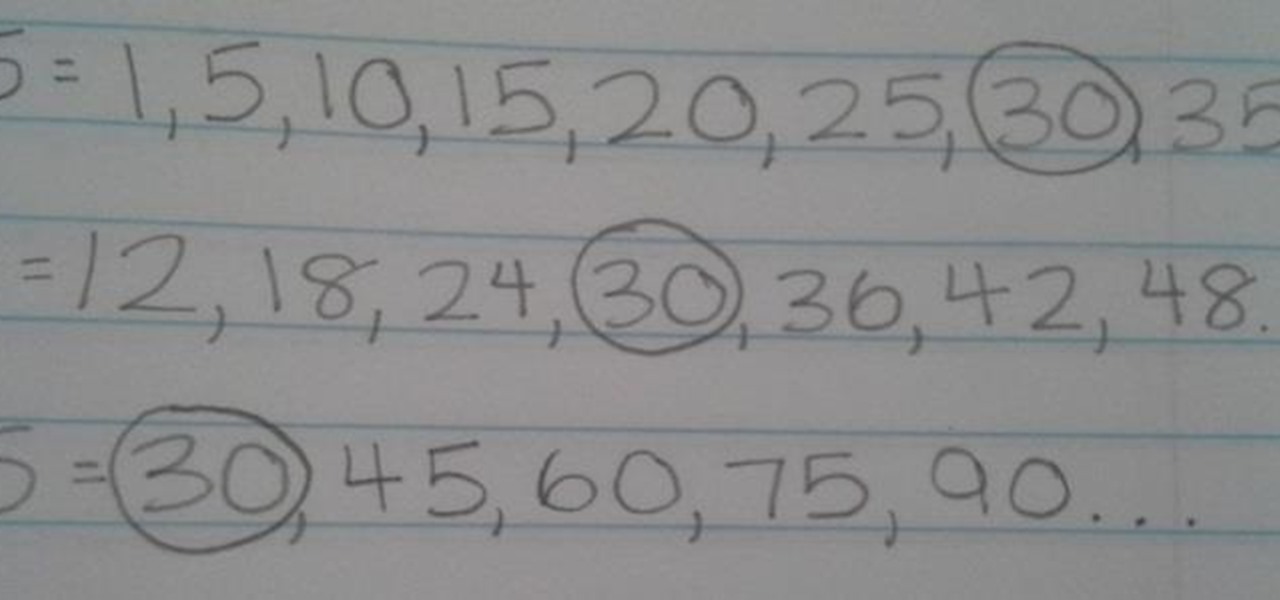Interested in creating your own dynamic, web-based applications using Visual Web Developer 2005 Express? In this installment from the Absolute Beginner's Series of Visual Web Developer C#/ASP.NET video tutorials, you will learn how you can display content on your website with the Multiview and View controls. This lesson will be particularly helpful to programmers to those with experience using both Visual Basic and simple HTML syntax. For more information, as well as tips for being a smarter ...

Interested in creating your own dynamic, web-based applications using Visual Web Developer 2005 Express? This video shows how to use the Windows Media Player ActiveX control to play wma and MP3 audio files in your application.his lesson will be particularly helpful to programmers to those with experience using both Visual Basic and simple HTML syntax. For more information, as well as tips for being a smarter user of Microsoft Visual Web Developer, take a look! Play MP3s in ASP.NET web applica...

Interested in creating your own dynamic, web-based applications using Visual Web Developer 2005 Express? In this installment from the Absolute Beginner's Series of Visual Web Developer VB/ASP.NET video tutorials, you will learn how to use the FlowLayout panel to create dynamically resizing Windows UI. This lesson will be particularly helpful to programmers to those with experience using both Visual Basic and simple HTML syntax. For more information, as well as tips for being a smarter user of...

Interested in creating your own dynamic, web-based applications using Visual Web Developer 2005 Express? This video will show you how to use the SoundPlayer control to play .wav audio files in your web application. his lesson will be particularly helpful to programmers to those with experience using both Visual Basic and simple HTML syntax. For more information, as well as tips for being a smarter user of Microsoft Visual Web Developer, take a look! Use the ASP.NET SoundPlayer control to play...

Welcome to the Goodnight Byte for HackThisSite, Basic Mission 4. In Friday's session, we tackled some coding in Gobby. Nothing special, just a few modifications to the NullBot script we made a few session ago, and some education on regular expressions. Apart from coding, we did our scheduled HackThisSite mission. We had to take on some JavaScript, which was a new thing for Null Byte. This mission taught us about client-side HTML manipulation through JavaScript injections. This just means that...

