In this six-part drawing tutorial hosted by artist Wayne Tully, learn how to draw a firey flaming skull. Start from scratch in part one with the outline of the skull, then move onto the skull's features including the eyes and jaw in part two. Part three takes you through shading under the skull's eyes and around the skull's cheekbones to add dimension. In part four, learn how to strengthen pencil lines & add shading to define the cheekbones. Once the skull is done, part five goes over how to ...

Add a party favor to your next hosted New Year's Eve bash. Ring in the New Year wearing personalized party glasses! It's a fun project for kids and adults.

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Why have a plain old barbecue when you can host an Oktoberfest? Make it authentic with these tips. You Will Need

Check out this Scam School video on leanring the ultimate strength tricks. Bend frying pans and horseshoes with your bare hands! Watch Brian make you think he can use his bare hands to bend a horseshoe and to roll a frying pan!

Secret Ingredient host Mark Law and Denver chef Jean Philippe Failyau of Osteria Marco take the mint out of the mojito and add it to a fresh summertime salad of cherry tomatoes, fennel, red onion, cucumber and mint, served over seared halibut. Follow along in this cooking how-to video as Whole Food's Market shows you how to prepare this delicious seafood dish. The tomato, fennel, cucumber and mint add a refreshing taste to the seared halibut.

Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

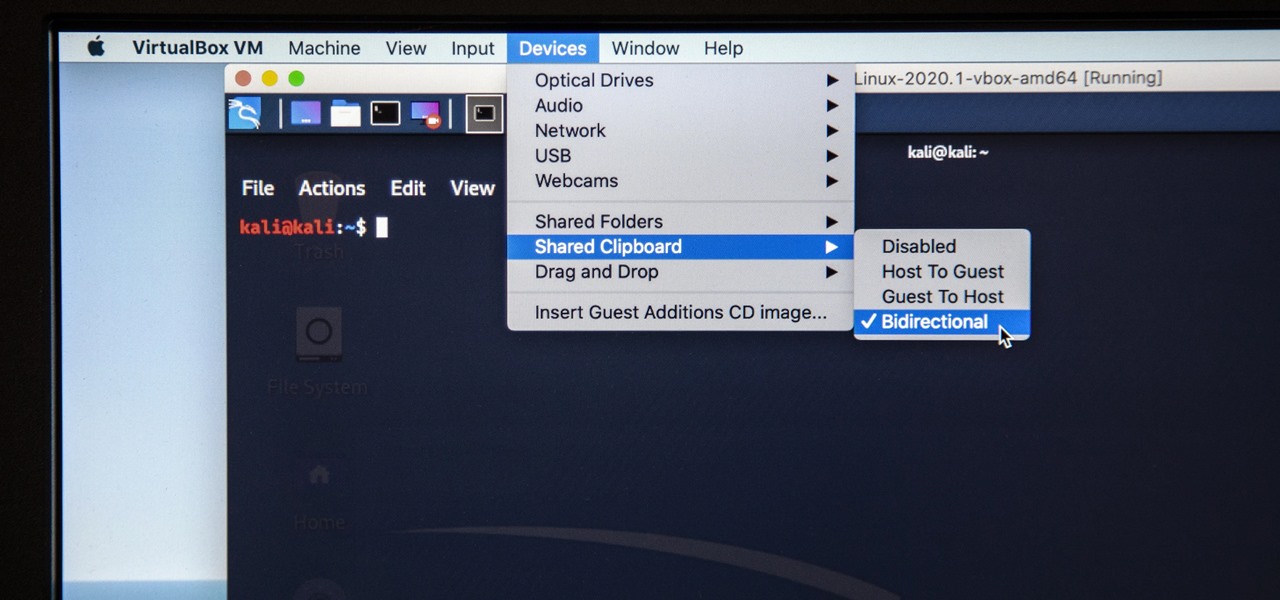
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

With all this time spent stuck at home because of the COVID-19 pandemic, HQ Trivia would be a prime way to beat the boredom. Unfortunately, HQ went belly up in February, just before everyone had stay-at-home orders. While HQ has teased a potential comeback, there are other trivia games out there that are live right now. One of those brings the spirit of HQ Trivia back to our phones.

Facebook has announced the cancelation of its annual F8 developer conference, citing concerns around the developing coronavirus health crisis.

Ratings and reviews apply everywhere, from a restaurant you want to try to a new camera you're thinking of buying and games you might want to play. Podcasts are no different. Reading reviews of shows can help determine which are worth listening to, and your opinion is valuable to other people too. In Apple Podcasts, there are a few different ways to read, rate, and review shows.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

HBO's Westworld has touched down on iOS as a mobile game, giving players the chance to manage their very own futuristic theme park set in the wild west. Unfortunately, the game is currently only available in select countries as a soft launch until its fully developed. But if you'd like to try out this game right now, there's a simple workaround to get Westworld on your iPhone.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

