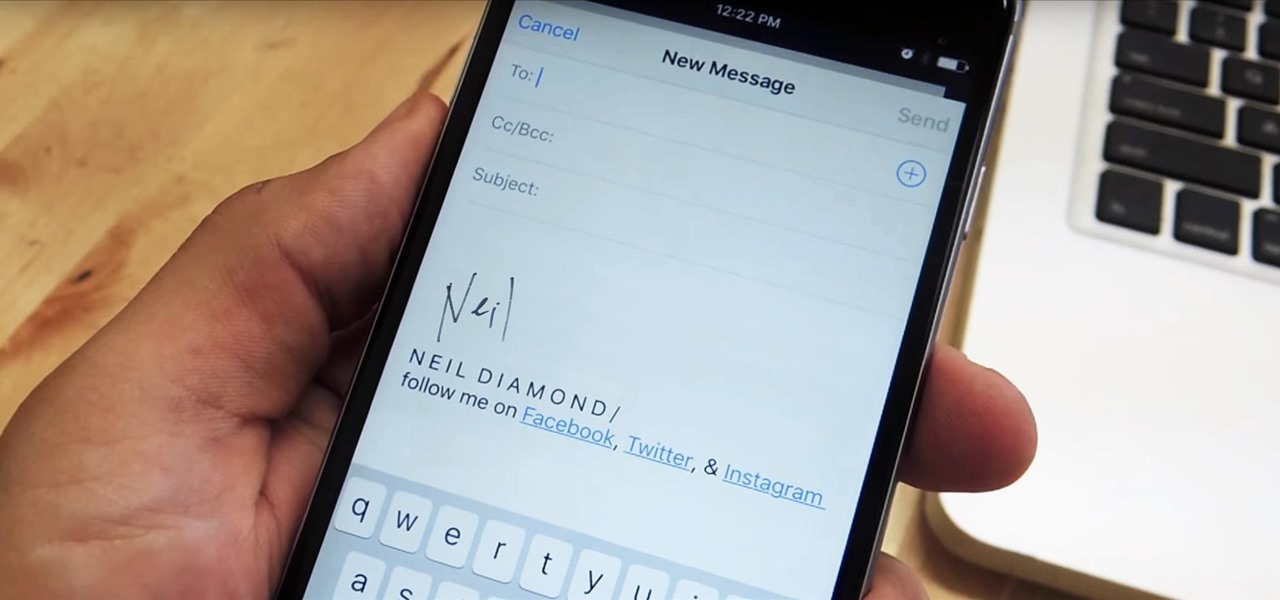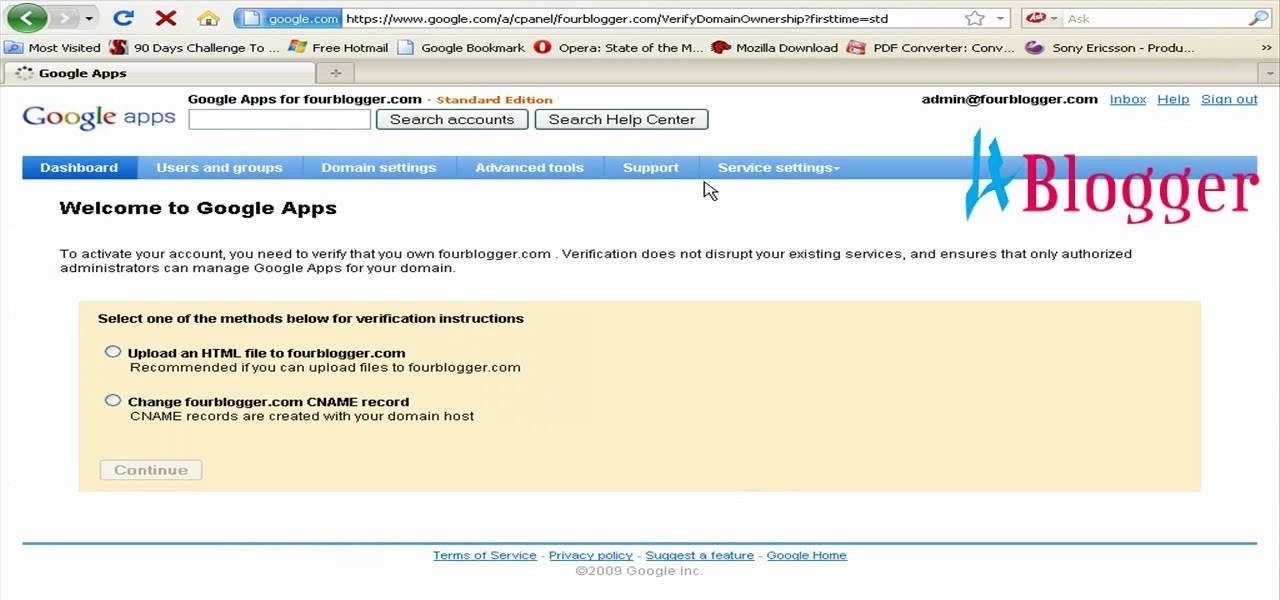
You can create the Google apps email like Gmail for your domain. So to do this first you need to go to the google.com/a and click on the standard in "other Google apps editions". Now click on "get started". Now select "administrator: I own..." and enter your domain name and click get started. Now on next page create your account by filling all the fields and click continue and now fill the info of your administrator