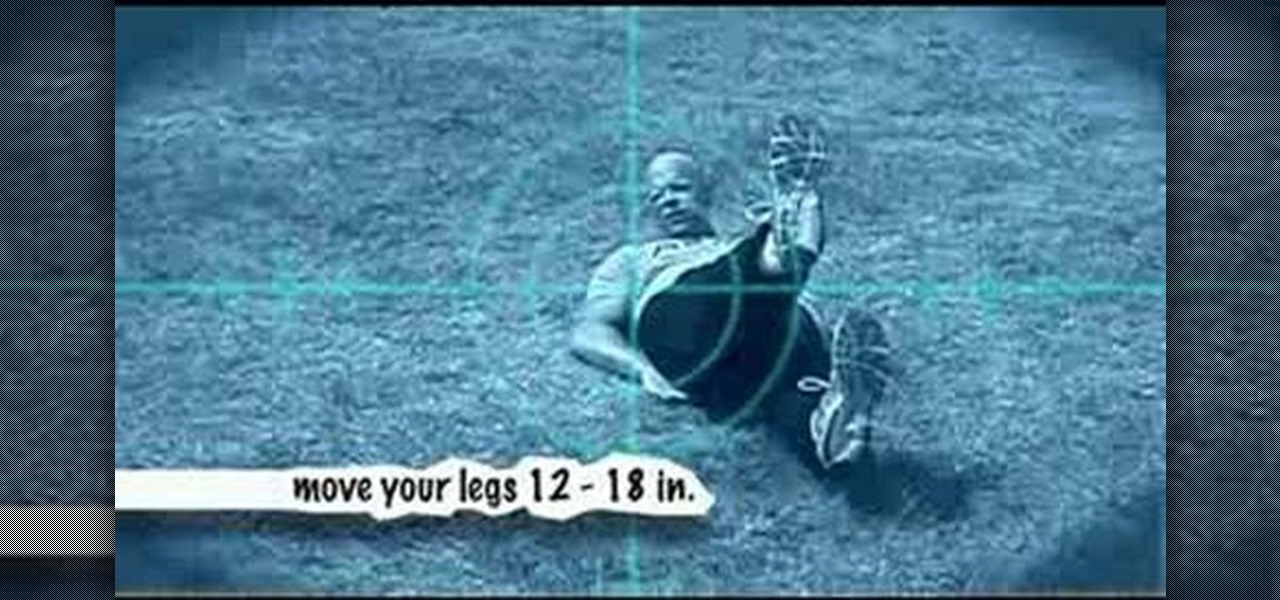
The dive bomber push-up is an advanced push-up format that targets chest, arms, abdominals, back and legs. The dive bomber push-up gives a whole body workout in one exercise. Learn how to properly do the dive bomber push-up with this fitness tutorial.
Want to get great abs, thighs, and a butt all by doing just one exercise? Then save time while still getting awesome results by doing the flutter kick exercise, which involves kicking your legs one on top of the other while keeping them at a 45 degree angle.

Donny Gruendler, a faculty member at Musicians Institute, has become and expert at performing with backing tracks, manually triggering samples, and playing with loops (both live and in the studio). In this installment from his video tutorial series in which he discusses the fundamentals of playing with loops, Donny provides tips for complimenting a drum loop (and thus avoiding "target practice").

Skittles is an old European target sport that is very much like bowling. Discover how to make home made skittles with just a tennis ball, glue, empty water bottles, water, paint, and newspaper. Watch this kids activities how to video tutorial to get ideas for a great rainy day kids activity.

Short Plank is derived from original pilates exercises in order to teach proper abdominal and torso support in the push up position. The exercise in this how to video will strengthen your core, strengthen your shoulder girdle stabilizers and target the deep muscles of the abdomen and spine to protect your lower back. Watch this fitness tutorial and you will be toning your body with the Short Plank pilates move.

This video tutorial goes over methods for defining the topology of an organic object in Adobe Photoshop. This is helpful as a planning stage before you begin your 3ds Max 8 digital 3D modeling to make sure that your have proper distribution of faces and your target mesh will deform nicely. So, if you're using Autodesk's 3D Studio Max for awesome 3D graphics, this could help you out with Photoshop topology.

Don't have time to workout? Then watch this how to video and learn how to do a five minute workout that will workout your abs. Start by doing a in-betweens, bicycles, and toe touches. Finish with side reaches which target your obliques.

Adolfo explains how to use the double end bag. This will help your boxing by allowing you to learn the timing and coordination between your hand and target. You always have to be thinking offense and defense.

Targeting Notes and Creating Harmonies Using MIDI -- Jeff Dykhouse shows us how to use MIDI to tell Auto-Tune which notes to tune. In addition, you can use this technique to create harmonies. Antares Auto-Tune is the fastest, easiest, and highest quality tool for pitch correction. Use this in conjunction with DigiDesign's Pro Tools for awesome sounds.

Let Deb Cross and John Hendron demonstrate how to paste text on a Macintosh without keeping the style information (font size, color) in your target application.

Increase web traffic with these 10 steps in this how to guide. Learn how to generate free targeted website traffic and dominate your niche.

Sadie Nardini shows you how to transform the basic sun salutation yoga exercise into a core-targeting exercise that burns calories.

Sadie Nardini demonstrates a 10-minute yoga sequence that targets your abs, waist, and lower back.

The Swiss ball brings an element of instability to basic exercises like the straight leg bridge. This stimulates and conditions your deep core muscles improving spinalstability. In addition to these small but important joint stabilizer muscles the Straight Leg Bridge also targets larger prime movers in your back, glutes and hamstrings.

