Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.

The biggest problem with plastic wrap is also its most useful trait: its incredibly clingy nature. Plastic wrap seems to stick to itself or you before you can get it over the plate, bowl, or food you're trying to preserve. And once you do manage to get it in the right position, it never sticks as well as you need it to. Fortunately, you can combat these inconveniences with two extremely helpful methods—a change in temperature or a bit of added moisture—as Jenny Stewart of CHOW explains in the...

The following are 10 simple yet effective pranks you can set up around the house, school or the office on April Fools' Day. You'll won't need any special tools or materials to pull these off.

Video: . The following are 5 Simple household pranks you can pull off on friends and family this upcoming April Fools' Day! All the material needed you already have at home so lets get started! Check out the video tutorial for further instruction.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

One of the biggest new features in the soon-to-be-released Android 6.0 Marshmallow is something Google is calling "Now on Tap." Essentially, this service will be able to scan the contents of any screen on your Android device, then after you long-press the home button, it will provide you with relevant information about anything—from movie times to directions or dinner reservations.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

Last year, Apple debuted a feature that allows families to share iTunes and App Store purchases across their various accounts. Us Android users, on the other hand, have to buy separate copies of apps for each of our accounts—well, at least from an official standpoint.

This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Everybody loves the stars. Well, I certainly do. As a child I'd spend hours outside during summer nights marveling at the seemingly endless amount of sparkling dots spanning the sky. Maybe you have children of your own and want to create a sparkle in their eyes, or in your own. This tutorial will provide a basic method of bringing the stars inside—at least, in part.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Welcome back, my nascent hackers!

Brought to you by Tomcat. Falling snow, warm fireplace, delicious hot cocoa, quiet reading time, mouse. Quick quiz - which one is not like the other? Nothing can ruin a perfectly cozy afternoon in your home like a pest on the loose. With dropping temperatures, you may have some unwelcome residents, like mice, looking for shelter from the cold.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Welcome back, my greenhorn hackers!

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

A new coat of paint is an easy, cheap way to make your home look instantly better, but dealing with paint fumes for days afterward isn't so fun, especially if you have kids or pets.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

One good thing about having friends who are constantly on their phones and tablets is it's easy to figure out what to get them for Christmas. Everyone hates getting gifts that just sit around, so it's always nice to get something that improves an item you use on a daily basis.

When I was moving into my current apartment, I had to store some of my things in my ex-roommate's garage for over a month while I was getting settled. One of those things was my dresser. Upon moving it into my new place, I realized something was horribly, horribly wrong—none of the drawers seemed to fit quite right anymore (if they fit at all). The combination of the differences in temperature and humidity in the garage caused them to swell and change shape. Several months later, they fit bet...

Duct tape is the king of all household items. You can use duct tape for practically anything, like this sweet wallet. But duct tape isn't the only crafty tape out there; masking tape holds its own, too.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

When the time comes to move home, the logistics of moving your belongings can easily become tiresome, tricky and even disastrous. However, with a little careful planning and foresight, the act of packing can be a simple process. The key to getting the most from your move is in efficiency, planning and care. Here, we take a look at the best ways to pack in order to ensure a safe and simple move.

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

In this video series, watch as professional homemaker Vickie Pavone teaches how to iron clothes and other household items. Learn how to iron fitted sheets, how to iron flat sheets and pillow cases, how to iron a blouse, how to iron a skirt, how to iron pleats, how to iron a men's button down shirt, how to iron a men's polo shirt, how to iron slacks, how to iron denim, how to iron a law enforcement uniform, how to iron clothes using starch, how to iron, delicate silk fabrics, how to iron synth...

In this series of informative videos you will learn new ways of cleaning your home. Watch as our expert,Paige Williams, demonstrates cleaning techniques for cleaning the bathroom sink, bathroom, and fixtures. You will also learn more about cleaning the dust from your ceiling and light fixtures. See our expert demonstrate mopping basics and other techniques for cleaning household floors and walls. Get tips on cleaning faucets and countertops in the kitchen and bathroom. Cleaning windows and ot...

Perform your own fun and exciting science experiment from the comfort of your own home. With the help of this instructional video, create a beautiful Borax snowflake with simple household items like boiling water, string, pip-cleaners and pitcher. Fun for both kids or adults, this step by step guide will give you exact measurements and in less than twenty four hours, anyone can have a unique gift or decoration! You can even add food coloring to make a rainbow of delicate snowflakes that are p...

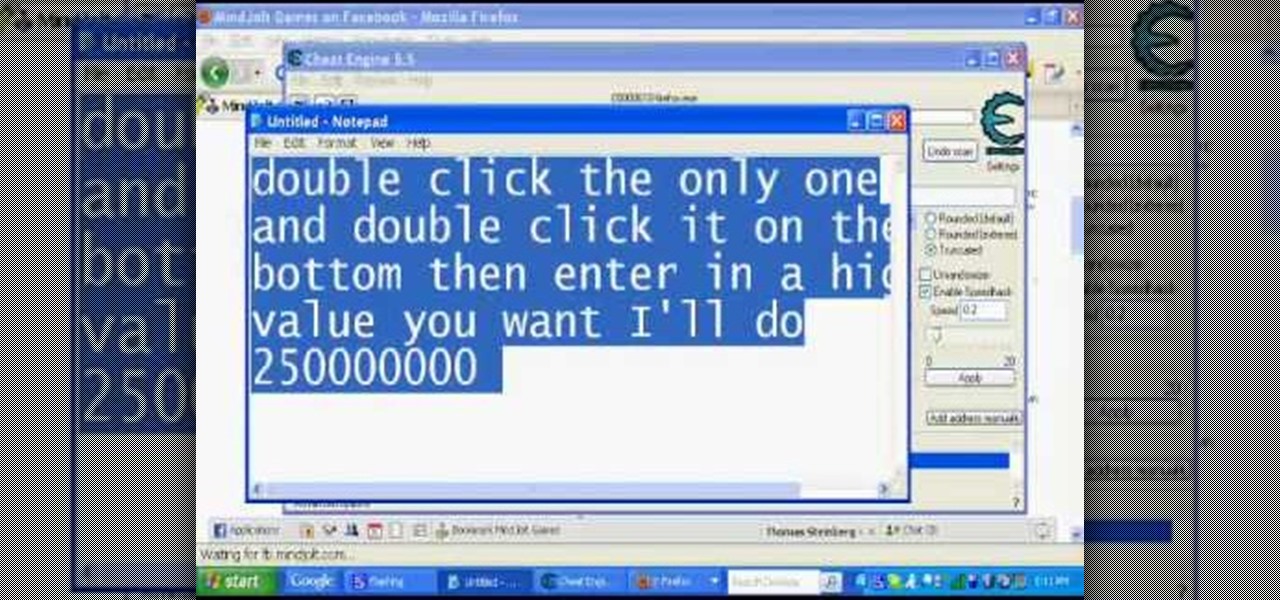
Bouncing Balls is one of those Facebook games that can be quite addicting to play. It's even more addicting to hack it. To do that, you need Cheat Engine, the ultimate flash game hacker.

It's easy to screenprint. Draw a design, tape it to a t-shirt, and use regular household bleach to stain the fabric. Watch this video printmaking tutorial and learn how to design a t-shirt using simple supplies from around the house.