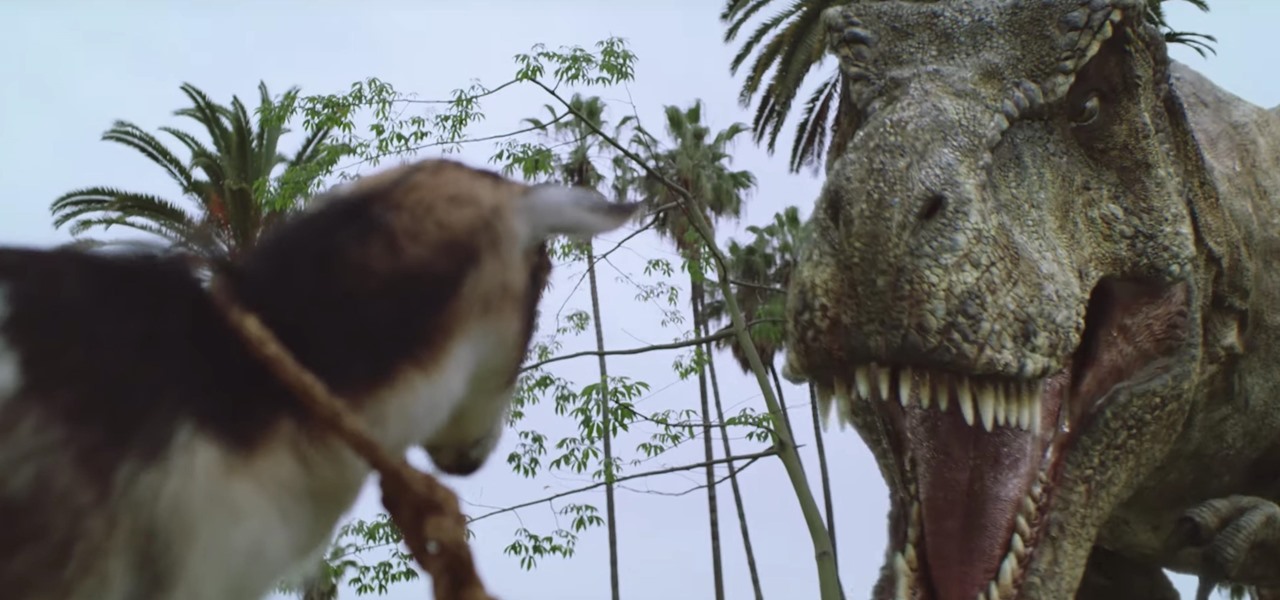This video discusses the basic steps necessary to start an online business. The first thing you need is a name for your business. Keep it simple, easy to spell and remember. Once you have your name, register it with the government. Next, find a good hosting company for your website. He recommends Godaddy.com. Also a good web designer is a necessity. They will meet with you to discuss your ideas, and your website should be ready in about a week.

