Have a hard-to-open jar? If it's never been opened, the air pressure inside the jar is making it harder to break the seal. If it's been in the fridge, it's possible that the lid shrunk slightly—just enough to be extremely frustrating.
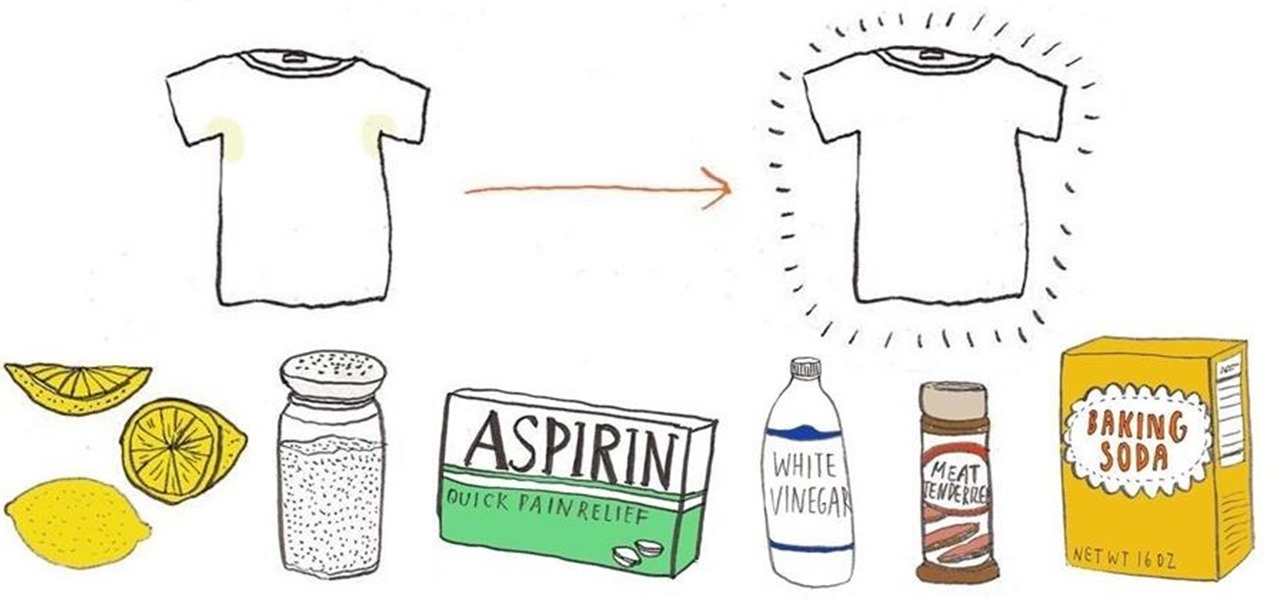
Got a bad sweat stain on the underarms of your light-colored clothing? You probably have something in your kitchen or medicine cabinet that will help get rid of the stain immediately. Aspirin, table salt, lemon juice, white vinegar, baking soda, and even meat tenderizer (make sure it is unseasoned!) are some of the many common household ingredients you can use to make your sweaty clothes look brand new again.

Turning your abode into a haunted house of horror for Halloween takes a lot of time and work. Finding ways to build props on your own can save you some money that's better spent elsewhere.
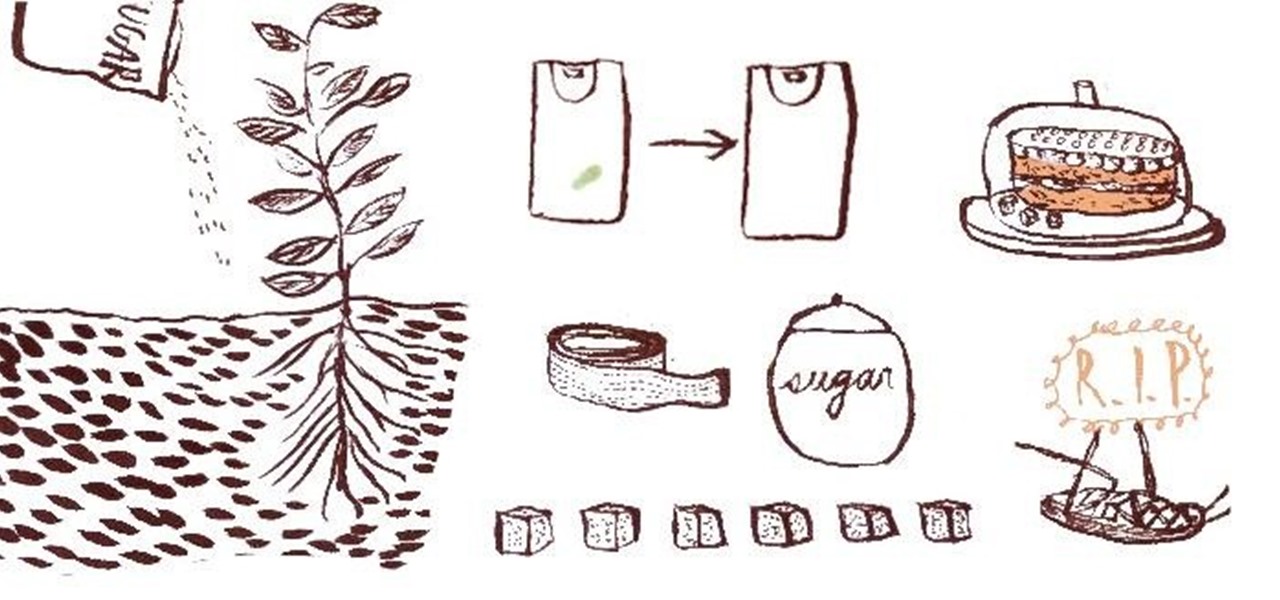
If you are cutting down on sugar and don't know what to do with the excess box of sweet stuff taking up space in your pantry, you are in luck—sugar is another one of those super-common household items that has many practical, non-edible uses around the home and garden.

