hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Video: . Optimize your Marketing with a Mobile Website

You may use Safari on your iPhone or iPad to open links and browse the web, but there's so much more it can do for you. On updated software, you can implement third-party Safari extensions in your browser that go above and beyond content blocking, sharing, and performing basic actions.
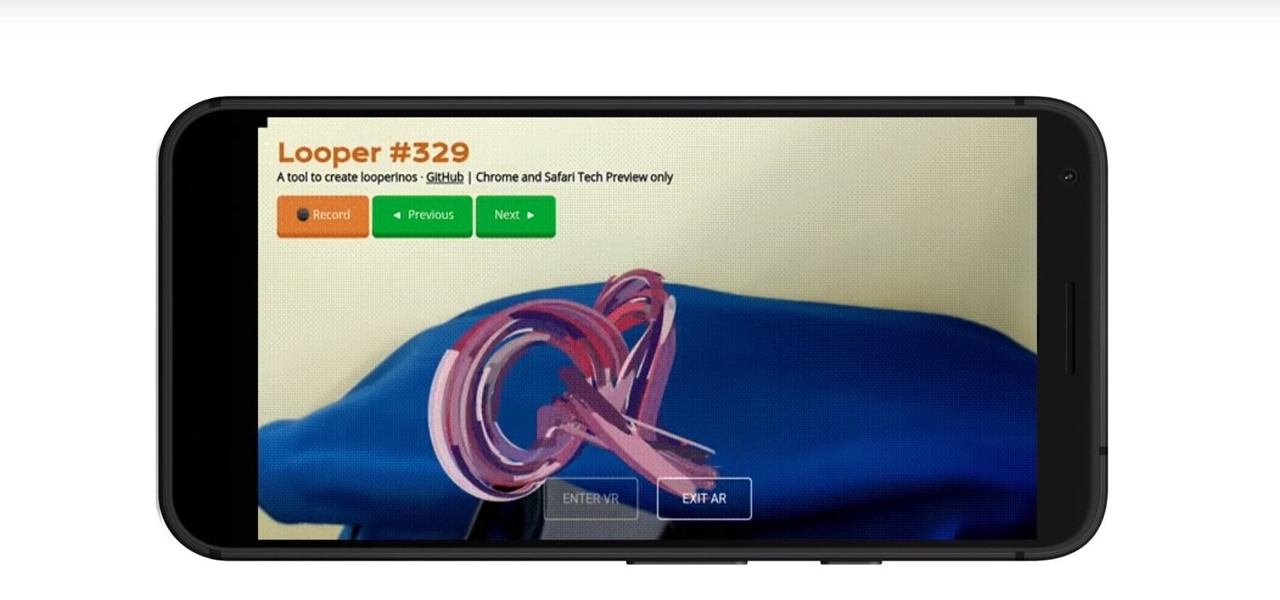
Web-based mobile augmented reality technology continues to gain momentum as Google is set to expand the standard for immersive web content to AR.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.
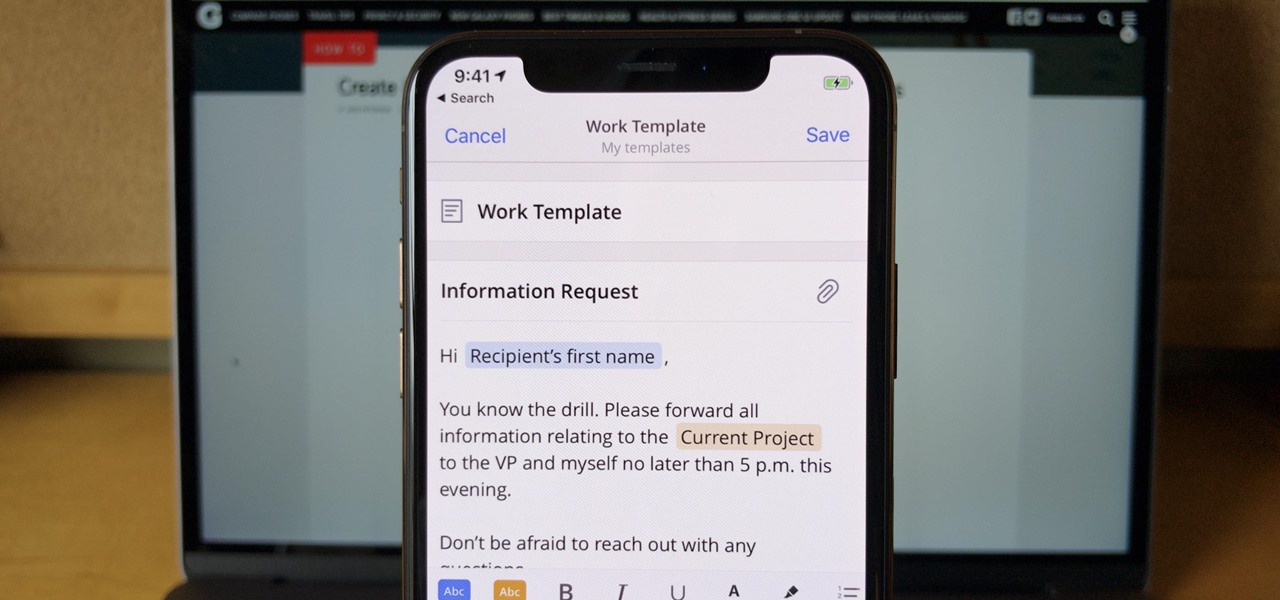
If you find yourself emailing the same email over and over again with just a few changes such as new addressees, or if you're constantly replying to messages with the same response, typing it out every time is, well, a waste of time. Spark, a third-party email client for mobile devices, takes all the work out of this — no matter which email account you need it for.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Tony Parisi, the global head of VR/AR at Unity Technologies, has been passionately working with virtual and immersive spaces for a long time. And while the internet world we live in now is very different than when Parisi was co-authoring VRML (Virtual Reality Modeling Language) — an early attempt at creating 3D environments that would work in a web browser — some of the questions that were assumed answered are being asked again.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

