
How To: Turn an wireless X10 camera into a helmet cam
See how to make an X10 wireless security camera into a nice helmet cam on the cheap in this three-part video. All it takes is an X10 camera, ten bucks in parts, and two hours of your time.


See how to make an X10 wireless security camera into a nice helmet cam on the cheap in this three-part video. All it takes is an X10 camera, ten bucks in parts, and two hours of your time.

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.

While most iOS updates will only improve the experience on your iPhone, some can cause more havoc than good. If an update unexpectedly breaks or degrades certain functions on your iPhone, you may be able to roll it back to the previous software.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.
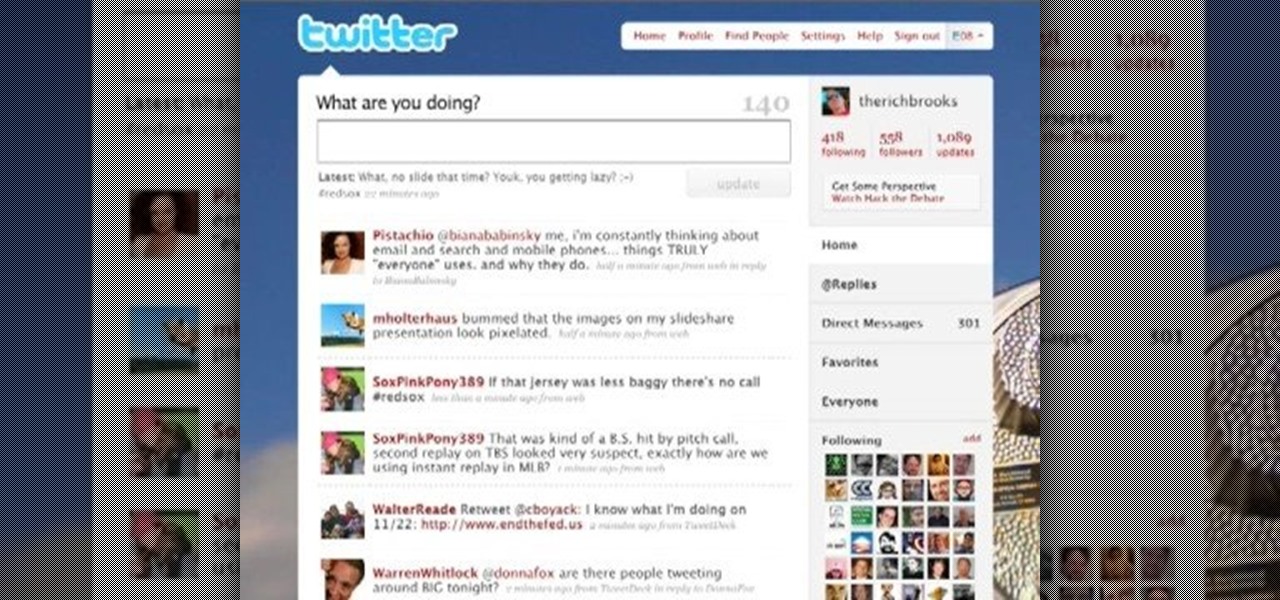
In this tutorial, we learn how to sign up and set up a Twitter account. Twitter is a social networking site where you have 140 characters to tell your friends how you are feeling, what you are doing, or talk to them! You can follow people and other people can follow you. You can choose who follows you, which will create and strengthen online relationships. You can even get business referrals from this! Just by getting yourself out there, this is a great tool. To sign up, you will simply go to...

