Have you been sharing your Netflix password with your friends? How about Rhapsody or Hulu Plus? If you get caught sharing your online subscription accounts, you could be slapped with a fine and even imprisoned.
Nintendo's Wii Remote came close, but never has a video game peripheral garnered such adoration from the hacker community than the Kinect.

Meet Newstweek, a hidden device engineered to hack news items being read at public WiFi hotspots (cafes, libraries, airports, etc.). Both nefarious and tech-saavy, the ingenious mechanism wasn't fathered by a group of web hackers, but rather a pair of Berlin artists, Julian Oliver and Danja Vasiliev. The duo are interested in exploiting the "trustworthiness" of big media outlets in order to demonstrate the vulnerability of relying on just a few dominant networks.

According to PlayStation Network @ Home, a new app may allow hackers to ban or unban anyone they please from PSN.

Every key on a telephone keypad has its own sonic signature, a sort of calling card composed of two distinct tones: one high, one low. While it's easy to tell the difference between the individual pitches in a single row—see, for example, this article on using your cell phone as a musical instrument—, it's often difficult to differentiate between notes within the same column. Unless, of course, you outsource the work to a computer! Which is what Uruguayan hacker [Charlie X-Ray] recently set o...

Turkey's been consumed, you've awakened from the food coma, and you've escaped the madness of Black Friday. Isn't it about time you tackle a new project? We've got some great new projects for you to help illuminate the darkness of winter.

The Kinect is sure to swarm the homes of Xbox 360 gamers this holiday season. Even though some of us are amazed at the hands-free gaming capabilities it offers, others feel it to be frustratingly limited. Adafruit Industries is one of them.

Ever been warned that sitting too close to the TV might damage your eyesight? It won't. That probably won't stop this electronic View-Master from giving your poor mother a heart attack, however.

MacGyver. How can he not be a WonderHowTo hero?

Applications are finally beginning to make use of Android 6.0's fingerprint authentication, letting users access sensitive information without having to enter (or unsafely store) complicated passwords on their phones.

People have asked: "Here is an IP address. Can you hack this? Can you hack me right now?" Hacking takes time and skill. You can't just get an IP or an email and hack it in ten minutes unless the password is 1234.

As you all know, the first Null Byte Technical Excellence Tutorial Contest ends this coming Monday, Feb. 15, 2016. If you are working on another great article or your first article, try to complete it and submit it before midnight Pacific Standard Time (PST) to be considered in this contest. The winner of this contest will not only receive a certificate verifying the technical excellence of their tutorial, but they will also receive a free copy of the Professional version of the Exploit Pack ...

Hello to you all I've been reading for a long time now and haven't seen anything about this vulnerability so i thought id post it to make sure it was here
In this tutorial we will be go over how we can make use of conditionals. In Perl the main conditional is the if statement. The if statement in

Hi Guys, I just decided to throw this out here for anyone who might not be familiar with the utility or would like to do some reading on it.
Hello, Hackers/Viewers, Today's topic is going to be based on how to disable autorun for Removable Disks and Drives. Doing that is very easy, i you read the below!

Welcome, my aspiring hackers! In this tutorial I'm gonna be showing you how to hack Wi-Fi using the wps compatibility of a router, in , of course, Kali. First, fire up Kali.

Hi there, nullbytes! I've been recently using NullByte as my only source of learning (almost) and it has proven to be really good to me.

Welcome back Hackers! We have embed a Backdoor in to a PDF file,Android package File.

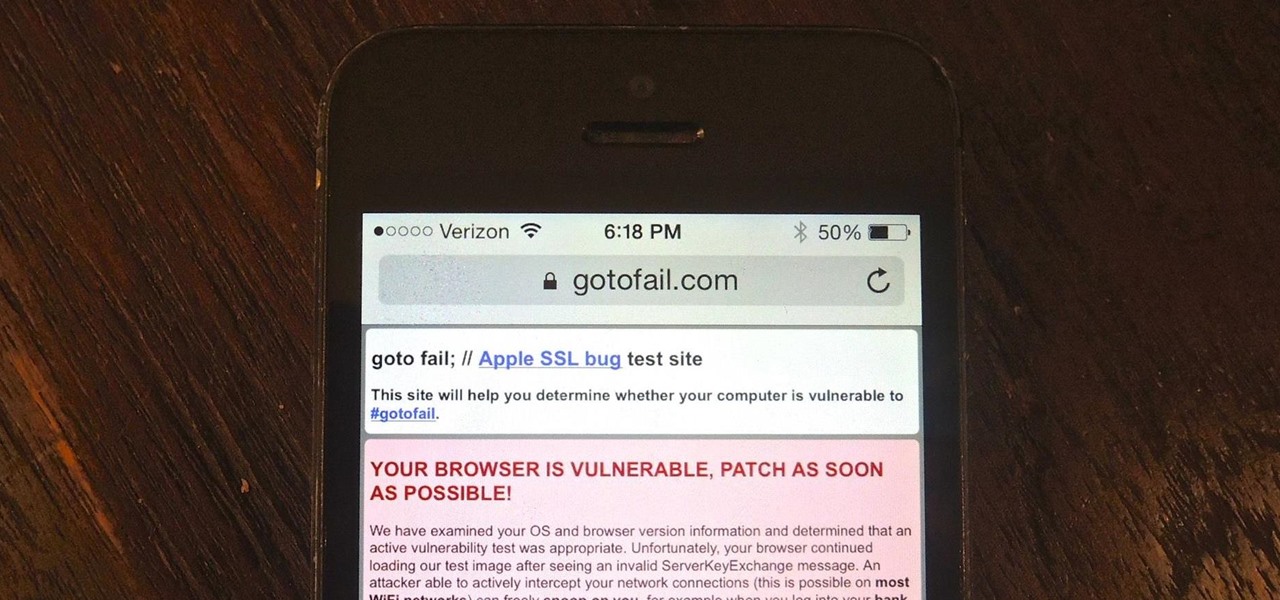
Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions.

