This meal is simple enough for every day and special enough for guests. Follow along and learn how to make a teriyaki pork tenderloin. This cooking how-to video is part of a Healthy Appetite with Ellie Krieger show hosted by Ellie Krieger. Cooking healthy food can be quick, easy, but most of all, delicious. Nutritionist and author Ellie Krieger has created fast and simple healthy recipes for the real world. She'll show you how simple it can be to stay on the healthy track no matter how busy a...

This sun dried tomato pesto-stuffed pork roast is ready for the oven in ten minutes. Follow along and learn how to make this pork recipe. This cooking how-to video is part of Quick Fix Meals with Robin Miller show hosted by Robin Miller. Busy people everywhere face the same dilemma, how to get healthy weeknight dinners on the table when you've only got minutes to spare. Cookbook author, nutritionist and food journalist Robin Miller guides you through the landmines of getting food on the table...

For a health conscious change of pace, try a tuna burger! They are so easy to make, all you have to get is some canned tuna, which you probably already have in our pantry. This cooking how-to video is part of Quick Fix Meals with Robin Miller show hosted by Robin Miller.

Bake an incredibly simple side dish of honey roasted sweet potatoes, Follow along to learn how easy it is to incorporate healthy vegetables into your diet. This cooking how-to video is part of Healthy Appetite with Ellie Krieger show hosted by Ellie Krieger. Cooking healthy food can be quick, easy, but most of all, delicious. Nutritionist and author Ellie Krieger has created fast and simple healthy recipes for the real world. She'll show you how simple it can be to stay on the healthy track n...

Is your kid's desk all cluttered? Help them stay organize by making an easy desk desk set for your child's school supplies. Watch this how to video tutorial as our host shows you how to make a pencil holder using a can, paper and some glue. Have your children help you with this fun activity.

The "Cotton Eye Joe" is one of the most famous American folk dances. In this tutorial you will learn how to do this country western style line dance, the "Cotton Eye Joe." The version of "Cotton Eye Joe" in this video is by the Rednex.

Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

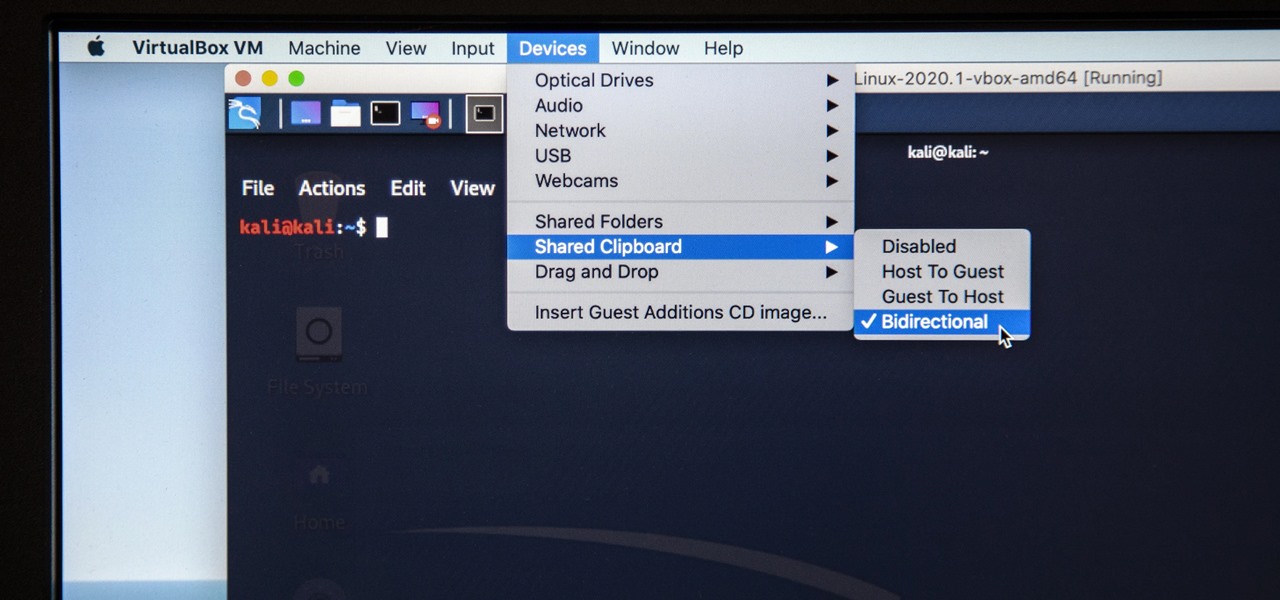
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

