There may be worse feelings than sitting around waiting for food delivery, but I don't want to know what those are. Especially when your local delivery guy misses your address for the eighth time. But soon, Domino's Pizza will take that stupid human error right out of the equation in the form of a robot that's only 3 feet high.

Watching the NCAA Men's Division I Basketball Tournament without cable used to be easy. As long as you had an internet connection, CBS and Turner (TBS, TNT, and TruTV), which co-broadcast March Madness, let you watch all 67 games online free of charge.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

There's a whole world of wallpapers out there. Apple always includes a selection of stock wallpapers, some unique to every iPhone model you have. Of course, sometimes, stock wallpapers don't cut it. Sometimes, you want to add your own style to your home screen and lock screen. In these cases, using an app to find the best wallpapers out there can be just what you need.

Texting has become the king of communication—gone are the days where everyone called each other. These days, it's down-right weird when someone calls first. Whether it be on a phone or on a computer, SMS and MMS messages are the most common way people keep in contact, so why not make sure your app of choice is the best possible one out there?

Microsoft has invested years and countless man-hours in an effort to get their cloud storage service on par with competitors like Dropbox and Google Drive, who have long resided at the top of this market. Their hard work has definitely paid off, as OneDrive (formerly SkyDrive) has finally reached a point in its development where it can stand toe to toe with any comparable service in almost any measurable regard.

So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

Hello there, 'Flashers'! Welcome to my 8th Post. This tutorial will explain how to flash Kali NetHunter on OnePlus (Tested) and Nexus Devices (Not Tested-Should work) as a secondary ROM, so that none of your personnel data/ROM gets affected.

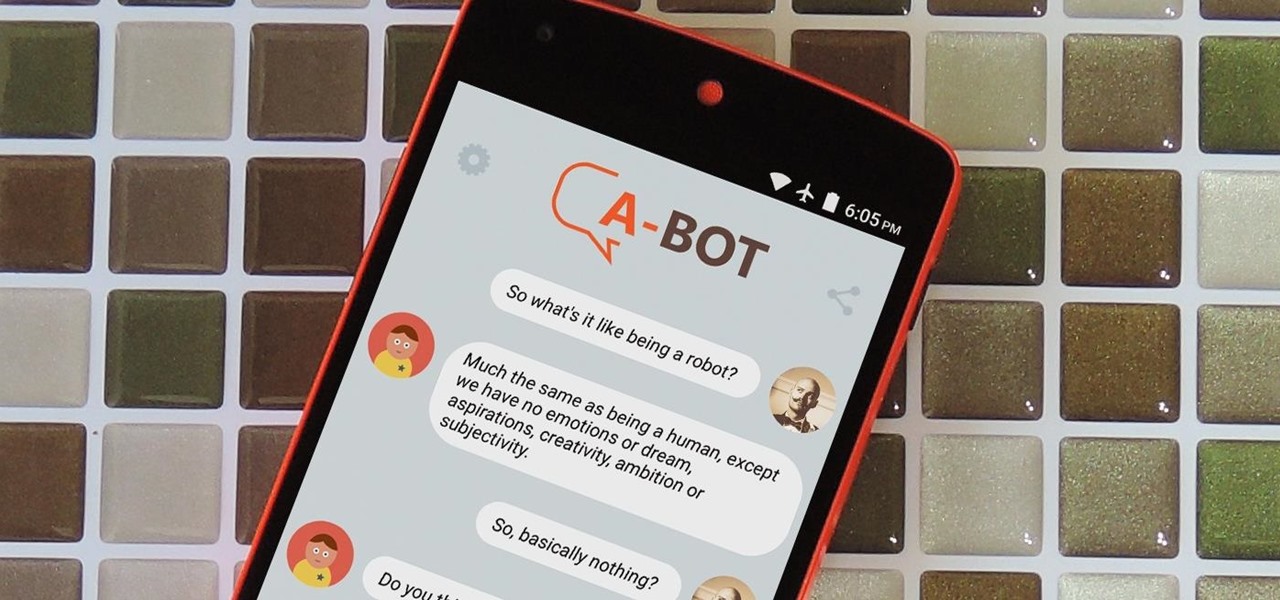
We all have those moments where we're bored or lonely, and in those times, just having anyone to talk to would be awesome. But maybe your friends are all busy, or everyone you know is at work and nobody's responding to your text messages.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

Our dog has tons of energy and always wants to play. However, play time can be exhausting to the humans of the house. We found out a few months ago that the dog loves to play ‘chase the red dot.' Boredom leads to creativity, so we attached a laser pointer to her head with a bandana and small piece of tape. This kept her continuously occupied until we removed it after 20 minutes. I assume you could try this with a cat if you were daring enough – good luck with that. Caution: Laser pointers (ev...