Most of us love Ikea because it is cheap, contemporary design-conscious, and the megastore's cafeteria serves 15 delicious Swedish meatballs for the low price of $4.99.

UGC beauty How-To video is a true YouTube phenomenon. Considering the internet's tendency toward the male bias, the complete domination of beauty in YouTube's How To & Style section is noteworthy.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

Since the rise of private property and industrial production, modern capitalism has been on a undeniable crash course with Mother Nature. It's no so much that we'll end up murdering the entire planet, but just that the planet will quietly smother us with a pillow of famine, heat, cold and hurricanes. We over-farm land and replace the nutrients in the soil with oil. To package our oil-based produce, we wrap them in synthetic oil-based plastics, soon to be discarded in a trash heap or ocean.

Glass is one of the least reactive substances known to chemistry. It is the standard container material for almost all lab chemicals because it's so inert. But there are a couple of substances that have strong reactions with glass. Sodium hydroxide, aka solid drain cleaner or lye, can easily be stored in glass as a solid, but when molten, it reacts violently with glass and can actually dissolve it away! So, the next time you clog up your drains with broken glass beakers and flasks, rest assur...

If you're on a tight budget for food, whether you're in college, or someone just starting out living on their own, you're probably low on money and sick of ramen noodles. Don't get me wrong, ramen can be tasty and filling, and there is almost nothing cheaper.

Aside from food, oxygen, sunlight and water, there are other necessities that humans arguably need today to survive—clothing, love and shelter among them. Almost everyone wears clothes, needs somebody (or something) to love and a place to call home. And what's the one thing that connects all three? Something we all have? Keys.

There are a few different types of Apple iPhone and iPad users: general household users who largely consume media—e.g. surfing the web, watching movies, listening to music. Other iPhone and iPad owners use their device(s) to produce stuff—written documents, edited movies, blog posts, music tracks, and the like. And then there are those who are very mobile with their devices. They commute to and from work on a regular basis with their iPhone or iPad. Some users may travel a lot on business, or...

With over 60 commercials, chances are you've seen one of the Get a Mac spots run by Apple, which brands Mac as intuitive and hip, compared to their boring and clunky PC counterpart. You also probably saw Microsoft's response in their I'm a PC campaign. But who are Mac and PC users really? Do jeans and hoodie-wearing yuppies really use Macs? Are the suit-and-tie types strictly operating PCs?

Well suited for loft living, Studio Gorm's Flow Kitchen offers an extremely eco-friendly and efficient solution to all your daily actions in the kitchen. The Netherlands based design studio focuses on three major areas: Waste, Water and Energy. My favorite element? A cutting board that sits above a compost bin. Slide it forward, and sweep your scraps right into the (eco-friendly) trash.

If you have any little ones in your life (or you're simply a grown-up kid yourself), Just Bento has has posted Maki's Top 10 Bento Rules for Back-to-School. Rules listed below, click through for full explanations.

Mad Science is looking for more hackers, makers, and DIYers to participate in our community madness. If you've recently designed or made a project, we want to see it! Share with the other Mad Scientists out there by posting up a how-to of your pet project on our community corkboard, or even just a few cool, inspiring photos of the build.

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

Sometimes, paying for the whole Xbox LIVE service might seem like a waste of money. You're constantly experiencing lag, you've got people modding and cheating, kids are being loud and obnoxious over the mic, and your kill-to-death ratio is getting dumped on. Basically, the whole multiplayer experience just isn't cutting it anymore—you want to go back to the classic world of single player. Well, there's always downloadable content—simply known as DLC.

Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.

Hardware hacks are something I feel we don't get enough of at Null Byte, so today I figured I would introduce a fun one. I've always been a curious hardware hacker. Taking things apart and learning how their internals work has always been a part of my nature. Quite some years ago, my father showed me a really cool trick on how to hack normal radios to scan frequencies that are normally non-listenable. This little hack allowed us to scan frequencies belonging to law enforcement, and even frequ...

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.