In this tutorial, we learn how to remove pop up screens when Avira Antivirus updates. First, locate the installation folder for Avira, this should be in your computer programs. After this, locate the file "avnotify.exe". Next, right click this and go to the preferences option. Now, go to security, then edit, then click on the system option. Click "deny" on all the boxes in the bottom section, then save these. Now, the next time your Avira updates, you will not get a pop up box that tells you ...
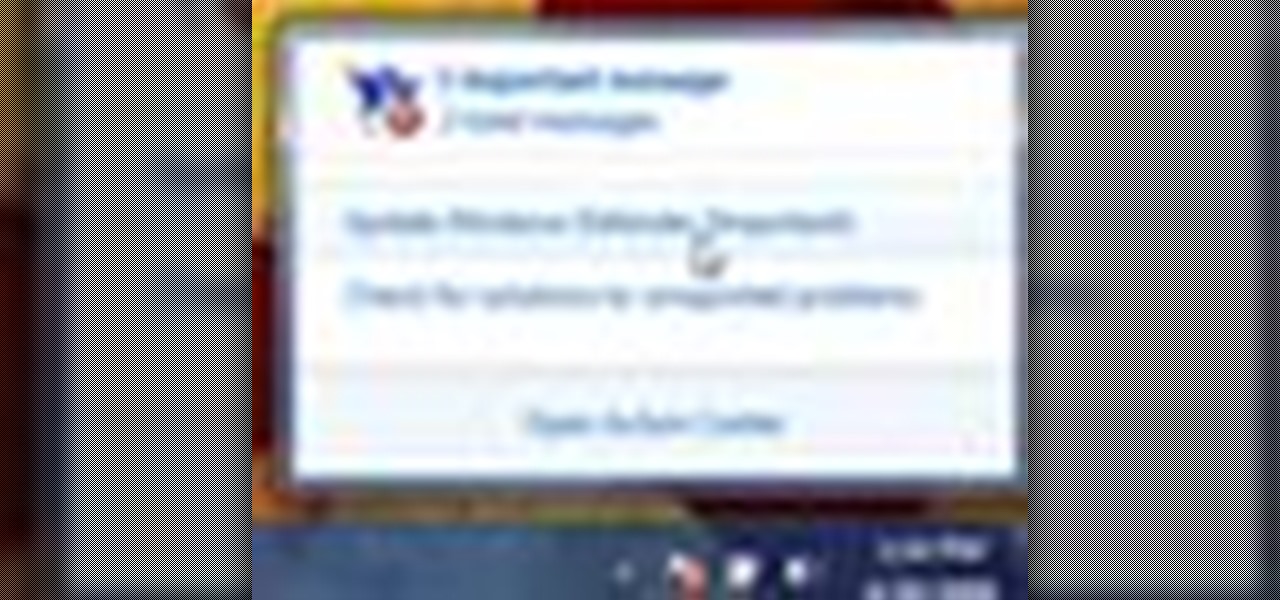
Tired of your PC pestering you to check this or fix that? Are you sick of all those pop-up balloons? Well, Windows 7 now has a feature called Action Center, and it lets you decide which alerts you see and which ones you don’t. See it in action!

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

You have an online store ready to go… almost. You still have to deal with getting the perfect shopping cart to go along with your e-store. Matt Winn from Volusion walks you through what to consider when choosing a shopping cart software for your online store. From what type of software exists in the market, to the required features, to security levels (PCI certification), to the type of support you may need.

