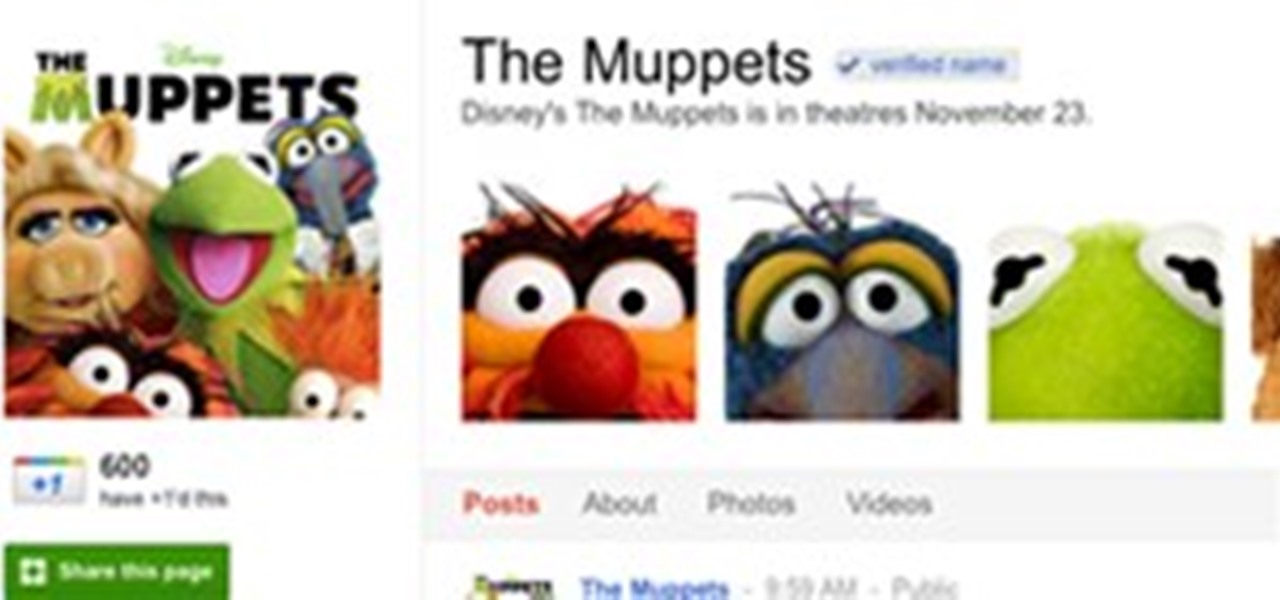
Many companies were disappointed when Google+ rolled out and banned the creation of accounts specifically for businesses and brands. Fortunately, today, Google began rolling out Google+ pages, for them to start connecting with customers and followers. For an example of what a Google+ Page looks like, check out the one for the +The Muppets:

Welcome to the second Goonight Byte! Our second coding session was kindly hosted by th3m, so props to him for letting this happen.

Our first Community Byte went well! We had around 8 people in the room coding collaboratively and watching to learn. LukeStav did the kind task of hosting it on Gobby for all of us, so big thanks to him!

Beginning this week, Null Byte will be hosting a new feature called Community Byte, a weekly coding and hacking session held in the Null Byte IRC. This is a chance for our community to do something fun, and make something awesome together!

We've all seen FOX News commentators get worked up about silly non-issues. It occurs more than we'd like, but what happened last week on popular morning show FOX and Friends was not only a misleading and pointless attack on video games, it was an unintelligible attack on a mediocre and forgotten game from 2007, along with a handful of recent indies that no FOX and Friends viewers, or any of their close family members, had ever heard of before this broadcast.

Google+ Hangouts are proving to be a proficient platform for teaching and communicating in real time with others. If you're someone who creates instructional content online, you may want to consider using the platform for your next project.

So what if he's right just 39% of the time? On Wednesday, February 2nd, when poor old Punxsutawney Phil crawls forth from his simulated tree stump in Gobbler's Knob, we'll be watching. After all, if an octopus can predict the outcome of the World Cup, we fail to see why a sedated marmot can't predict the weather.

