If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Want to build a fire extinguisher using things you can find around the house? Science shows you how to properly apply technology to kitchen safety! Your main supplies for this project are a mayonnaise jar, some vinegar and baking soda.

A new twist on the classic fish recipe. With a very light breading and use of rosemary this simple recipe will become a weekly go-to recipe in your household. Watch this how to video to learn how to cook a breaded rosemary fish recipe.

Learn how to make edible sugar glue using household items. Cool sugar art video.

Apple and AT&T can keep changing the baseband and the firmware on the iPhone as much as they want and hackers are gonna stay ahead of them, especially now that jailbreaking is legal. This new video will show you how to unlock a jailbroken iPhone 3G or 3GS with iOS version 3.1.3 or 4.0.1 and basebands 5.12.01, 5.13.04, 5.11.07, and 4.28.08. Now you can use it on any carrier, breaking free of AT&T's crappy network for good.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

The "Hacker" style was created for hackwars.net for their avatar system. You can basically take the simple shapes as seen at first in the video and draw pretty much any kind of character. Just go wild! Don't forget to add the thick black line around the outside. It really makes this style. Check out this video drawing tutorial and learn how to sketch a Hacker style kid with a bazooka.

In this tutorial, Jenny Jones invites you into her bedroom to show you how to give yourself an easy, 6 step at-home facial. Keep your skin young and bright with these fantastic tips from America's favorite talk show host.

Would you know what to do if someone ingested poison? Equally important, would you know what not to do?

Create lasting memories by organizing a well-planned family reunion. This video will show you how to organize a family reunion.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

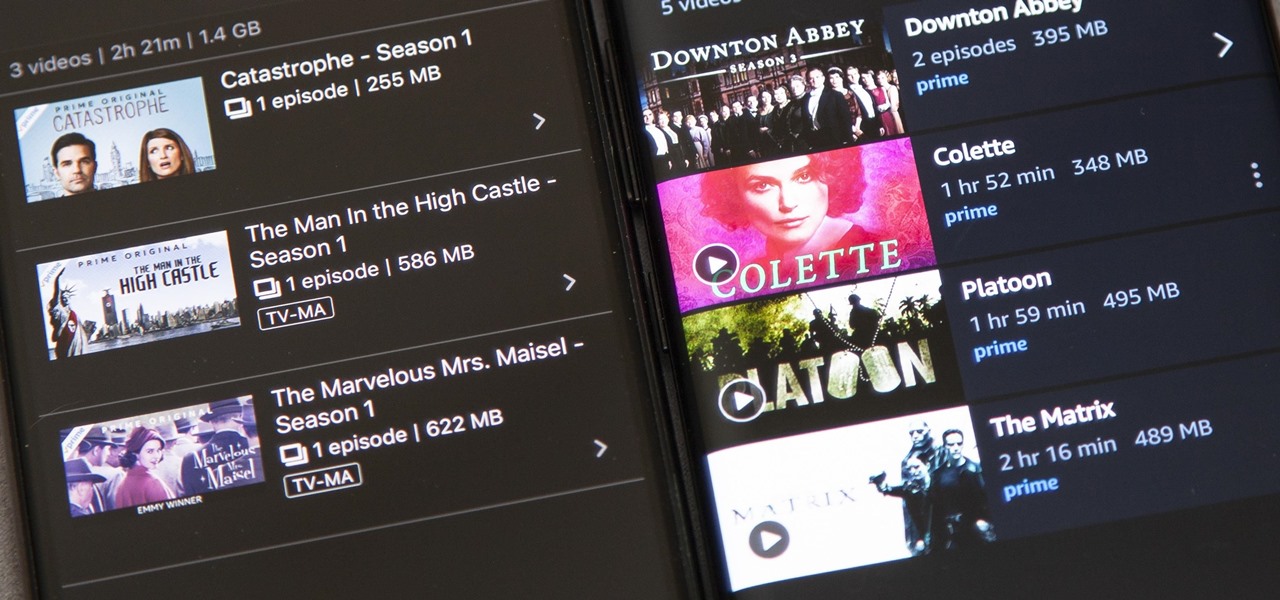
Back in 2015, Amazon Prime Video was the first subscription-based streaming service to introduce the ability to download movies and TV shows for offline viewing on mobile devices. For travelers and users with limited data plans that like to watch films and episodes on the go, this was a godsend. Amazon has updated its apps many times since then, but the process remains relatively the same.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Watch to learn how to replace the hose on a Dyson DC07 vacuum cleaner. This Dyson spare parts video we show how to remove and replace the Dyson DC07 Hose Assembly. A broken vacuum hose will cause poor suction.

Watch to learn how to replace knobs and buttons on a Neff oven. You'll remove and replace the knobs and buttons on a Neff oven. Lost oven knobs or worn oven buttons detract from the ovens appearance.

Watch to learn how to change an AEG Electrolux fridge freezer lightbulb and how to fit a replacement door bottle shelf. Changing a blown fridge light bulb is a simple fridge repair. This fridge maintenance video explains the process.

This is a bare bones science experiment using only items that would be sitting around the average household. Set up, research, and clean up of this volcano experiment will take under five minutes. Watch this video tutorial and learn how to make a model volcano. All you need is a bottle, water, shampoo, vingegar, baking soda, and paprika.

This tutorial video will show you how to apply a fake beard using makeup and other househould products. This beard could almost pass for real, except for the fact that it's made of tea.

The kitchen is the command center in many households where paper clutter piles up. This how-to video offers easy and inexpensive ways to organize all your paper clutter in the kitchen.

This quick video tutorial shows how to easily mix plaster at home. Learn how to use simple household appliances to prepare plaster for molding and sculpting.

A quick tip that can be used to create solid joints and fill gaps in scale models. Learn how to easily fix flaws in model toy cars with basic household items.

Watch this how to video to learn how to make a sachet with common safe and natural household items. Use an old t-shirt, or any other old piece of garment, and your favorite sent

Learn how to use household items to make a pulse jet engine that really works out of a jam jar. Pay attention to safety because the jam jar may explode when you make your pulse jet engine.

Make your own hot air balloon using only 4 household items, bought from any supermarket for under $10. This balloon will fly for miles.