This video shows us how to install a ceramic soap dish in our bathroom shower. In this demonstration the instructor already had a slot in the shower tiles for the soap dish to go. Attach a long strip of masking tape on the edge of the soap dish. Mix some grout and place this on the part of the soap dish you are attaching. Be generous with the amount so you know it will stay. Place the soap dish in the slots and use the tape that you attached to be extra security that your dish will not fall. ...
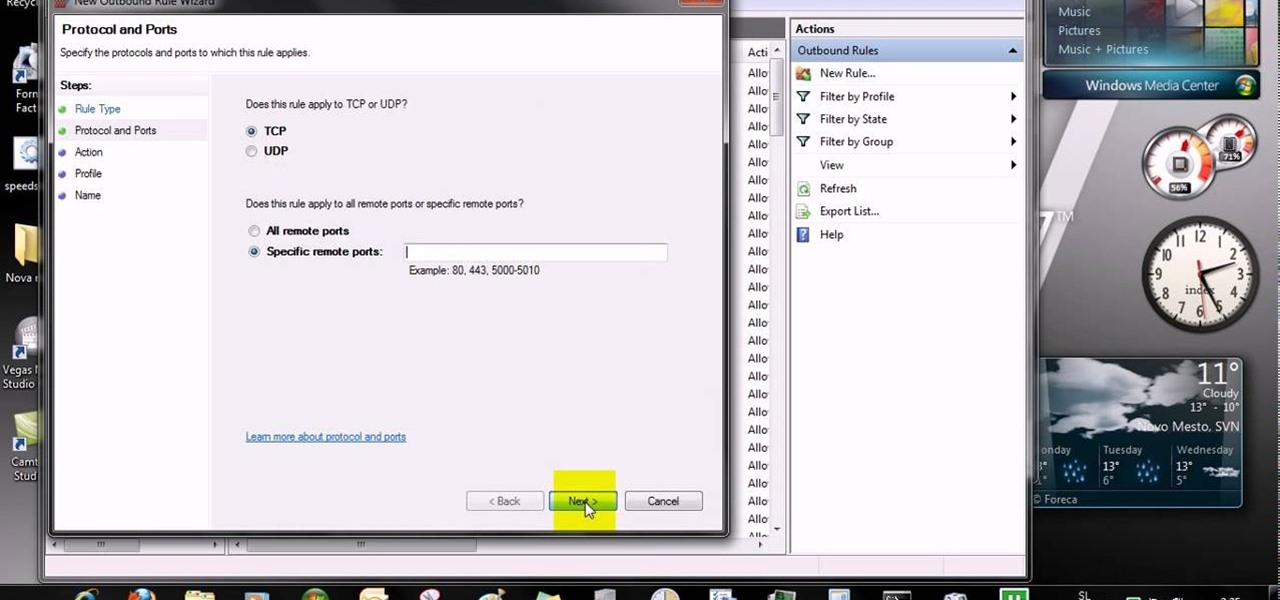
This video tells us the method to open ports in Windows 7. Click on myu icon and go to 'Preferences'. Copy the port number from the resulting window. Go to 'Start', 'Control Panel' and 'System and Security'. Go to 'Windows Firewall' and 'Advanced Settings'. Go to 'Inbound Rules' and 'New Rule'. Click on 'Port' and select 'TCP' and 'Specific Local Port'. Type the port number in the text box. Click 'Next' and 'Allow Connection'. Press 'Next' twice and put the name in the space provided for it. ...
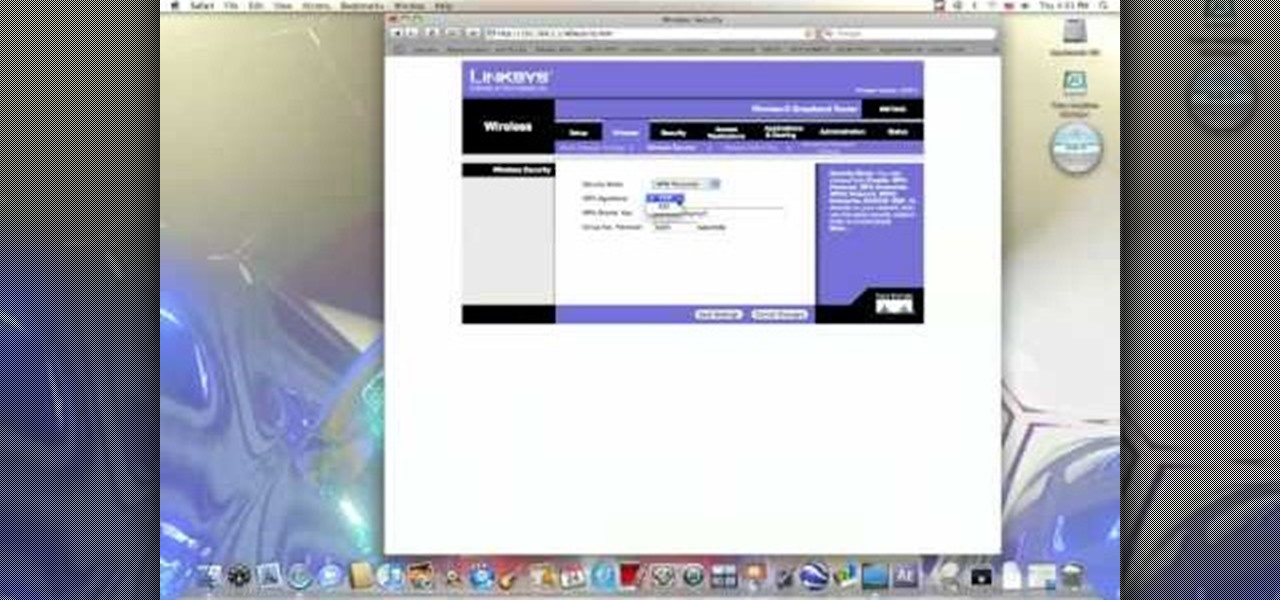
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...
