
How To: Do single leg twisting dumbbell curls
Learn how to do single-leg twisting dumbbell curls. Presented by Real Jock Gay Fitness Health & Life.


Learn how to do single-leg twisting dumbbell curls. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do dumbbell straight-leg deadlift and dumbbell rows. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do reverse dumbbell flys on incline bench. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do seated arnold presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do medicine ball pull-overs. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do jump triceps bench dips and sculpt your body without weights. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do seated dumbbell hammer curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do dumbbell 45-degree angle raises. Presented by Real Jock Gay Fitness Health & Life. Benefits
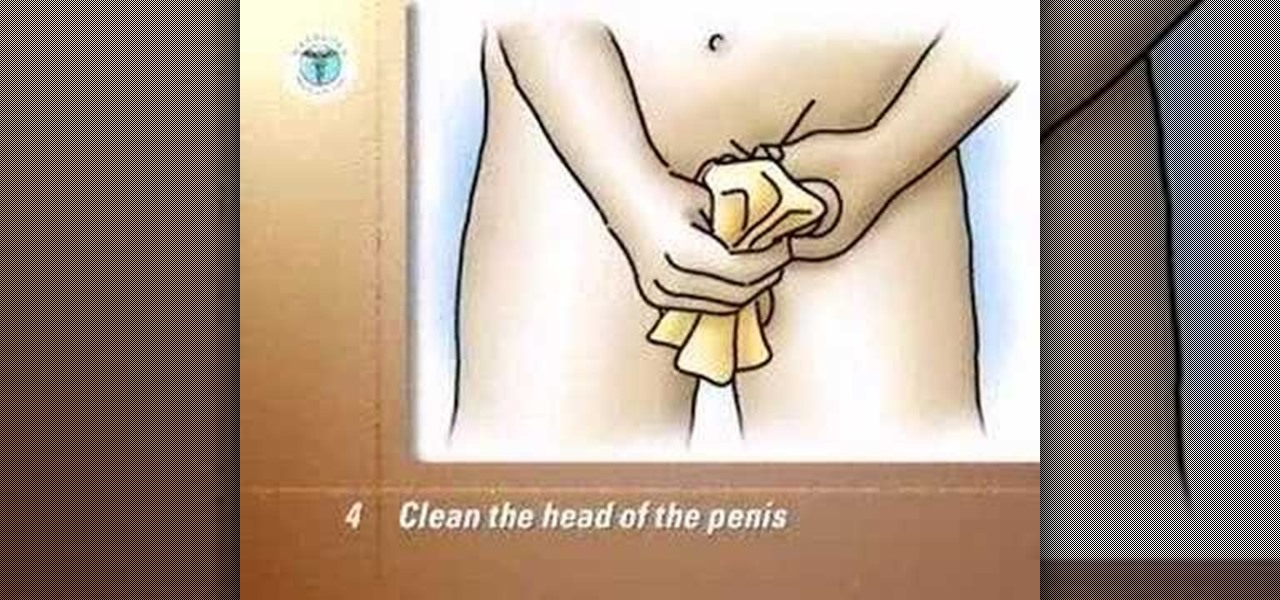
Void into the hat. Measure the amount of urine and record it in the voided volume column on your record sheet.

Origami isn't just folding paper, it's a form of art. So, if you want to try a new creative way to express yourself, and if you like birds, try out this tutorial on folding an origami paper swan.

Tim Carter shows you how to install the sink with these easy to follow tips. Watch this video for best results. Position the new sink upside down on the countertop and accurately trace the outline of the sink. This provides a guideline for the real mark for the cut-out. The cutout will normally be about 3/16" inside the original mark. This allows for the lip of the sink to overhang the counter top. Check the sink installation directions for the proper measurement. Don't make square corners wh...

Improve you crocheting skills by learning the basics. This how to video is a tutorial that will show you how to hold yarn while crocheting. There is no right or wrong way to hold yarn, but this method my help you.

This video illustrates how to spike your hair for the cosplay. Here are the following steps: Step 1: Shampoo your hair and then deep condition them and then with a hair brush start teasing your hair that means take small strands of your hair and then brush them back with fast strokes .

Learn how to hold a golf club properly in this sports video tutorial. The first thing is to allow the handle of the club to lie on the fingers of your left hand. It should lie diagonally. As you close your hand around the grip and lift the club off the ground, you should have a sensation that the handle is underneath the back of your palm and the last three fingers are applying pressure and squeezing it into your palm. The second step is to put the right hand on the golf grip in a diagonal li...

In this instructional video you will learn how the WWE choke slam is performed. Be sure to understand the stunts performed should not be done by just anybody but by professionals. Now, whoever the attacker is they want to place their right hand on the very top of the defenders chest, and once that happens the defender will take his left arm and hold the attackers arm like he's actually being choked. Next, the attacker will put the defenders right arm over his right shoulder and the attacker d...

This quick video will teach you how to make the most effective paper airplane. Follow these steps to make a very effective paper airplane: You will need a sheet of computer paper. Fold it in half and open it back up. Fold in the top corners. Fold the top half down. Fold the corners down and fold up the little area in the middle to hold down the flaps. Fold it backwards and fold the edge of the wing to the bottom of the plane. Repeat for the other side. Hold your plane at the triangle, and thr...

This video shows the basics of limit Texas Hold 'em. Limit means that there are set amounts that you can bet, unlike no limit where at any given time you can bet your whole stack. He explains a game of $2 /$4 limit Hold 'em. This means that before the flop and after the flop you can only bet $2. On the turn and on the river you can bet $4. If you decide to make a raise on someone's bet it can only be in the set increments of 2 and 4 dollars.

Lock picking is a great skill that takes lots of practice and patience to master, but some locks simply can't be picked, like a Master Lock combination padlock. With a combination lock, you'll have to do it the old-fashioned way—cracking combinations.

