Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

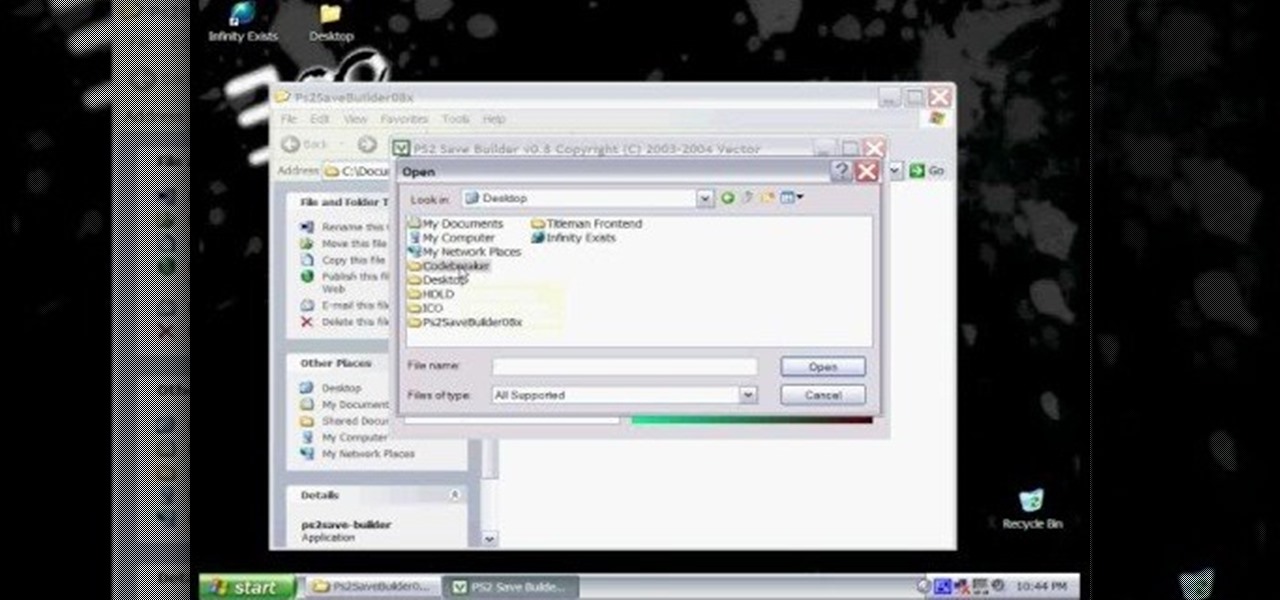
In this hacker's how-to, you'll learn how to softmod your old Playstation 2 to enable you to run third party software and how to use CogSwapLoader and HDLoader to backup your PS2 games and play them either from a burned DVD or off your hard drive. This will let you hack the PS2 to play pirated games. Remember, pirating software is illegal! This will let you unlock your PS2 to play games if you copy them from somewhere else.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

Hydrazine sulfate has many uses, but most notably, it's been used under the trade name of Sehydrin, a treatment for anorexia, cachexia and some even think cancer. But for we DIY chemists, it's useful for something entirely different— as a substitute for the more dangerous pure liquid hydrazine in chemical reactions. NurdRage shows you how to make it via some hypochlorite and the Ketazine process.

Tired of cleaning the stove and oven every time you cook? (It always gets so messy, doesn't it?) Well, there's one solution to keep the cleanup to a minimum, albeit a little unconventional, and that is to use your dishwasher!

This video is presented by A K Dlnny. The video starts with common location in any household. A K shows a CD which is fairly scratched. Most of us have scratched CDs with us and he teaches us a very simple way of cleaning these CDs. As first step A K takes good portion of common toothpaste on surface of CD and spreads it all over with rubbing it with circular movement of his finger. Once the entire surface is covered then he allows the CD to dry for five minutes. In next step he washes of the...

