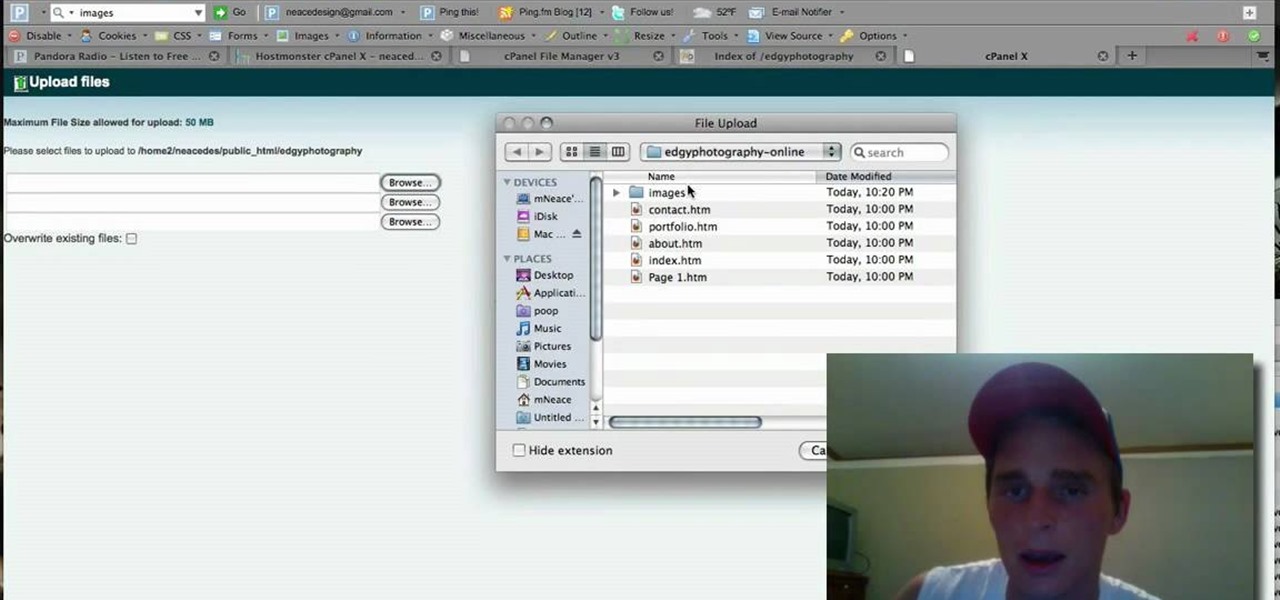
NeaceDesign explains an easy method of setting up a website online without having to use FTP programs. He begins with correcting an error made previously in which the main web page was name 'Home'. This should be renamed to 'Index' and the file re-exported. NeaceDesign suggests going with well-known web-page hosting services such as 'hostmonster'. The first step is to go to File Manager and upload the image files to a new folder. This is done by sending all the files to a zip folder and then ...
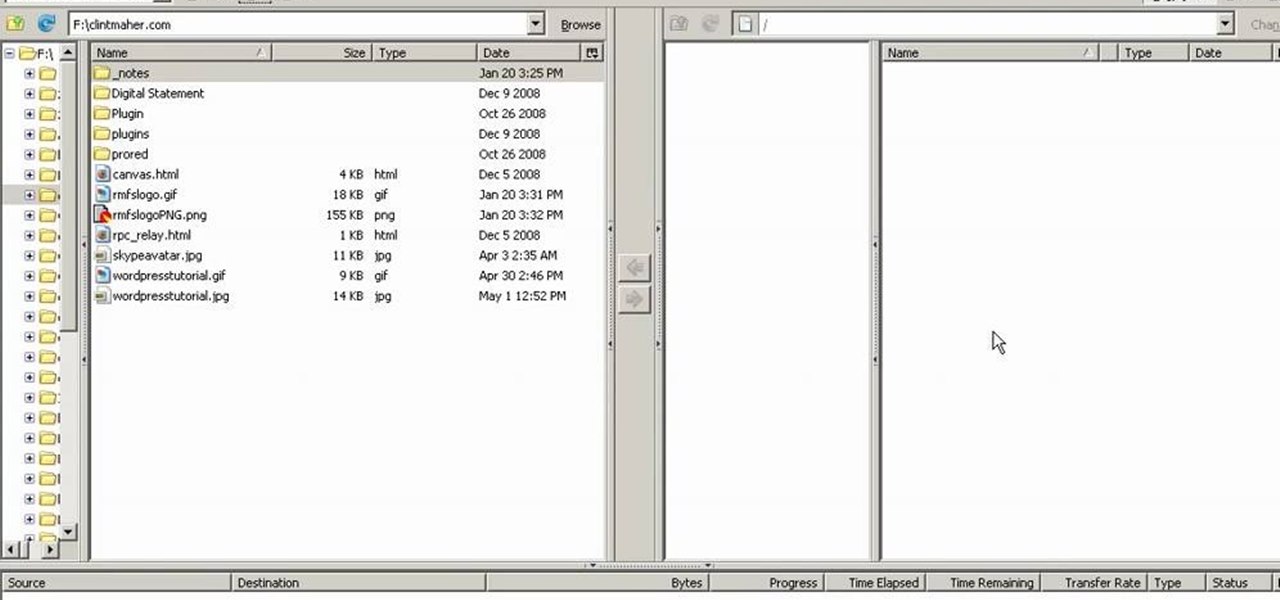
In this Computers & Programming video tutorial you will learn how to update websites from Firefox with the FireFTP add-on. Go to the Firefox add-ons page, search for FireFTP, add it to Firefox and install it. Restart Firefox to activate the add-on. Go to tools and click on FireFTP and that will open up a new tab with the FTP client. To configure the FTP to your account, create a new account by giving it a name. The host will be your domainname.com and use the login and the password for the ho...

