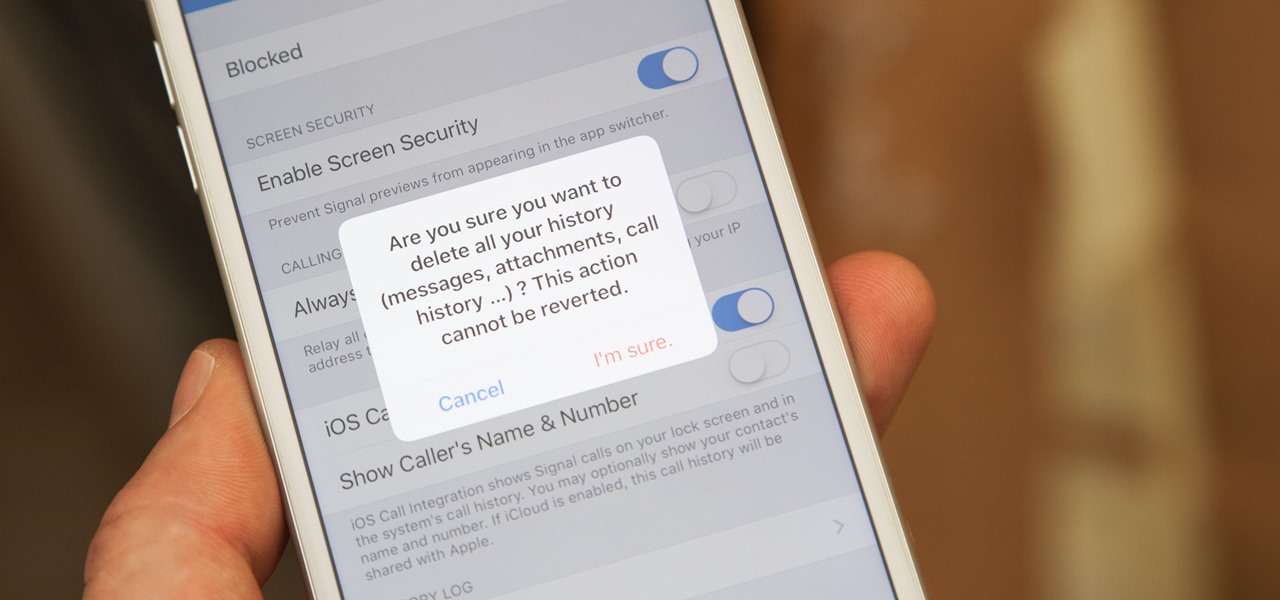
Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Do you see a red door and wonder if it might be a good idea to paint it black? You could "ask Ask Sherwin-Williams," or, better yet, you could just ask the new augmented reality features in the retailer's mobile app.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

If the end of every year is focused on new iPhones, then February, which coincides with Mobile World Congress, is often when we get new Android news, and this month is no different.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

If you're on Instagram, you may start to see Babadook all dressed up this month. This beautiful monster is taking Instagram by storm by #babashooking it's way all around the world in its brand new Pride attire.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

Microsoft announced yet another exciting partnership for HoloLens today — thyssenkrupp, an industrial engineering company best known for their elevators — continuing to prove how useful augmented reality is in the workplace.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