account and click I accept button. Now next step is for the verification of y...
This video tutorial from izbyfl shows how install Google Chrome and enable its plugins in Ubuntu. First download application from here: http://www.google.com/chrome/intl/en/eula_dev.html?dl=unstable_i386_deb.
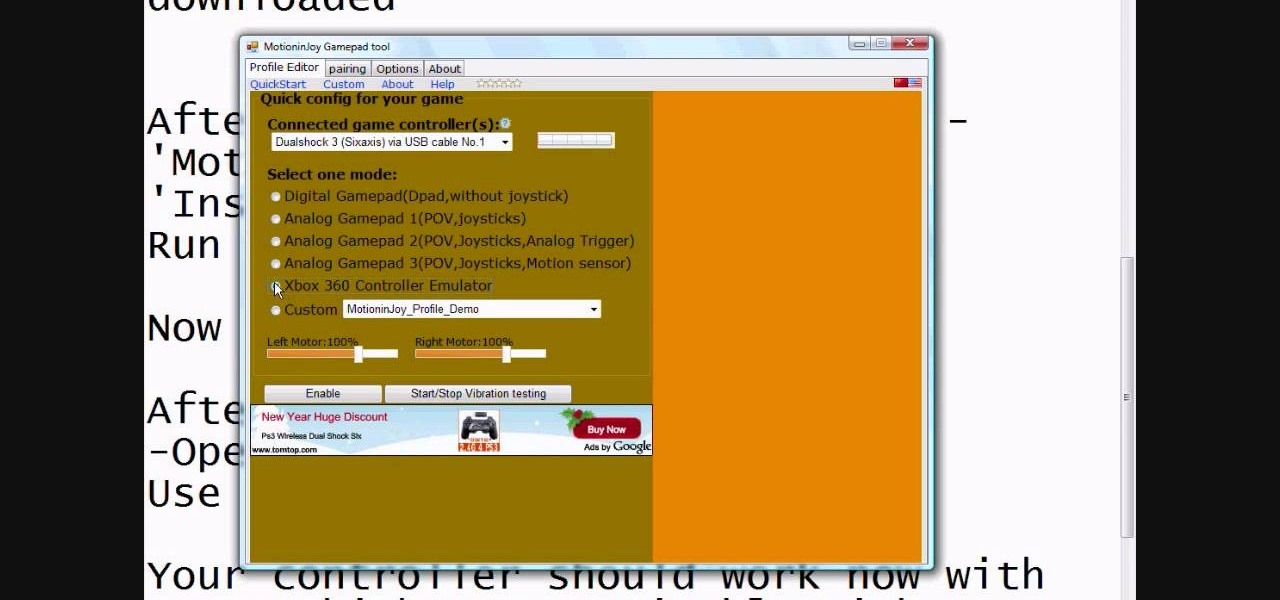
This video tutorial from radeon4350 shows how to connect dualshock PS3 console controller to PC. First, download driver software from here: http://www.motionjoy.com/download

