You know YouTube is able to host high-defintion video content online now, right? Well, how do you watch it, or make it, or embed it? Well, this video tutorial will show you how to upload, embed and watch 720p HD video on YouTube. This YouTube hack will let you watch and embed videos in true 1280x720 high definition.
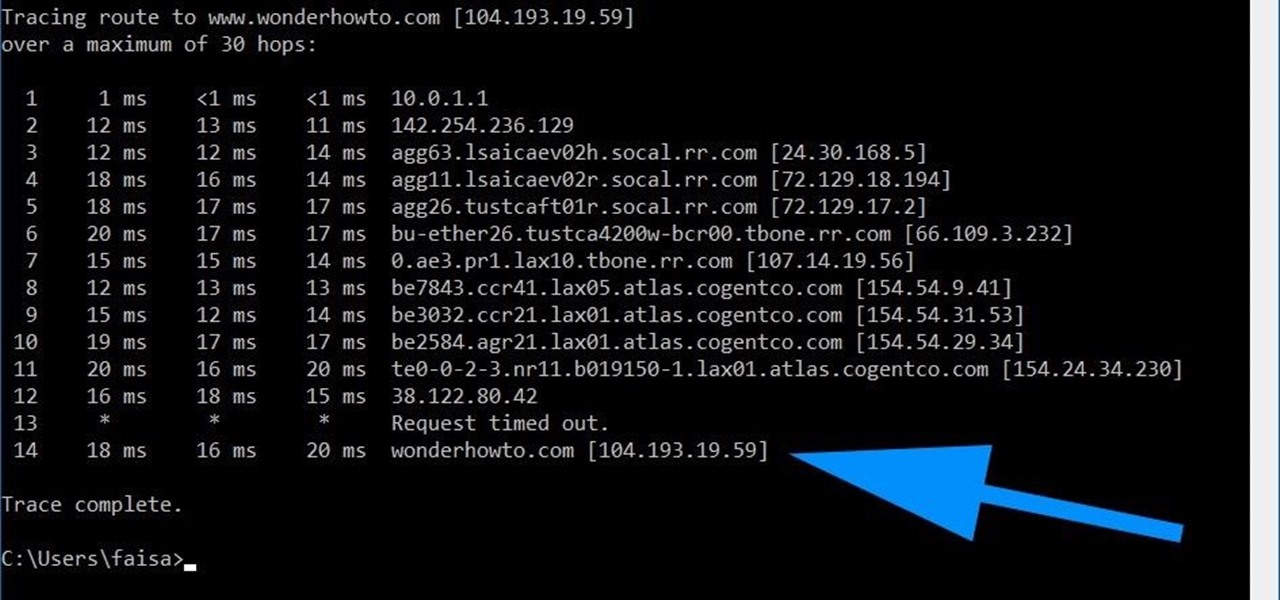
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.
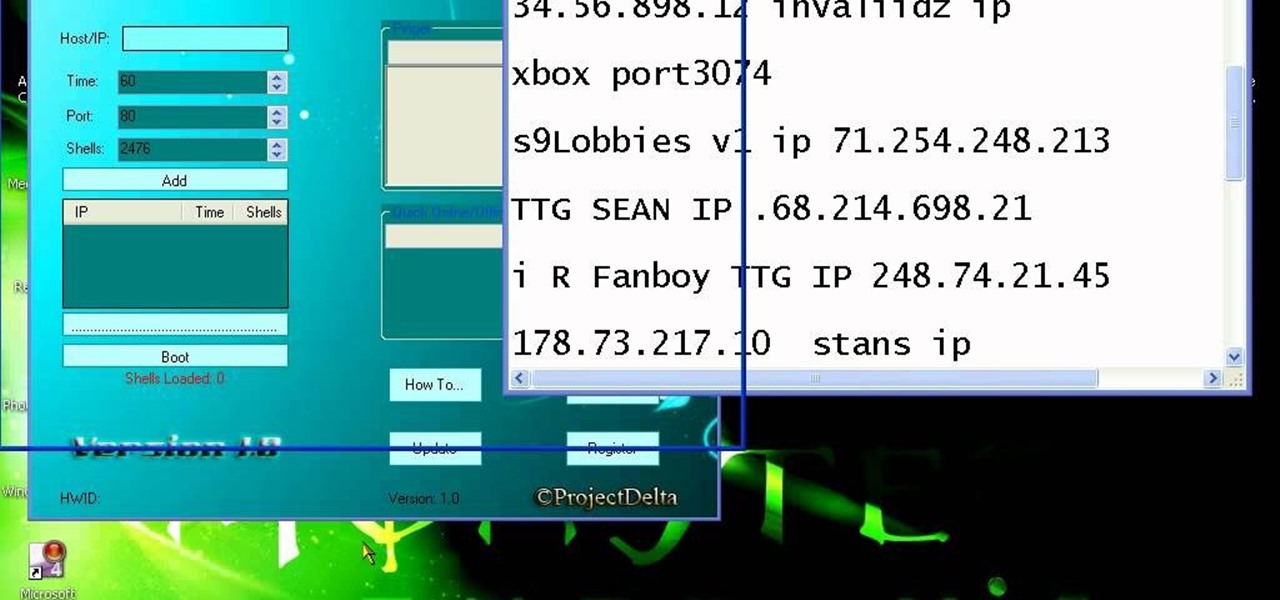
Using Cain & Able and a host booter, you can kick someone off of Xbox Live. If you are annoyed with another player, this is how you take their ball and throw it into the scary old man neighbor's yard.