Baby showers are fun ways to celebrate new mommy-hood. You won't want to forget the traditions though. Check out this video before you start planning and make sure you have an nice balance of etiquette and fun.
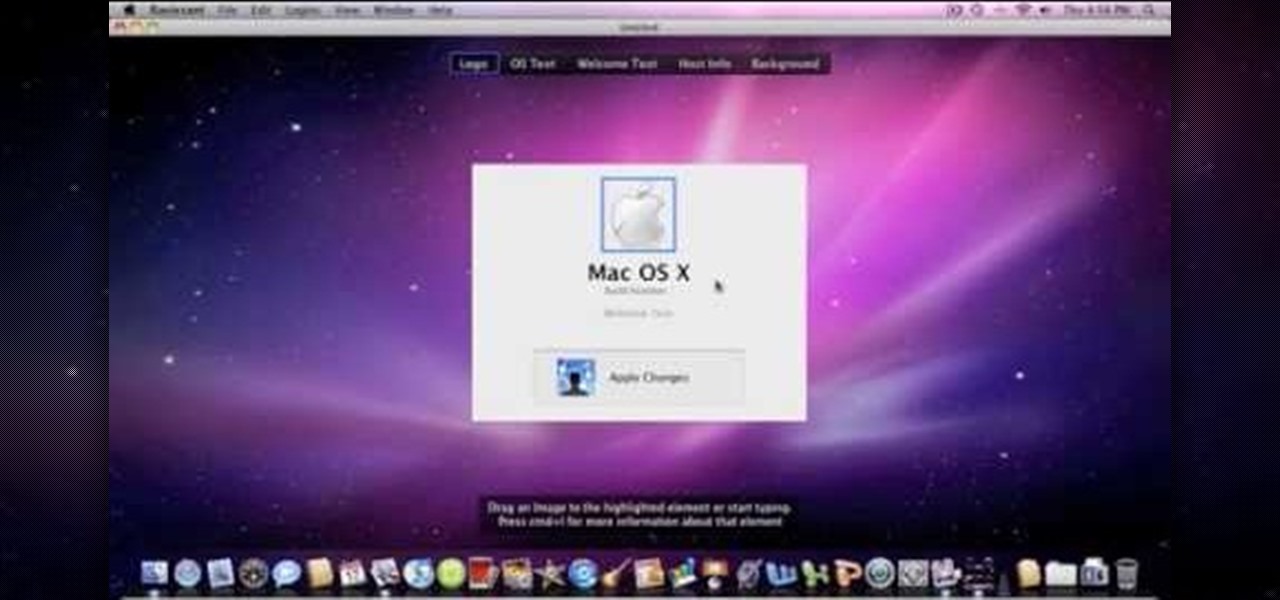
Change the Snow Leopard login screen with this video tutorial. Download and install the application Ravissant, an app that lets you customize the login screen in every aspect. Have a background image ready and an Apple logo image, if you want. Modified Apple logos can be found here , created by Evil-Slayer]. Open Ravissant, and you should see your login screen, but don't try to log-in! IMPORTANT! If you want to keep your original login screen, go to the top...
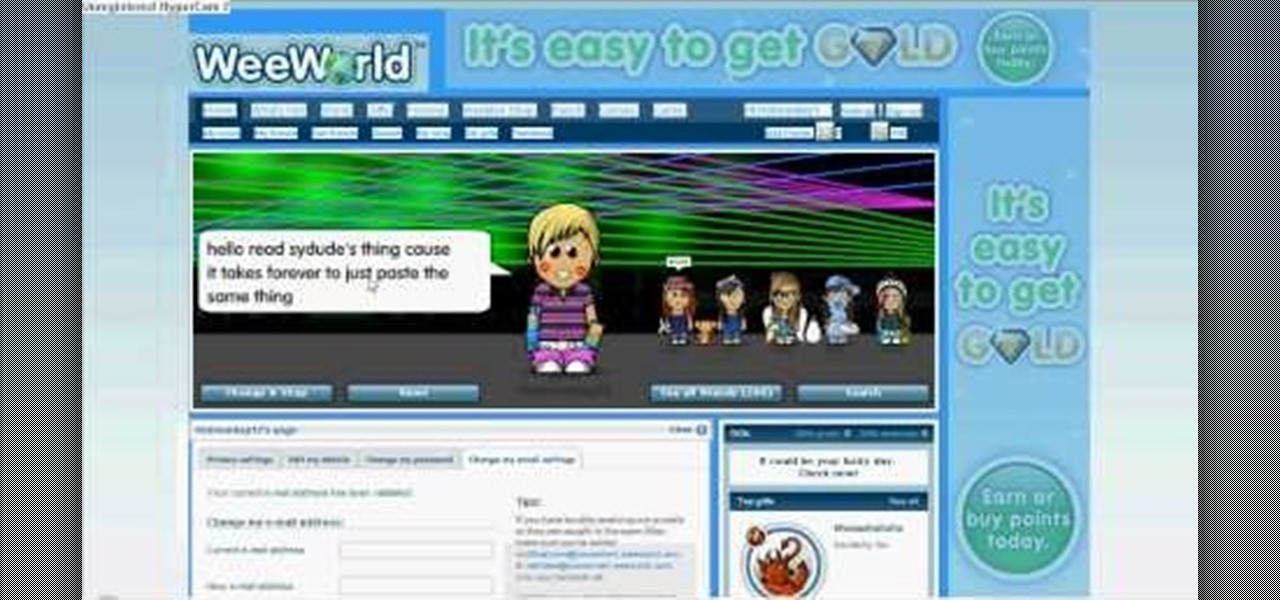
Want to know how to get free green points in WeeWorld? Sure you do. They're free! And there's 500 of them. No hacking involved, just a little trick, but you can't do it over and over again.

