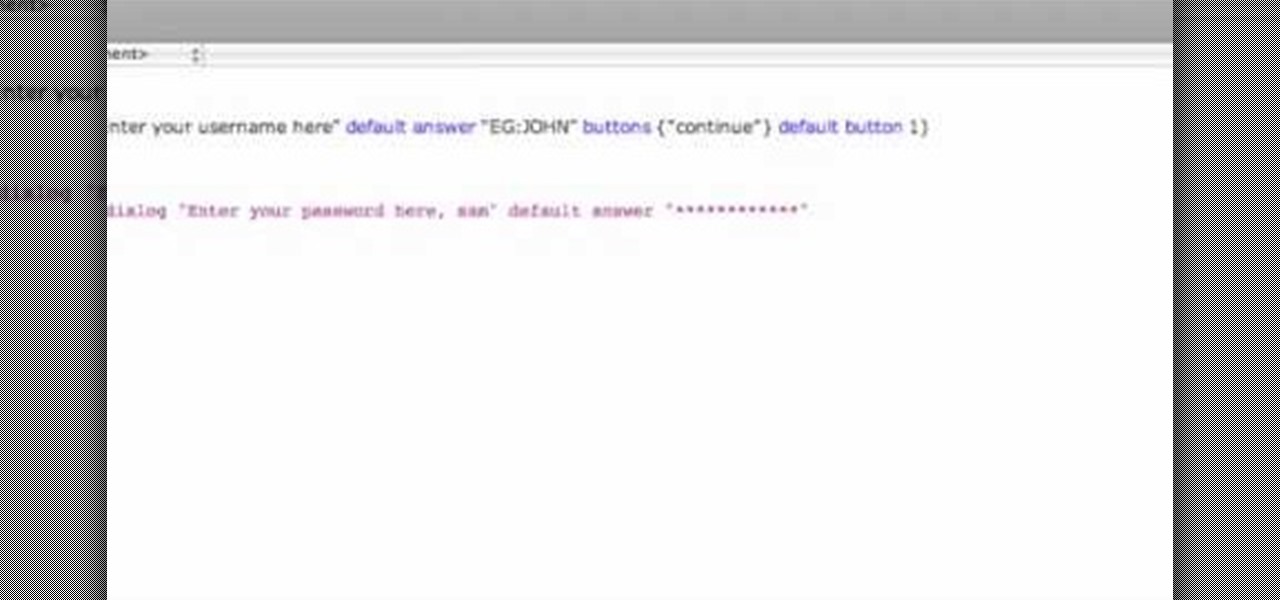
How To: Build a password and user protected app in AppleScript
This video shows how to program a password and user protected application in AppleScript.


This video shows how to program a password and user protected application in AppleScript.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

Whether you're coding a simple app, trying to learn a new programming language, or building an entirely new operating system from scratch, being able to quickly and clearly organize your thoughts is absolutely paramount — even as an ethical hacker or penetration tester.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

It's not an official app, but for fans of Rick and Morty, it's a welcome piece of the series' universe until the recently renewed animated show returns to Adult Swim.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Baidu signed a cooperation agreement on June 7, the first day of the CES Asia conference, with multiple companies in the autonomous vehicles industry. The companies listed in the press release include Desay SV, United Automotive Electronics, and Hangsheng Electronics, as well as possibly additional auto manufacturers. Baidu plans to "jointly develop" upcoming intelligent driving production plans.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

It's the bane of many a tech geek's existence that the customizability of Android software cannot be combined with the sleek design of the iPhone. A new Kickstarter project titled Eye, however, is looking to change that with a new iPhone case that allows you to combine the two.