With all this time spent stuck at home because of the COVID-19 pandemic, HQ Trivia would be a prime way to beat the boredom. Unfortunately, HQ went belly up in February, just before everyone had stay-at-home orders. While HQ has teased a potential comeback, there are other trivia games out there that are live right now. One of those brings the spirit of HQ Trivia back to our phones.

It's OK to want an extended break when you're working or learning from home. Maybe you want to play a video game, spend more time with your family, hang out with your dog, or FaceTime with friends. But how can you do that when you're supposed to be in a Zoom video conference or class? Thanks to one Zoom feature on your iPhone, it may be easier than you think.

Facebook has announced the cancelation of its annual F8 developer conference, citing concerns around the developing coronavirus health crisis.

Ratings and reviews apply everywhere, from a restaurant you want to try to a new camera you're thinking of buying and games you might want to play. Podcasts are no different. Reading reviews of shows can help determine which are worth listening to, and your opinion is valuable to other people too. In Apple Podcasts, there are a few different ways to read, rate, and review shows.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

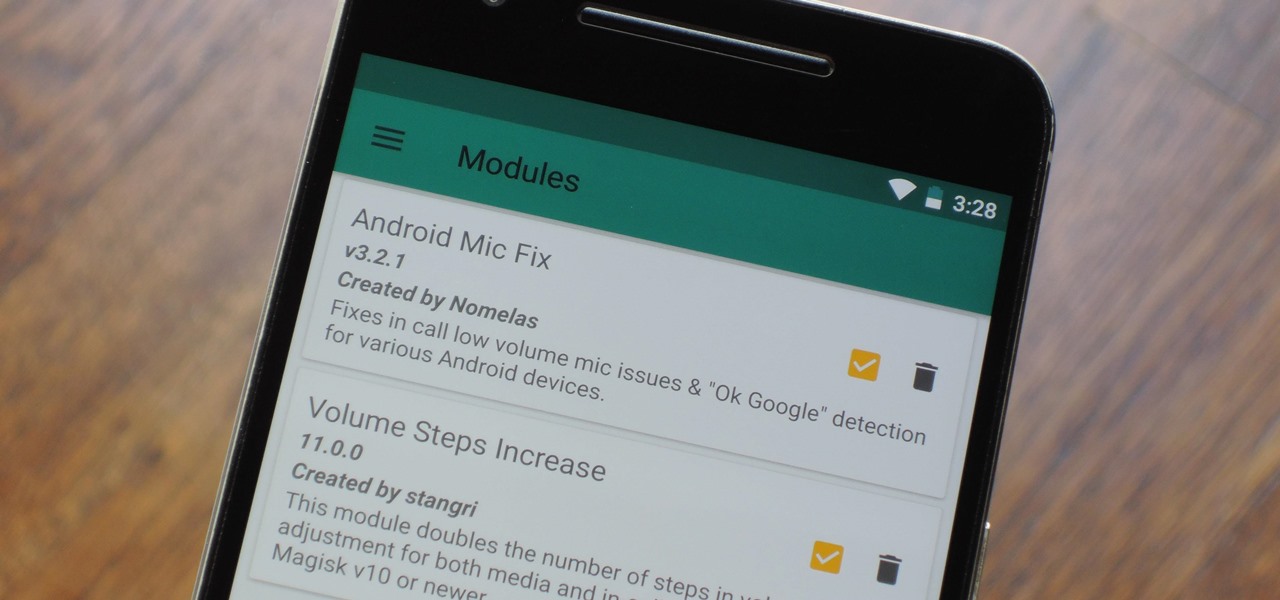
Much like Xposed or Cydia, Magisk has an official repository that makes it easy to download root-level tweaks. These tweaks are called modules, and they can do anything from changing your emojis to installing high-level audio mods. But as it stands, a large number of Magisk modules are not hosted on the official repo just yet, so there are two primary ways to install them.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry.