I recently posted a Tutorial about setting up Dendroid: http://null-byte.wonderhowto.com/how-to/setup-dendroid-android-rat-0167299/. I have worked the last 5 days on getting the Dendroid Binder, given with the Dendroid Source, working. This solution only works on Windows systems!
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

Just in time for the holiday festivities, iOS developer Tristan Kennedy has created a snowy HTML widget for your jailbroken iPhone's home screen called SnowScreen. Simply apply the widget and you'll have a falling snow animation layered over whatever wallpaper you already have. Without further adieu, let's show you how to apply this tweak.

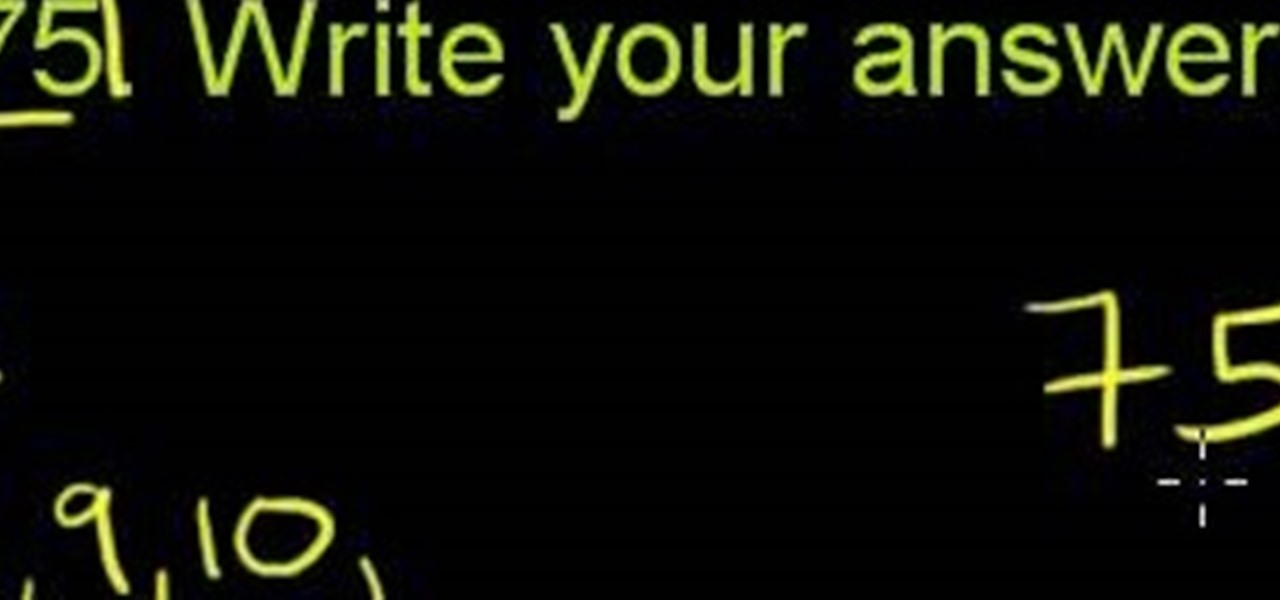
What Is Prime Factorization? Prime factorization is finding prime numbers that, when multiplied, equal the original number.