I don't know about you, but I was obsessed with handheld gaming devices when I was younger. Between my Game Boy and multiple Tamagotchis, I was guaranteed hours of entertainment that could fit comfortably in the palm of my hand.
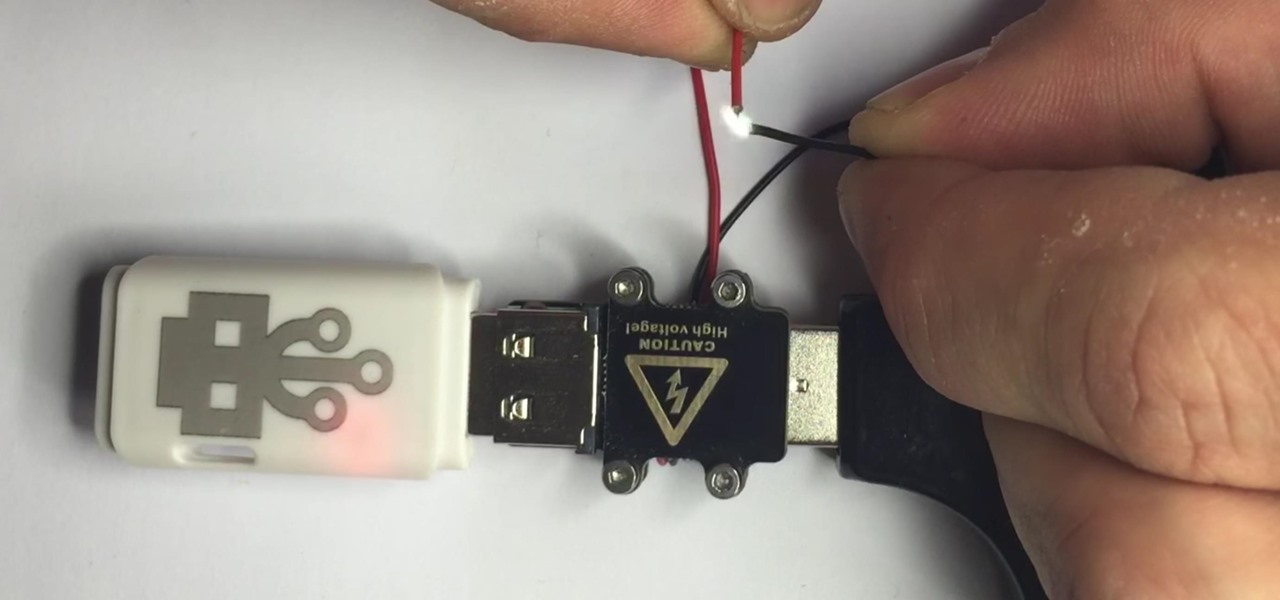
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.
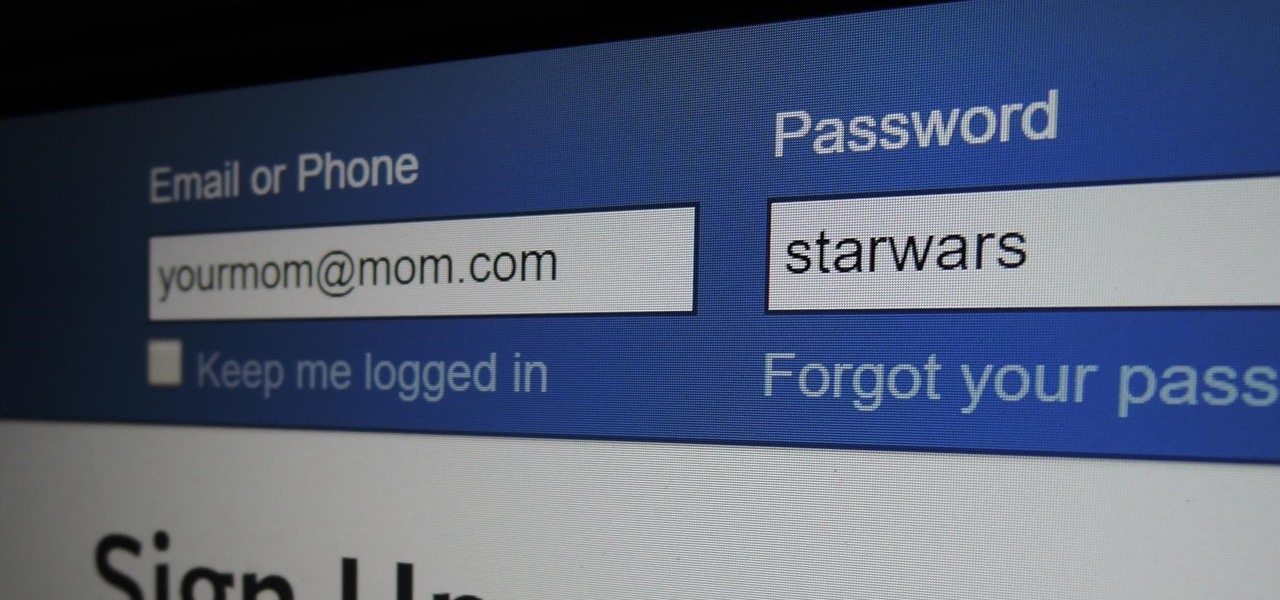
Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms).
Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

Snapchat has had more than its fair share of security failures and mishaps. The photo-sharing company is looking to better address some of these security gaps by adding new features, and today its most recent addition is live: the Captcha. New users will be asked to verify their "humanness" by selecting the infamous Snapchat ghost out of a selection of images. The feature is supposed to help block hacker-made bots from creating fake accounts or accessing existing ones. But rather than using t...
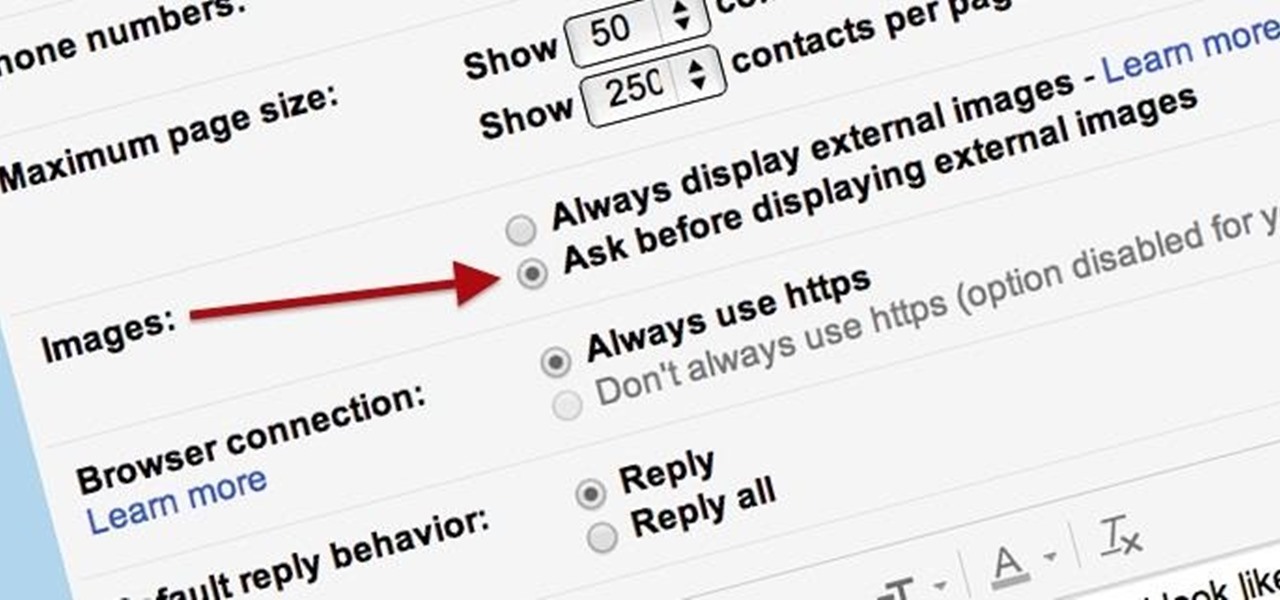
Securing your email address is one of the most important things you can do on the internet. Hackers, spammers, and overly aggressive marketers can turn your Gmail inbox into a heap trash if you're not careful.