This video shows how to check your hosts file for spyware. This is a valuable tool, if your computer has spyware it can greatly affect the performance of your computer.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

It's OK to want an extended break when you're working or learning from home. Maybe you want to play a video game, spend more time with your family, hang out with your dog, or FaceTime with friends. But how can you do that when you're supposed to be in a Zoom video conference or class? Thanks to one Zoom feature on your iPhone, it may be easier than you think.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

A 6,000-year-old forest inhabitant awakens to find life in the forest around it in crisis. Plants, trees, animals, and birds are moving north to escape increasingly heated air, even as mass extinctions take place around the world. The inhabitant stirs and remembers it has lived this before and knows what to do.

For regions that experienced a boom in mouse populations last year, scientists say 2017 could see a surge in cases of Lyme disease.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Avian flu is making the news again with new human cases in China reported in January. What does "avian flu" mean to you—and how dangerous is it?

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

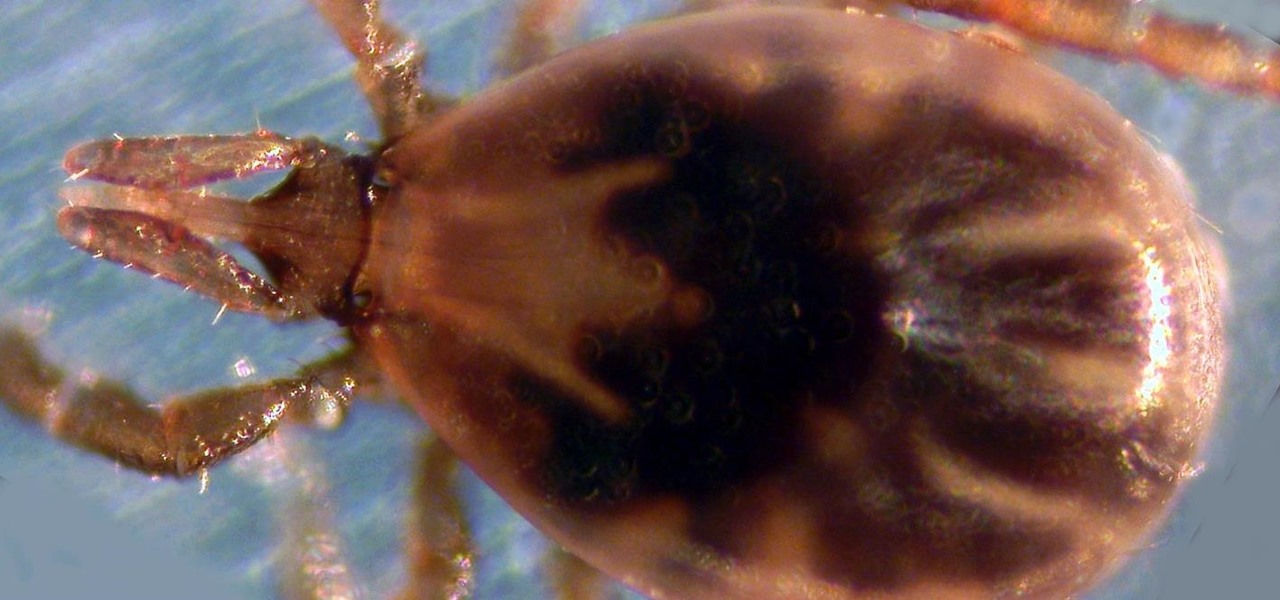
Transmitted by ticks, Lyme disease is a serious infection that is probably headed your way. A recent study confirms the pathogen that causes Lyme disease is now established in nine national parks in the East, including Acadia and Shenandoah National Parks.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

In this detailed three part tutorial, learn exactly how to draw a scene from the cartoon "Three Delivery", using Flash. This expert how-to is hosted by Loogaroo, the animators responsible for this popular series. The series was created over a period of two years with more than 100 artists because every second of this kung-fu action was hand drawn in Flash. Check out this clip, and you too can share in this labor of love.

Fourth of July is near, which means we'll soon be seeing an influx of red, white, and blue flags, banner, and of course patriotic sweets for those who indulge in the foodie side of the holiday.

With the current oil spill in the Gulf, the victims suffering the most are birds and fish. All of these gorgeous animals that have been living in this area forever are suddenly covered in BP oil and fighting for their lives.

The JET Programme is a teaching exchange program between the USA and Japan. If you are accepted into this program, you will get the exciting opportunity to travel, teach and live in Japan. This is a dream come true for a lot of people, and applying to this program is similar to applying for college or a job.

