Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

The world of root is upon us, folks. While the LG G3 has be available for purchase for a couple of months now, rooting had been a shaky subject. International and T-Mobile variants enjoyed root from day one, while various security patches left the AT&T and Verizon Wireless variants as a mixed bag, and Sprint completely out in the cold.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

It was only a matter of time before the apps from the new Samsung Galaxy S5 leaked for everyone to download and install, and today we've got one that takes advantage of the IR blaster on your Galaxy Note 3.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Smartphone users these days can get bombarded with texts and emails every hour. Online retailers sending you coupons to get you to buy stuff. Girlfriends asking where you are. Service providers reminding you to pay your bills on time.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

With the Android 4.4 KitKat update slated for release sometime in October (according to Nestle), I'm sure you're excited to get your hands on and test out all of the new features of Google's latest mobile operating system.

There are many impressive features on a Samsung Galaxy Note 2, but just like any other smartphone on the market, the most used one is the camera. How many times did you take a picture today? Or admire all the selfies in your gallery? Or upload a video to Instagram, Vine, or Snapchat?

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints.

There was recently a case that came to national attention where a gentleman was arrested at an airport for having a watch that looked like a bomb, among other things. As it came out, the watch was, in fact, not a bomb, and the man was just an artist who was probably trying to make a statement of some sort. Well, that message was lost amongst the hail of people shouting that either he had been stupid for bringing that watch on the plane and so deserved to be arrested, or that it's a free count...

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

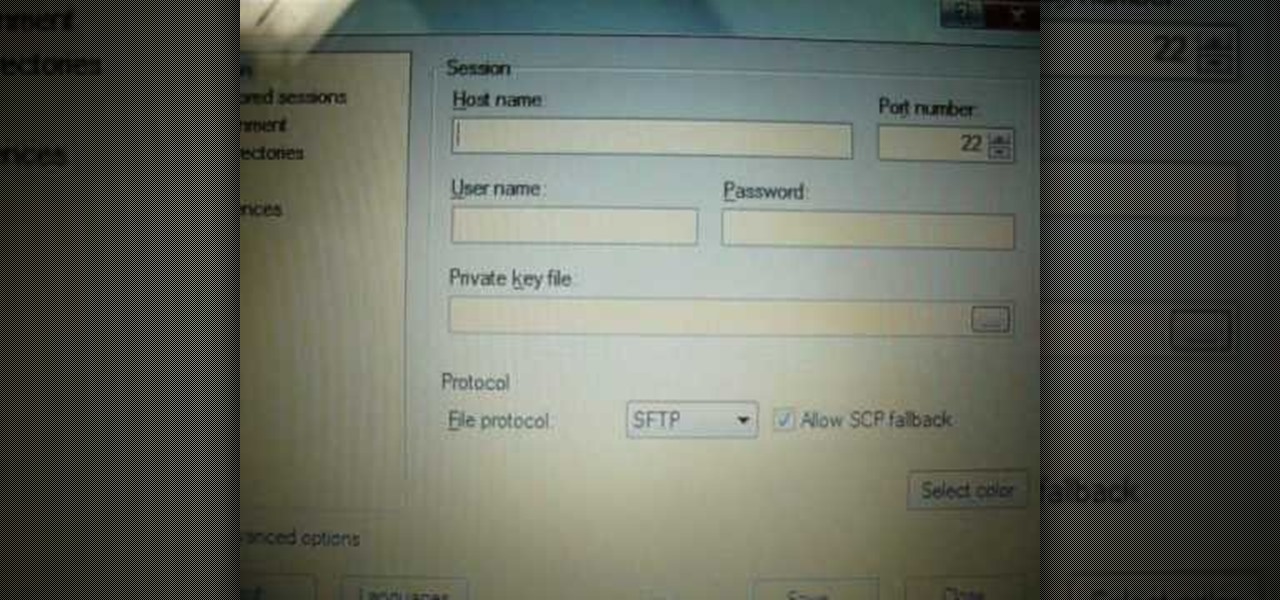
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