This will show you how to host your own teamspeak server for PC games. Very simple and easy, hope you learn something from it. Host your own teamspeak server.

In this two part episode, Aharon Rabinowitz shows you how to use audio to control time. You'll learn how to make your video automatically move forward in time to the beat of the music - a technique used in tons of music videos and commercials.

This is a 3 part tutorial. Be sure to click on Chapters 2 & 3 to get the full tutorial. In Part 1 of this 3 part Adobe Illustrator tutorial series, Vincent Rosati explains how to use the free transform tool to take the first step in creating a helix with AI.

In this two part Photoshop tutorial, Richard Harrington takes a look at the camera raw files and the camera raw interface. Many video professionals do not know much about the camera raw interface because it is a technology mainly used by digital photographers. The key advantage to using with a camera raw file is that the data is usually stored in the picture more than you can normally see in a single exposure.

This is a two part video tutorial. Be sure to click on Chapters 2 as well to get the full tutorial. Taking a look at the popular technique of designing lower thirds and the process it takes to design these using Photoshop. Photoshop is the perfect solution for this task with the ability to mix text, texture, graphics and logos to create compelling titles for your show or video.

In this four part video tutorial, Creative Cow leader Carl Larsen shows you how to create a 360 degree camera-aware environment in After Effects without the use of third-party plug-ins. In part two, build a title sequence within the 360 degree environment created in part one of this tutorial series. Part 3 shows you how to track a lens flare onto the surface of a 360 degree camera-aware environment without the use of a third-party plug-in. Part 4 shows you how to track a lens flare onto a 360...

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

There are several virtual machine managers present in the market. However, the main functionality of all VMs are the same. Most people like to get free VM managers, so that they can install as many operating systems as they like over the host operating systems. One of these free VM managers is Oracle's VM VirtualBox, which can be downloaded from Oracle's website for all popular operating systems, such as Linux, Windows and Mac.

Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to install a short-throw shifter on your car properly.

If you want to catch more bass this spring, then you need to fish soft plastic jerk baits. They drive bass wild. Wade Bourne, host of Wade's World on MyOutdoorTV, shows you how to use a jerkbait stinger hook.

How many times have you been on the water and you've cast off a crankbait? You pick up the crankbait rod and make a cast, start your retrieve and your bait runs off to the side. Tuning will keep it straight. Wade Bourne, host of Wade's World on MyOutdoorTV, shows you how to tune up a crankbait.

There's no more exciting ways to fish for bass than top water. There's a big explosion with a bass hooked up. Wade Bourne, host of Wade's World on MyOutdoorTV, shows you how to use a follow-up lure when you've missed on a big bass.

Nothing is better than getting on a bream bed. You'll catch bluefish one after another. Wade Bourne, host of Wade's World on MyOutdoorTV, shows you how to fish for bluegill and panfish in bream beds.

If you like to catch big fish and small fish… anything… then the one way you'll catch anything is with the horsehead jig. Wade Bourne, host of Wade's World on MyOutdoorTV, shows you how to use the horsehead jig.

Wade Bourne, host of Wade's World Hunting at MyOutDoorTV, shows you how to create a "path of least resistance" for deer this season. Let's face it: deer can be pretty stupid. With a little leg work, you can trick your deer into going exactly where you want them. Hunting your prey will be a snap!

Today I will show you how to create a simple keylogger in Visual C# Sharp, which will start up hidden from view, and record anything the user types on the keybord, then save it into a text file. Great if you share a PC and want to track what someone else is writing.

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

Scrabble has invaded just about every medium out there. It started as a mere board game, but has since spawned numerous board game spinoffs and variations, an electronic version, mobile apps for just about anything (Android, iPhone, iPhone, iPad and Kindle), games for both PC and Facebook, and video games for handheld consoles like the Nintendo DS and Sony PSP. Heck, it's even on the PlayStation and Xbox 360 gaming consoles. And it hasn't forgotten about film. You can see Scrabble featured in...

One of the coolest things about Twitter is the fact that you can get direct access to some of your favorite celebrities, and have one-on-one conversations with them in less than 140 characters. With Google+, you can have the same advantage, but you don't need to feel constricted by the 140 character limit. Although Google+ has been weeding out fake accounts, they do not currently have a system for celebrities to verify whether their accounts are legitimate or not.