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

Here are the13 best articles on How to Build a Potato Gun. http://www.scribd.com/doc/15796837/To-Make-A-Spudgun-An-instructionally-informative-document-by-Enoctis

Technology: The Less You Know the Better?

Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person. It's usually placed in abnormal places like HTML image tags.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about posting peaceful poetry.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).

Last Friday's mission was to accomplish solving HackThisSite, basic mission 8. This meant that we had to learn some more basic Unix commands.

Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

Facebook Fan Pages have become extremely popular and are being used by everyone from large companies like Coca Cola and Ford Motors all the way down to people's pets.

I already had a mishap shooting my Canon 5d MII tethered....I broke my circuit board because of the stress that a USB cable causes the camera. I wish Canon went with their 1ds route and made a positive locking device, but alas they have not. So the best alternative I could find was a left-angle cable that will reduce the stress and make it quite easy to gaffers tape to my vertical grip for some added safety. Check them all out here, I just purchased the "15' Left Angle" will let you know how ...

http://www.nationalgeographic.com/adventure/0505/photo_index.html

It's that time of year again, filmmakers... time to make your new year's resolutions. And no, I don't mean quit smoking or stop drinking - smoke and drink all you want SO LONG AS YOU FINALLY GET THAT FILM FINISHED AND SUBMIT IT TO A FESTIVAL OR TEN. Rajo has signed up for a withoutabox.com account and scoured the internet for the latest film festival submission deadlines just so he can clue you in to which ones are coming up soon - whatta guy. And just for fun (a.k.a. future reference), here'...

Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will make the effort to learn even when I am not present. So, a tip of my hat to Mr. Sol Gates and the rest of you fine people.
What Is a Rational Number? A rational number is a number that can be written as a ratio and a/b.

What Is LCM? LCM is an acronym for "Least Common Multiple." LCM is the smallest number that is a multiple of two or more numbers.

There are many places where you can get help. If you are under 18 you will need your parents to take you, if anything the counselor will need to talk to your parents to see what is your home situation. Remember the counselor will not say anything to your parents or anyone else unless you want to harm yourself or anyone else. If you are 18 and older you could sing up for yourself to receive help. You could get help from places like HOPICS, (For Teens) and People Who are.

On the same day that Google launched their new social network, Google +, a team of Google engineers calling themselves the Data Liberation Front announced their first service on Tuesday—Google Takeout, a product that allows users to easily move their data in and out of Google products, including Buzz, Contacts and Circles, Picasa Web Albums, Profile and Stream (the equivalent of Facebook’s newsfeed).

By Huffingtonpost Meg Whitman New Spanish- Language AD: I stood up against The Arizona Law

Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security, because X10 is here.
http://web.mac.com/scifione/orig/BOOKS/HEX/hex-def.htm
Here are some places in Los Angeles that offer art programs! - Homeboy Industries http://www.homeboy-industries.org/curriculum-education.php
jQuery is a fast and concise JavaScript Library that simplifies HTML document traversing, event handling, animating, and Ajax interactions for rapid web development. jQuery is designed to change the way that you write JavaScript.

Ad from circa 1880, found on http://copyranter.blogspot.com/2010/05/its-easy-to-die-with-diamond-dyes.html. Nothing Disturbing here

Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.

Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do not show up on time, we have to go backwards and catch everybody up. This wastes time and will also make other users' experience less enjoyable when they have to watch and listen to the same thing 100 times. Punctuality as...
www.greattech4us.weebly.com/shopping.html The items if bought will help me produce more wooden surfboards.

Here are the instruction on how to download and get started:
In This video I explain how you can change that background image you see when you logon. In the video I use winrar to extract the program you can download winrar here.

When Floyd Landis accused competitor Lance Armstrong of doping last May, I dismissed it as just an instance of Landis' lashing out.

lol. Personally, I used his calls as ring tones. If you like the video, there is another one at cracked. It's based on his movie Ransom and it's just hilarious towards the end:

Something so basic, yet so mysterious... Gravity seemingly a law that we must live by... or is it? Check out this fascinating article from the New York Times, examining one scientist's bid to redefine what we think about as gravity.

Hold The Beef This top ten list is packed with creative burger alternatives, from a Dungeness Crab Burger at Malibu's Paradise Cove to my Venice favorite, Seed's Tempeh Burger!