OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.

Phone in one pocket, wallet in the other? It's the classic combo guaranteed to give you more pocket bulge. But it's 2024. Half that stuff in your wallet is practically antique. It's time to finally ditch all the dead weight and get a MagSafe wallet for iPhone — and we've got the best picks to slim you down to the essentials.

Apple's new iOS 16 software update is finally here, and there are over 350 new features and changes for you to enjoy on your iPhone. There are major lock screen and home screen improvements, a pleasant surprise for the Contacts app, and tons of new upgrades to Safari, Mail, Messages, and more.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

In a time where we're more connected than ever, privacy and security have never been more important. Maybe you're not concerned, but I'm sure there's someone in your life who is, and shopping for them can be daunting. However, with these gifts, you can provide them the tools they need to enhance their protection.

Smartphones are vital travel companions. While you're on the go, they connect you with loved ones back home, help you find tickets and passes for tourist attractions, and make it easy to find your way through foreign roads — but even the most powerful smartphone could use help from travel accessories.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

Will the predicted apocalyptic date — December 21st, 2012 — really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyberwars, earthquakes, or aliens actually destroyed our planet — and how you might survive.

Not all work environments permit their employees to browse the web. So, whether you're updating your Facebook/Twitter status or surfing the naughtier sites, this simple How-To from Household Hacker may come in handy.

This video illustrates us how to make a compass with household items. This process is done by following steps,Step 1Take a needle and rub it to a magnet at least 10 times.Step 2Take a cup and pour water in it.Step 3Now attach the rubbed needle with a paper with the help of a tape.Step 4Put the needle in the cup and place a cellophane paper on the cup and tape it.step 5See the direction to which the needle is pointing and mark it north.Step 6Mark the opposite direction South.Step 7Mark the Eas...

Contrary to popular belief, eliminating household pests from your home can be accomplished without completely bombing your living space with a mess of toxic fumes. Whether you have annoying fruit flies in the kitchen, fleas on your beloved pet or silverfish lurking around your bathroom, it is very likely that a DIY, non-toxic and super inexpensive solution exists for your household bug problem.

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

This video will show you how to make a funky hand bound art journal using only consumer waste and unused household items for materials. Items and materials for the project include cereal boxes (as the main material), scrap papers, scrap fabrics, broken jewelry, along with whatever else you wish to use to jazz up your art journal and make it unique.

If you ever stepped in gum, this is the video for you. Learn how to take household peanut butter and remove that pesky gum from your show. eave your shoes smelling better than before and maybe make yourself a sandwich while removing gum from your shoe with peanut butter. Remove gum from your shoes with peanut butter.

Too much partying and lounging under the mid-day sun? If your attempt at a toasty caramel tan has instead resulted in a bright red sunburn, you fortunately have many common household items at your disposal to relieve the discomfort and speed up the recovery of your burnt skin.

Need to keep your favorite feline entertained at home? Using common household items lying around your bathroom or kitchen, you can craft together DIY cat toys that cost nothing to make and will provide endless entertainment for your favorite cat.

Though summer is almost over, that doesn't mean you should ever be lax when it comes to protecting your skin from sun overexposure. However, should you find yourself with red and burning skin after a last-minute weekend trip to the beach, listed below are 9 simple and cheap home remedies for relieving symptoms of sunburn.