Mediocre free Flash game websites are all too common. Many of them thrive off peddling the same few popular games to fans who have slim cause to pick one over the other. They thrive off the indifference of casual gamers and an environment that does not have to stand out to survive, only appeal to the lowest common gaming denominator with tower defense clones and brightly colored Peggle knockoffs. In that context, what Nitrome is doing seems downright commendable.

Introduction to KVM KVM is a free and open-source Kernel-based Virtual Machine using the Linux kernel for virualization and is very similiar to a hypervisor like Xen or VMware's ESXi. It is based on Qemu, a processor emulator. Any virtual machine created on or working on KVM can work on Qemu also, but with a great reduction in speed.

This tutorial will walk you through the steps required to install the Ubuntu 9.10 operating system (Karmic Koala) on your computer. I have a Suzuki Kuiper 1411 HKS notebook computer with 2.1 GHz Intel Dual Core processor, 4GB RAM and 320GB hard drive. It has a dedicated 256MB Nvdia GeForce 9300M GS graphics card and 1270++MB of VRAM in SLI mode.

Hey now! Brazil, Paraguay, Chile, Argentina and Uruguay are doing very well in their respective groups. The are all expected to qualify to the final 16. In fact, they are doing better than any other continent. Europe's top flight teams are disappointing, as are the host African nations.

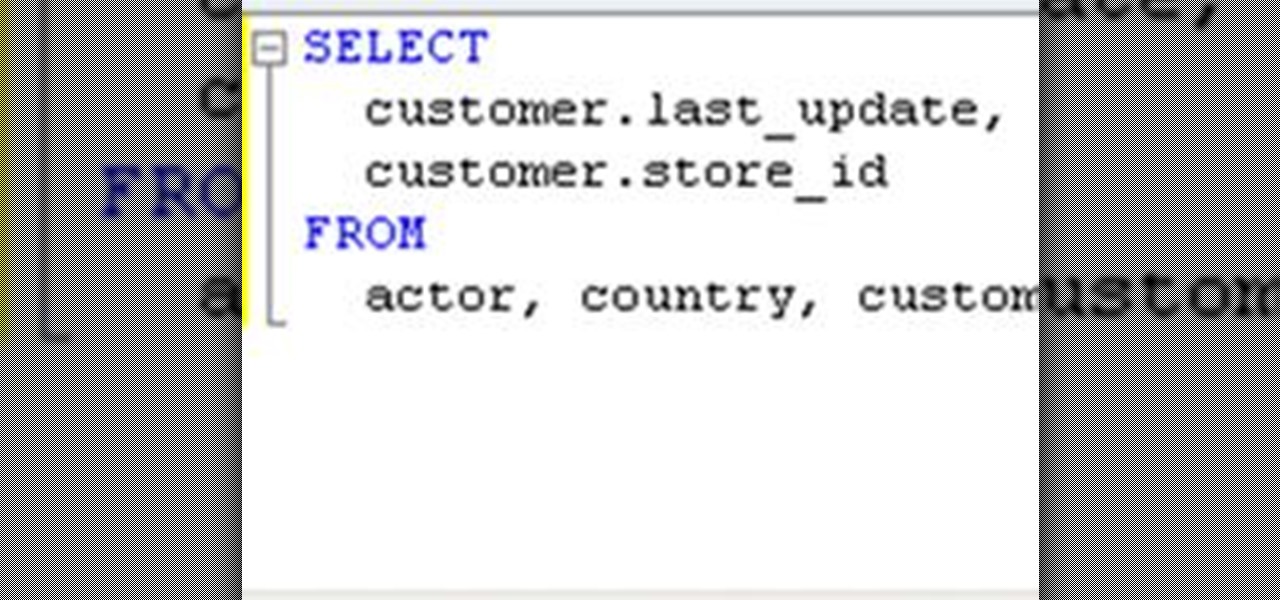
If you need to build a SQL query, you can choose one of two alternatives. The first and a rather old way is using a console. But if you build your queries in MySQL console, you have to remember all the commands and keys. This is not a convenient way, because query execution is a time-consuming process. Another way is to use some graphical interfaces for MySQL. It can fulfill many developers' requirements, including query execution.

