In this Labrats video tutorial the instructors Andy Walker and Seab Carruthers show how to undelete the deleted files and recover them. When you save data to your computer, the computer stores the data in the binary format on the hard disk. To keep track of the files, the Operating System maintains a file table that shows the location of the data on the hard disk for a specific file. There are many file formats like FAT, NTFS etc. So when you are erasing the file only the entry in the file ta...

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

Check out this informative video tutorial from Apple on how to get started using Numbers '09. iWork '09, the office productivity suite from Apple, is the easiest way to create documents, spreadsheets, and presentations. Writing and page layouts are easy in Pages. Numbers gives you simple ways to make sense of your data. You'll captivate your audience with new and sophisticated features in Keynote.
Check out this informative video tutorial from Apple on how to use tables, color, images and fonts in Numbers '09.

Check out this informative video tutorial from Apple on how to create formulas with Quick Formula in Numbers '09.

Check out this informative video tutorial from Apple on how to hide, filter and sort table cells in Numbers '09.

Check out this informative video tutorial from Apple on how to group rows into categories in Numbers '09.

Check out this informative video tutorial from Apple on how to highlight values with Conditional Formatting in Numbers '09.

Check out this informative video tutorial from Apple on how to print spreadsheets in Numbers '09. iWork '09, the office productivity suite from Apple, is the easiest way to create documents, spreadsheets, and presentations. Writing and page layouts are easy in Pages. Numbers gives you simple ways to make sense of your data. You'll captivate your audience with new and sophisticated features in Keynote.

Check out this informative video tutorial from Apple on how to create and edit charts in Numbers '09.

Check out this informative video tutorial from Apple on how to work with Excel users in Numbers '09.

In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Every iPhone since the 5S has come equipped with a microchip called a motion coprocessor, which collects data from integrated accelerometers, gyroscopes and compasses, and can then transfer that information to fitness apps that track physical activity. Essentially, the chip knows whether you're running, walking, sleeping, or driving — but what if you don't want it to?

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

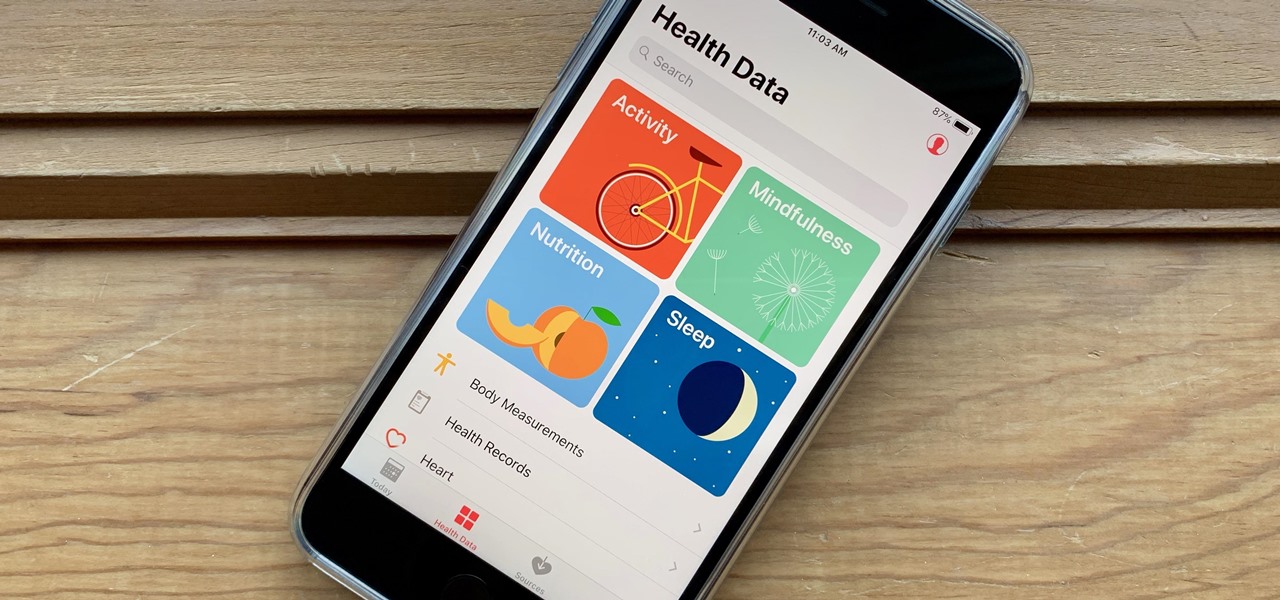
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

With the iPhone XS, XS Max, and XR, Apple introduced dual-SIM capabilities to iOS, made possible by eSIM technology. If you recently picked up one of these three new iPhones and need to utilize your eSIM while traveling abroad, you might want to take a look at the data plans offered by GigSky.