Sweating or leaving your feet damp after showers can lead to athlete's foot, a skin rash that targets damp, covered areas. Learn about treating athlete's foot from a doctor in this medical how-to video.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

When it comes to web-based augmented reality, 8th Wall has emerged as one of the leading platform providers, and the company just cranked up its capabilities another notch for AR marketers.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Hitman Sniper topped our roundup for the best premium shooting games, and it's easy to see why. Straightforward yet intense story. Awesome visuals. Stealthy action. Strategic gameplay. Hitman Sniper is easily the best sniper game available for your smartphone, and it's currently free on Android for a limited time, as well as discounted for iPhone.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Buyers can't wait for their Tesla Model 3 to be delivered. But with no clear arrival date in sight, buyers are starting to get a little antsy waiting to see what the Tesla Model 3 will look like up close. Luckily, Tesla accessories seller EVANNEX partnered with technology firm Kinetic Vision to try and satisfy buyers for a while by creating an app that lets you view an augmented reality Tesla Model 3 that's nearly life sized.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Augmented reality (AR) generally exists through the lens of our smartphones as information layered on top of what the camera sees, but it doesn't have to. Developer Jon Cheng worked with an indoor climbing facility in Somerville, Massachussetts, called Brooklyn Boulders, to turn rock climbing into a real-world video game where participants compete in a time trial to hit virtual markers on the wall.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

While I consider myself to be a pretty organized guy, there are often times where I just can't find a file I put on my phone. Most of the time, when I download a file it goes automatically into my Download folder, but when I use a third-party to download other files, like torrents, they could end up in a number of places. Filtering abilities on file explorers often fall short, so it was time to find an app that would automatically sort files in real time.

Don't throw away your dead light bulbs, they may come in handy one day. This video will show you how to start a fire using a dead lightbulb. And no electricity. The tricky part is emptying out the insides, but this can be done with sticks and stones, assuming you're in a survival situation and just happen to have a light bulb with you for whatever reason.

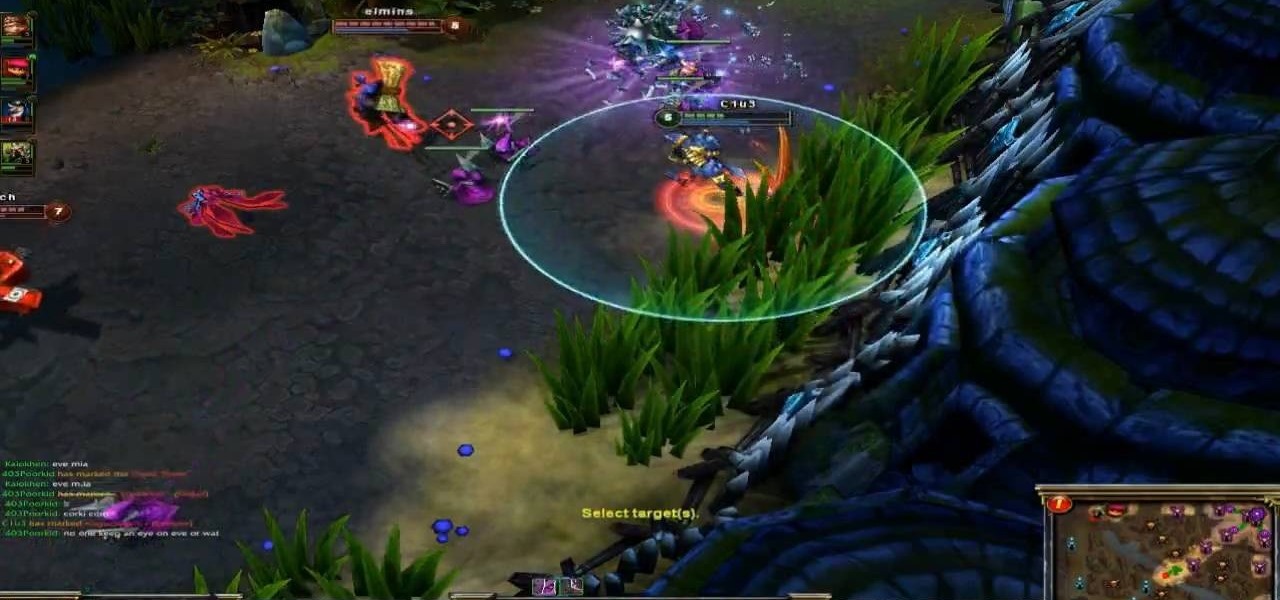
Warwick is one of the champions your summoner can bring onto the Fields of Justice, whose speciality is jungling. This tutorial lays out the best items, glyphs and masteries to take advantage of his innate talents so you can ensure victory in your next League of Legends game.

In this how to video, you will learn how to use the fawn feeding bleat. This is very effective for bow hunters. The call is easy to use. The key is when you make the sound, make it low and desperate. The fawn is hungry and calling to a doe to be fed. Make sure there is a sense of concern to it. Cuff it to create resonance when you make the call. You can make two or three of these calls. Hesitate for ten to fifteen minutes before making the call again. A doe should respond to feed the fawn. A ...

Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Filmic Pro harnesses the full native power of your iPhone or Android phone — and then some. If your smartphone shoots in 4K resolution, Filmic Pro will let you choose that resolution. However, it's not all about the pixels — bit rate is an essential factor in determining the overall quality of your 720p, 1080p, or 4K video, something Filmic Pro gives you full control over.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.