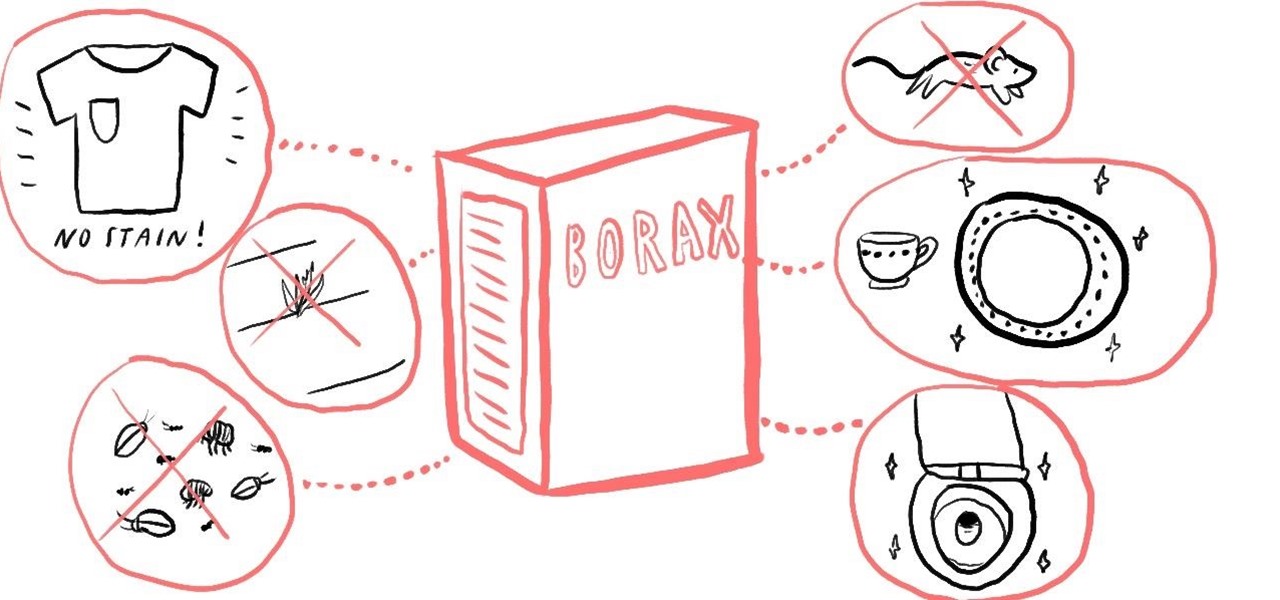
Originally discovered in dry lake beds in Tibet, borax is a mineral and a salt of boric acid, and is usually sold in white powder form in drugstores. Like baking soda, borax has many household cleaning uses, and can also be used to get rid of insects and pests from your living space.

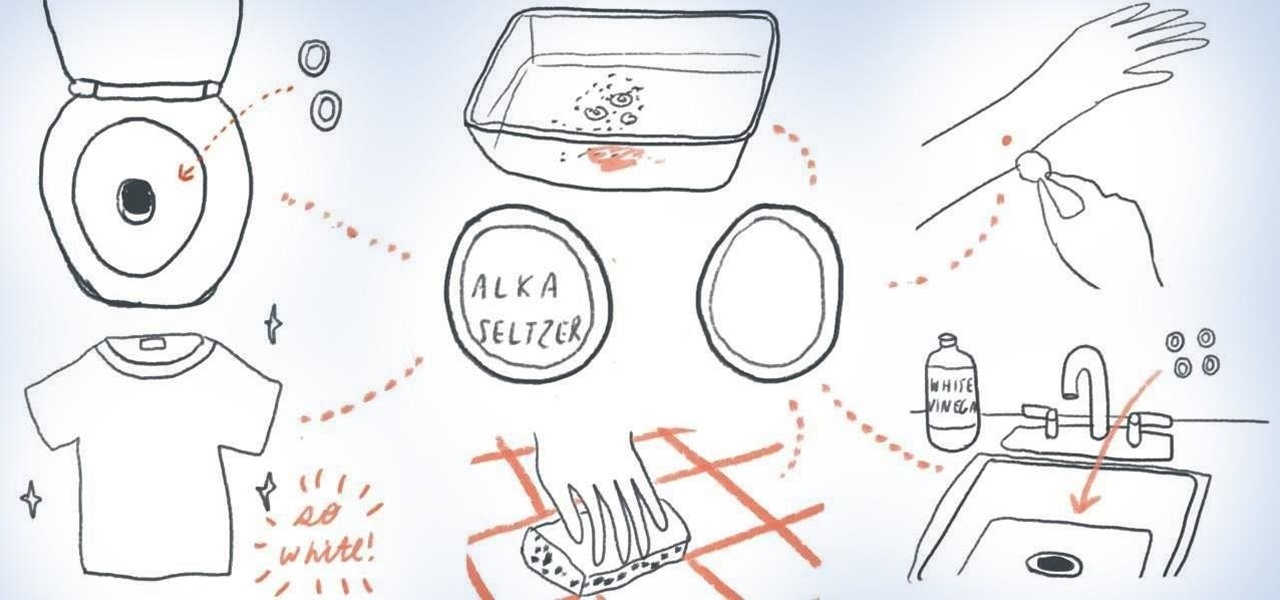
Got a clogged kitchen sink? Before you reach for the plunger, see if you can fix the problem using Alka-Seltzer tablets and white vinegar.

Want to attract more birds into your backyard for your viewing pleasure? With a simple household objects and bird seeds, you can easily turn your backyard or outdoor balcony into a bustling destination for your neighborhood birds.