A few weeks ago, Twitter announced that they would be creating an archive feature for its members, which they've been slowly rolling out to select users. After signing in today, I noticed the feature was finally available for my account, so I went to test it out.

Samsung's Galaxy Note and Note II phablets have been hailed for their large displays and responsive systems, making them ideal for gaming and movie watching. But if you've recently upgraded to Jelly Bean (Android 4.1) from Ice Cream Sandwich (4.0), you'll be sad to know that some Android devices running Jelly Bean no longer support Adobe Flash Player.

Forgot the passwords to your email or your other favorite websites? If you typically store your passwords in Internet Explorer (IE9 or other versions) it can be tricky to get your passwords back -- but this tutorial makes it really easy!

As useful as they can be, 360-degree photos are a total pain to create. The process usually involves taking a bunch of pictures with expensive equipment or software, and not just anyone can do it. But a new iPhone app called CupChair changes everything—it lets you take 360-degree photos with nothing but your iPhone and a cup.

The latest 17.4 update for Safari includes a prompt for EU users to choose a different default web browser available in their region. It also gives us new ways to customize the Favorites Bar on an iPad. And Apple Cash virtual numbers are now supported as an AutoFill suggestion. But there are also some hidden changes in Safari 17.4 for iOS and iPadOS that you might not ever notice unless you keep reading.

Ads aren't the only annoying part of navigating websites in Safari. Colorful banners, autoplaying videos, embedded objects, and other distracting elements can make it harder to read or watch what you want. Although ad blockers are one answer, they only get rid of advertisements, so you'll need something else to remove other irritating elements from your favorite websites.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

It's no secret that Apple's Notes app supports attachments such as photos, videos, and web links, as well as other file types like PDFs, word documents, spreadsheets, locations on a map, and audio tracks. While images, videos, and document scans are simple to add on an iPhone or iPad, other file types aren't as easy — at least until you know how.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

Wordle has been popping up all over in the app stores, but none of them are the real Wordle. The popular word game app has amassed two million users since its launch in November 2021 but has no plans to hit the iOS App Store or Play Store any time soon — but you can still install the official Wordle app on the Home screen of your iPhone or Android phone.