Benson Trenh and Mark Norris show viewers how to build a bottle rocket using common household items. To build this creation you will need tape, a hole puncher, scissors and string. Also use a black plastic bag, or any color, for the parachute! Cut the black plastic bag into a square, any size you would like! Next, take the square and punch a hole at each edge of the square and string the string through the hole tying a knot. You should now have the parachute! For the body of the rocket, get a...

If you've ever dinged your car—or worse, a friend's or parent's car—and caused a dent, you know how expensive it can be to fix. A two-second mistake can end up costing hundreds of dollars, but you can save yourself repairs costs and a headache with just a couple of household items.

Detect metal with a metal detector! In this video tutorial, you will see how to create a metal detector out of just two household items, for under twenty dollars. So, if you're on a treasure hunt, and have no money yet, then make your own metal detector.

Learn how to make a light bulb light up with common household items. This is how you make a light bulb light with:

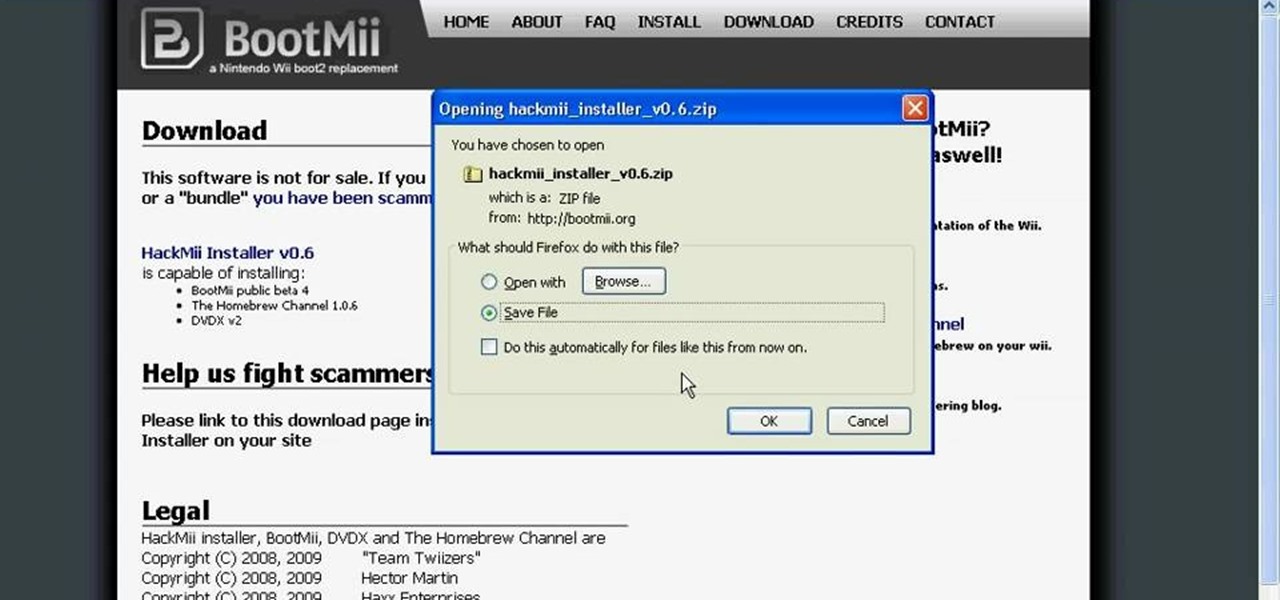
Installing the Homebrew channel on your Wii is one of the smartest things that you can do as a Wii owner. It allows you to use the console for all sorts of things like playing ROMs, movies, and homebrew games on your Wii. This video wills how you how to do it on a Wii with firmware version 4.2. If you upgraded to 4.3, we apologize, but the hacker are still working on hacking those, so be patient.

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

The Windows Phone 7 platform has been out long enough now that hackers the world over have had ample time to play with it, and the fruits of their labors are coming fast and thick now. This video will teach you how to unlock or "jailbreak" (misnomer in this case) your Windows Phone 7 with ChevronWP7 so you can install custom ringtones and perform other power-user functions. You'll also need the certificate for it, ringtone manager, and the Windows Phone Developer Tools.