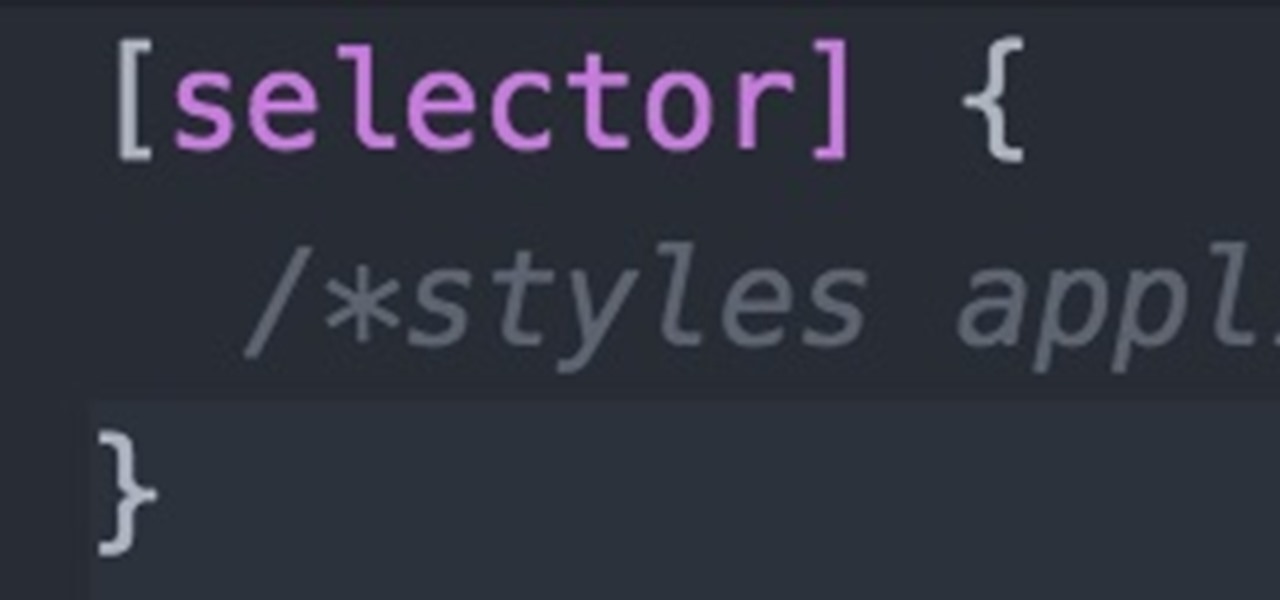
Open up dreamveiwer and click HTML on creat new. If the new page opens then go to design view and then go to insert and then layout object and then diff tag in that then click ok for that. There we have to create a scrollbar content. Then we have to right click there and go to css styles and then go to new. There go for selector type and click class and then name it as you want. Here he just named it as scrolldivstyle then go to go define in and take this document only and then click. Next yo...
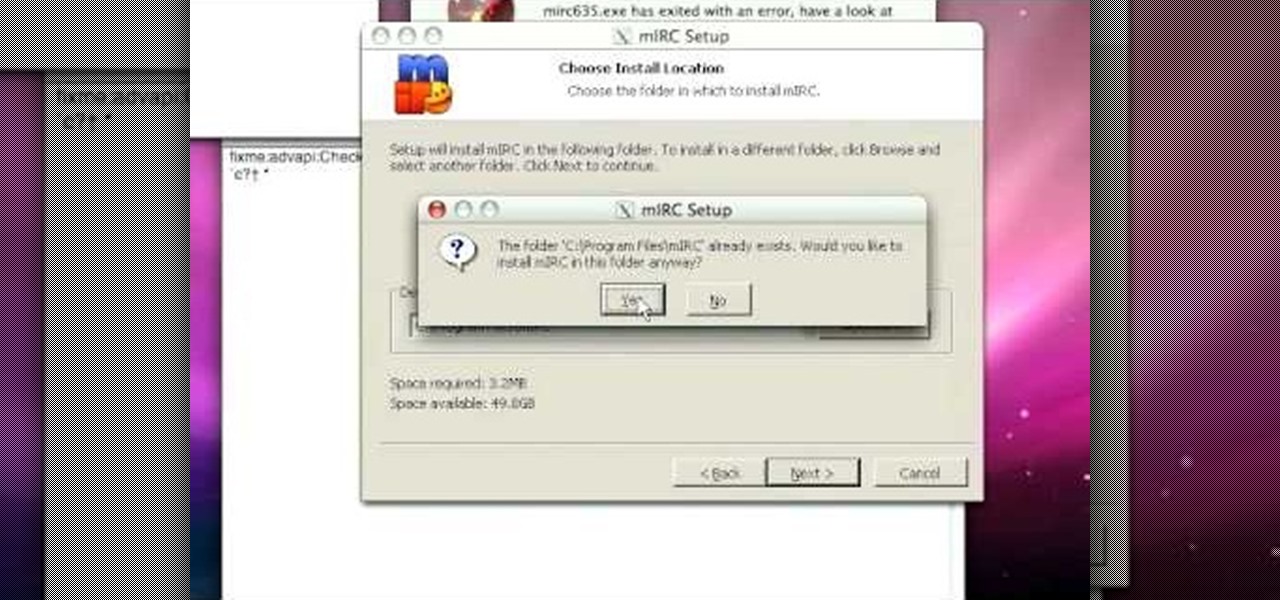
This video tutorial from gogeeks shows how to install mIRC application on Mac OS X operating system.