Welcome to the Official Jackass 3D Prank Contest Submission Page Think you've got the wit and imagination to be a Jackass? Well, here's your chance. Johnny Knoxville and Jackass 3D crew are hosting the first ever Jackass 3D Prank Contest to celebrate the upcoming release of their new film, in theatres October 15th!

A whistle is really all you need to scout for for squirrels. Squirrel sure is tasty when you fry them up, or whatever, but hunting those little guys can be kind of tricky. Wade Bourne, host of Wade's World on MyOutdoorTV, shows you how to scout for whitetail deer while squirrel hunting.

April is poetry month! During April Planet Poem will host the first Planet Poem poetry competition. People will be able to post two poems to our world. Two groups of four students will vote on the winner. The grand prize winner will win a French Beret!

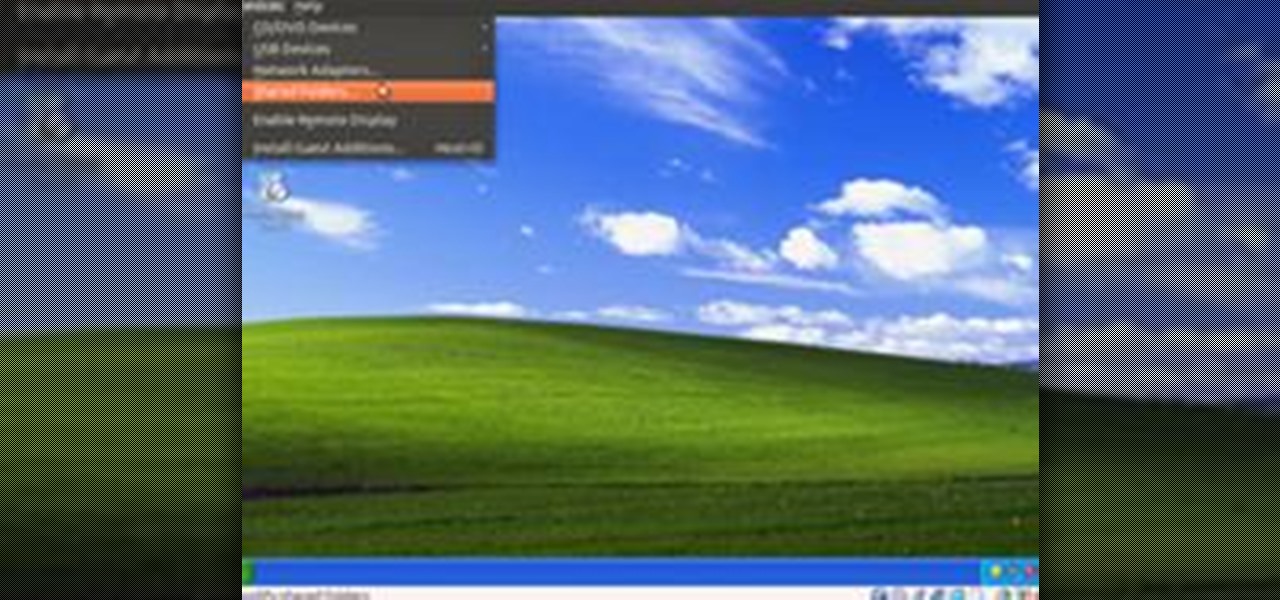
Many users of the virtualization software VirtualBox may have noticed that the USB system has been pretty buggy for quite a long time. I've had my USB randomly duck out on me way too many times to count. This can really be difficult to deal with when you require access to the devices and files from the host system.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

We've got a creative server and we're looking for players now! All slots are available! The server is set up to be the official playground for our tutorials, how-to videos, community contributions, contests, and even the occasional PvP. Whether you're interested in a place to build your personal projects or looking for tutorials and ideas, we're here to help you grow creatively.

Here is an alternative method to run Ubuntu 10.04 on a Mac without actually installing it on your internal hard disk.

Is Epic Meal Time a little too bro for you? If you're looking for something more extreme, with a hint of violence, headache-inducing screams, and endless rage, you have a couple options...