Not everyone in Hollywood owes their nice complexion to a dermatologist. Here are some homespun beauty secrets you can steal.

Grand Illusions is a site for the enquiring mind. This how to video demonstrates how to make Japanese origami tumblers. Your wonderful & charming host represents Grand Illusions, an amazing toy, magic & illusion web shop and gallery.

This week on Etsy How-Tuesday Kristen Couse aka cakehouse shows us how to make a decorative holiday trivet for the dining table. You can spice up your home decor, whether you're hosting Christmas or a potluck with friends!

Love to eat but can't cook? Watch this cooking how-to video tutorial to learn a quick and simple dessert. Watch as out hosts show you how to make banana's foster.

Knowing how to cut a straight line is essential for most projects. AsktheBuilder.com host Tim Carter demonstrates one technique for cutting a straight line. With his tips, you'll have no problem getting perfect cuts every time.

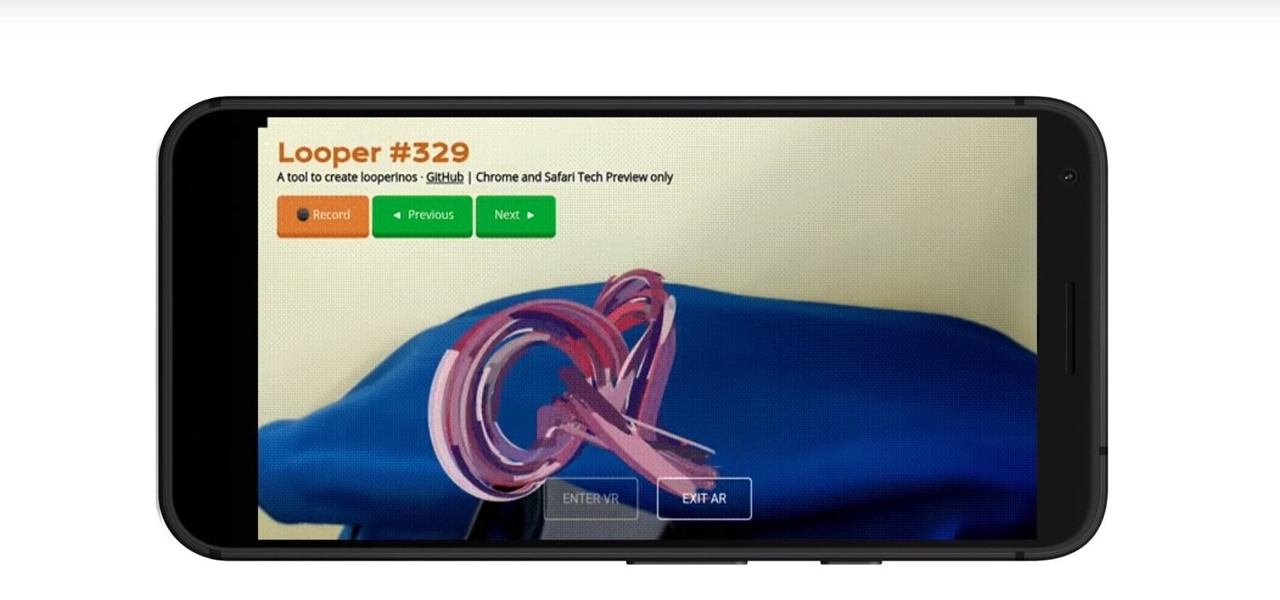
Web-based mobile augmented reality technology continues to gain momentum as Google is set to expand the standard for immersive web content to AR.

All Kohl's wants for Christmas is Snapchat augmented reality. In conjunction with a holiday pop-up hosted in New York City from Nov. 7 through Nov. 10, Snapchat ran a sponsored portal lens available to targeted Snapchat users in the AR carousel. The experience gave users the ability to virtually transport themselves to the pop-up.

Remember when typing without physical keys seemed ridiculous? Now, touch typing is the smartphone norm. That said, mistakes are inevitable on small screens. So before you start hammering on that delete key or shaking your iPhone like a madman, know that there's a better way to undo text you didn't mean to type — no shaking involved.