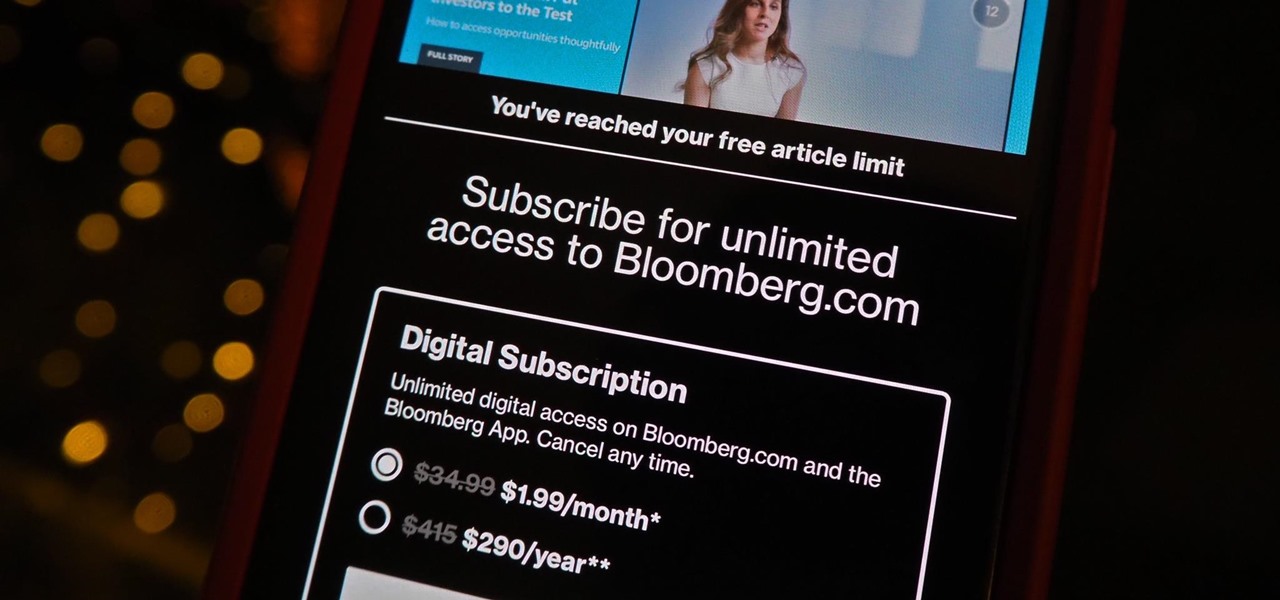
One of the most aggravating things that can happen on Facebook, Twitter, and other social media apps is when a friend shares an exciting story, and a paywall prevents you from reading any of it. You could pay for a subscription to unlock it, but there are so many news sites that it can be both confusing and expensive to spend money on all of them.

Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding education to get the skills you need to thrive.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

While Apple and Google have paved the way for developers to create web-based AR experiences through their respective mobile toolkits, an open source option has entered the space.

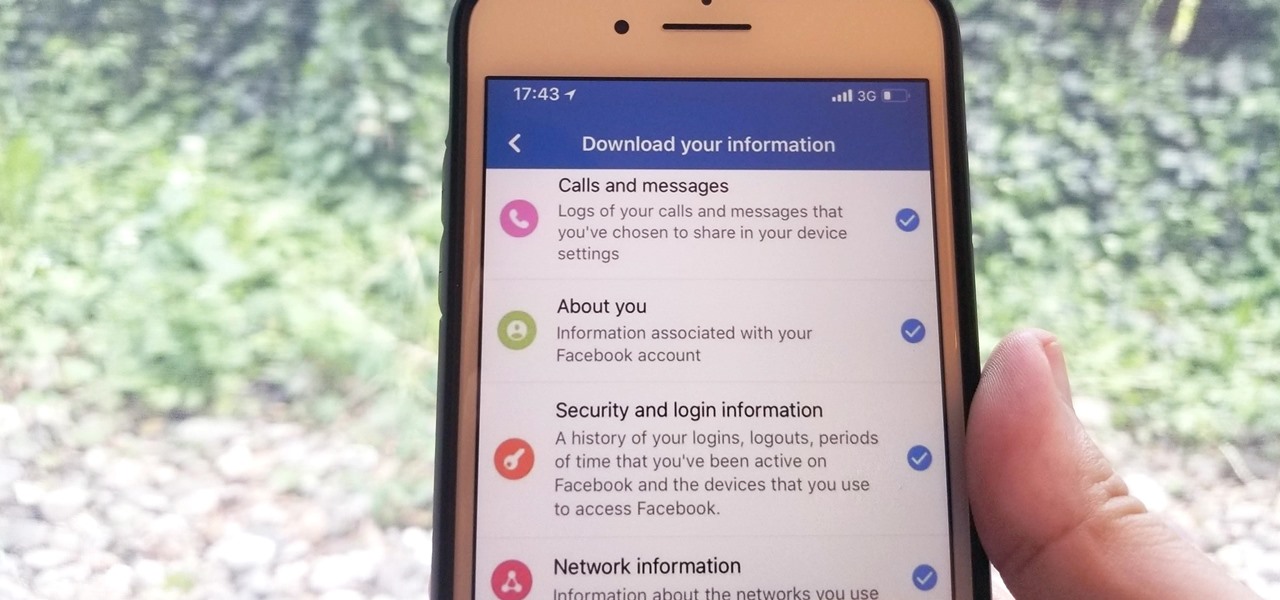
We've been able to download our Facebook data onto our computers for a while now, but now you can do so right from the comfort of your iPhone or Android phone. With it, you'll be able to integrate your data into other apps that support it or even just download it before you deactivate your account.