In this how-to video, you will learn how to light your web show. This is important as it will make your web show look more professional. Proper lighting allows you to see your face, eyes, and the colors of your shirt. If there is not enough light, you cannot see yourself as well. You will also look dark and grainy. Too much light will cause your face to look too hot. Backlit lighting will cause your face to be too dark because the light is in the background. This is why background lighting is...

Writer of 'How to Sew a Button: And Other Nifty Things Your Grandmother Knew', Erin Bried shows us how to make a Vodka Gimlet for those of us hosting guests. Don't struggle to remember how to make it, or exactly how much goes into the recipe for the drink, the clearly laid out instructions with accompanied video makes making this delicious drink a breeze. From the chilling of the water, to preparing the shaker, to each component ingredient such as vodka and lime juice, there will be no confus...

Hosting a Halloween party and looking for some inspiration? ThreadBanger's Decor It Yourself is here to help with a few spooky ideas that can be thrown together at home and for cheap! Projects include eerie terrariums, adding red to the eyes in your portrait wall art, and bloody-ing up your shower curtain like a scene out of Alfred Hitchcock's Psycho.
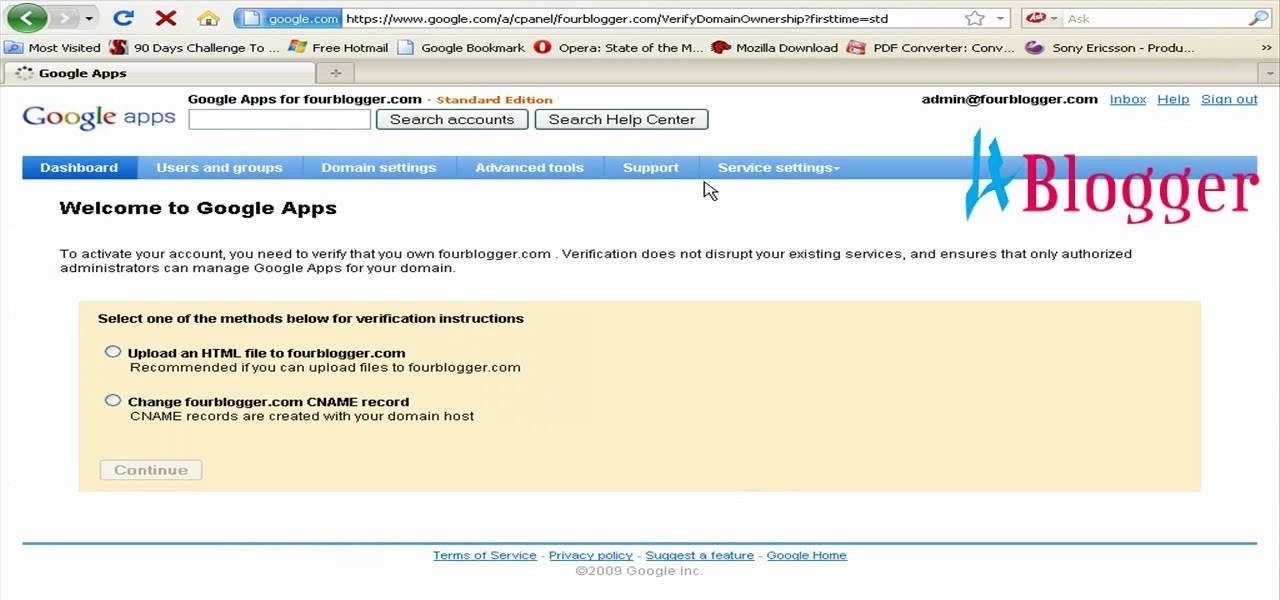
You can create the Google apps email like Gmail for your domain. So to do this first you need to go to the google.com/a and click on the standard in "other Google apps editions". Now click on "get started". Now select "administrator: I own..." and enter your domain name and click get started. Now on next page create your account by filling all the fields and click continue and now fill the info of your administrator account and click I accept button. Now next step is for the verification of y...

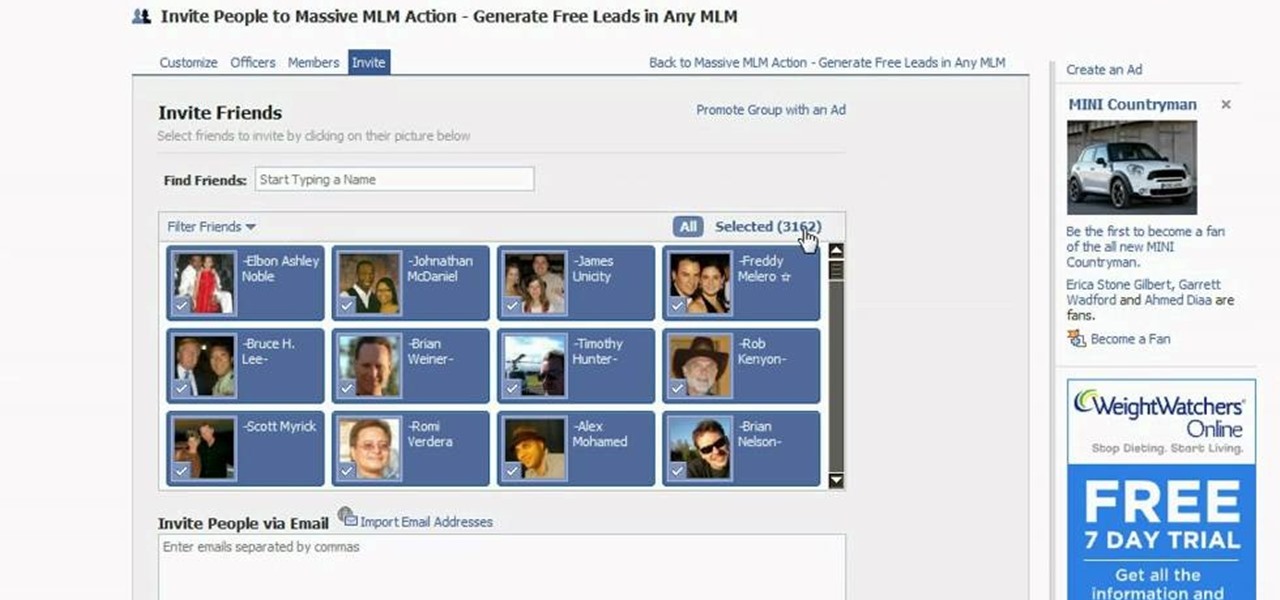
Do you have tons of friends on Facebook? Would you like to invite everyone you know to an event you are hosting or to try a product you are marketing? Normally to do this, you would need to select friends one at a time, reach Facebook's max invitee limit and then go in and do it again, and keep doing so until you get through your whole list. But what if you have hundreds of friends? This could take forever! Check out this tutorial and learn how to bypass Facebook's regulations and invite mass...