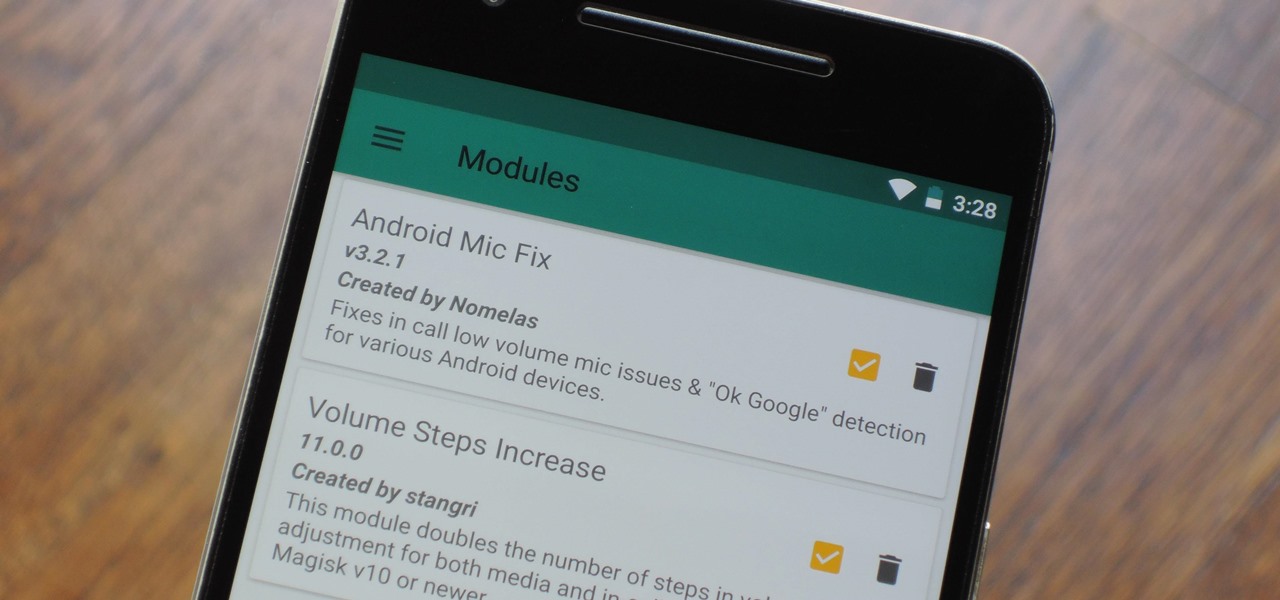
Much like Xposed or Cydia, Magisk has an official repository that makes it easy to download root-level tweaks. These tweaks are called modules, and they can do anything from changing your emojis to installing high-level audio mods. But as it stands, a large number of Magisk modules are not hosted on the official repo just yet, so there are two primary ways to install them.

The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry.

At Facebook's first Communities Summit, admins from top Facebook groups assembled to discuss tools to better manage and optimize their members. Here, Facebook CEO Mark Zuckerberg announced that these changes fuel the company's shifting focus from connecting the world to uniting it.

Stratford may soon become Canada's answer to Silicon Valley as the driverless car industry arrives. Potentially changing the character of the Ontario town known for hosting the Stratford Festival, a celebration of all things Shakespearean and stage-related.

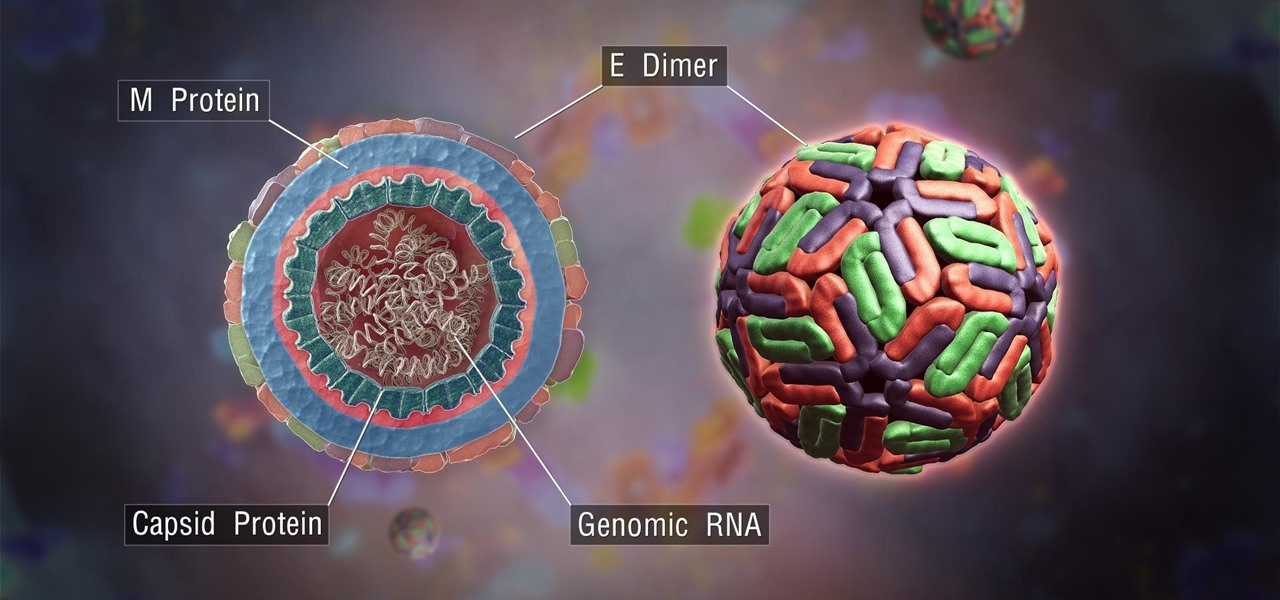
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

This morning, Google opened a pop-up showroom where anybody can visit to get a hands-on look at the new Made by Google hardware lineup. At 10 am the line at 96 Spring st, in the SoHo neighborhood of New York City, was growing but still manageable. As we waited to be ushered in, Google representatives came by to offer us coffee drinks prepared by a pair of baristas in the Peddler Coffee cart parked on the curb. "Now that's latte art," said the guy in line next to me when he saw that the foam-t...

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

Linux may not be the most popular consumer operating system out there, but what it lacks in consumer app variety, it definitely makes up for in flexibility and security. And if you've ever tinkered with a Linux distro, you know how easy they are to install—most of the time, I skip standard installation and boot directly from a CD.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.