With custom ROMs said to be impossible on Verizon's new Motorola Droid X, thanks to something called eFuse, many users will be deterred from trying to mod their Droid X mobile device. But it's only a matter of time before a hacker figures out a workaround for the Droid X, but if you want to try to hack it yourself, this video tutorial will get you started. It will show you how to get into the Droid X bootloader. It could possibly help you "root" the cell phone, if you're lucky.

Hacking the Wii is a fun and not-too-challenging way to have a lot of fun with your console and give yourself a geeky sense of accomplishment. This video will show you how to hack a Wii from any region and with any firmware version between 3.2 and 4.2 using these files for versions 4.1 and below and these for version 4.2. If you've already upgraded to 4.3 that's too bad, because as yet 4.3 is hackproof. You'll just have to wait for the hackers to figure it out.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

Sweet and sour sauce makes everything taste better. You can add this tangy dip to fish, chicken, meat and even tofu for an Asian flair. In this tutorial, Betty will show you how to use simple household spices to whip up your own easy batch. Enjoy!

Pranks are the world's favorite pastime. Everyone loves a good prank, and there's nothing better than keeping someones stomach empty. Imagine the pain and suffering one would endure if he or she could not eat because the fridge will not open. Most refrigerators allow for reversing the door swing. Normally you also switch the handle. But not if you want to thoroughly confuse the victim of this practical joke.

In this video, Liz Grotyohann demonstrates how to make decorative bowls from recycled paper. The materials required for the purpose a bowl shaped mold, a blender, a basin of water, a tray, a paper making tool, a sponge, some cloth and any kind of household waste paper like paper bags or junk mail. Liz prefers to use compressed packaging material and lines the bowls with old maps. She wets the map and covers the bowl with it. Pieces of brown paper are put in a blender with water and blended to...

This video shows how to make a cute vintage looking jewelery box. A cardboard cheese box forms the body of the jewelery box. Other items you will need include mod podge, white glue gesso, masking tape, ribbons, a mirror from a compact, some fabric, and some faux pearls and flowers. Begin my removing the labels from the box. Paint the inside and outside of the walls of the box and the lid. Paint the areas of the box that you just primed with gold metalic paint. Now use the box to trace three c...

Missa shows how to ‘Distress Jeans’ in this video. She lays a pair of jeans to be distressed on a table. Next, the creases near the top, which are formed by bending the leg portion of the jean, are marked with a white pencil or chalk. A hard rock is then placed inside the jean, near the knee area. That portion of the jean is graded using sand paper to make holes. The pocket areas are graded next, using a nail file. A pair of scissors is scraped along the edges of the pockets to make cuts. (Al...

If you have never dealt with wire color-coding then Old64goat takes you through a very elementary tutorial that will give you the helpful aid needed to deal with common household wires. The first cord that is reviewed is the three pronged cord. The color wires contained within it is the green wire which is the ground prong, the white wire which is neutral, and the black wire which is the heat. Old64goat then demonstrates where the wires are connected to on the prong. He even gives out helpful...

Watch this science video tutorial from Nurd Rage on how to make a mirror silvering solution from silver nitrate, ammonia, sugar, and sodium hydroxide.

BitLocker. What is it? And what can it do for you? Well, it's a handy new feature built-in to Windows 7, and it can help protect all of your data from loss, theft, or hackers. It's the easiest way to make sure your documents and files are safe from the devil's hands.

Bead frames are pretty simple to understand. Rather than simply stringing beads onto a pendant or necklace, you can attach them to bead frames, which come in all shapes and varieties, to make a novel design that can take advantage of negative space. It goes without saying that elaborate bead frames make the entire design more ornamental, whereas a simple round wooden bead base helps put the spotlight on the bead in the center for a subtle glamour.