ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.
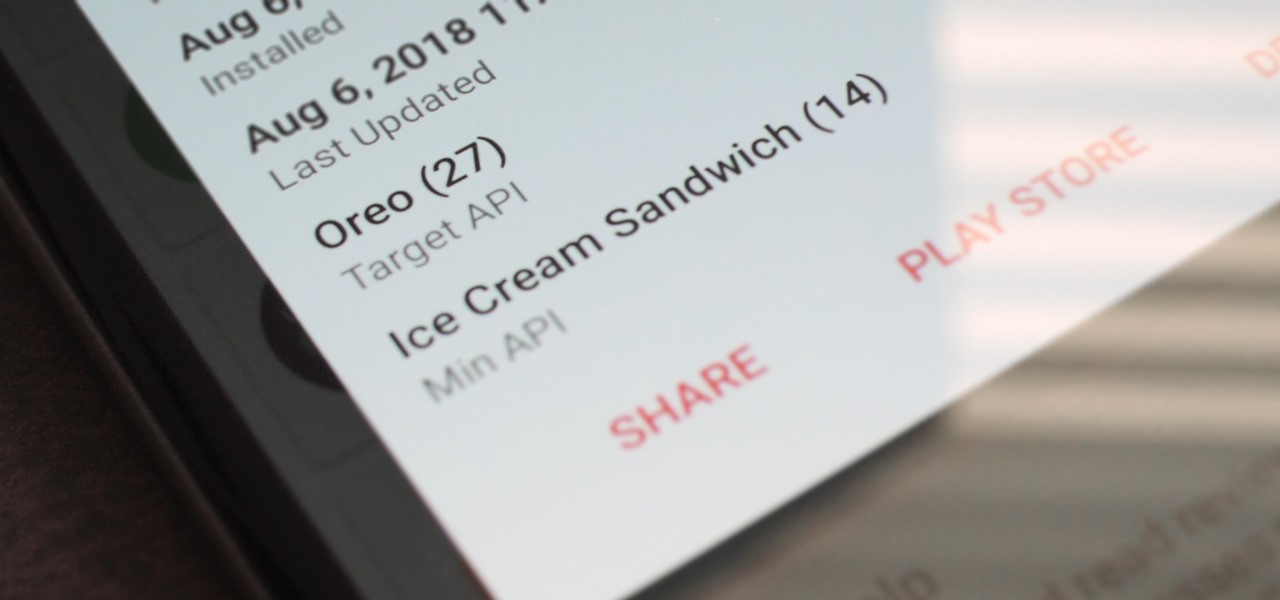
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.
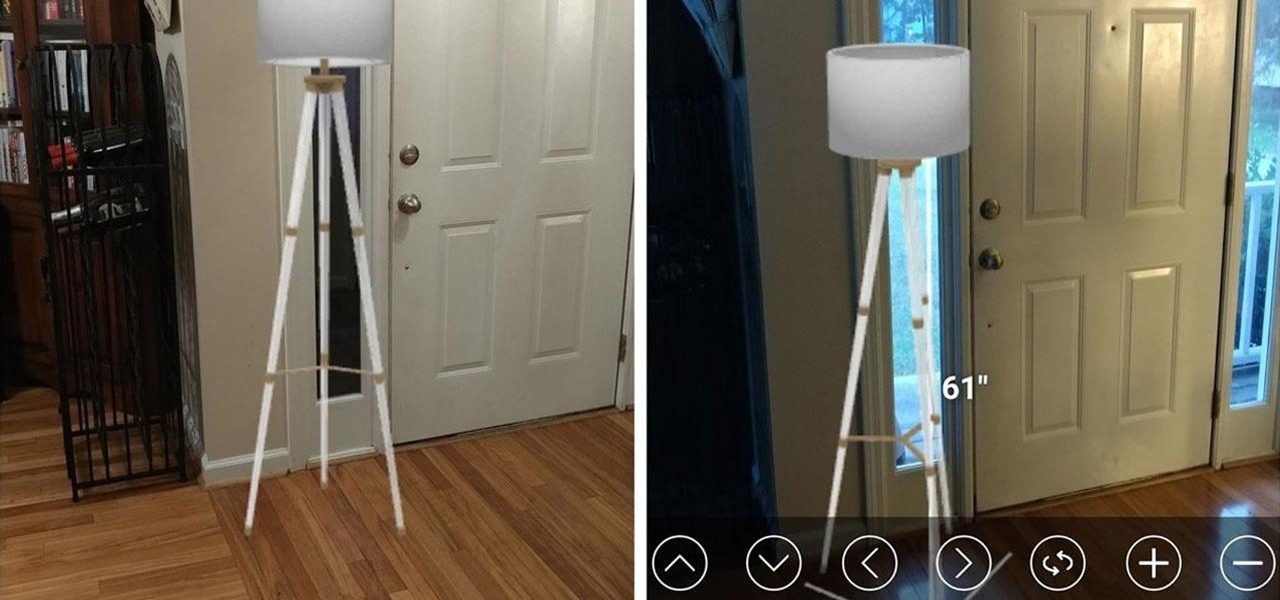
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

The object is to pass to ball between the cones in as few shots as possible, watch and learn how to do this target passing soccer drill.

All-American Skeet Champion Todd Bender explains the safety "does and don'ts" of shooting clay targets. He shows how everyone in the family can enjoy the game and still use proper gun handling techniques.

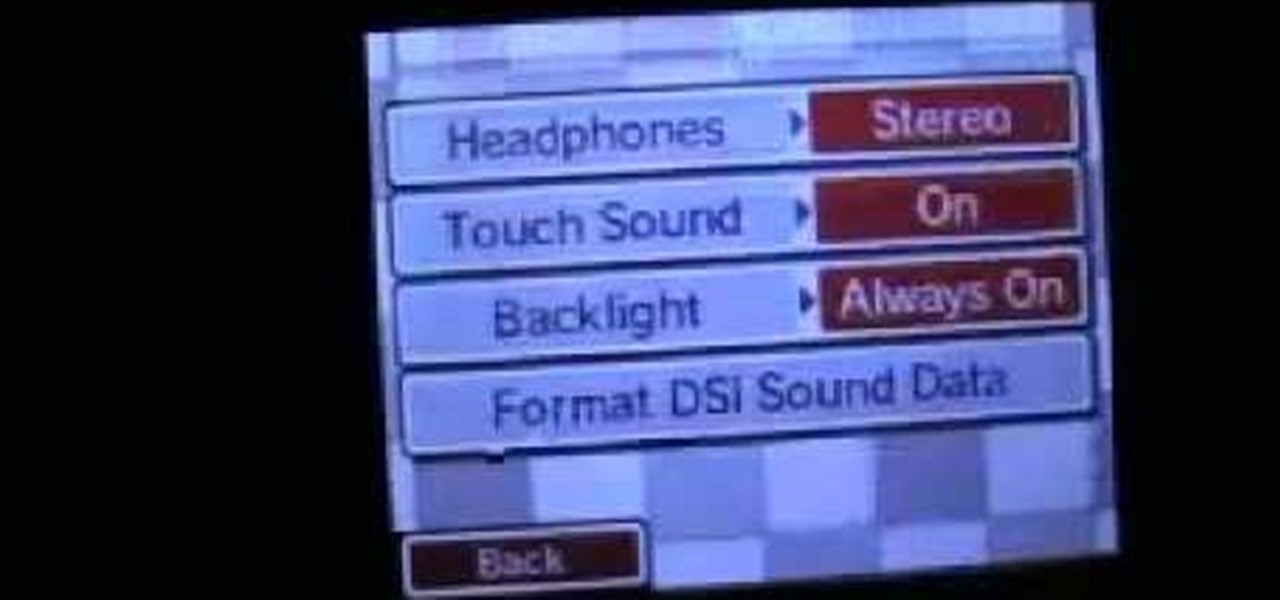
The Nintendo Dsi is a powerful little machine, packed full of cool features. If you're not familiar with all the things you can do, check out this video and see what other things can be done. From moving or removing icons, making cool sounds, set custom music, upload photos to Facebook and more! Don't just sit there watch this video and expand your knowledge of all the cool things your Dsi can do. Oh, and learn how to do a very important system update too!

Attention achievement hunters! In this next tutorial, you'll be finding out how to get the Crackshot achievement in the game Dead Space for the Xbox 360. To get it, you must achieve a perect score in the Shooting Gallery in the game.

Jango Fett and his father Boba from Star Wars are arguably the two most famous bounty hunters in all of modern Western art. This video will teach your how to make a custom Lego minifigure of Jango, using only simple hobby tools and patience. This is one of the more difficult Lego minifigures on the site, but then again, he's also one of the coolest, so try it out!

The cool thing about Just Cause 2, is not only do you play a shoot first, ask questions later type of character, but the game is stocked with a lot of hidden secrets. Or as they are referred to, easter eggs. This video tutorial is presented by the guys at Achievement Hunter and they show you how to find the "Baby" Panay Moustache easter egg. It's easy to find and involves some interesting art. Enjoy!

One of the great things about Just Cause 2 on the Xbox 360, is the main character is a butt-kicking, shoot first, ask questions later kinda guy. Not only does he have a parachute that he can just use at any given time, but he has an awesome grappling hook. A grappling hook! It can attach to moving vehicles and give you a free ride, if you shoot an enemy, you can then shoot another point and send him flying. It's awesome! So in this tutorial, you'll find out from the guys at Achievement Hunter...

Attention ghost hunters! Capture your ghostly findings on film with help from this video tutorial on how to photograph ghosts. Ok.... Yes, they aren't real ghosts, but merely physical people looking transparent and lucid. Nonetheless, this is a great technique to learn for beginning photographers who are looking to get started experimenting with their cameras. This instructional video hosted by Click Here Photography goes into depth about what equipment was used and how to adjust your camera ...

Austin Paranormal Investigations shows how

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Department store chain Target is the latest retailer to offer an augmented reality cosmetics app for customers to virtually try on lipstick.

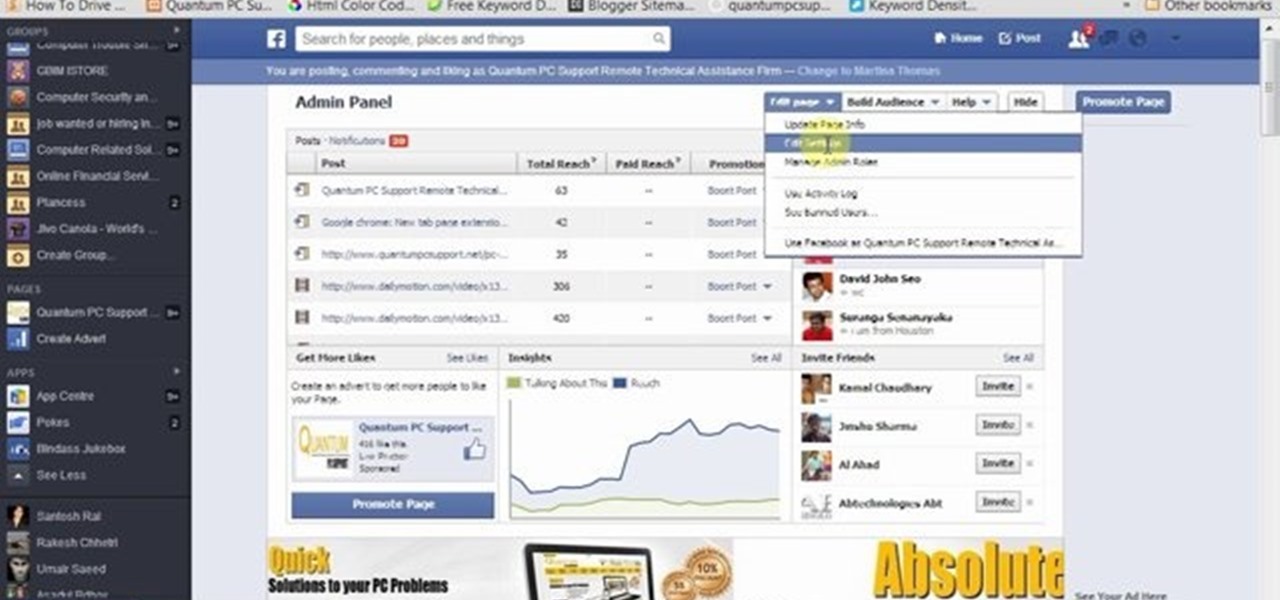
This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.

Kraven The Hunter, one of Spidey's deadliest foes, and a monster of a man on his own. Kraven has cleverly lead you into his trap while on your search for the fragments and has brought you to his home turf: the Jungle. Check out this great walkthrough of the entire first chapter with boss fight included.

Attention all achievement hunters! It's time to go searching for some glyphs in the hit title, Assassin's Creed 2. For this achievement, you must find all 20 glyph locations in the game. Not only will you unlock the Vitruvian Man achievement and 20 gamerscore, but a new video will be available for you to watch.

Attention all achievement hunters! It's time for, yet, another achivement tutorial. This time the game is Dragon Age: Origins. For this tutorial, you'll be finding out how to get the Perfectionist achievement in the game. This can only be obtained after you've played across all the playthroughs and discovered all the possible endings.

Attention all you achievement hunters! In this next tutorial, you'll be finding out how to get the Hell on Wheels achievement to the game The Saboteur.

Achievement hunters, listen up! It's time to head into the Transformers' world with Transformers: War for Cybertron. This game takes place on the planet to both the Autobots and Decepticons and it gives you a first hand experience of what happened on that planet.

Welcome back achievement hunters! In this Left 4 Dead 2 achievement tutorial, you'll be going after the Wing and A Prayer achievement located on Swamp Fever. This is an easy achievement that requires you to just sit back and let your AI team do all the work. It's an easy achievement to unlock and will result in a sweet 30 gamer points. So check it out and good luck!

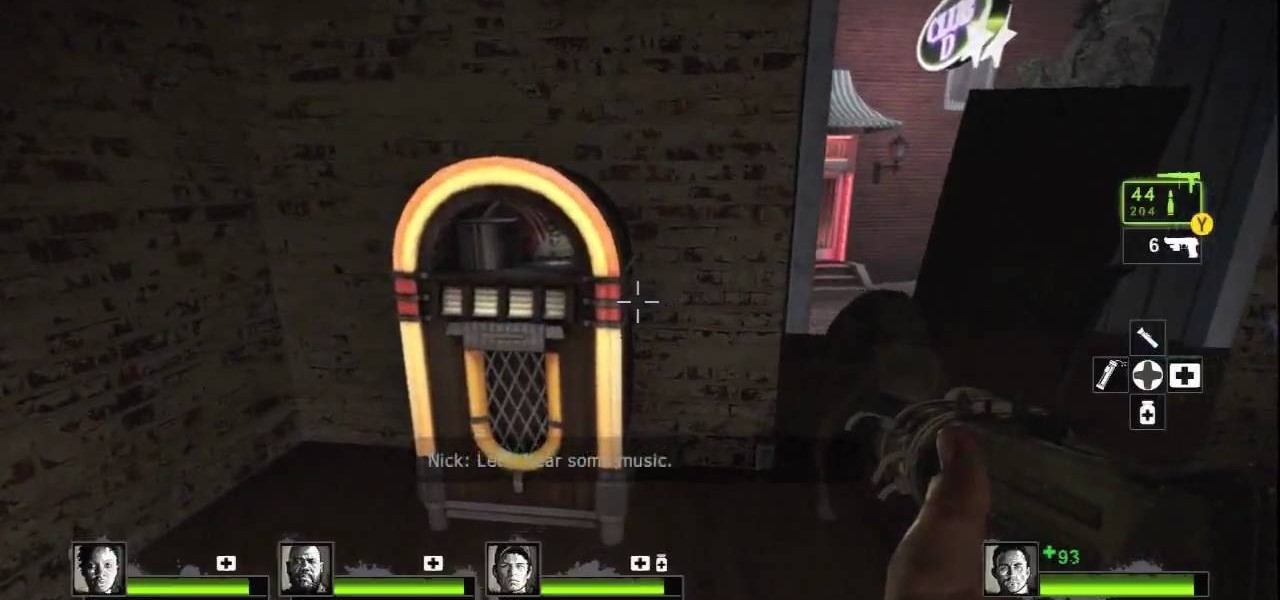
It's time to lock and load, achievement hunters! This tutorial is on the popular zombie shooter, Left 4 Dead 2. This takes place in their DLC, The Passing. The achievement is called Killing 'Em Swiftly and it requires you to find a jukebox and find a new song to play. It's an easy 20 gamer points to add to your gamerscore. So check it out and good luck!