Another AR cloud savior has emerged this week in Fantasmo, a startup that wants to turn anyone with a smartphone into a cartographer for spatial maps.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Most of the free apps you'll find on the Play Store have ads. These ads are personalized — in other words, they're for products and services Google believes you might be interested in. The way Google knows about your interests is by collecting data from your smartphone, including your location and app usage. While personalized ads have their advantages, the collection of data is unsettling.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.

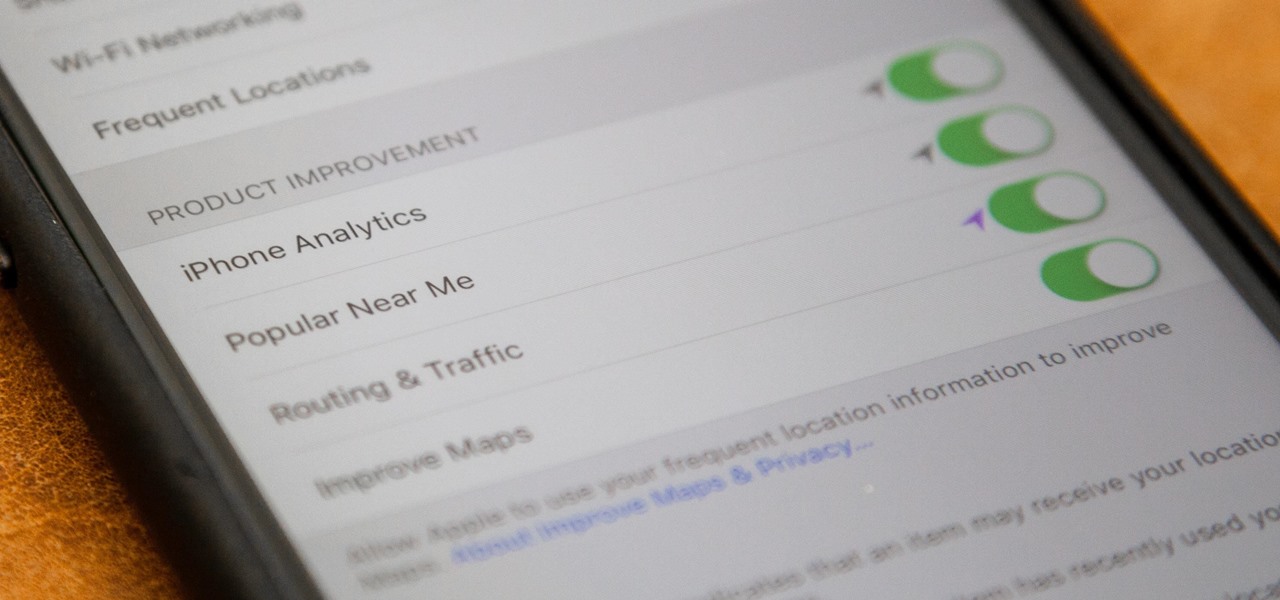
If you just installed the iOS 11 beta on your iPhone, you're automatically sending your location data to Apple — even if you don't want to. Luckily, there's an easy way to prevent Apple from seeing this data if you don't want them to.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