Is your BFF getting married? Looks like you have a bridal shower to plan! Organize a bridal bash that people will actually want to attend using these innovative ideas.

Earlier today, a meteorite flew over the Chelyabinsk region of Russia, triggering a shock wave that injured hundreds of people and caused damage to buildings and vehicles in the area. Witnesses describe seeing a bright ball of light streak through the sky followed by a loud boom as the 10-ton meteorite entered the Earth's atmosphere and exploded.

If you're a Firefox user and frequently use free image hosting services à la ImageShack & Photobucket, then you've no reason not to check out the ImageBot Firefox extension, which does quite a lot to streamline the picture uploading process.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

This holiday season, give yourself a gift that will keep on giving: a new web development skill. Whether it's to secure lucrative freelance work in the new year, bolster your résumé, or have fun with some frankly outrageous discounts on online course bundles right now (up to 99% off), there's nothing better you can do with your free time. Your future (pro coder) self will thank you.

You don't have to stress out about hosting the perfect family Thanksgiving dinner! You can make a fun and engaging centerpiece just from things you can find around your house, and this video shows you how to make a fun turkey centerpiece, or flowers on a gourd.

The runaway chainsaw family of glitches for Gears of War 2 enable the player to chainsaw a target to death instantly, without having to wait through the tedious process of watching their victim being sawed in half vertically. This video will teach you how to use the glitch in multiplayer, whether hosting or not. Like most of the game's glitches, this isn't all that useful in the game, but if you've finished all the other content, it's time to turn to the glitches!

Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present.

If you need to share something online but don't want your personal information attached to the file, use an anonymous file hosting site. By uploading files anonymously, you keep your IP address safe and won't need to create any kind of account that could provide further logging. You can do this in a web browser, but it's much easier to do using a shortcut on your iPhone.