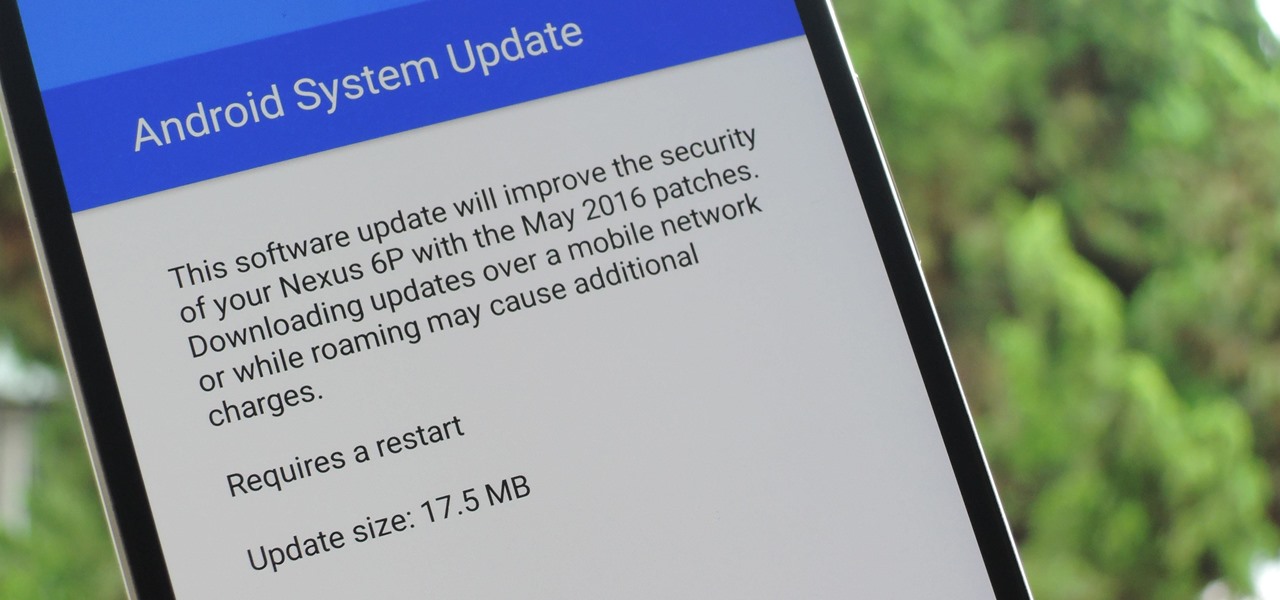
The beauty of Nexus devices is they receive firmware updates faster than any other Android phone, and keep getting updates for years longer than most of the competition. This means that you can always use the great new features that come along with an Android update, and even more importantly, your phone gets monthly security patches to keep hackers and malware at bay.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

For $35, there's hardly a better value in the online media player market than the Chromecast. Taking that sentiment a step further, if you factor in the promotions Google likes to offer with it, Chromecast practically pays for itself.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

Guardians of the Galaxy wowed moviegoers this summer with its sassy, strong team of intergalactic superheroes. From Groot, the ever-growing tree, to Rocket, the rough-around-the-edges raccoon, the film had an unending supply of unique characters—but no one stood out as much as Gamora.

Star-Lord may not have been a household name prior to the release of Guardians of the Galaxy, but you can sure count on a flood of kids and adults alike wanting to dress up as Chris Pratt's character this year for Halloween.

The Billboard Charts have been a measurement of commercial success for pop songs since roughly the time that radios became a household item. In its modern form, Billboard ranks the sales and performance of all singles with its "Hot 100" chart, as well as many other genre-specific rankings.

On a recent trip to Palm Springs, I found myself navigating with Google Maps and virtually exploring my destiniation using its built-in Street View feature. The thing is, using Street View can make keeping track of your exact location difficult as you zoom in, out, and about. It's a little discombobulating.

Interesting reaction coke and milk The reaction of phosphoric acid (V) to proteins in the milk - they are cut and causes a precipitate

Creating awesomely messy slops of DIY slime and curdled fake blood isn't something new—we even have guides on making Dr. Seuss-friendly Oobleck and the radioactive green ooze that created my childhood favorite Teenage Mutant Ninja Turtles (minus the radioactive part, of course).

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

The cord on your headphones is usually more enemy than friend. While they obviously need it to function, a tangled or unnecessarily long cord can wreak havoc on your sanity. Personally, I've broken at least two pairs of headphones by tripping over the cord and yanking the jack right off of the wiring. There is a fix for that, but you can prevent the problem altogether by organizing your cords. There are plenty of ways to wrap a cord so it won't get tangled, but you still have to unwrap it if ...

Separating an egg yolk from the white is one of the most universally hated kitchen tasks out there. Most cooks prefer using their hands or the egg's own shell to separate them. For those who don't like getting messy, there are countless devices designed solely for this purpose, and a lot of shortcuts that use household items to make it easier. Remember this water bottle trick?

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much attention is due to several, well-known features like Google Talk, Project Butter and expandable notifications.

Forgot the passwords to your email or your other favorite websites? If you typically store your passwords in Internet Explorer (IE9 or other versions) it can be tricky to get your passwords back -- but this tutorial makes it really easy!

A spectrometer is a device that splits light into all of the different colors it's composed of that can't be seen with the naked eye. It does this by using a prism to refract or bend the light. Jeffrey Warren over at Public Labs created a tutorial showing how you can make your own video spectrometer and create spectra like the one pictured below. Any guesses as to what the subject is? Believe it or not, that's what whipped cream looks like when viewed through a spectrometer. You can do this w...

Unless you're living in some weird parallel universe where plug-in light bulbs are the norm for household lighting, chances are you've had to unscrew a light bulb every now and then.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.