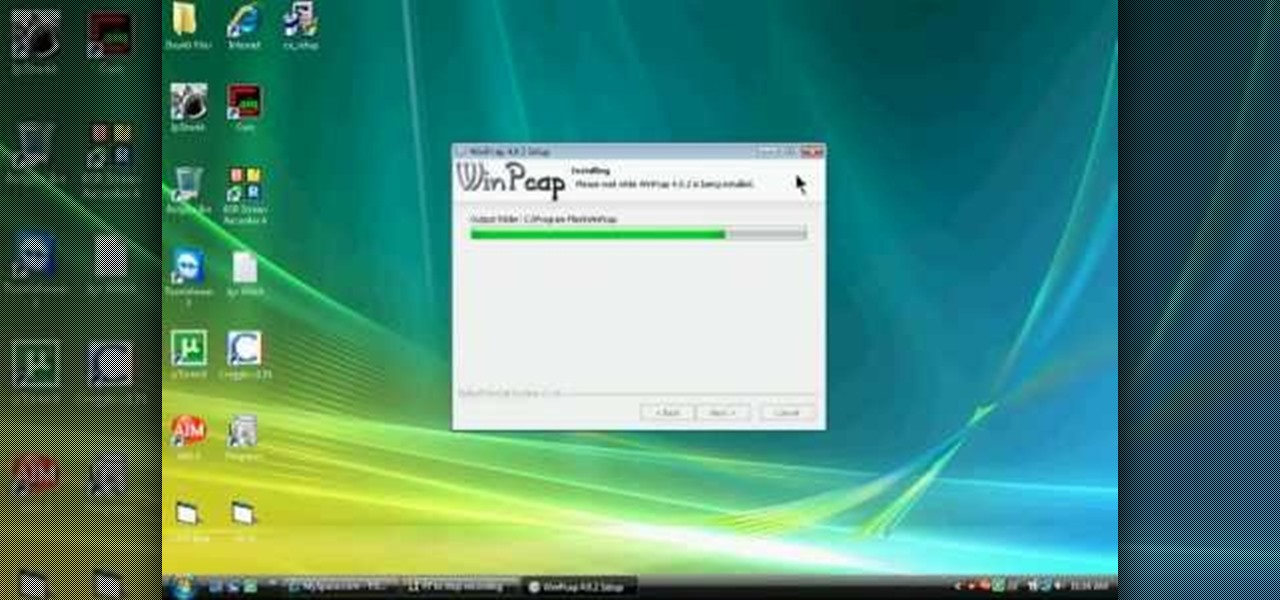
First you have to install program, called 'Cain and Abel'. Then, you will be automatically asked to install 'Win Pcap' and you should do that. After installation you have to click on 'Cain and Abel' program icon with right mouse button and start it as administrator. Then push blue plus sign to scan Mac addresses. After scanning go to the bottom of program window and press APR tab. Then push blue plus icon again. When table appears push first option in first square and first option in second a...
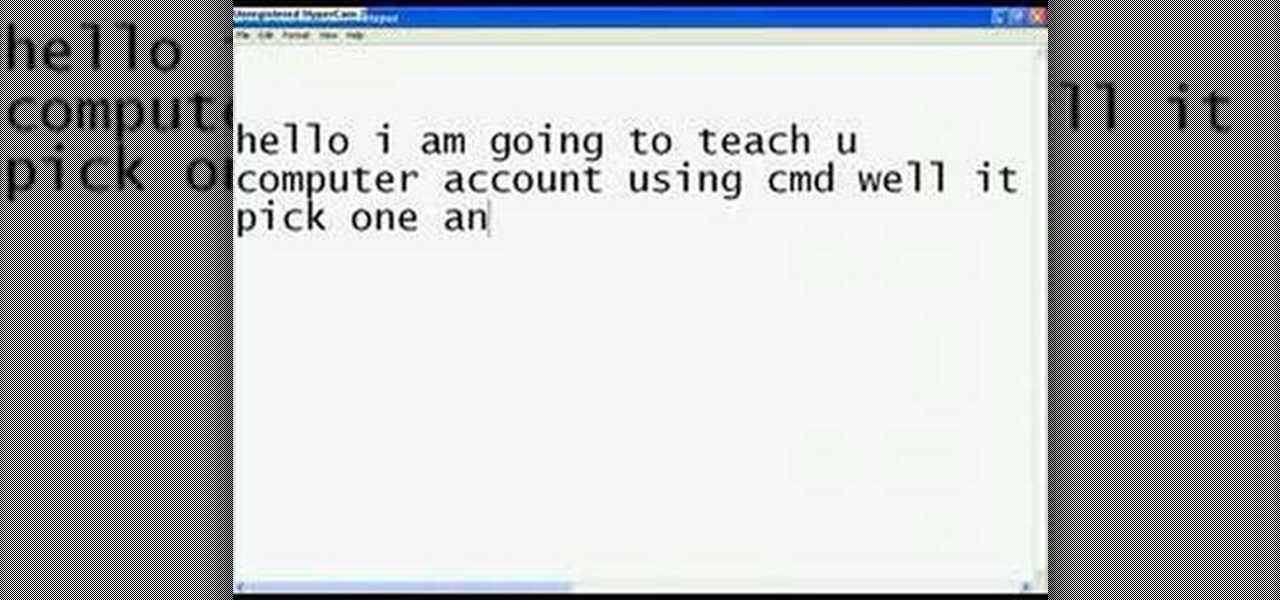
This video teaches you how to change your computer's account password using the DOS command prompt. The first step is to get to the command prompt, you can do this simply by clicking run in the start menu and typing "cmd." You next type "net user" which will show you all of the user accounts on the computer. Choose the one you would like to change the password for and type "net user (account name)." It will then ask you for a new password, you may type anything you like here keeping in mind t...