Make light saber glow effects in lsmakerThe author found freeware that helps create light sabers. The freeware is not as good as adobe after effects, but it will serve the purpose. Download the software from the website http://www.lsmaker.uw.hulpage.php?main=lsmaker.html. Extract the folder. Open lsmaker.exe. Save the extracted file to the desktop. Select import. Add either picture or video file. Change the saber color to red. Click ok. The blade needs to be white. In the dialog box change pi...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

This video is a tour of circlepad rather than a tutorial, for people who would like to make web pages without having to learn html using circlepad.

This genius video shows the viewers how to easily embed and add a YouTube video into a PowerPoint presentation with no internet connection! First you will need to make sure you are using Firefox. After getting Firefox, make sure you install a Firefox Add-on called Video downloader. To get this add-on, Google 'video downloader' and install the add-on. you will see a new icon at the bottom of the screen to the right. First, go to the video you would like to download on YouTube and click on the ...

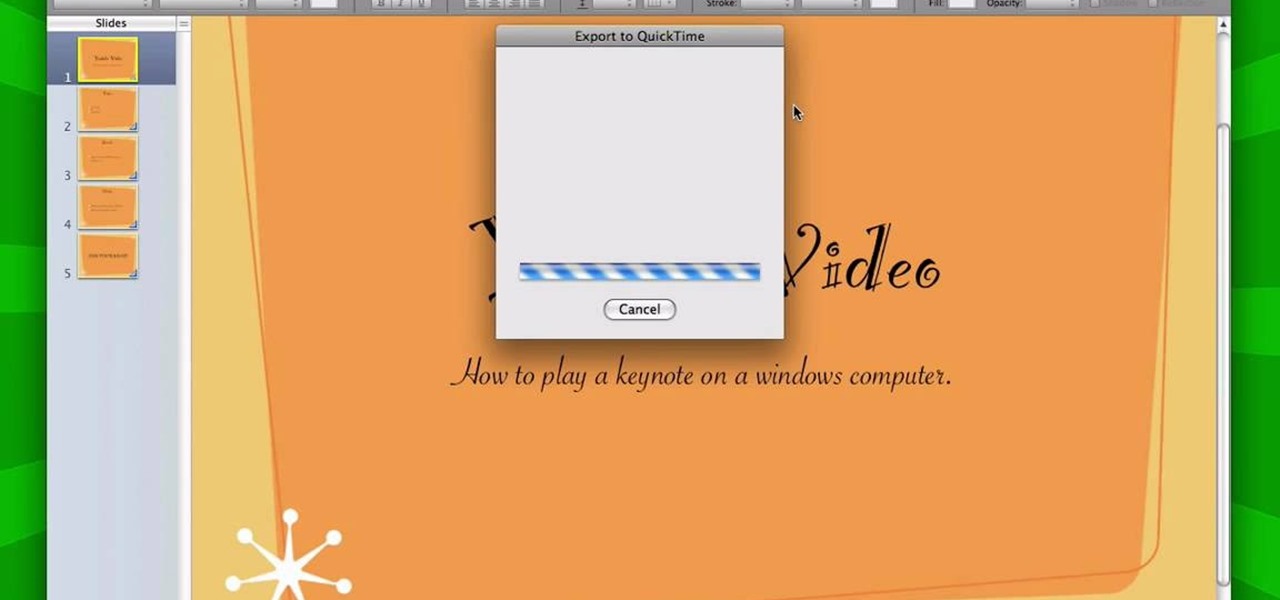
It is a great video tutorial about how to create a keynote presentation to run on a windows platform. After opening the keynote presentation, click on file menu and open up the export window. This window shows different file formats and types. By using this we can export a quick time movie, an html, PDF, images, flash or a PowerPoint presentation file.

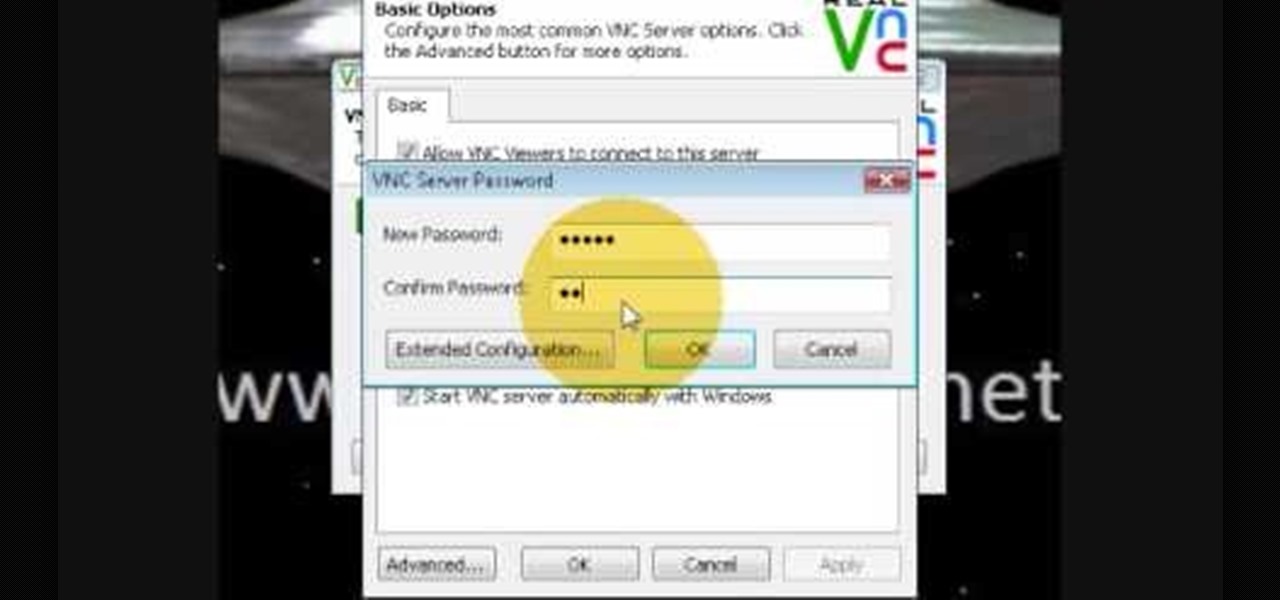
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...