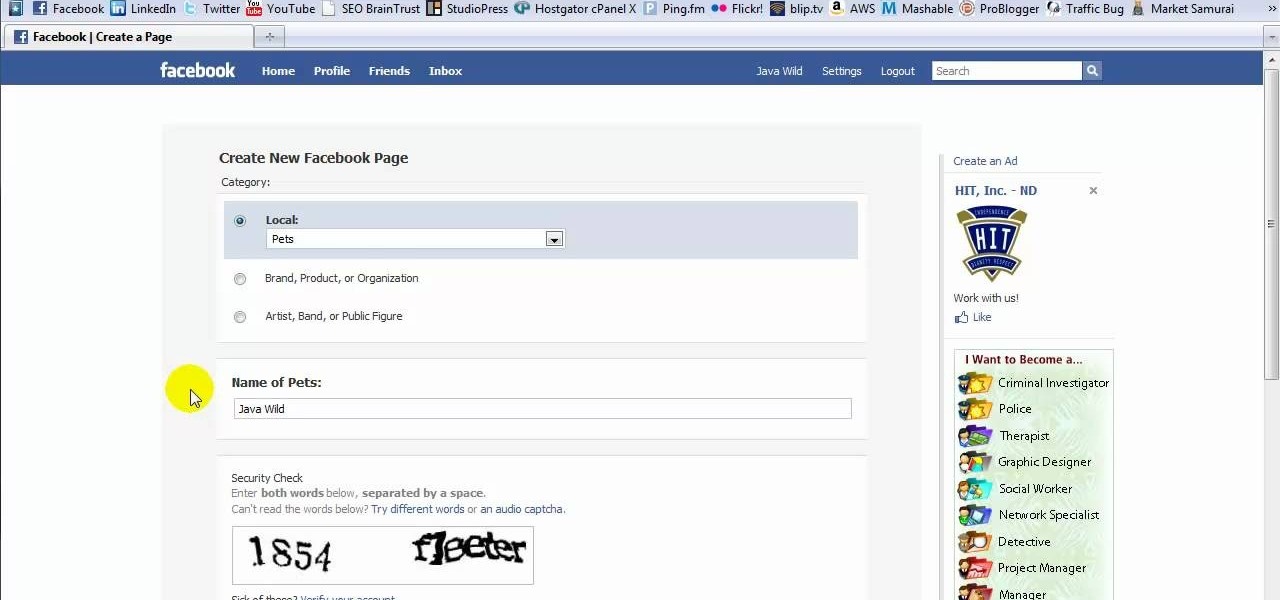
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

This video is a step by step guide for creating exposed teeth makeup . This is loosely based on the Harvey Dent character from Batman: the Dark Knight.

Reduce your chances of becoming the seatmate everyone hates by learning how to head off a screaming jag.

Research shows that color can have a powerful effect on our emotions. Start harnessing that power today. Watch this video to learn how to improve your life with chromotherapy.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

Archie Leach. It just doesn't have the same ring as Cary Grant, does it? Marriage, divorce, or just dislike of the name your parents gave you – all are reasons to follow these steps toward a new name.

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

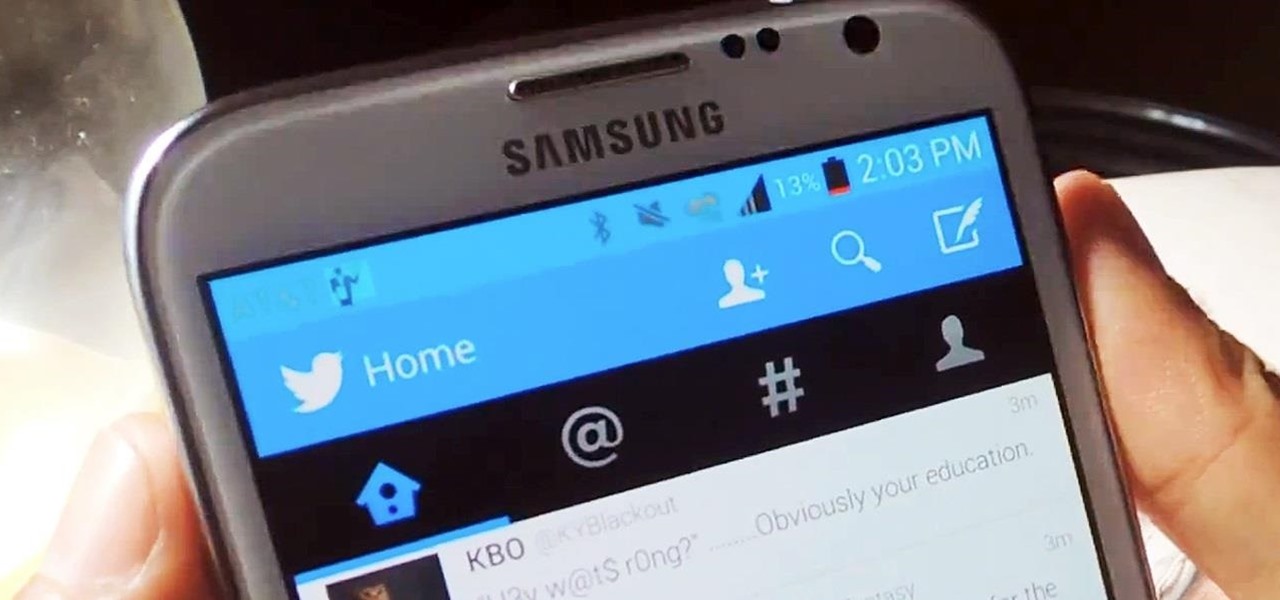
Android has a new security feature that every Android smartphone user needs to start using — even you. It won't change how you use your phone, but it will make life harder for nearby thieves.