Have some files you don’t want anyone to see? Or maybe it’s just been a while since you’ve emptied your trash bin. The trash bin function is not a permanent delete but you can erase files off your Mac with this tutorial.

Watch this video to learn how to get Aircrack on your iPhone or iPod touch. You can use Aircrack on your iPhone or iPod touch to recover wireless network keys. The program runs directly on your iPhone or iPod touch device. It is installed as any other third party iPhone app, easy to launch and speedy to set up. Aircrack can be used as a security testing tool. Use it to verify that your network is attack immune.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hack a SharePoint site.

Check out this instructional con video that demonstrates how to pick a Wafer lock. They are commonly used in thefts. Regardless of the security level, the picking technique is the same. Follow the simple instructions outlined in this tutorial video and learn how to pick a wafer lock. Start picking locks like a pro!

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.
Apple seeded the official version of iOS 13 to compatible iPhones on Sept. 19. Since then, we've seen two major updates — iOS 13.1, which, by our count, introduced 22 new features, and iOS 13.2, which also added 22 new features. Today, Dec. 10, Apple introduced the third major update: iOS 13.3.
Since the release of iOS 13.3 beta 3 on Nov. 20, Apple has remained silent on new beta updates. That's likely because there was a holiday the following week, and then all of the major shopping events after that. But now, it's back in the game, and on Thursday, Dec. 5, Apple pushed out iOS 13.3 developer beta 4 and public beta 4.

In iOS 13, Apple introduced HomeKit Secure Video, which allows smart home devices with cameras to give iPhone users a private and secure way to store recorded videos. Plus, it has benefits such as object detection and activity notifications. Logitech is the first to add support for HomeKit Secure Video with its Circle 2 cameras, and all it takes is a quick firmware update to get started.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

Who's ready for another beta season? We beta testers have had quite the break: Apple released the fourth public beta for 13.2 on Oct. 23, and since then, two full weeks have gone by without a shred of beta news. It seems this Wednesday, Nov. 6 is our lucky day, as Apple just released the first public beta for iOS 13.3.

In recent years, the US military has been utilizing augmented reality as a training tool, giving officers and soldiers an opportunity to train and hone their decision-making, tactical efforts, and weapons accuracy via virtual scenarios.

