Bleach is a great product for getting rid of tough stains and disinfecting areas around the house, but the amount of harmful chemicals these products have inside of them is extremely high, as you can probably tell by reading the MSDS for the Clorox brand.
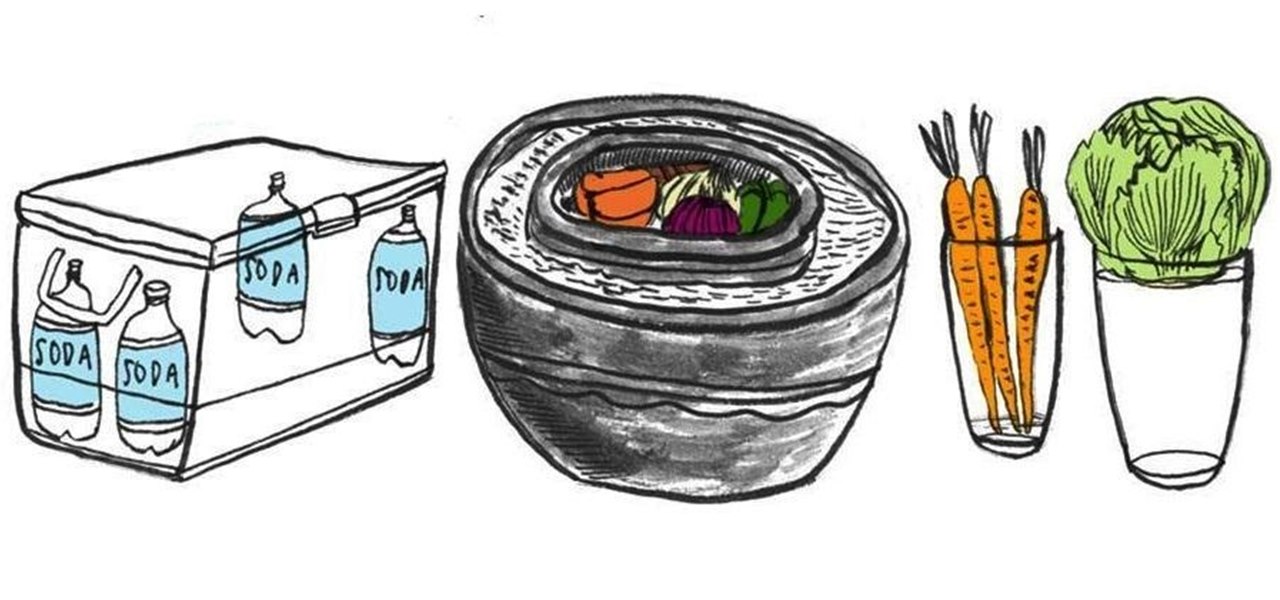
Believe it or not, it is absolutely possible to get by without a big refrigerator in your kitchen. After all, before refrigerators became a household staple in the last century, people somehow managed to store their perishable fruits, vegetables, legumes and meats for an extended period of time with ice boxes, root cellars, evaporative cooling pots, preserving, canning and more.

Are you in dire need of some visual eye candy? Dazzle your eyes by building your own kaleidoscope with a sheet of foldable plastic, common household items and whatever small and sparkly things you can get your hands on.

Tom Friedman. One of my very favorite contemporary artists. Friedman injects the wonder into the humdrum. He creates magic from the unsuspected with his incredible sculptures assembled from simple, everyday materials. His materials have included: toilet paper, drinking straws, construction paper, masking tape, toothpicks, bubblegum, spaghetti, toothpaste, soap powder, sugar cubes.

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut down some of the games that offer web users a giant share of their online fun. World of Warcraft, League of Legends, EVE Online, and Bethesda Softworks have all been targeted by LulzSec's hacking efforts in the last week,...
Scroogle was shut down this month due to " a combination of throttling of search requests by Google and a denial-of-service attack by an unknown person or group."

A hacker from Anonymous broke off communication with an FBI agent posing as a Symanec employee after being offered $50,000 to not publish the Symantec pcAnywhere code online. And in a not surprising turn of events... the code was released today on peer-to-peer networks.

Know how some people have a natural way of lighting up a room? Well, hacker i-am-jen has an artificial one—LED sneakers! Powered by a pair of 6-volt batteries and two teeny-tiny RBBB Arduino microcontrollers, the shoes offer a high-tech, DIY spin on the mass-market L.A. Lights of yesteryear: Interested in kickstarting your own LED shoe project? You'll find Jen's step-by-step here.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

The multi-talented Amy Sedaris (creator and star of TV show Strangers With Candy) has a new gut-busting venture, now available in bookstores near you. Simple Times: Crafts For Poor People is a tongue-in-cheek DIY guide to projects like seashell toilet seat covers and ringworm pompons. In a recent interview with NPR, a couple statements rubbed some DIYers the wrong way (ahem, ugly people are doing crafts; pretty people are having sex). Or perhaps this didn't sit well:

Been hacked once? Twice? Maybe more? You thought abc123 was the only password that is both 6 characters wide and easy to remember? I have some suggestions in store for you. Just read on...

