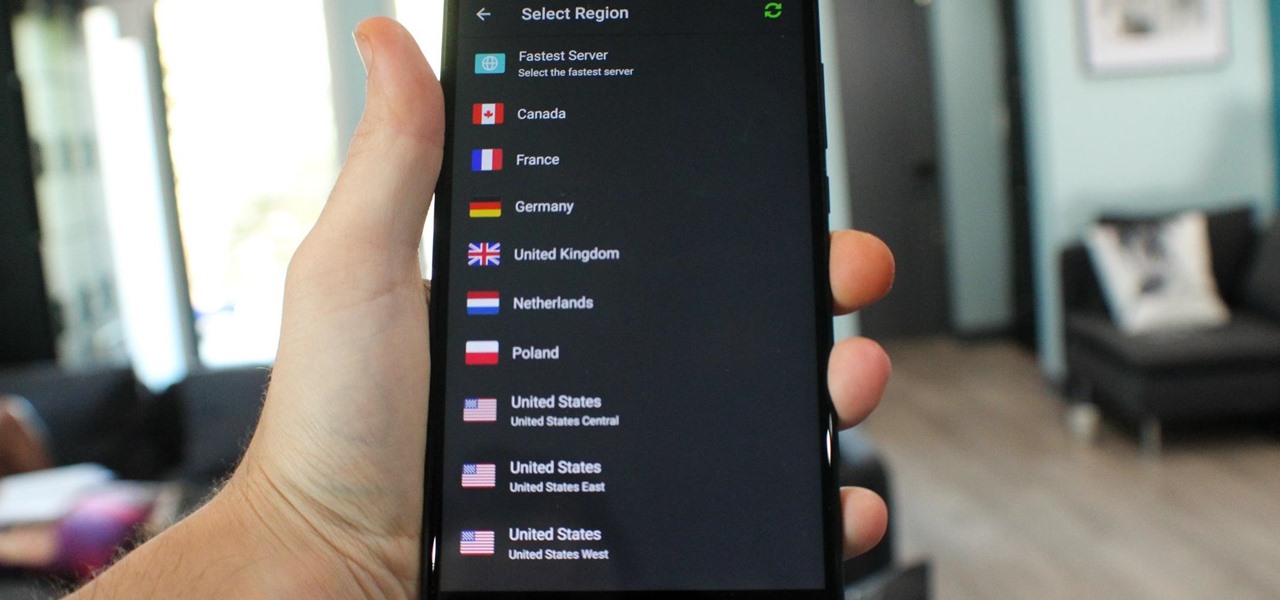
What you see when you open the Play Store is completely dependent on your country settings. Search results and top charts are specific to each region and there are lots of popular apps and games that simply won't show up unless your Play Store country matches up.

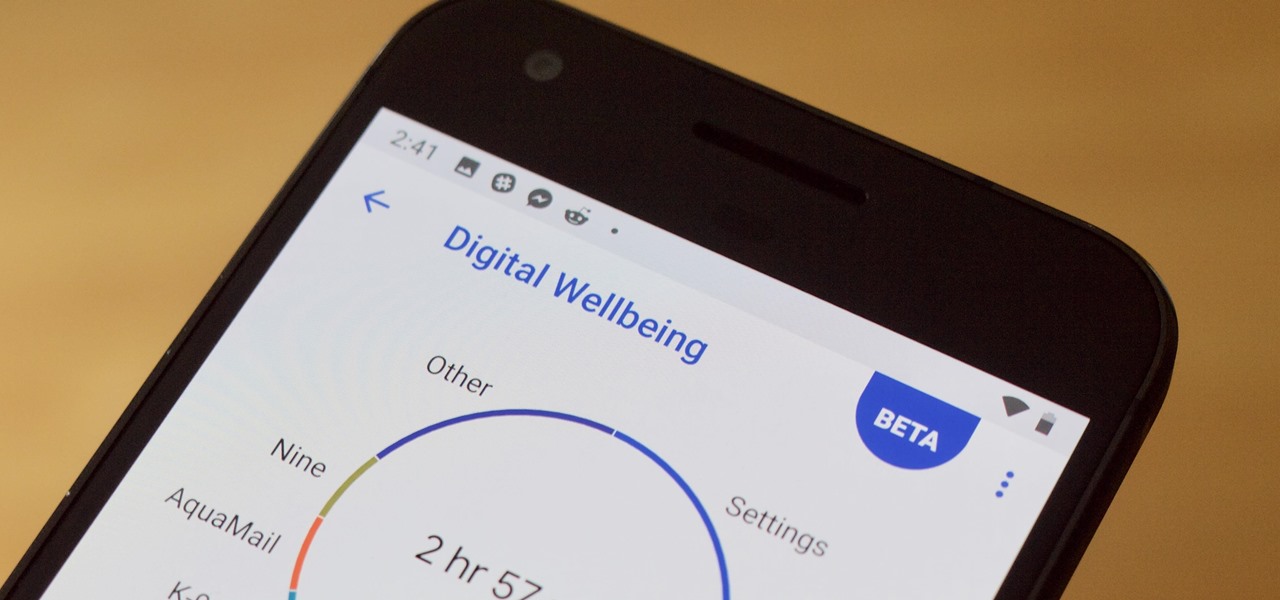
Is your smartphone taking over your life? Do you need help putting your Pixel down at night? Well, update to Android Pie! Android 9.0 comes with Digital Wellbeing, a new tool to both help you understand your smartphone habits and perhaps step away from the apps, games, and notifications every now and then.