While the eyes and ears of the iPhone world are singularly fixated on iOS 13 and its suite of over 200 new features, Apple was actively piloting iOS 12.4 in tandem with the big iPhone update, in preparation for the release Apple Card. Today, Apple has finally seeded iOS 12.4 stable, 116 days after its first beta version, and there's still no concrete evidence that Apple Card itself will show its face.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.
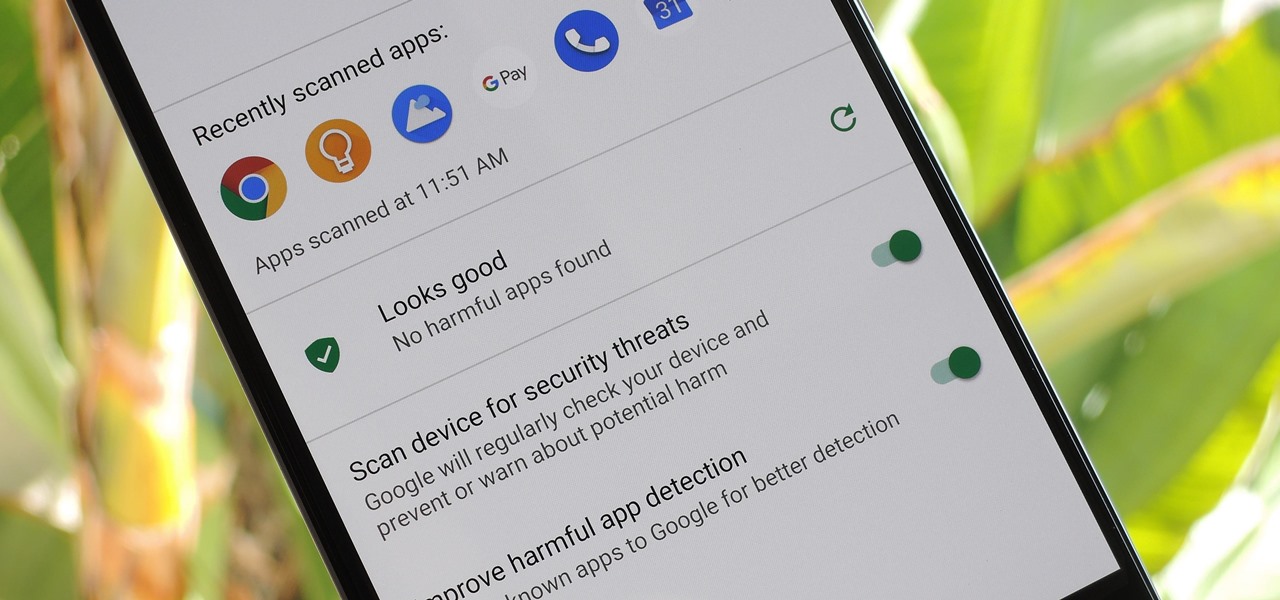
According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