Players who have stuck around with location-based game Jurassic World Alive just got a new treat that makes the augmented reality experience even more fun.

One of the most prestigious annual events for the advertising industry, the Cannes Lions is the ideal backdrop for Snapchat to show the brands and agencies in attendance what it's got.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

While the 49th Annual Gay Pride Parade and Festival will take place on Santa Monica Boulevard and West Hollywood Park, revelers will also be able venture Northeast to the TCL Chinese Theater on Hollywood Boulevard to continue celebrating via Snapchat.

You already know that the best place to learn about the cutting edge of augmented reality is Next Reality, but the best event to meet the people and companies pushing the space forward is the annual Augmented Reality Expo (AWE), and we're giving away free tickets!

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

We already know that Microsoft has something big planned for later this month, and now we have details on how to watch the company's big reveal.

The mystery surrounding the release of the next version of the HoloLens has been swirling for months, but at least some of that mystery may removed in the coming weeks.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

If you've gone anywhere near a television in the US in the last 48 hours, you've probably seen some of the reports of Hurricane Florence and its devastating wind and rain making its way toward the Carolina coast.

On Friday, the release date for her new album, Queen, Nicki Minaj is already grabbing headlines for the track "Barbie Dreams," where she disses Drake and a host of other rappers.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

With the launch of the Magic Leap One looming over summer's horizon, on Wednesday, Magic Leap released an essential component that will differentiate it from current augmented reality platforms.

With a new version of its ARCore in the wild and more than 30 devices now supporting it, Google is helping beginners get up to speed with augmented reality.

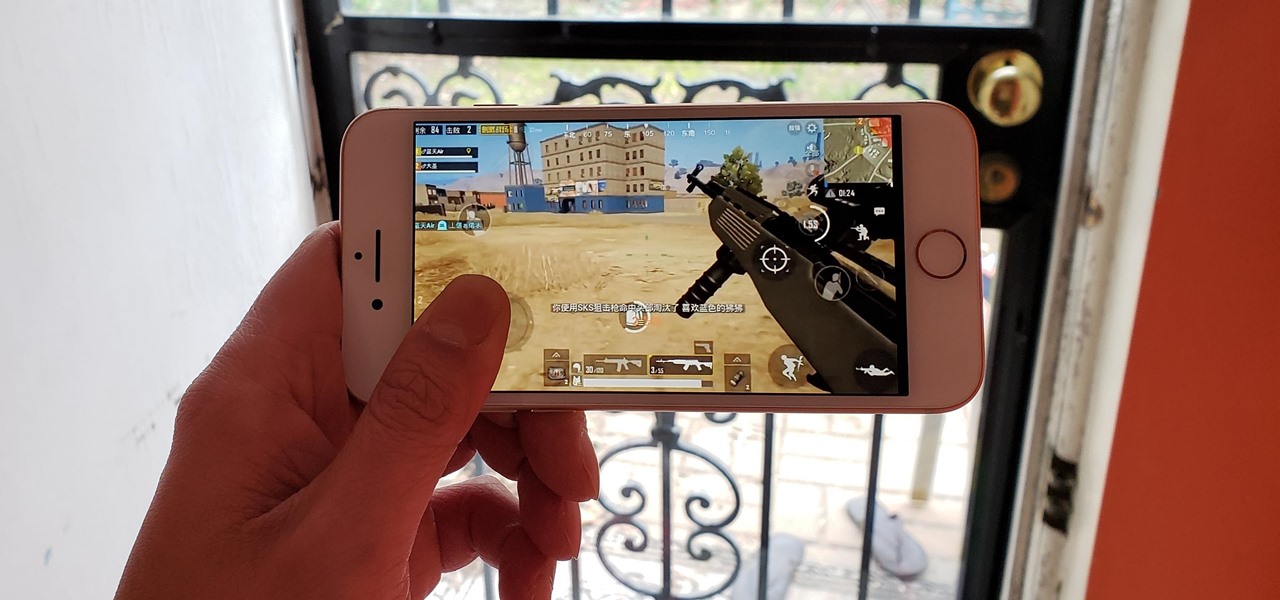
The recent 0.4.0 update for PUBG Mobile brought us a host of welcome features like the training ground and arcade mode. Sadly, one highly sought-after feature remained out of our reach: The ability to play in first person perspective, or FPP mode. Our wait may soon be over, as this gameplay mode could be out as soon as the next update hits for both Android and iOS.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

A new telemedicine application for the Microsoft HoloLens is promising paramedics and EMTs a new tool for diagnosis and treatment of patients in the field.