Patrick Norton and Veronica Belmont from Tekzilla will show you how to dual boot Windows 7 and download videos from YouTube. The hosts show viewers how to dual boot Windows XP Pro32 bit and Windows 7 RC 1 64 bit. In the first step as always you will want to back up your hard drive and at the very least they recommend to back up your most important files. In the case that something goes terribly wrong you can use a free program called EASEUS to make a complete image of your whole drive, this a...

This video from Southwest Yard and Garden tells viewers why it is important to wash your hands after gardening, and when and how to do so. It also emphasizes the importance of cleaning cutting boards. You should wash your hands before eating, after using the bathroom, and while you are handling food. While handling food, if you handle any meat, you must wash your hands before touching anything else. You should wash your hands for twenty seconds, with soap and water. To demonstrate the importa...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

"Fast food" can be healthy and gourmet! Foodie Gwyneth Paltrow hosts this quick cooking show to take you through the steps of a roast chicken and potato meal. You'll need a chicken, a couple lemons, garlic, rosemary sage, thyme, pepper, olive oil, and fingerling potatoes. You don't need to be a fan of Gwyneth Paltrow's to enjoy the tasty meal prepared in this mini cooking show from her website GOOP.

DreamWelder Productions presents this video tutorial from their show Info Tech, hosted by Jay A. Kelley. They take an exciting new look into new equipment for the film and television industry, showing you the best gear for your movies and shows.

Check out this strength trick from Revision3, Brian Brushwood and Scam School. We're back with another dirty trick, designed to teach you how to FAKE your way into (almost) duplicating the feats of the world's strongest men.

This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead!

Tune into this hot dog how-to video and watch host Scott Herbert get frank about his passion for Chicago-style hot dogs. Also, learn the secret to a frosty root beer float that's especially sweet when made with Whole Foods Market's 365 Everyday Value root beer crafted with cane sugar, not high fructose corn syrup.

A fairy princess party isn't the same without fairy wands! Eschew traditional conceptions of wands and create wands that are both girly and good to eat by watching this tutorial on how to create fruit wands!

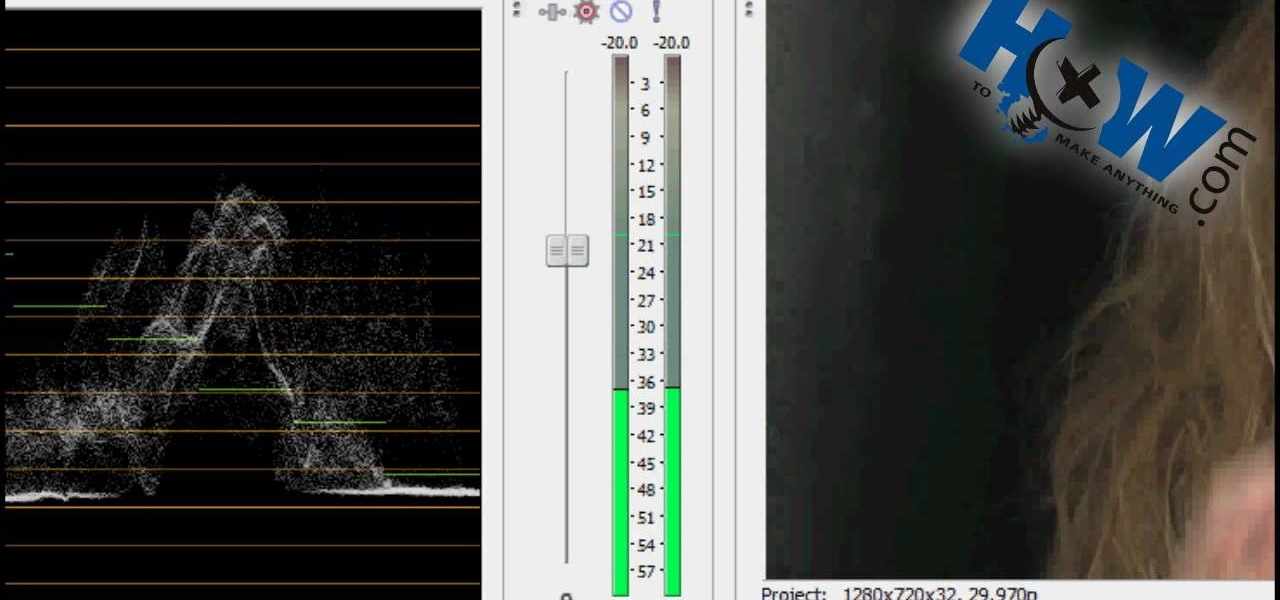
First of all put your video on the timeline where you have a wave form representing your audio track control tools. If you right click on the audio tracks then you get a lot of options available to you. Click on the 'switches' then 'normalize' and this shall choose the highest peak and calibrate the whole audio to that peak. So if your audio is little low or it is too noisy then you can normalize it. Now click on 'channels' and then you have the option of picking left or the right channel. No...