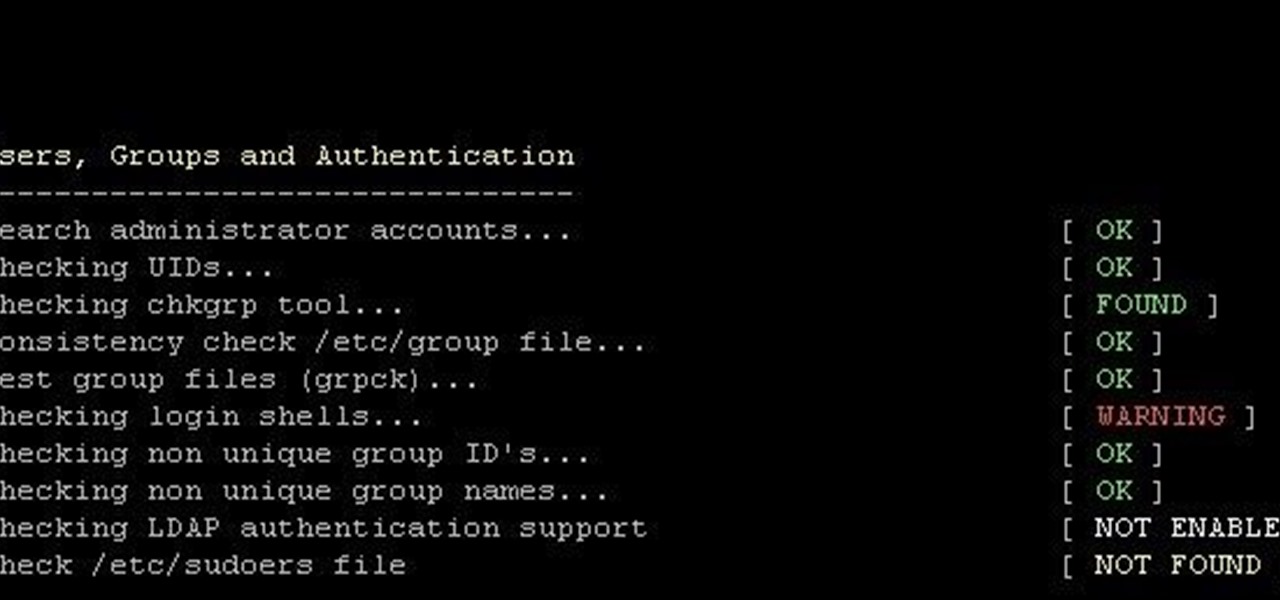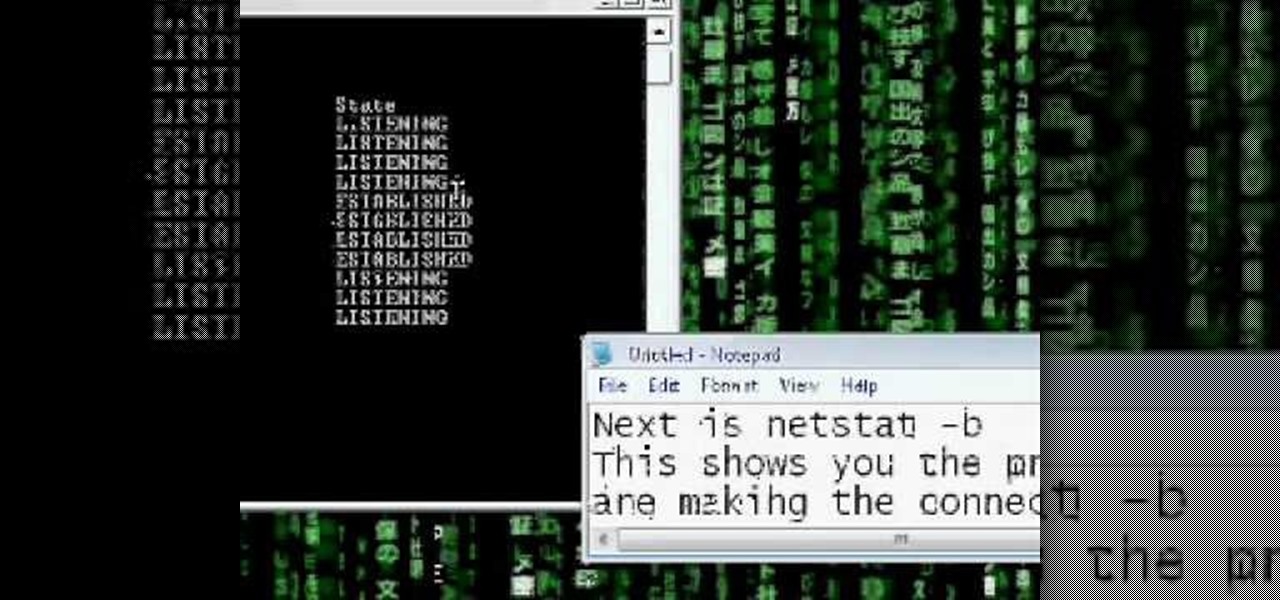
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.
In this video tutorial, a CEH-certified Ethical Hacker will teach you how to exploit the old netbios remote IPC$ share while also demonstrating the beginning stages of a successful network security audit. For more
This is a tutorial about how to browse the web anonymously on a Linux server. Requires some knowledge of Linux. Be sure to note that information sent through this system is ever MORE open to hackers than the normal Internet. Don't send any personal information this way.

