
How To: Clean green
Learn how to clean green. Forget the industrial cleaners and acids: a few household basics are all you need to breathe fresh air into your home.


Learn how to clean green. Forget the industrial cleaners and acids: a few household basics are all you need to breathe fresh air into your home.

Don’t laugh—butter sculpture is a true art form that originated in Tibet in the 7th century. It is now one of the highlights of many American harvest fairs. Learn how to make your own butter sculpture.

Remove mildew as soon as you see it: not only is it gross, the longer the mold is allowed to grow, the more damage it can do to surfaces and even your health.
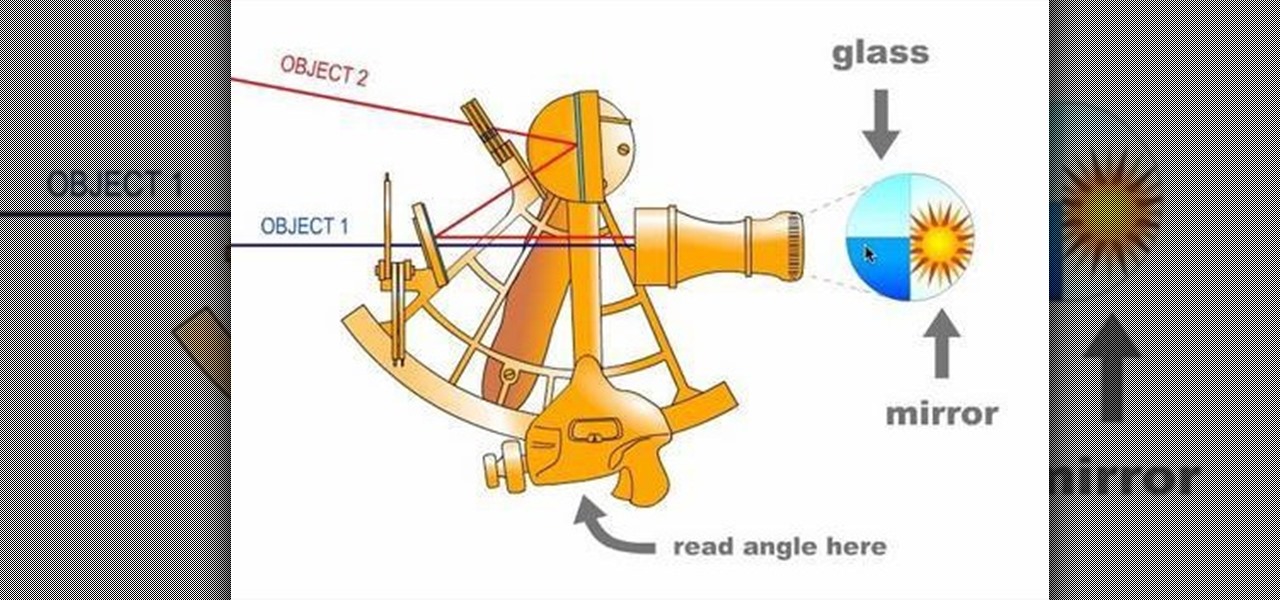
Learn how to find south, your latitude, and your longitude with only a few household items and some know-how, just by watching this science video tutorial. However, if using the homemade quadrant cited, the precision of your findings will be rather low. Don't worry, you'll be within a few hundred miles though.

Sometimes as a pet owner it is difficult to keep your home clean and smelling fresh. In this Housekeeping how-to video the Dog Channel offers five tips to battle dog odor in your home. Follow these five tips and have your home smelling fresh.

Craft projects are a great way to recycle household items and clothes. Learn how to make three recycled crafts, a beach bag, a puzzle and a hat, in this free arts video series.

Power tools can make an household repair job a breeze. Learn how to use and maintain an electric hand drill with expert tips in this free video series.

African violets make great household plants. Learn how to grow and care for African violets in this free gardening video series.

Kids' art projects don't have to be expensive or time-consuming. In this free online series of art videos about crafts for kids, learn how to make fun projects from household items, taught by expert Pamela Grier.

Making a PCB is very simple; it does not consume a lot of time and the results look professional. After watching this step-by-step how-to video, you will be able to make your own PCB in your workshop using just a few inexpensive materials.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

Chumby is the dream toy of hackers and tinkerers everywhere. Made up of a few simple parts, Chumby takes your favorite parts of the Internet and streams it so that you'll always have access to your favorite podcasts, music, photos, games and more. What's great is that you can put together the Chumby yourself. In this video MAKE shows us how to put the Chumby guts kit together. Be sure to make sure you have all the required parts.

While there are many advantages to working from home, properly managing your time can be a real issue. Working remotely requires a particular skill set, including an ability to focus, self-motivate, and communicate from a distance. Thankfully, all of these skills are teachable.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.


Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

Bad news first: It's not out yet, but it's coming really soon. The premise for the game is this: