Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Our canine best friends could spread our bacterial worst nightmare, according to a recent study. The problem with drug-resistant bacteria is well known. Overused, poorly used, and naturally adaptive bacteria clearly have us outnumbered. As science drives hard to find alternative drugs, therapies, and options to treat increasingly resistant infections, humans are treading water, hoping our drugs of last resort work until we figure out better strategies.

Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended.

The "Discover" tab in the latest version of the Google Home app has a new tip that says multiple users are now supported. Google Home uses a built-in speaker and microphone combo to give users access to smart search, a personal assistant, and smart home controls. This addition has the potential to make the voice-activated speaker powered by the Google Assistant much more efficient for households with more than one user. However, it seems that Google wasn't quite ready to announce this new fea...

Sony has upped the ante for the promotion of Smurfs: The Lost Village, which was released on April 7 in the US, with a mixed reality experience via Microsoft's HoloLens.

Norovirus outbreaks occur all year long, but peak in the winter months, which means we are in the middle of norovirus season. But there's still time to protect yourself from the highly infectious bug.

These days, if you walk through Best Buy, you will see an entire area designated to smart home technology. Thanks to the interest and growth of the Internet of Things (IoT), this exciting new technology has finally entered the mainstream. Appliances, thermostats, and even the lighting throughout your house can be controlled from your computer or smartphone. You could also use artificial intelligence; Simply tell Amazon's Alexa what you want your house to do, and she will do it.

The rumor train for Samsung's upcoming flagship phone is now running on full steam, and some of its cargo (or lack thereof) might not be warmly welcomed by many when it finally pulls into the station.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

If you're a tech geek who cares about the environment, you probably concerned with your personal carbon footprint. You may feel like your love for gadgets is slowly contributing to the degradation of our planet, but tech is your life. And in this scenario, small changes matter.

My first time opening a coconut was a confusing and frustrating experience. I remember the loud echoing noise as I hit it with a knife, a hammer, and my countertop. It took multiple tools, YouTube videos, and plenty of angry sighs for me to get it open.

Amazon has completely changed the way we purchase household items, to the point where many of us haven't visited a big box, brick-and-mortar store like Walmart or Best Buy in years. And when you think about it, all of this success comes down to two main factors—convenience and price.

In my household, we are frugal and somewhat picky eaters, so we have to be a little creative with the things we buy. We like to purchase items that can be used in multiple dishes to reduce cost—and because it's just more practical. Pancake mix is a favorite because it can be used in various dishes where any type of breading may be involved. To help inspire you, here are some of my favorite ways to use pancake batter at home.

If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard dongle (receiver).

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

When roast chicken is concerned, perfection is hard to attain. The reason for this is surprisingly simple: the light meat and the dark meat should be cooked to different temperatures. Ideally, chicken legs should be cooked to at least 170°F, while breasts should be cooked to 150°F. Naturally, this poses a conundrum: how can you cook two parts of the chicken to two different temperatures, without taking the bird apart?

Cast iron pans are a timeless treasure—they're an essential kitchen tool that will stand the test of time, and no home kitchen is complete without one. However, they do have a reputation for being difficult to care for... with arguments both for and against regular seasoning. In 2010, a blogger named Sheryl Canter claimed that she found the best way to season a cast iron pan that would keep the cast iron from rusting... or requiring re-seasoning! And after a few hands-on test by Cook's Illust...

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Many home chefs are deterred from whisk-intensive recipes such as mayonnaise because they seem to require more than two hands—which is obviously the maximum number we possess. One hand is required to stabilize the bowl, another must be whisking constantly... and a third hand is needed to pour a steady stream of oil.

Onions add essential flavor to almost any dish, whether it's a sauce, main dish, or salad. They are one of the humblest "superfoods," full of vitamins and nutrients but generally inexpensive, which is why they're also one of the most widely eaten ingredients in the world.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

When I was a little kid, I was obsessed with shells. And while most of my shell collection came from combing the beach for treasure, some of it came from a different source: dinner. Whenever my parents had fresh clams or mussels, I would take the leftover shells, soak them overnight in soapy water, and add them to my collection.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

While honey is one of the most popular ingredients on kitchen shelves the world over, honeybee pollen is still a relatively rare find in most households. It's not hard to guess why: eating pollen just sounds weird... it would probably sell a lot better if it had a more appetizing name, like honey. Furthermore, it looks unlike any other common ingredient, and the smell can be off-putting to some. But it's good, it's healthy, and it's altogether pretty awesome!