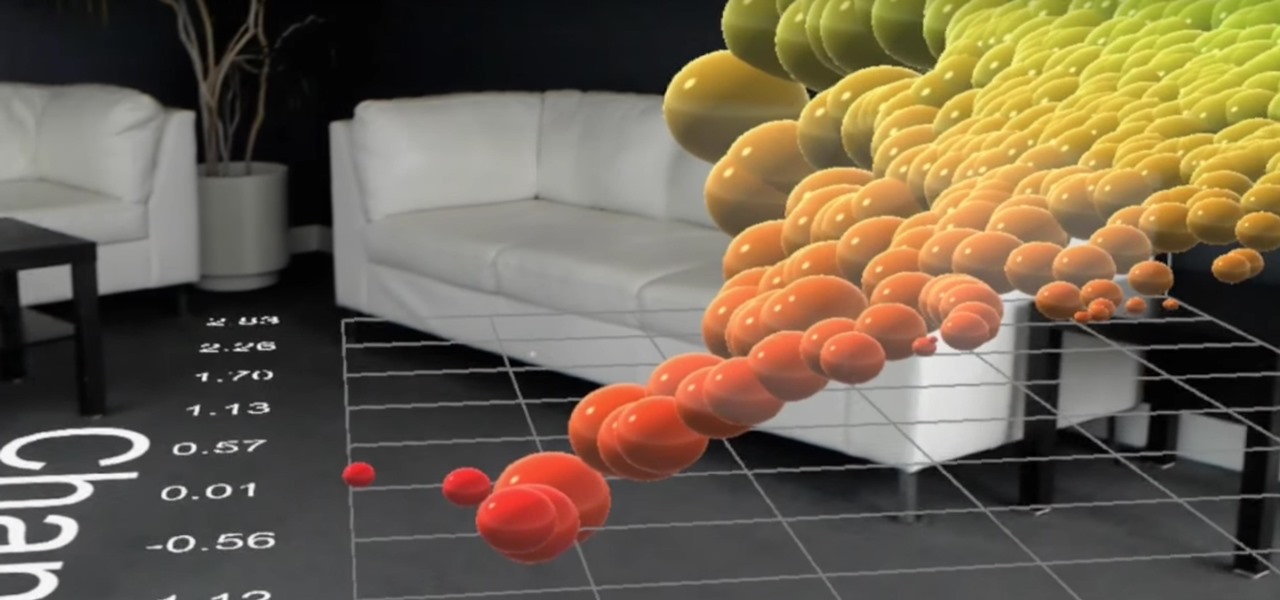
HoloLens developer Michael Peters of In-Vizible has released quite a few videos since receiving his HoloLens last year. Many of his experiments are odd and funny, but some include serious potential approaches to data visualization. In the videos embedded below, you'll specifically see stock market information beautifully rendered in different ways to help understand the data.

Everyone loves sharing pictures and quick video clips with Snapchat, but while the service itself is tons of fun, the Android app is one of the worst on the market. For one, Snapchat takes terrible photos even on high-end Android phones. And to make matters worse, the app is a notorious data-sucking battery drainer.

If you tend to go over your data allotment each month, or are constantly afraid you will, Verizon Wireless is giving you chance to relax a little bit with up to 2 GB free data for two months.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

Tons of iPhone 5 users with Verizon Wireless hit the message boards last week complaining about their phones sucking down massive amounts of cellular data when they were actually using a Wi-Fi connection. Of course, that means Verizon customers could have been getting charged for cellular data they weren't actually using.

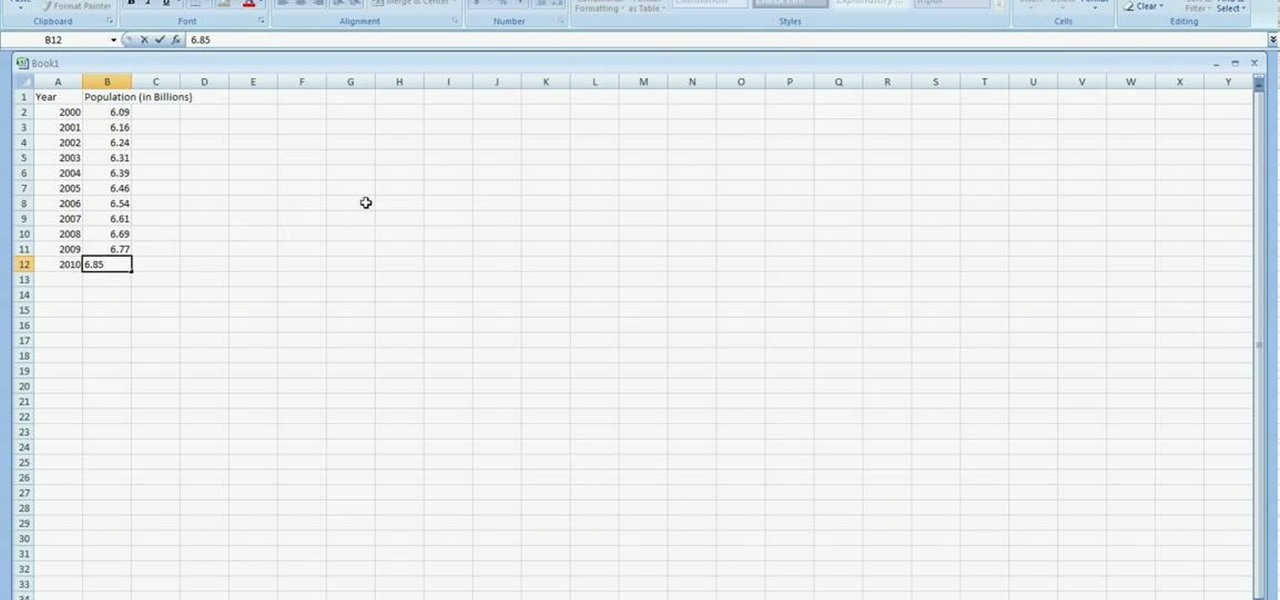
In excel a left click is made on box A1 and the X title is typed in as year. In A2 the year 2001 is typed and in A3 the year 2002. Both A2 and 3 boxes are highlighted and the bottom right hand corner is used to drag the work into a copied sequence down to A12. In B1 "population in billions" is typed. From the web site the data is copied and typed in as it appeared and the numbers are rounded off. A click is made on the "insert" tab and line is selected from the menu which appears. The upper l...

