Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.

A piece of paper and some common household supplies are all you need to make yourself a wallet. Inspired by the Instructables project: http://www.instructables.com/id/Paper-Wallet/

In this how-to video, Bethany takes us on a garden tour this week with a lunch sack! She shows how to turn this ordinary household item into a dreamy scrapbook. And then she raids the cupboards again using packing tape to create some filmy image transfer embellishments. So grab your lunch and get ready! Watch this video scrapbooking tutorial and learn how to make a garden of my dreams album out of a paper bag.

Here is a video tutorial that offers basic tips on crafting a simple claymation character using everyday, household objects. Soften a single chunk of material and pull your claymation character's limbs and head from it. Insert a toothpick (or armature) to stabilize the body and head. Pull out facial features with small tools. Experiment with different poses and facial expressions to make a fun animation. This playful claymation how to video is great for beginning animators, so sit back and en...

You just bought a laptop, but how to do you protect it? Buy a laptop case! No wait... make your own laptop case out of household items. Watch this how-to video from Gianny L and learn how to make a simple laptop or notebook case out of old pants or jeans and a piece of plastic.

Lisa shows us how to clean up spilled candle wax using an iron and a paper towel, a trick from Japanese Urawaza.

This how to video shows us how to clean up spilled egg yolk using salt. Avoid a slippery sticky mess with these great cleaning tips.

Joy and Gracie show us how to make a newborn infant stop crying and sleep in peace using a wine tasting secret. This is a Japanese Urawaza trick that uses the white noise of a gurgle to ease a baby's cry.

This how to video shows us how to fix a scratched cd or dvd using toothpaste. Don't throw out that scratched cd or dvd, just fix it with this DIY home project.

There are dozens of light bulbs on your vehicle, illuminating everything to the road in front to the license plate in the rear, and for all of the modern technologies given us, most automotive bulbs are essentially the same as on out grandfather's car. So, it's no wonder why burnt out auto light bulbs are the number one cause of lighting failure.

Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.

F for FAKE. This video has been labeled a "Faux-To". Commonly contested as bogus science, we believe this video to be a hoax. What's your opinion? Comment below.

here are lots of products for fertilizing Roses and Roses need fertilizing for the best blooms. A household product that works well is Epsom Salt. The Magnesium Sulfate in Epsom Salts is great for Roses. All you do is take a half cup of Epsom Salt Crystals and sprinkle it around the Rose, once in the Spring and once in the Fall. That will be enough when you water it in to get those blooms going. The only thing to be concerned about is if you have high magnesium levels in your soil. It is alwa...

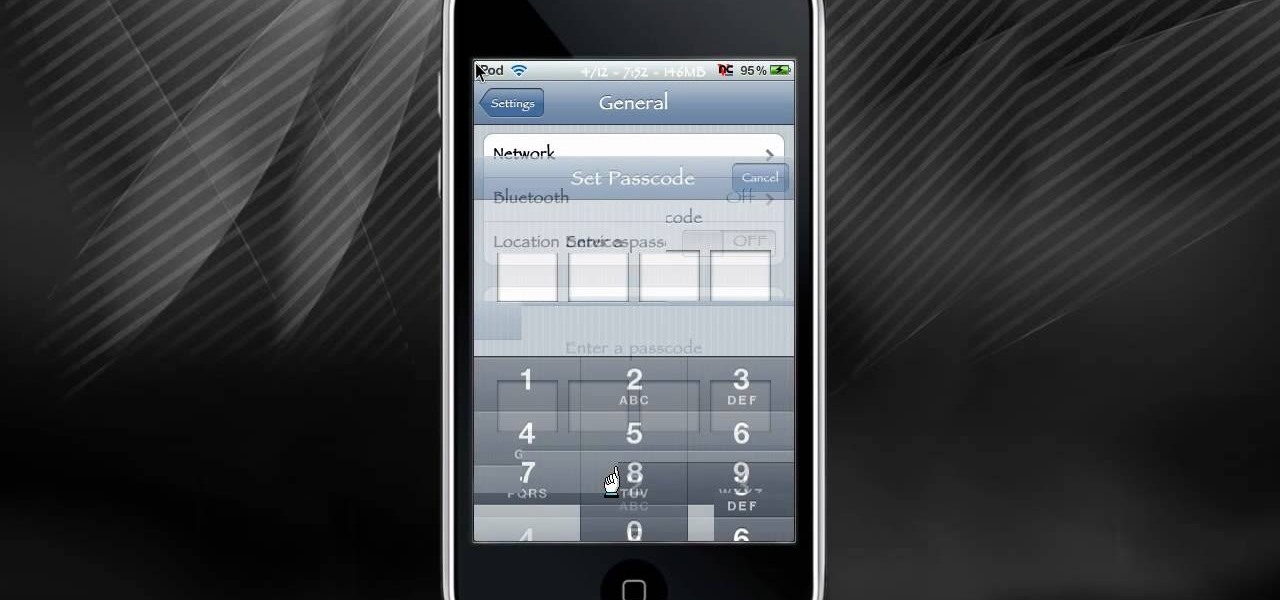
Back in the olden days, if a lock was, well, locked, you couldn't get in the door. At least, the average individual couldn't get in the door. But inventive and scheming folk (read: ye hackers of olde) devised crafty ways to pick lock keys and sometimes even created skeleton keys that opened any door or chest. This will let you unlock someones password on an ipod or iphone touch.