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

One lump or two? That was the age-old question with sugar cubes, which used to be a staple of any tea salon or dignified household this side of Downton Abbey. These days sugar isn't really used in cubes much except in bars and restaurants, and that's a shame. Cubes are a lot less messy than granulated sugar, and you can measure the exact amount you put in your drink no matter what.

As a kid, my favorite part of Easter were the days leading up to the holiday, when my family would dye eggs. This became an enormous event in my household, as dozens and dozens of perfectly white eggs would become little oval canvases for arts and crafts.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Alcohol is a marvelous thing. It might even be responsible for saving civilization. And we're always fans of hacking our booze intake, whether it's learning how to drink all night long without getting drunk or how to discreetly get your drink on without anyone knowing.

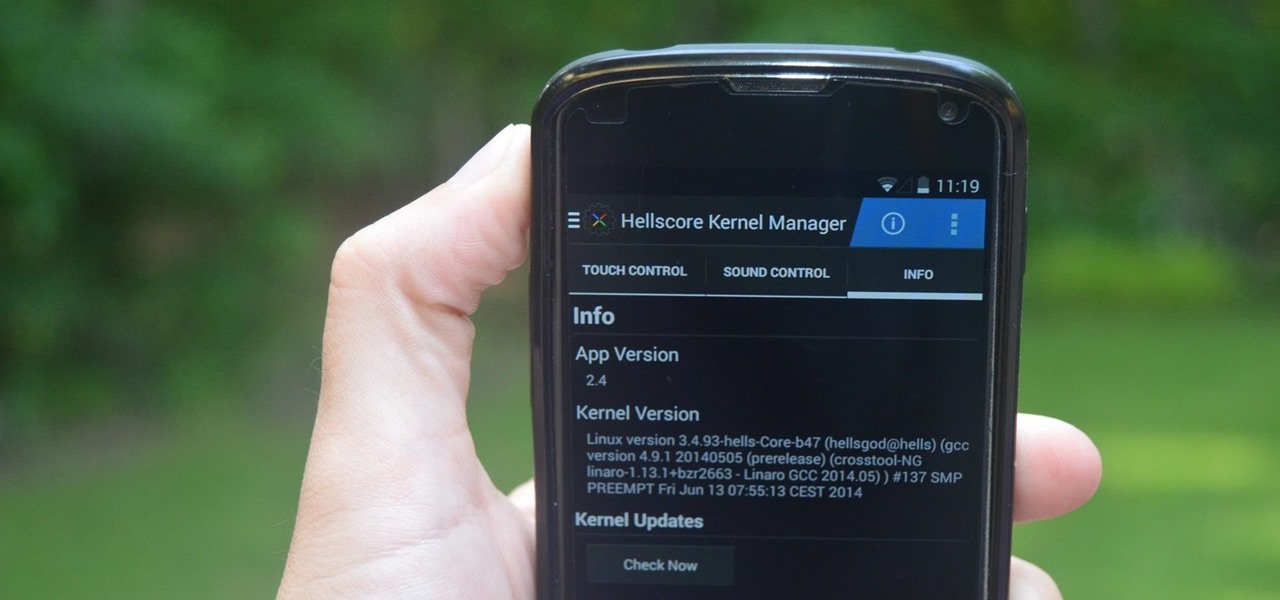
Increased battery life is easily one of the most sought after improvements to a device and often drives intrepid users to root their phones, flash new ROMs, and try out experimental kernels.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Sometimes when non-Asians go to ramen bars, they're mildly weirded out by watching the patrons eat. To the uninitiated, the eating behaviors can seem kind of extreme. Why are people hovering over their bowls like animals at a feeding trough? Why do they let endless lengths of noodles dangle from their maw as they slurp—very, very loudly—over their bowls of broth?