Welcome to the sixth Community Byte for coding in Python and beating the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the fifth Community Byte for coding in Python and beating the challenges given to us from HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers—even people that are nearly computer illiterate.

Many FarmVille farmers want money fast, or experience fast, or want to level up, or want to speed things up— make and earn things faster. No matter how long they play, they're not getting what they want, and that is to outshine everybody else. But you can't reach the top by simply playing the game.

Last Friday's mission was to accomplish solving HackThisSite, basic mission 10. This mission teaches us how to use JavaScript to manipulate cookies on poorly coded cookie-based authorization.

Friday's mission was to accomplish solving HackThisSite, basic mission 7, which required us to learn some basic Unix commands. If you have any prior experience using Unix commands, this should be a breeze for you if you sit and think for a second.

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...

It's remarkable that a gaming device (from Microsoft, no less) designed for geeky gamers has incited broad innovation in medicine and robotics. But that Kinect has captured the imagination of hackers-with-MBAs-in-mind is downright amazing.

In the far away land of Japan, gold is out, glow-in-the-dark is in. LED "grills" were recently conceived of by two Japanese designers/hackers for a winter advertising event at clothing store Laforet Harajuku. The LED teeth attachments quickly became a hot item. Foreseeably, one of the two designers demonstrating the teeth in the video above is the familiar Daito Manabe (our favorite "self-electrocuting" mad hacker). Manabe's partner, Motoi Ishibashi, came up with the idea when "he saw a video...

A diamond ring is probably one of your most prized possessions. Like most possessions, it requires care to keep it as good as new. Learn how to clean a diamond ring with the folks from Martha Stewart's REAL SIMPLE. Diamonds are made to shine! But daily wearing can result in a less-than-sparkling stone. There's no need for a professional cleaning: Polish your gem at home using common household products.

Learn how to polish silver with the folks from Martha Stewart's REAL SIMPLE. Beautiful silver pieces shouldn't languish at the back of a shelf. Removing tarnish might seem like a time-consuming task, but some simple household products make for an easy clean? no backbreaking scrubbing required. Watch this how to video for tips on polishing your silver. Take care of your silver, so you can pass it down for generations to come.

If you're a musician in need of some lessons, there's no better way to learn than with MusicRadar's so-called "Tuition" instructions. Although the title tuition is misleading, this video class is anything but costly, because it's free, right here. Whether you're looking for help with your voice, bass, electric guitar, drums, guitar effects, piano, Logic Pro or production techniques, Music Radar is here to show you the way.

THC-Hydra is a remote dictionary attack tool from The Hacker?s Choice group. It?s a well made tool that supports a lot of protocols and options. The following protocols are supported: TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, SMB, SMBNT, MS-SQL, MYSQL, REXEC, RSH, RLOGIN, CVS, SNMP, SMTP-AUTH, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS, ICQ, SAP/R3, LDAP2, LDAP3, Postgres, Teamspeak, Cisco auth, Cisco enable, LDAP2, Cisco AAA. Audit remote password using THC-Hydra.

Working from home is already challenging. Add the threat of a cyberattack into the mix, and the situation gets even hairier.

Charlie Miller and Chris Valasek conducted an experiment earlier this month that ended up with a Jeep in a ditch, although the driver didn't drive it there. The two remotely hijacked the car, controlling it through a laptop and a cell phone. FCA says vehicles from the 2013 and 2014 model years with 8.4-inch touchscreen are affected. That includes Ram pickup trucks, the Dodge Durango, the Jeep Grand Cherokee and the Viper. Some 2015 Chrysler 200 sedans are also affected.

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?

What if your fridge knew your food and expiration dates? What if your fridge could tell you which ingredients are missing and where you can get them the cheapest?

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

One of the most simple and cost effective ways to liven up your landscaping is through subtle illumination. Low voltage lighting is simple to install and offers many benefits including ambiance, safety and security. They can be used to illuminate a walkway or to lighten up your home's street address at night. Today's manufacturers are making low-voltage lighting products geared for the do-it-yourselfer, which makes purchasing and installation easier. These low-voltage kits come with a transfo...

One of the most simple and cost effective ways to liven up your landscaping is through subtle illumination. Low voltage lighting is simple to install and offers many benefits including ambiance, safety and security. They can be used to illuminate a walkway or to lighten up your home's street address at night. Today's manufacturers are making low-voltage lighting products geared for the do-it-yourselfer, which makes purchasing and installation easier. These low-voltage kits come with a transfo...
Fort Leonard Wood Public Affairs director Tiffany Wood has provided the first official response to the shocking U.S. Army document that outlines the implementation of re-education camps, admitting that the manual was “not intended for public release” and claiming that its provisions only apply outside the United States, a contention completely disproved by the language contained in the document itself.

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Null Byte is looking for forum moderators! Welcome to the ninth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

Want to keep an eye on your home while on vacation? Terrorize your family pet while at work? A homespun telepresence robot might be just the ticket! Luckily, thanks to shrinking hardware costs and the efforts of renowned hardware hacker Johnny Chung Lee, building a physical avatar has never been easier! Lee's robot has two important parts: an iRobot Create and a lightweight netbook running Skype. Notable extras include a wide-angle lens and a plastic stand to raise the computer to tabletop he...