The volume buttons on the side of your iPhone can do more than just adjust the volume levels for media, ringers, alerts, Siri, and other sounds and voices. You can use them to perform different actions in certain apps and even create custom actions using the Shortcuts app. It's not exactly button mapping, but it's as close as you'll get without jailbreaking iOS.
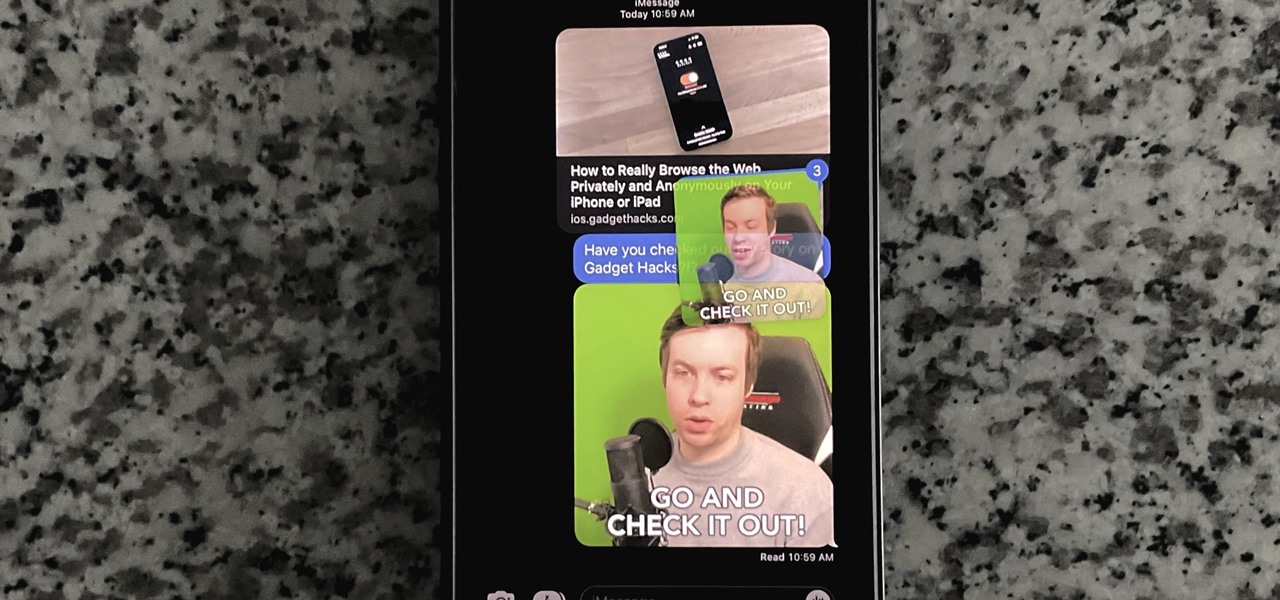
The Messages app for iOS and iPadOS has a lot of hidden features, but one in particular can save you time and energy whenever you need to forward or copy and paste messages from within an SMS, MMS, or iMessage conversation.
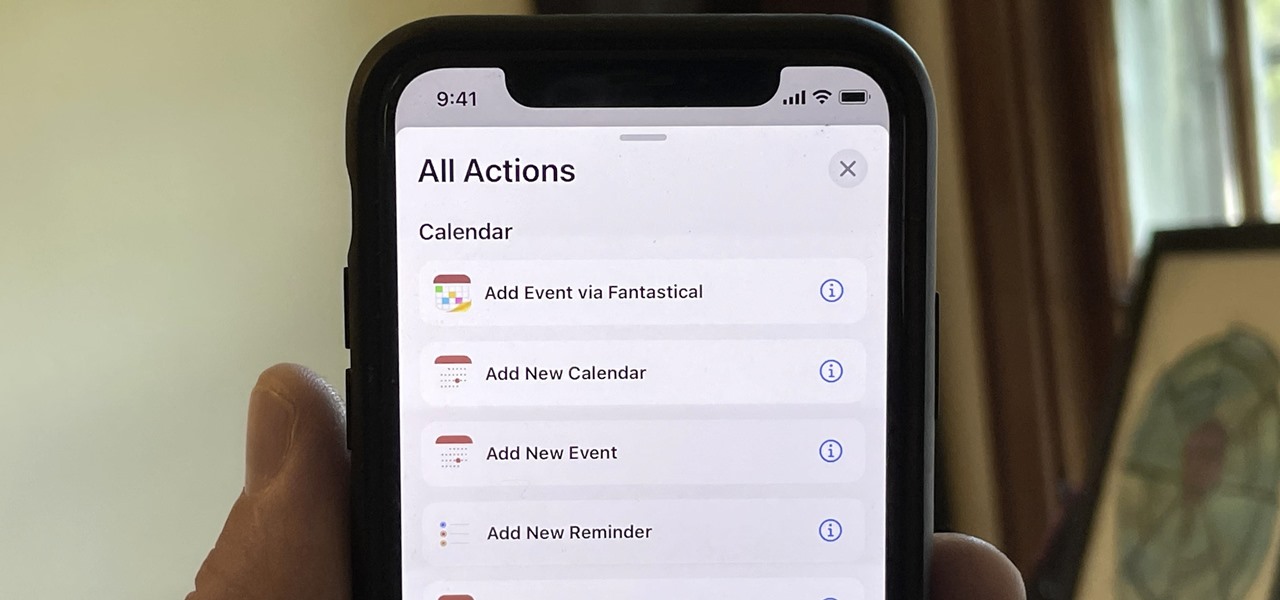
One thing you couldn't do in the Shortcuts app when building a shortcut was browsing the entire list of available actions for all of the apps and services on your iPhone. That all changes in iOS 15.

With non-fungible tokens (NFTs), particularly those that are 3D in nature, holographic displays are becoming more indispensable for those looking to show off their valuable works of art.

Everyone needs a great website. Whether you want to launch the new business you've been dreaming about in 2021, increase your brand's web presence and bring it into the digital realm, or promote yourself and your portfolio, a fully optimized website is the way to do it — and the results can be life-changing.