Are you feeling flu-like symptoms that involve fever, headache, muscle pains, vomiting, and a skin rash? Take a glass cup and press the glass surface against your skin. If the rash doesn't fade under pressure like a normal skin rash, then you are suffering from meningitis and you need to seek medical attention right away.

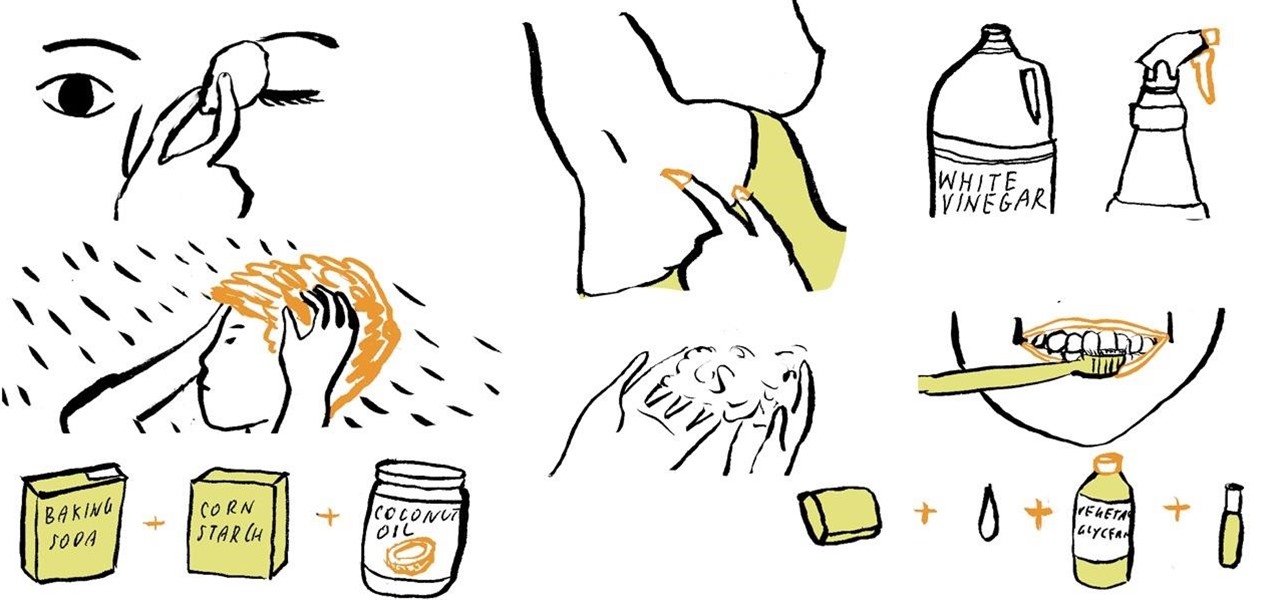
If your shoulders are starting to look like a white Christmas in the summertime, then you might have a chronic dandruff problem. Thankfully, there are numerous DIY home remedies at your disposal, which use cheap and common household products that are probably already in your kitchen or medicine cabinet.

You just ran out of shampoo, but need to give your hair a quick wash. Use baking soda! You can make an emergency shampoo paste from 1 part baking soda, 3 parts water, then work the paste into your hair, allow to sit for a few minutes, and rinse out with warm water.

It'd be a financial burden to have to buy new shoes every time a current pair gets scuffed up, but thankfully there are some easy DIY tricks for saving us that trip to the shoe store. Scuff marks can easily be remove from shoes and sneakers using common household items found in your medicine cabinet or in your desk.

Need to remove an ink stain from your carpet, clothing, wooden furniture, or new pair of jeans? Thankfully, as with most DIY stain removal techniques, you can probably concoct your own stain-removing solution from common household items in your bathroom or kitchen. Some examples include white vinegar, corn starch, toothpaste, WD-40 spray, dishwashing soap, hair spray, and even milk. Yes, milk.

Found your calling Mr. Locksmith? Need a fresh set of lock picking tools? Using household items, this conning how-to video will show you how to make lock picking tools from scratch. Follow along and learn how easy it is to create lock picking tools to be a regular old con artist. Make lock picking tools.

This video provides information on how a hacker can find an vulnerability on a remote computer and exploit it to gain remote access. Also, the video shows how a hacker can raise their privileges on the remote machine to administrator. Hack a computer for remote access.