1. On the browser, type www.weebly.com. If you are a new user, then sign up. Write your username, email, password, and click on Sign Up and Start Creating.

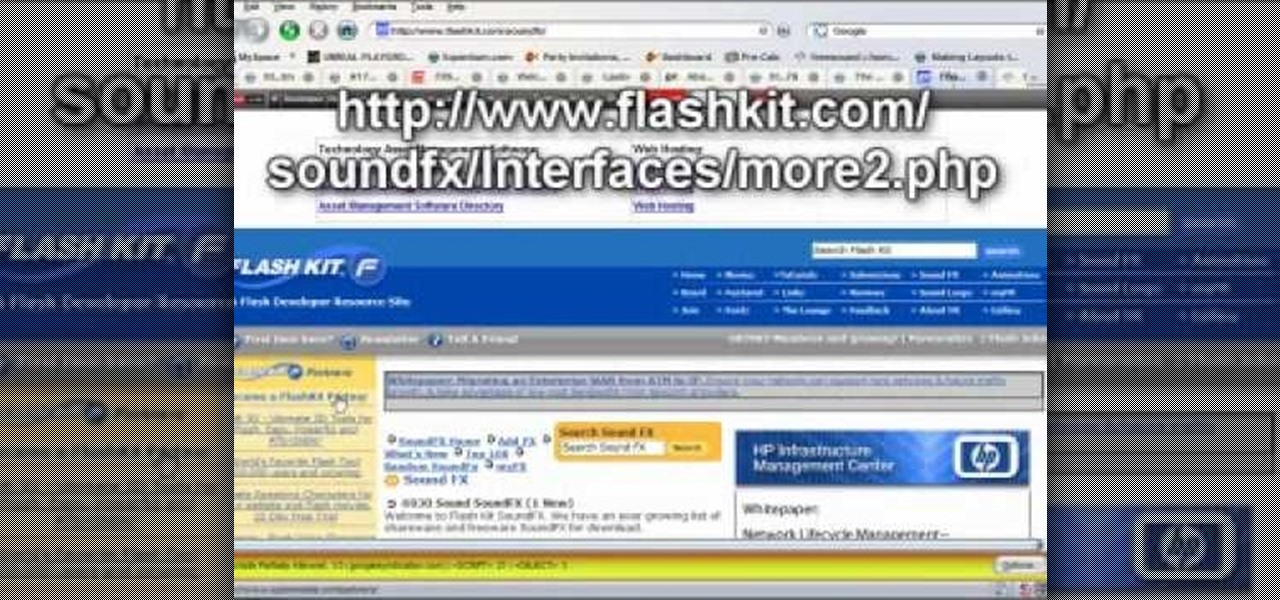
If you need some sound effects for your upcoming film, you better watch this video! After principle photography in production, you have to get into the editing process in post-porduction, which leads to sound department for ADR, Foley, Sound Effects and Sound Design. If you can't afford a professional sound designer for your movie, you can do it yourself, and this video will help you find sound effects on the Internet for your film.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Changing computers or switching to a different type of web browser? If you have been using Firefox for a while, you most likely have some good bookmarks saved. Check out this tutorial and learn how to export your bookmarks from your old browser and take them along with you, wherever you go.

You know this is the job for you. Here’s how to convince the person doing the hiring. Learn how to do well in a job interview.

Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

In these PHP basics video the tutor shows how to do form processing. Handling forms in PHP is basically the main functionality of PHP. The forms in HTML take the values of a from and send them to the PHP in real time to do the form processing. In this video the tutor shows how to make a HTML form from the scratch inserting a form into it with some fields and buttons. Now he makes the form post a method to a PHP page when you submit it. Now he shows how to make a PHP file from the scratch by w...

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

This video tutorial will talk about html formatting on YouTube. specifically how to make your comments bold, italicized (italics), underlined, or all of the above. It also explains html entities.