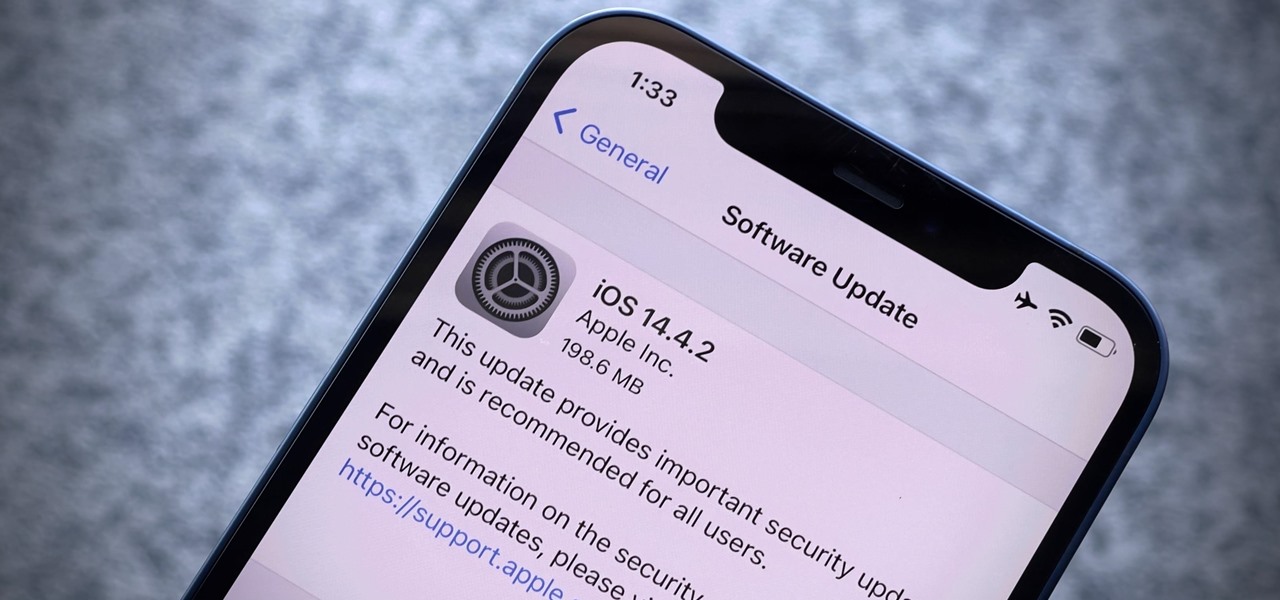
Attackers may have actively exploited a new WebKit vulnerability on iOS and iPadOS, but Apple just released a patch to secure your iPhone and iPad from attacks.

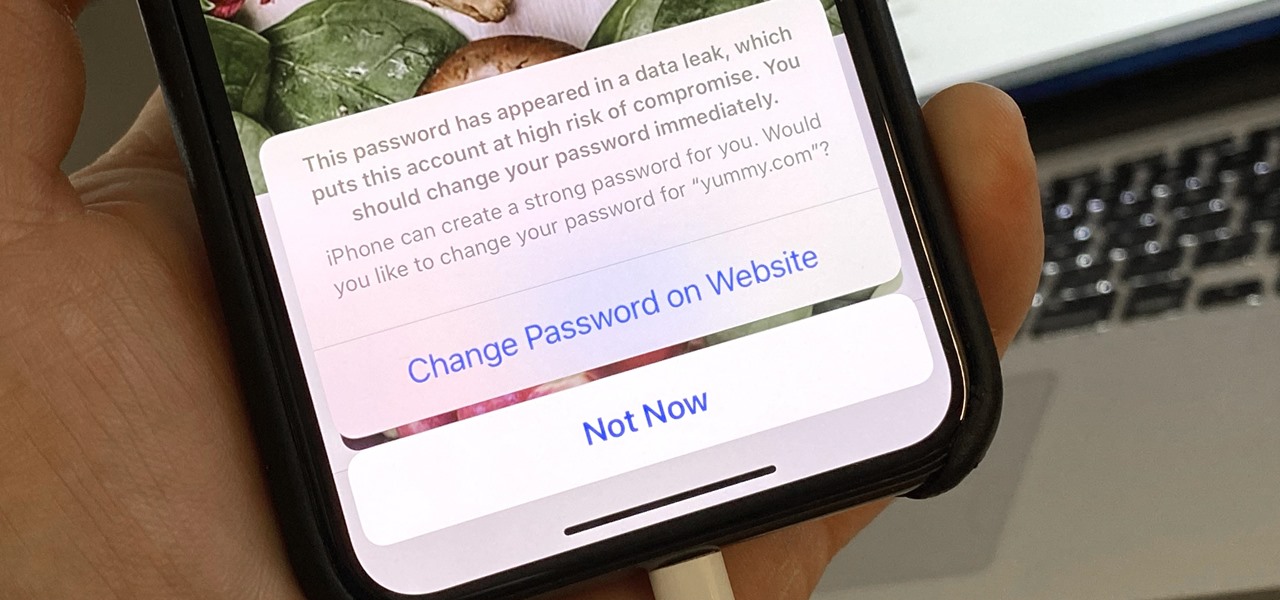
Everything lives online these days, so it's not uncommon to have hundreds of credentials for different accounts on apps and websites. That's why a password manager is a must, and your iPhone has one built right into iOS that you can start using today. In iOS 14, it's gotten even more useful since it can now monitor your passwords regularly to see if any match leaked password lists online.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.