Uber has lost market share to Lyft, its main competitor. Uber's US market share dropped from 84% to 77% between January and the end of May this year, and the ride-sharing company has continued to run into legal, public-image, and internal trouble. Lyft, on the other hand, has been growing.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

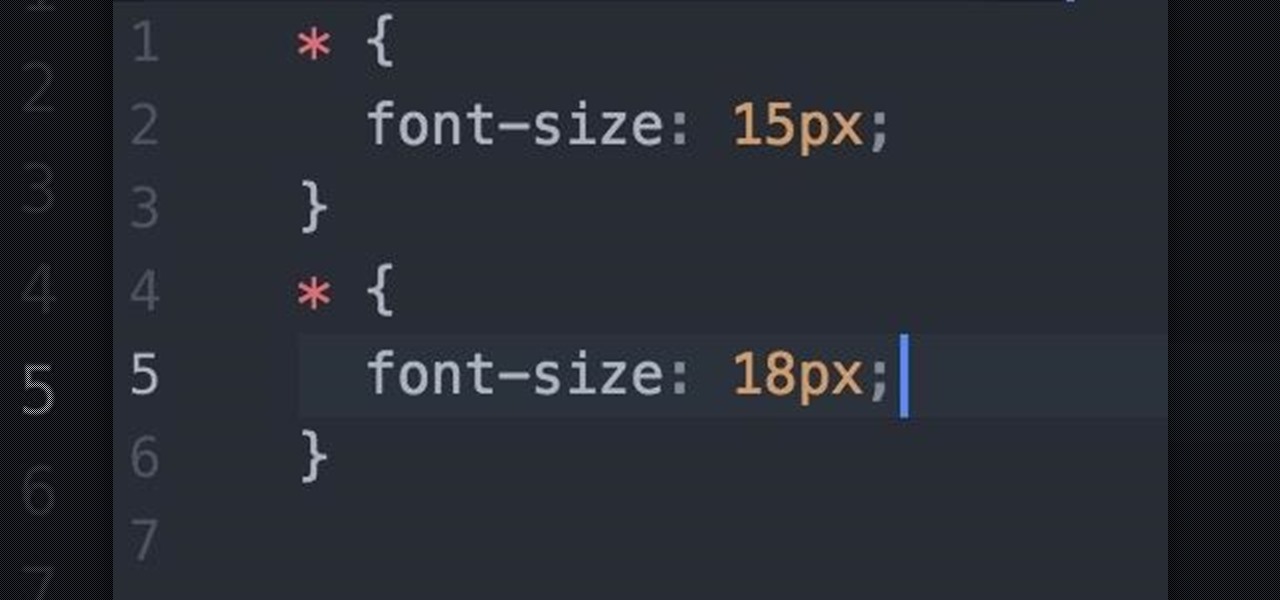
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Over the course of the past few years, many websites have begun offering up a mobile-friendly HTML 5 version of their content. Videos that once required Adobe's Flash can now be played on any modern mobile web browser.

I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills.
Here, you will learn all you need to know about prime and composite numbers. What Is a Prime Number?