Learning Style What kind of learner are you? There are three different ways people learn:

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

A few quick and easy jobs could add hundreds of pounds to your car’s value before selling. Watch TV’s used car expert Jason Dawe show you how to prepare your car before selling.

How to... Remove A Very Tight Lid? Use Items You Have Around The House! Step 1Want to remove a very tight lid? Do you have a weak grip or arthritic pain in your hands? Have you already tried tapping the lid with a spoon? Thumping the bottom of the jar with the palm of your hand, and it still won‘t come off? An easy, quick way to remove a very tight lid is to put on rubber gloves! Yes. Ordinary household rubber gloves. Hold the jar in one hand, then use the other hand to twist the lid off. Thi...

Can you guess which household liquids sink and which ones float? Play along with the A-TV science team in this video lesson!

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

A butcher block table (or counter) is a solid, wooden table. Originating in butcher shops (hence the name), this has become a popular household item. Butcher block tables and counters are durable and attractive looking. The downside of butcher block is that the wood is so porous it can stain easily. Butcher block can be sanded and refinished to get rid of stains, but that drastic step isn't always necessary.

take any household item, take a downhill drag race, snow or dirt.... and race them, from fridges to sofas and sinks... have a downhill race... loser must eat yellow snow or hit with a piss filled water balloon

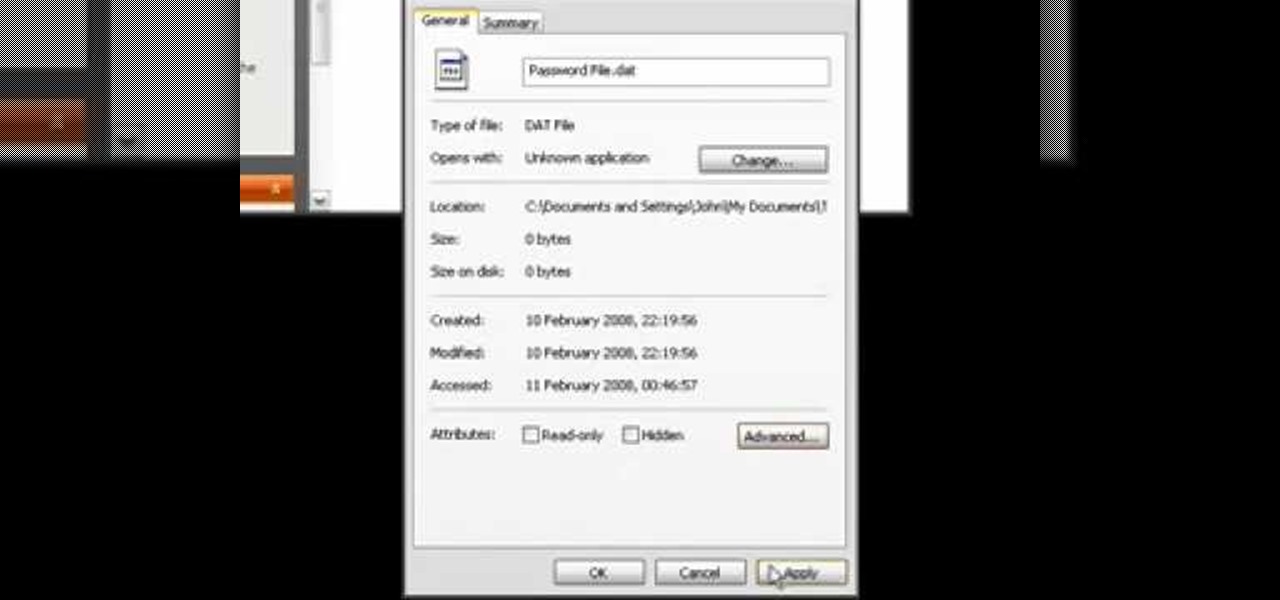
If you have files on your PC that you don't want other window's accounts to be able to access, you can encrypt them. Right click the file that you want to encrypt and select properties from the drop down menu. Once the properties page comes up, choose advanced. Now choose Encrypt contents to secure data and click ok. Now you click on apply. Select encrypt the file only and click ok. Hackers and administrators will not get an access denied message when they try to open the file. To make things...