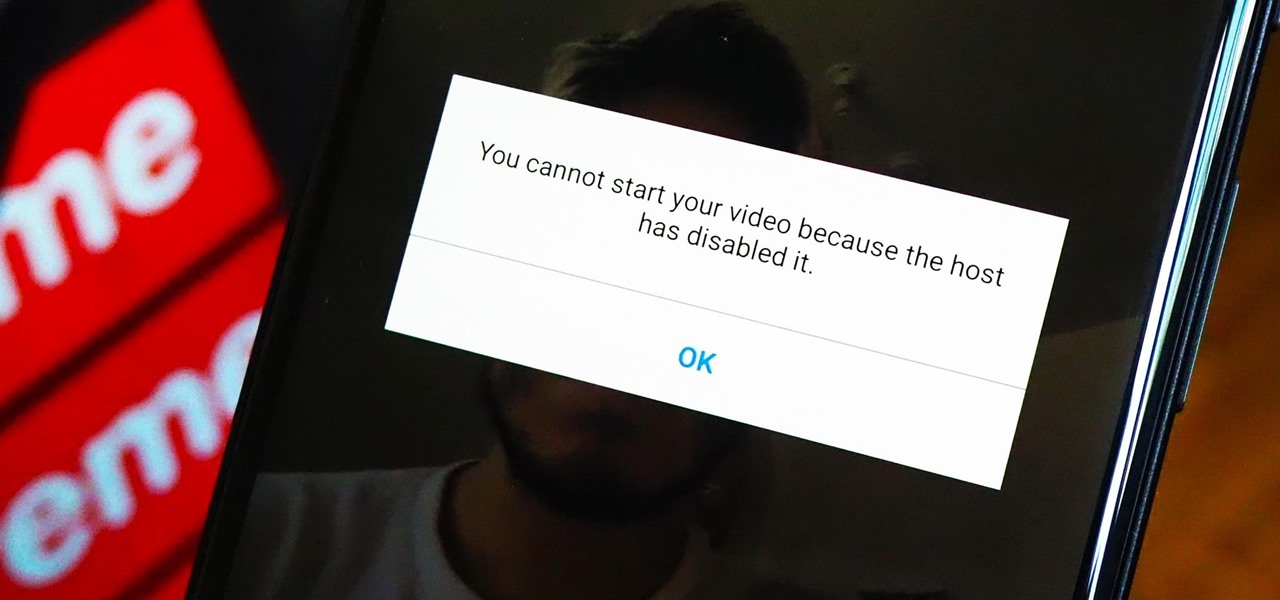
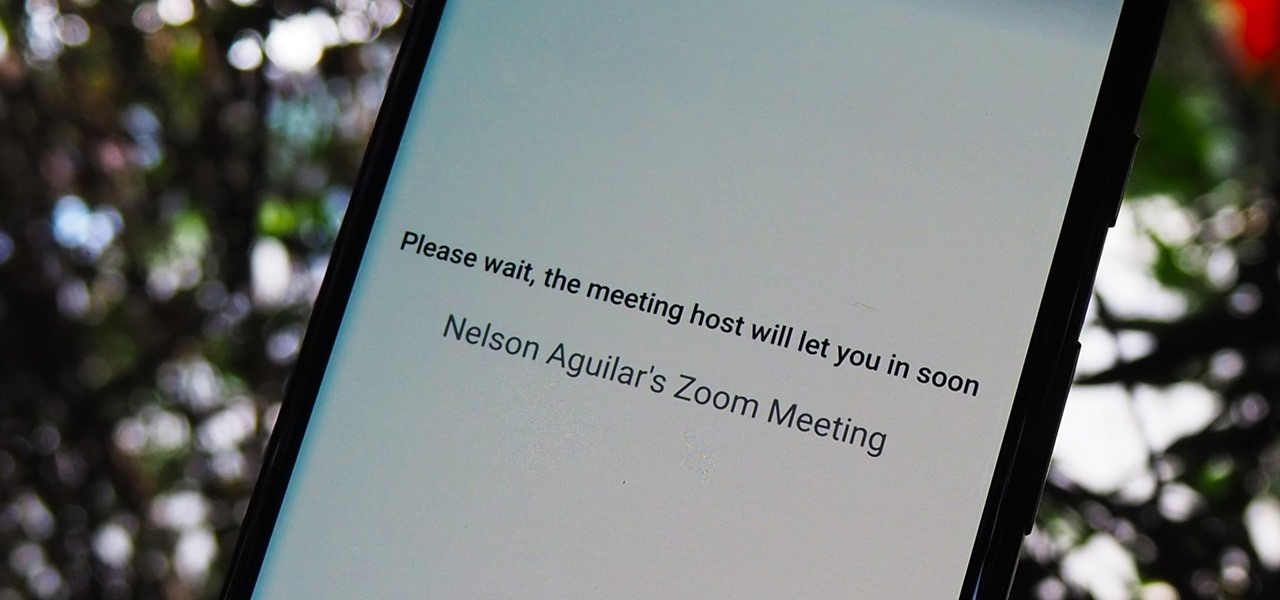
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

In this Hosting & Entertaining video tutorial you will learn how to fold a cloth napkin into a flower. First fold the napkin in half. Then lift one corner and fold it back up to the center fold line and do the same for the other corner also. Now fold the center point back up to the center fold line. Flip the napkin over and repeat these steps. Then open up the center fold and fold the protruding triangles back up to the center point of the napkin. You now have a square folded napkin. . Now fo...