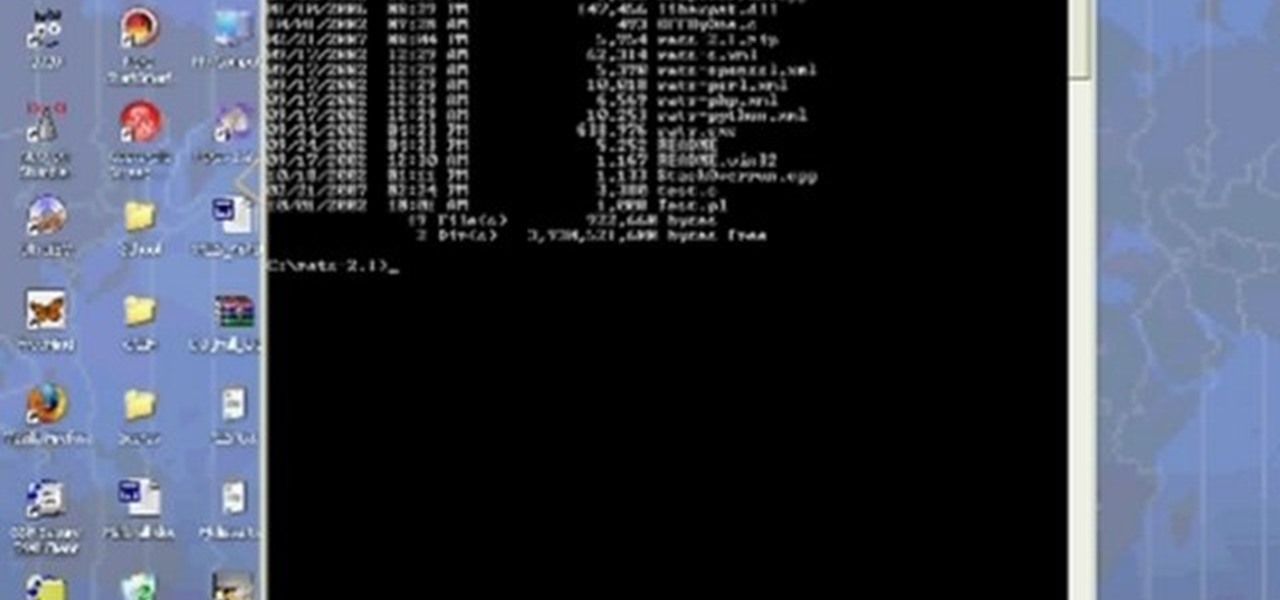
Any hacker worth her salt will need to debug from time to time. One particularly efficient way to check your code is with the RATS code checking tool. In this video, you'll learn how to use the RATS code checking tool for C/C++, PHP and Perl. For a detailed walkthrough on how to use RATS scanner to audit your source code, take a look!

The purpose of this video is to show an e-mail security flaw using telnet that allows hackers to send e-mails using anyone's e-mail address. Thankfully, many major e-mail providers have software that blocks this. My intention is to make people aware of this flaw so that other e-mail providers can protect themselves as well.