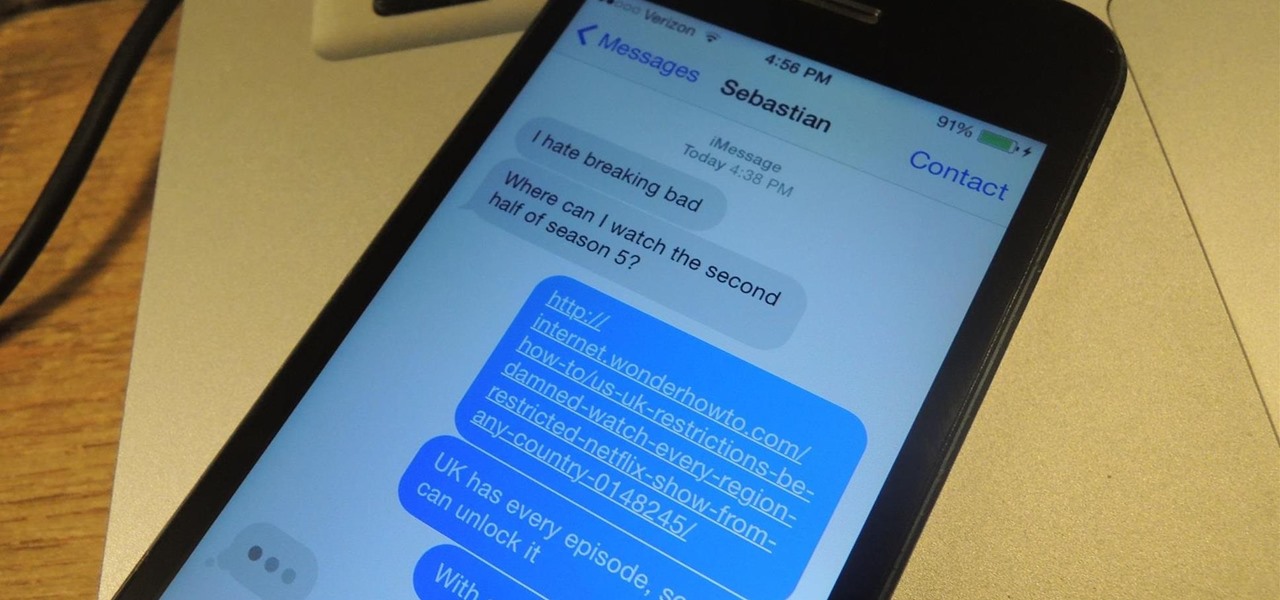
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

If you know how to solve the Rubik's Cube, then why don't you try yourself at the Square One puzzle? If you thought the Rubiks Cube was puzzling, then you haven't seen anything yet! This video tutorial will show you how to solve the Square One puzzle. The Square-1, also known as Back to Square One and Cube 21, is much like the Rubik's Cube, but its shape changes when twisted, adding an extra level of difficulty.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

Learning to code is difficult, particularly if you're doing it alone. While coding may be among the most valued job skills in many markets, the education is sometimes inaccessible.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

This tutorial is about how to create the floating bar with social media buttons on a weebly website. Weebly has change its layout on the dashboard. Its a new video of new layout of weebly dashboard. I found many quesiton regarding 4 different HTML files instead of one index.html. Users were asking about in which they have to change the code so here is the solution. Watch the video, drop your comments and feel free to ask.

If you're a Firefox user and frequently use free image hosting services à la ImageShack & Photobucket, then you've no reason not to check out the ImageBot Firefox extension, which does quite a lot to streamline the picture uploading process.

If you've been thinking about changing careers and you have just a little bit of time, The Ultimate 2021 Web Developer & Designer Super Bundle may be just what you need. This is also the perfect time to get it because it's on sale for $34.99, which is 98% off the regular price of $1,886. You'll get 14 courses that offer 39 hours of content on HTML, JavaScript, CSS, and more.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Arts and crafts are a whole bunch of fun, and in this tutorial jewelry making video, Jessica Poundstone of Jewelry By Jessica teaches you how to make a three-layer flower pin out of shrink plastic! The templates needed to complete this project are available as a PDF download at http://www.jewelrybyjessica.com/tutorials.html

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.