There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer security, networking, software development, testing, and so on...It's probably a bit premature to decide what you want your speciality to be, but keeping the question in the back of your mind will help give you direction in ...

This article will be about setting up a static IP (Internet Protocol) address in Windows Seven. To see whether you should set one up, ask yourself the following: Do I have many computers in the house hold? Do I get connection issues often? Did you answer yes to both? Then you should set one up.

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

What is Google Dorking? Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly by using specific search criteria that should yeild results, should it find matches to known mistakes/errors in a website or webserver.

Another Community Byte announcement from Null Byte! The Community Byte projects serve to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you. In our sessions, we have started to both code and complete HTS missions. There is something for everyone here, so make sure you join in on the fun learning experience.

Studio Ghibli is the most well known anime feature film studio in the world. For over 26 years, their films have represented the peak of mainstream anime, and since Disney began distributing their films in America back in 1997, they've become a household name here in the States—not just in Japan. In 2001, they even bested Disney and Pixar, taking home a Best Animated Feature Film Academy Award for Spirited Away. Eight years later, Ghibli and Fukuoka-based developer Level-5 announced that they...

Looking to go "Green" When I'm looking to do new remodeling projects around the house, I find myself asking, is this Eco-Friendly? Is this main stream America brain-washing me into a "Greener Tomorrow?" I doubt it! Embracing Eco-minded products is not just good for preserving the natural environment, but it's about creating a healthy living environment in your home as well.

Apartment Therapy posts a simple household hack on removing a stripped screw without an extractor. For all our WonderHowTo Home & Garden DIYers, you never know when you might accidentally strip a screw clean. Here's how to remedy the problem.

ZERO WASTE. Yes, You read that right. This kitchen of the future aims to have zero waste. Ekokook the kitchen concept out of design company Faltazi gives us hope for a greener future. How is this possible you ask when in most homes 85 or 90 percent of a family's trash is generated in the vicinity of the kitchen? Ekokooks kitchen system is divided up into disposing and storing your waste in three mechanized sectioned systems Solid Waste, Liquid Waste and Organic Waste. Solid Waste- The solid w...

If you've ever jailbroken an iPhone, iPad or iPod Touch, then you're probably already well acquainted with PwnageTool. What you may not know, however, is that, thanks to the efforts of an iPhone hacker named Johnny Franks, there now exists a PwnageTool bundle for the beta version of iOS 4.3, iOS 4.3b1.

Hello, fellow Null Byters. Today, with mixed feelings, I want to let you know that this is my last official post as the admin of Null Byte. I've come to the decision that I need to spend more time focusing on my studies. Over the past 5 months, I have enjoyed building this community and teaching people unorthodox methods of doing things, creating things, and hacking them. But I'm also excited to be delving deeper into the studies that brought me here in the first place.

Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."

Without Much Delay: The Below Videos Are Awesome! 'Nuff Said.

Have you ever wondered how to create an invisible folder? I mean an invisible folder, not a hidden folder. Nowadays, we are facing lots and lots of problems requiring us to keep our data safe and secure. There are millions of hackers all around the world that are trying to steal our information whenever we get onto the internet. Even some of our friends are trying to lay their hands on our personal and confidential information.

Merry Christmas all! I hope you are all having a very wonderful day!

Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites.

Google+ isn't filled with just Google workers and tech-obsessed nerds. Many creative people are part of the community, and they're using Google+ to connect with their fans. Authors, especially, love talking to people about their work. We've rounded up the best published authors for you to follow on Google+. We've listed their best known works so that you can get an idea of the topics they write about.

A few months ago, we showed you a pretty awesome light painting project that visually captured invisible Wi-Fi signals around town using a Wi-Fi detecting rod filled with 80 LEDs. With some long exposure photography, the results were pretty amazing. This project was inspired by those crazy Norwegians, but this build lets you do something even more amazing—capture pictures of colorful written text and drawn images, frozen in midair.

Smartphones are impressive devices, to say the least. A smartphone user can consume TV, music & movies; communicate via streaming video; check the weather; record audio; take professional quality video footage; snap high quality photos… The list just continues to grow and grow. With all of these incredible capabilities, why not add surveillance?

Meet DareDroid: sexy nurse, geek couture and mobile bartender, engineered into an all-in-one technologically advanced garment. Created by fashion designer Anouk Wipprecht, hacker Marius Kintel, and sculptor Jane Tingley, the team calls themselves the Modern Nomads (MoNo), and their series of garments fall into Wipprecht's invented family of "Pseudomorphs". Pseudomorphs are tech-couture pieces that transform into fluid displays—which is exactly what DareDroid does.