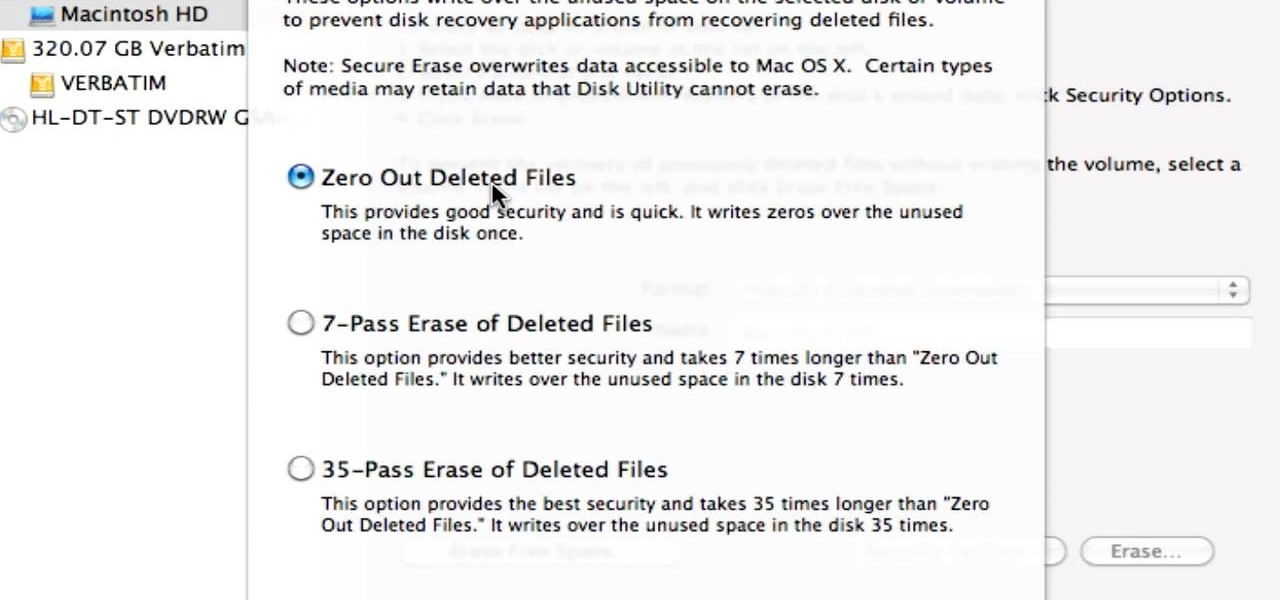
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...

Crochet loopy granny squares will indeed remind you a little bit of your Gran Gran's favorite knitted coasters that she collected en masse throughout her lifetime. But the snuggly, historical and vintage quality of these granny squares is exactly what makes them so delightful.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