Did you know that malicious people can use scanners to read the Radio Frequency Identification (RFID) chips in your credit cards and identification documents and steal your personal information? Learn to protect your personal information from hackers and scammers with this simple method involving aluminum foil.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Cursed treasure is a very popular and challenging web game that, like most of it's webgame contemporaries, has attracted a lot of attention from hackers looking to make it easier to cheat in the game. This video shows you how to use cheat engine to get more money and change other numerical values in the game to improve your gameplay experience.

Protect your email account from would-be hackers and crackers with this free video tutorial from the folks at MacMost. If you have a Gmail, HotMail, Yahoo! Mail or other web-based email account, this video is much recommended. For more information, and to secure your own online free email account, watch this helpful guide.

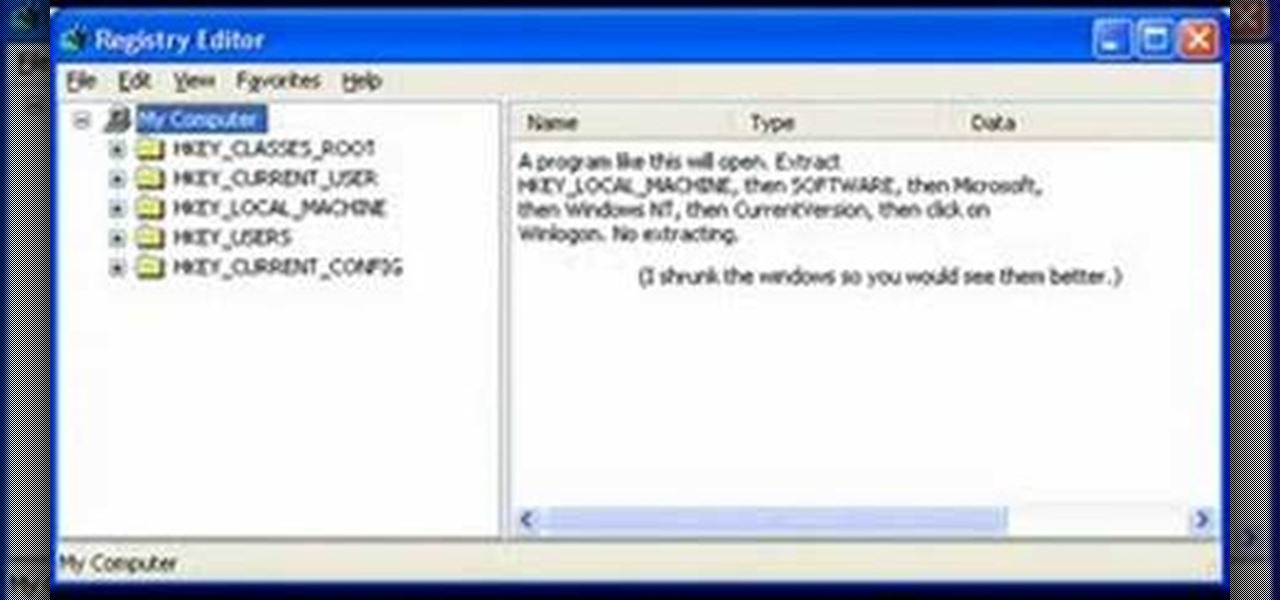
In this how-to video, you will learn how to change your start menu text. You will need resource hacker and regedit in order to perform this. First, open resource hacker. Click file and open. Go to 37, and click on 1033. Change 578 to whatever you want the text on the start menu to be. Press compile script. Next, save this file. Now, open regedit and go to software. Go to shell and click modify. Change the value data to the name of your .exe file, which should be saved in the windows folder. N...

In this video one of the ultimate iPhone hackers, Jonathan A. Zdziarsk, demonstrates how to use a forensics toolkit to recover deleted text messages on an iPhone. But wait - there's more! Not only can you access text messages, but almost any other data on an iPhone as well. We can't be responsible for what you find though!