Apple released the third beta for iOS 11.4 on Tuesday, May 1. This update comes exactly two weeks after the release of the second beta, which, in addition to adding a new wallpaper, fixed issues with AirPlay, Music, and Keychain. The only noticeable change in beta 3 is a fix for unresponsive 3D Touch.
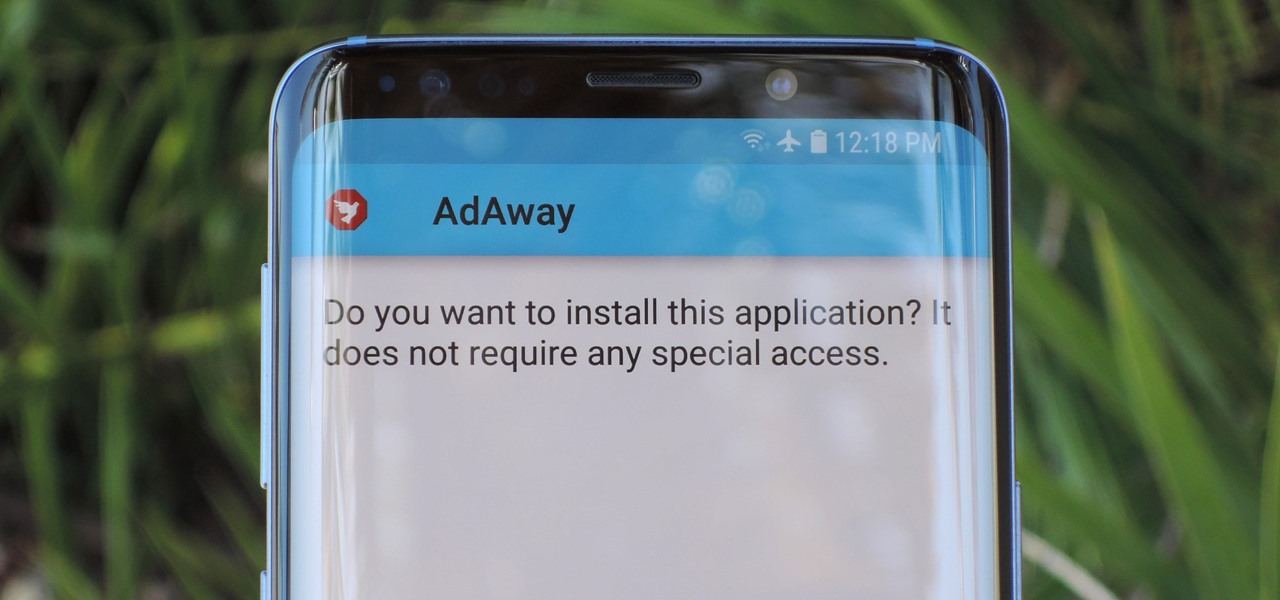
Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.
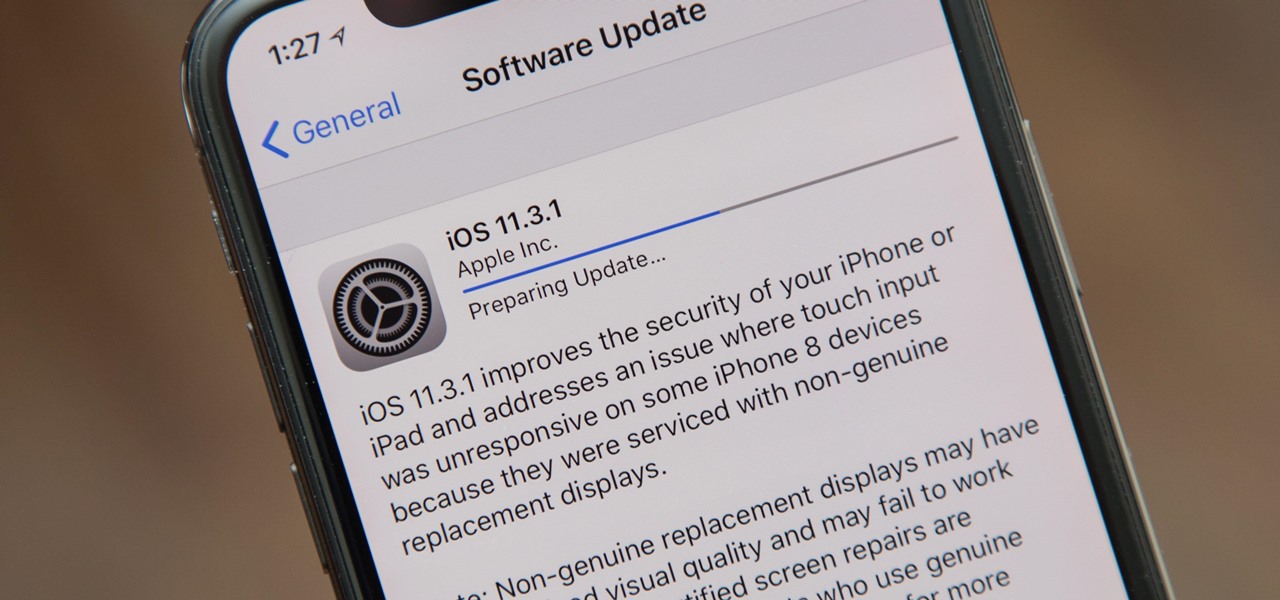
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.