A 6,000-year-old forest inhabitant awakens to find life in the forest around it in crisis. Plants, trees, animals, and birds are moving north to escape increasingly heated air, even as mass extinctions take place around the world. The inhabitant stirs and remembers it has lived this before and knows what to do.

At Facebook's first Communities Summit, admins from top Facebook groups assembled to discuss tools to better manage and optimize their members. Here, Facebook CEO Mark Zuckerberg announced that these changes fuel the company's shifting focus from connecting the world to uniting it.

Stratford may soon become Canada's answer to Silicon Valley as the driverless car industry arrives. Potentially changing the character of the Ontario town known for hosting the Stratford Festival, a celebration of all things Shakespearean and stage-related.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Avian flu is making the news again with new human cases in China reported in January. What does "avian flu" mean to you—and how dangerous is it?

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

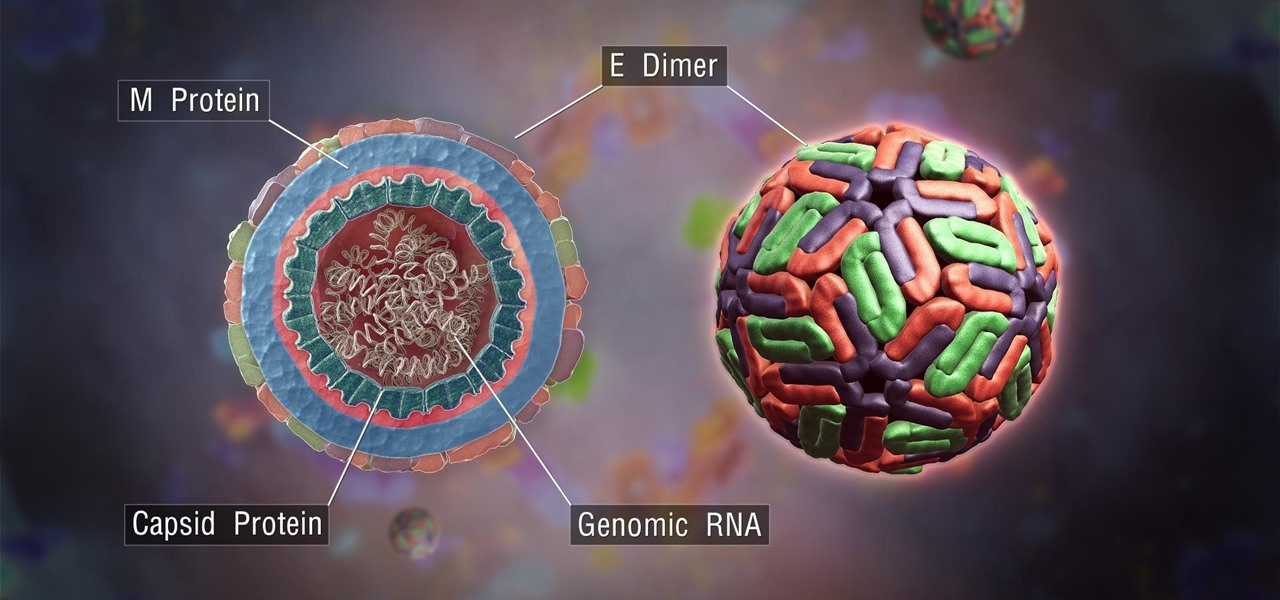
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

This morning, Google opened a pop-up showroom where anybody can visit to get a hands-on look at the new Made by Google hardware lineup. At 10 am the line at 96 Spring st, in the SoHo neighborhood of New York City, was growing but still manageable. As we waited to be ushered in, Google representatives came by to offer us coffee drinks prepared by a pair of baristas in the Peddler Coffee cart parked on the curb. "Now that's latte art," said the guy in line next to me when he saw that the foam-t...

So you're finally ready to head out on that big trip you've been planning for months, huh? It's an exciting time, but there are plenty of things you'll need to prepare before you head out. For instance, it's hard to imagine life without a smartphone these days, and with useful traveling apps like Google Translate and maps, you'll almost have to make sure that you have a working smartphone when you arrive at your destination.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.