Canned foods aren't only for Doomsday Preppers—they're great for camping trips and super quick meals on the go. When the hunger starts knocking, that can of goodies could be a savior during the Zombie Apocalypse or that day before grocery shopping.

Whether it's forgetting your driver's license or misplacing your cell phone, forgetting things at home can be a pain in the butt. Car keys, wallet, purse, papers, sunglasses—the list can go on. Sometimes I even surprise myself at the important things I forget... Oops.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.

A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide.

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Nicole Pantaleon shares some plant care tips for your household plants. She shows you what to do when your green thumb becomes too green, resulting in a mammoth, overgrown leafy beast lurking in the corner. Learn how to cut back and trim down your house plants, how to re-pot a plant, and how to fertilize and water your house plants. Nicole also gives you tips on the type of pot and soil you should use for household plants.

You paid a lot of money for and now your worried your computer screen is ruined with scratches. Just open up your bathroom cabinet and you will find everything you need to get your trusty computer screen shining like new.

Watch to learn how to replace the HEPA filter on a Dyson DC07 vacuum. This Dyson spare parts video we show how to remove and replace the Dyson DC07 Pre Motor Filter and Dyson DC07 HEPA Post Motor Filter. This vacuum maintenance video also outlines the Dyson airflow path as well as removal and replacement of the Pre Filter Housing, Post Filter Lid and Filter Seals. Prevent loss of suction and motor cut out by changing the filters on your Dyson.

Watch to learn how to replace the blade on a Flymo Hover Compact 330 mower. You'll remove and replace the 33cm Flymo blade on a Flymo Hover Compact 330. If your mower is not cutting properly remember you need a sharp blade for the perfect lawn. We use spacers to adjust the Flymo cutting height. This lawnmower maintenance video includes cleaning and we use a scraper tool to do this.

Watch to learn how to remove and repair a Neff oven door. You'll remove and replace parts on an oven door, as well as how to remove the oven door. This oven maintenance video demonstrates removal and replacement of the oven door outer glass, oven door inner glass, door hinges and door handle. Use a professional oven cleaner and ceramic scraper to remove burnt on stains from the oven inner door glass.

Watch to learn how to replace the fan oven element in a Neff oven. You'll remove and replace the fan oven element in a Neff oven. Oven fan working but no heat? You could have a faulty fan oven element. This straightforward oven repair video also shows how to remove the oven door.

Watch to learn how to replace the door seal on a Neff refrigerator. You'll remove and replace the fridge door seal on a Neff fridge. Replacing the fridge seal is an energy saving tip: If there is a fridge door seal gap, you will not create the correct fridge temperature to store food. To increase fridge efficiency fit a new seal. As part of this fridge maintenance video we also replace the fridge door bottle shelf and use a professional fridge cleaner.

Watch to learn how to replace the wave guide cover in a Neff microwave. You'll remove and replace the waveguide cover on a Neff microwave. Microwave sparks, or arcing in the microwave, could be the result of a damaged waveguide cover. As part of this microwave maintenance video we explain that you can replace a broken glass turntable or a melted roller ring. There are also microwave cleaning tips included.

Watch to learn how to replace basket wheels in an Electrolux dishwasher. You'll remove and replace upper basket wheels and lower basket wheels on an Electrolux dishwasher. Broken dishwasher basket? Perhaps you have a missing basket wheel. As part of dishwasher maintenance we replace the wheels and explain that you can also get a replacement cutlery basket.