This how-to video shows how you can hack a standard baseball cap into a cool invisible IR mask to hide your face from cameras anywhere, and look perfectly normal to the human eye! You have to admire a technically accomplished hacker. Now don't go out a rob a bank or anything. Watch this video tutorial and learn how to camera-proof your face with a creepy infrared mask.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

So, how does someone keep their hacking life completely secret? What This Is:

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Being healthy and active will help you live longer, but finding the strength to work out? That's hard. What does it do for me right now? I mean, here I sit, writing this article, thinking about going for a run, and I feel good just for thinking about running. But will I do it? Nah, I'm too lazy.

There's nothing better than gathering up all the cushions, pillows, and blankets in your home and having a good ol' fashion movie night. But if you're still rocking the old 19-inch TV your parents gave you in college, you may want to upgrade to something bigger.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

In this homemade craft projects video series, get ideas and tips on how to decorate everyday household items with stickers and stencils. Our expert artist will show you how to liven up your life using a few crafts supplies, some great ideas and a little time. Have fun!

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

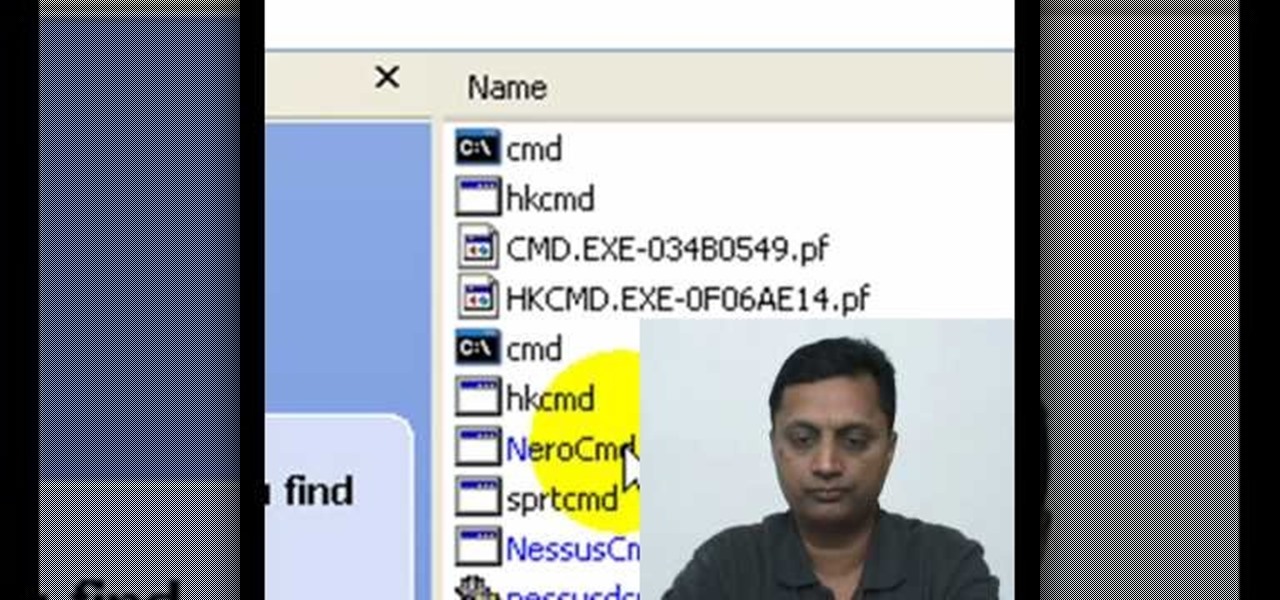
Here is a basic walk-through of how to remove the harmful file known as the cmdd.exe. The cmdd.exe file is a backdoor trojan virus that can allow a hacker remote access to a computer infected with it. Your computer can be infected with this threatening virus at any time and it must be removed immediately. This video provides several techniques that can be used to completely get rid of the file from your computer.

Believe it or not, people are still using Friendster. Which is great news for all you hackers because that means there are accounts to hack! With this video you'll find out how to exploit a programming loop hole in order to hack into someone's Friendster account. We can't promise you'll find anything interesting!

Need to know how to customize your general system information? It's handy if you build or fix your own systems and want a way to brand them, or just to personalize your system. This is a great tutorial on customizing operating systems in XP by informationleak.net hacker Halla.