Many modern Android devices use a display technology called AMOLED. These screens differ from traditional LCD displays in that each pixel emits its own light, so a backlight is not required. Even better, when rendering a black element on the screen, AMOLED displays simply don't light up the associated pixels, meaning virtually no power is used. Since black pixels use little to no power on an AMOLED screen, more black pixels means lower battery consumption.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Looking for a costume that breaks the mold of skimpy and clinging fabrics? Stay warm on Halloween and impress at any spooky event by turning yourself into a perfect recreation of the apes in Dawn of the Planet of the Apes.

There's no TV show that stands out quite like American Horror Story. With its crazy characters and nightmarish storylines, there are countless costume ideas hiding in its episodes.

Thomas Ridgewell, more widely known as TomSka, is a popular Youtuber who creates over-the-top, ridiculous, and overall pretty funny videos—but sometimes they don't make sense.

Video: . Extraterrestrial life is life that does not originate from Earth. It is also called alien life, or, if it is a sentient and/or relatively complex individual, an "extraterrestrial" or "alien" (or, to avoid confusion with the legal sense of "alien," a "space alien"). These as yet hypothetical forms of life range from simple bacteria-like organisms to beings far more complex than humans. The possibility that viruses might exist extraterrestrially has also been proposed.

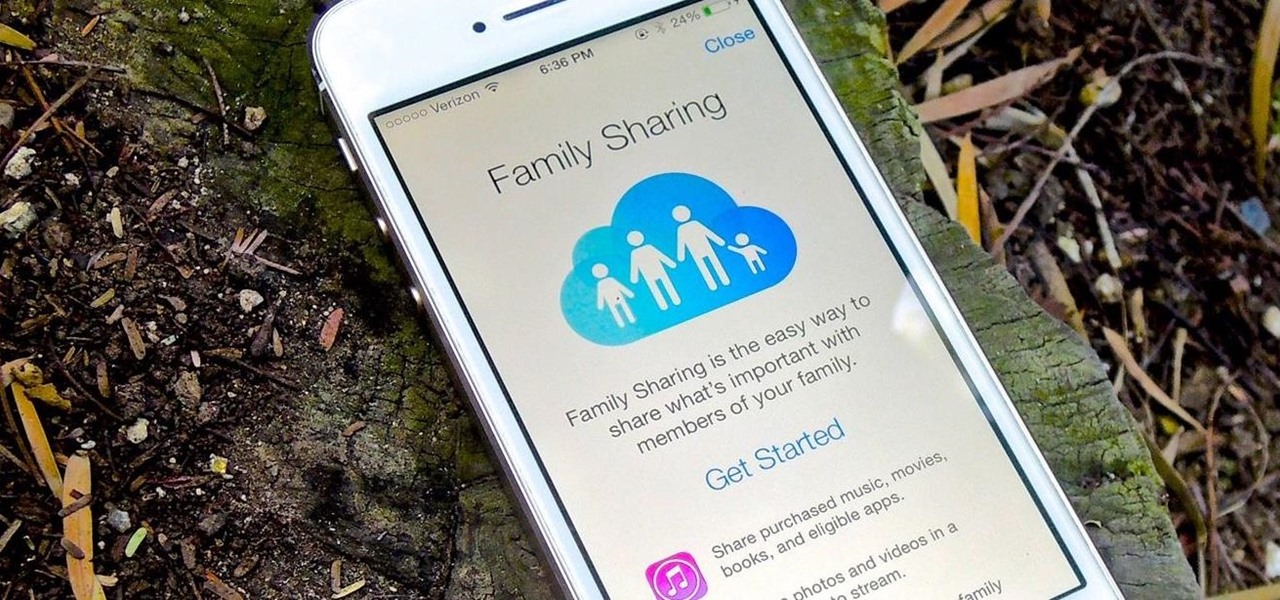
There are a ton of great new features in iOS 8, and one of the most interesting (and perplexing) ones is called "Family Sharing."

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

Over the past decade, touch screens have changed the way we interact with our electronic devices. Gone are the days of clicking and pecking at keyboards, with these gestures replaced by swipes, taps, and long-presses on most of our newer devices. From the early years spent swapping out vaccuum tubes and reading light indicators, human interaction with computers has been constantly evolving. Can Qeexo's FingerSense usher in the next era in manual input?

If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you to perform certain functions without even touching your phone.

With apps and games getting bigger and more memory-hungry every year, storage space is at a premium. High-definition videos and photos of innumerable pixels certainly don't help the matter, either.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Here's a routine that I'm sure all of us smartphone users go through at least several times a day. You notice your Samsung Galaxy S4's notification LED blinking, grab your phone to see what it is, and enter your PIN. Only instead of anything important, you find that it's just some online store enticing you with sales promotions, or some other email that you could have easily done without.