Effective communicators are always in high demand in every industry. Whether your team is building the next billion-dollar app or you have a giant data set in front of you for filtering, communicating with your team is essential.

We all know how hard it can be to stay productive, especially when working from home. There are many distractions throughout our day. Organizing your workflow is necessary for getting anything done.

Your iPhone's almost out of battery power, there's no wired or wireless charger in sight, and you left your portable power bank at home. You don't want your battery to die, but you still need to use your iPhone. This is when Low Power Mode comes in handy, but you could be wasting valuable time and power if you're activating it the wrong way.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

We're living in a world that runs on Big Data. As the driving force behind everything from self-driving cars and Google algorithms to the latest medical technology and financial platforms, massive sets of increasingly complex data lie at the heart of today's most exciting and important innovations.

When you need to type in all caps on a computer, you just press the "caps lock" key. But no such key seems to exist on iOS. The "shift" key appears to work at first but will deactivate once you type one capital letter. Holding down the shift key while you type gets the job done, but it's a pain. While it might not be obvious, enabling caps lock is actually really simple.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

If the interconnected worlds of blockchain, Bitcoin, and cryptocurrencies scare you a bit, you're not alone. Thanks in part to the extreme and seemingly random fluctuations in the value of Bitcoin over the past three years, more than a few developers and investors are wary of the cryptocurrency revolution and its ties to blockchain development.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.
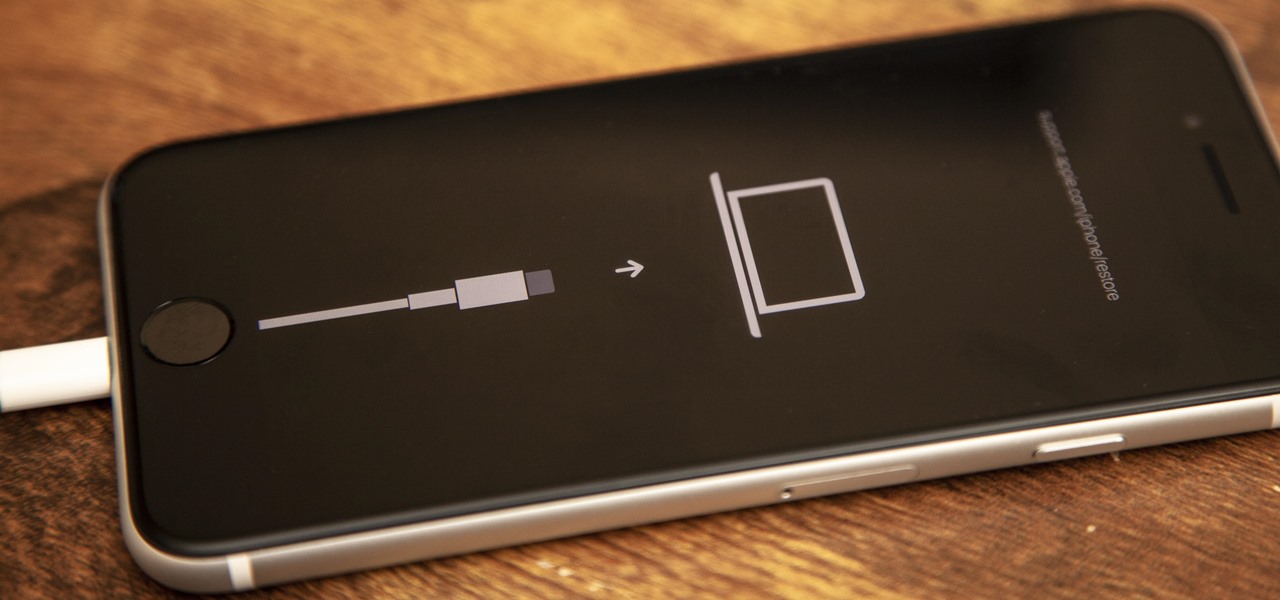
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your fail-safe.

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

The book is almost closed on 2019, but Magic Leap has one more gift to offer its users before the new decade arrives.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.