This Hosting & Entertaining video tutorial will show you how to make a bow for any occasion. LeAnn Dolan, owner of Ecru Modern Stationer, shares her secret of creating a wonderful gift pack topper. For this you will need two pieces of ribbon of same color and of course the gift box. First wrap the gift box with one piece of ribbon around all four sides, tie a knot at the center of the box. Then with the other piece of ribbon, make plenty of loops wrapping them at the center till the whole len...

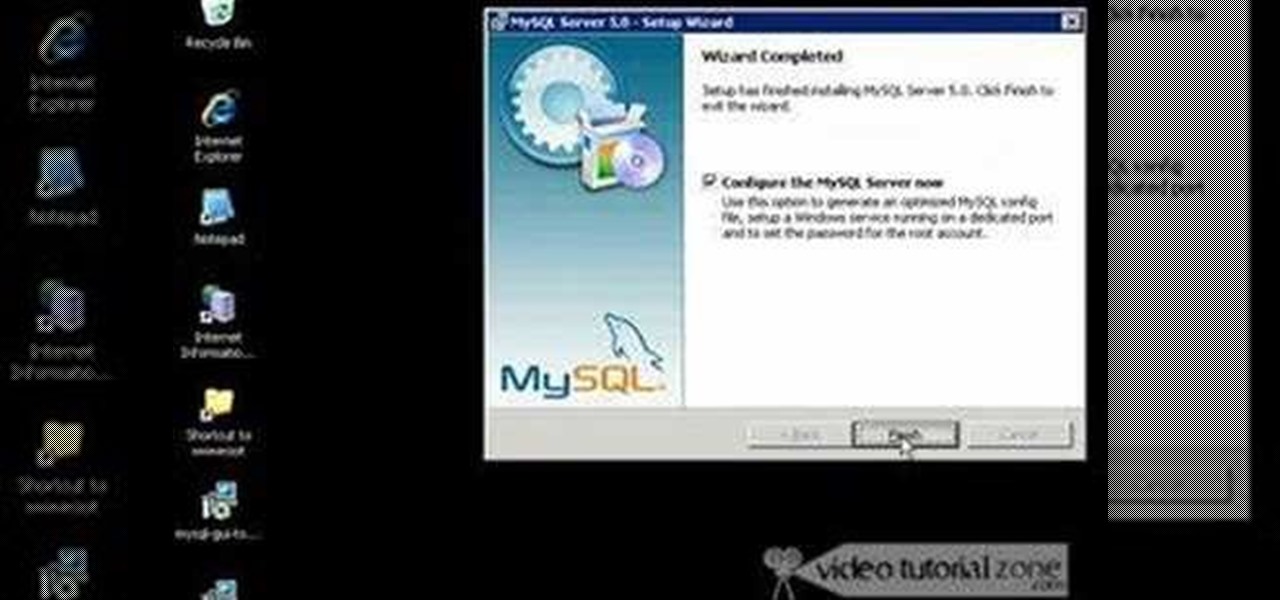
MySQL is a multithreaded, multi-user SQL database management system which has over 10 million installations. It runs as a server providing multi-user access to databases. It is by far the most popular and common database used in web applications throughout the world, and almost all hosting companies provide it free of charge to their users. MySQL AB makes MySQL Server available as free software under the GNU General Public License (GPL). For this tutorial we are going to download and install ...

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

This morning, Google opened a pop-up showroom where anybody can visit to get a hands-on look at the new Made by Google hardware lineup. At 10 am the line at 96 Spring st, in the SoHo neighborhood of New York City, was growing but still manageable. As we waited to be ushered in, Google representatives came by to offer us coffee drinks prepared by a pair of baristas in the Peddler Coffee cart parked on the curb. "Now that's latte art," said the guy in line next to me when he saw that the foam-t...