Jim Twamley teaches us how to perform RV air conditioning maintenance in this tutorial. It can be expensive to replace an air conditioner, cleaning it will help give it a longer life. First, remove the top of the unit by removing the screws from the front and back. After this, blow out the inside to make sure everything is nice and clean with air pressure. Next, clean the inside of the top of the unit with household cleaner and a clean rag. After this, replace the top to the unit and insert t...

In this video, Do It Your Self Central demonstrates to viewers how to clean a dirty penny by using common household products, namely vinegar and iodized salt. He suggests to put 1/2 cup vinegar and 2 teaspoons of iodized salt into a cup. This solution will be used to clean the penny. He demonstrates the power of the solution by holding the penny into the mixture for a few seconds. After only a short time, he shows the dramatic change between the portion that was dipped in the solution and the...

In this video, Lusitano 9514 will show you how to make a homemade rubber band bow and arrow out of common household items. To do it, you will only need a basic plastic coat hanger, a long rubber band, and some kind of a stick (for the "arrow"), all of which are quite inexpensive. Watch Lusitano 9514 demonstrate for you exactly how to make the bow and arrow, and show how it works. You will also learn tips and tricks, such as what materials make better ammunition, and what kind of "arrows" are ...

This video teaches you how to open a Rubik's Cube using a pair of scissors (and it says other household "tools" might work). After taking out the first block you can simply disassemble the other components as well. It's very useful if you are looking to replace a broken piece or if you can't solve the cube. Following the steps in this video will make you feel more comfortable about taking one of these cubes apart, since you might be afraid to break the cube while disassembling it. There is al...

A breakaway chair is one of the best pranks, or one of the easiest effects for your indie film project. A breakable chair can be made out of simple household items, and is very cheap. The biggest material needed is cardboard. So basically, you'll make a cardboard chair, that breaks. Watch this video tutorial to learn how to make a fake movie prop brick.

Watch skilled potter, Simon Leach, give his expert instructions on how to glaze a set of tea bowls. He also suggests some household supplies which can be used to embellish your ceramics when the clay is still soft, such as a bolt or a comb. This glaze is a combination of Scotland Hills red mud, feldspar and wood ash. He also uses white clay slip on some of the pots. This is a process wear one glazes the tea bowls while the clay is still semi-soft.

Scrapbooking is all about using a variety of materials to create different effects. This idea just uses simple household masking tape and watercolor paints. Masking tape can be stuck onto a glass surface or anything else where it can be easily removed, and then painted with watercolor paints. The end result is a really great finish. Watch this video scrapbooking tutorial and learn how to use masking tape and watercolor paints to create a unique look for any scrapbooking project.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

Video: . This is a very simple way to set up a booby trap inside your house for your friends and family, It can get messy so prank at your own risk.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

This is a compilation of 5 of the best evil pranks that you can get away with doing on your friends and family. The best part of this is that you'll only need everyday household items you already have.

There are some practical jokes that are funny and will give everyone a good laugh including the person being prank, There there are those pranks that will annoy and infuriate anyone. These 5 pranks will do just that, especially the last one which involves 2 matches and a pen, then again we have a condom inside a water bottle prank. There just too funny and mean to describe, you'll just have to watch the video tutorial to find out how to pull them off. The best part is that they're all househo...

"Oh God! Again this Zipper got stuck. I'm gonna through it away." People… cool! This kinda things can be done on your own… by yourself by some simple household items.

So you've fallen for many pranks on April Fool's day and surely you feel like a "fool" well it's time to dust yourself off and start pulling pranks of your own on those that got you earlier. Here are 5 pranks you can set up on your enemies on April Fool's Day.... Most require the use of household items which you might already have. Check out the video tutorial provided for further instructions!

Welcome back, my greenhorn hackers!

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

Ah, Halloween—the funnest, but scariest day of the year. You don't just dress up and go door to door asking for candy—it's the best day to pull off scary/spooky pranks.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

Amazon.com has been around for a long time now, but there are still a few things most people don't know about when it comes to buying products from them. Here's a quick roundup of tips to help you get the most out of Amazon and save some money in the process. The holidays are the busiest time of year for online shopping, but these tricks will work all year around.

In this video, I will show you how to perform the color-changing, blue bottle experiment with common household products.

In this video, I'll be demonstrating how anyone can make their own iodine clock reaction with simple over-the-counter chemicals.

Hey guys. A mohawk is usually for punk rockers or maybe just for people who stand out, but many people dont know how easy it really is to spike a mohawk! There are a variety of ways and many of them can be done with products bought at a store. None of the products include "Elmers glue" or "eggs and sugar" but you will need a hair dryer!

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Life stinks. Literally. Daily living leads to lots of lingering smells. Household odors from cooking, kids, pets, bathrooms, and guests can accumulate. Get rid of them with some simple remedies.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.