With just a few more days to go before its release in theaters, the Star Wars: The Last Jedi push has gone into overdrive. On Monday, Google released "The Last Jedi AR Stickers," a set of augmented reality stickers that lets users put a number of different Star Wars characters and objects into the real world.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Now, when the weather outside is frightful, Pokémon GO players can expect it to be just as unpleasant in augmented reality.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

On Oct. 19-20, the MOC Exhibition Center in Munich, Germany will play host to the Augmented World Expo (AWE) Europe 2017.

Over the weekend at IFA 2017 in Berlin, Huawei introduced the Kirin 970 processor, the first of its kind to include artificial intelligence baked into the chip.

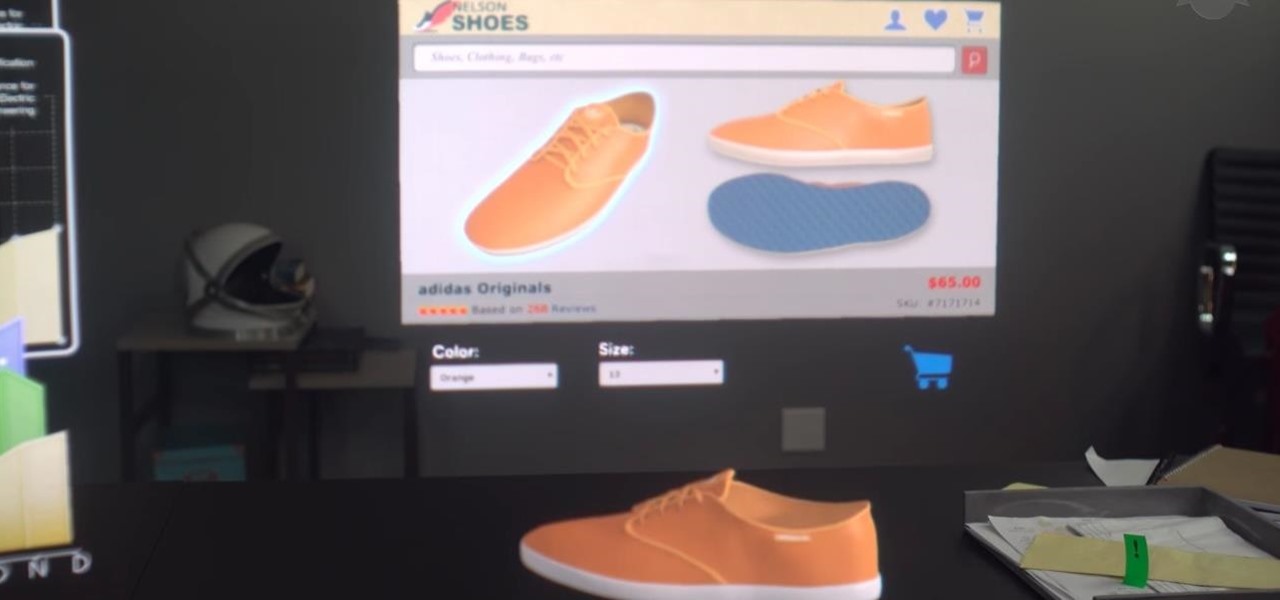
If you've ever browsed a restaurant menu and wondered what a particular dish looks like, then the augmented reality mobile app from Kabaq was made for you.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.

Single and living in NYC? Forget bars, the female-empowered dating app, Bumble, has just opened a place where you can meet up with your online lovers.

In a video released Tuesday, Microsoft arguably began to position the HoloLens and Windows Mixed Reality as the future of education. A smart tactic meant to coincide with their other education-related announcements made on the same day.

Experts from the World Health Organization just expressed concern for the rising number of measles outbreaks across Europe. Despite a perfectly capable existing vaccine, "immunization coverage has dropped below the necessary threshold of 95%," causing the measles to spread throughout the European region.