Believe it or not, the 2012 Presidential Election is (finally) almost over. While most of us are breathing a collective sigh of relief (no more political ads!), it still seems like it hasn't been that long since the last election results were announced. This time, though, one of the biggest differences is how people will watch. Since traditional cable is on its way out, and mobile devices are getting more popular every day, a lot of people will be watching this year's election results online ...

This video discusses the basic steps necessary to start an online business. The first thing you need is a name for your business. Keep it simple, easy to spell and remember. Once you have your name, register it with the government. Next, find a good hosting company for your website. He recommends Godaddy.com. Also a good web designer is a necessity. They will meet with you to discuss your ideas, and your website should be ready in about a week.

The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

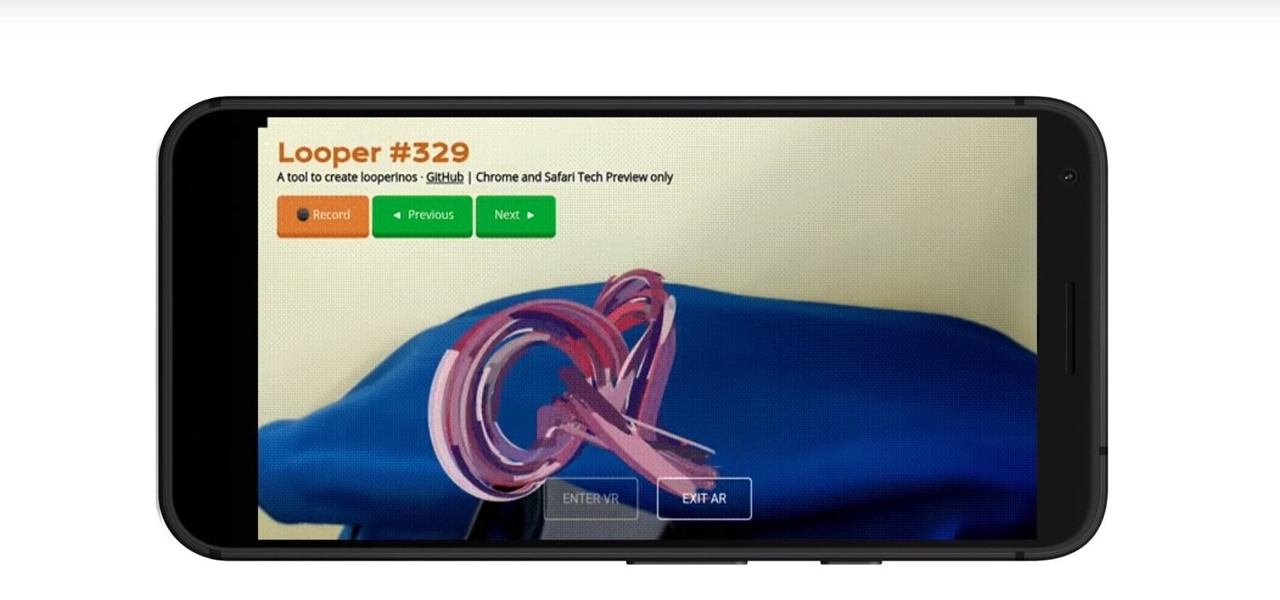
Web-based mobile augmented reality technology continues to gain momentum as Google is set to expand the standard for immersive web content to AR.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Over the weekend at IFA 2017 in Berlin, Huawei introduced the Kirin 970 processor, the first of its kind to include artificial intelligence baked into the chip.

According to the National Safety Federation (NSF), pet bowls and toys carry coliform bacteria, including Staph bacteria, yeast, and mold. Additionally, an (unscientific) survey from Petco found that almost one-third of pet owners do not know the extent of contamination that their pet toys contain.

This Video is about my Trying a New Braid pattern for a Crochet Weave.

I will Show you in this Video How I dust my Ends... PLEASE NOTE:

Playlists are more than just a list of songs that you enjoy listening to while in traffic or hosting a party—they're stories that illustrate who you are or your frame of mind at a certain point in your life.

Video: . Saran Wrap Technique done on Natural hair.