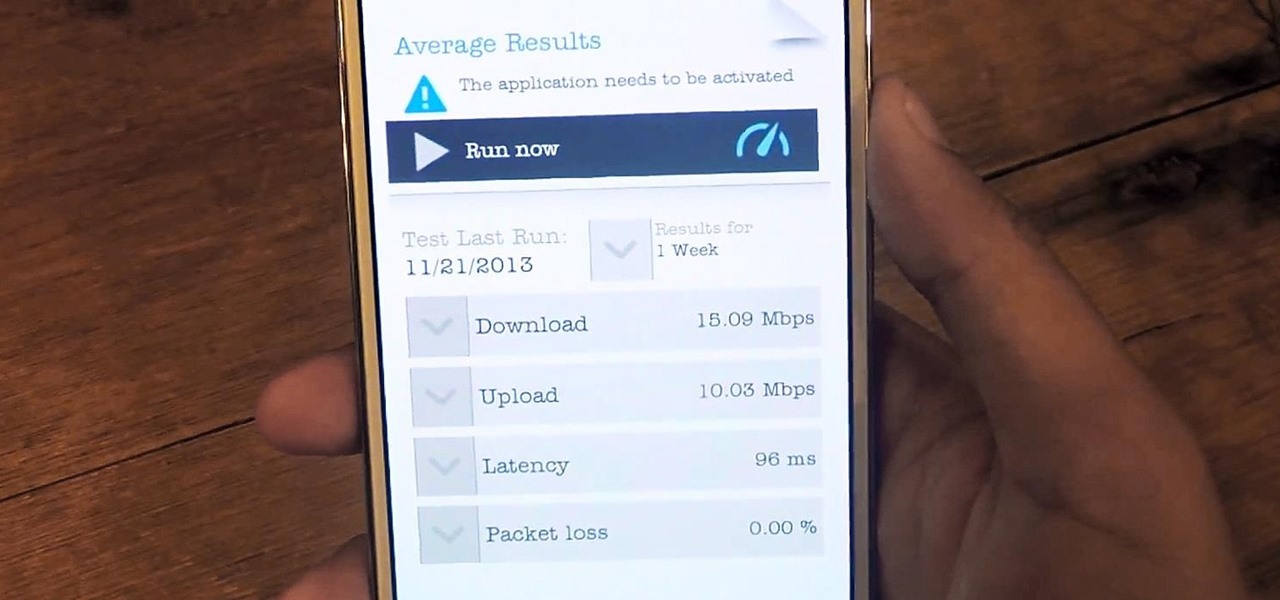
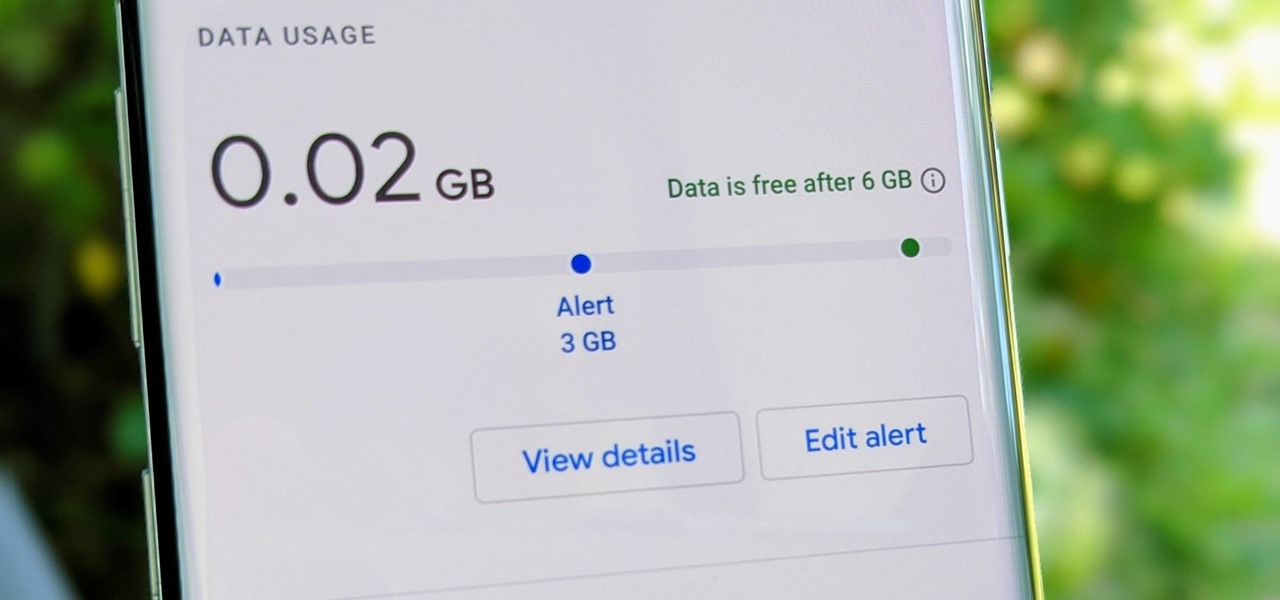
Google Fi Is a great wireless carrier alternative and can be quite beneficial when used correctly. If you don't require much data, you can easily get away with a $30 or less bill. However, if you wanted to crank out more data during your current billing cycle, there's a setting you should use to keep your data in check.