Here's another Red Dead Redemption achievement tutorial for all you hunters out there. In this video, you'll have to be able to have access to the North in RDR. Once you do, find the buffalo and shoot as many as you can but let them run off. Then setup camp or fast travel to another place and comeback. Keep doing this until you've killed the last buffalo. Once that is done, the Manifest Destiny achievement is yours. So good luck and enjoy RDR!

For all you achievement hunters out there looking to rack up your gamerscore, here's another video that may help you on your quest. If you've played any of the Skate series, you already know how awesome the game can be to play. In this tutorial, you'll be finding out how to get the Extreme Grindage achievement in their latest version, Skate 3. To get it, all you have to do is perform a 100 meter or 300 foot grind and boom, 10 gamer points are yours. So check it out and enjoy!

Just like the Pokemon saying, "gotta catch em all!" That quote is in reference to all the easter eggs that are available on the title Just Cause 2 on the Xbox 360. The guys at Achievement Hunter will be taking you on another trek to find another awesome easter egg. In this tutorial, you'll be finding the bubble blaster easter egg. It's a fun, cute little easter egg that will have you weilding a purple little bubble blaster. Enjoy!

The guys and Achievement Hunter are here again to give you a quality video on how to jump the shark on the Skate 3 demo for the Xbox 360. Although this tutorial does not help add any points to your gamerscore, it's a fun video on how to jump one of the most hardest obstacles in the game demo. You'll find out just how difficult it can be when you check out the video above. So sit back and enjoy!

ITS tactical is going to show you how to make a handcuff knot, which is usually used to restrain things. To make this loop you want to make 2 loops, the first being an overhand loop, while the second is an underhand loop. Once you make the loops you want to stack them and then reach inside and grab one side of each loop with the opposite hand and pull the loop through, which if done correctly should create a loop on the right and left. By creating that type of knot it can be used on game if y...

In this video we are shown a workout that targets your stomach and helps you to lose belly fat and tighten your lower abs.

Shooting a recurve bow in archery is different than other bows. Learn about shooting a recurve bow including draw length and arrows in this archery video tutorial. Take action: keep glove tight, use a more instinctive shot, and expect less accuracy. John Swindle, the instructor of this how-to video from Live Strong, is the owner of Arrowhead Archery in Tampa, Florida. He has been an archer and a bow hunter for over 18 years.

Recurve bow or compound bow? Learn the differences between a re-curve bow and a compound bow in this archery video tutorial. Take action: use consistent shot, ensure consistency to allow for humane shots, and expect 20 yards with recurve bow. John Swindle, the instructor of this how-to video from Live Strong, is the owner of Arrowhead Archery in Tampa, Florida. He has been an archer and a bow hunter for over 18 years.

Take a look at this instructional video and learn how to fit a projected image onto a target surface with Johnny Chung from Carnegie Mellon University. Typically, you'd need to use a screen to be directly in front of the projector and at a very specific orientation to get an undistorted image. What this tutorial is trying to accomplish is to place a screen at any location that is convenient and then calibrate the projector onto the target surface. This technique is used to automatically disco...

Watch this video tutorial to see how to make a ghillie suit, cheap and easy. But wait, what's a ghillie suit? A ghillie suit, or yowie suit, is a type of camouflage clothing designed to resemble heavy foliage. It's 3D camouflage, primarily used by military snipers and hunters, or to hide from terrorists. These camo ghillie suits include burlap and natural vegetation. Pull tall grass out, break down trees, hide yourself. Grab the burlap for less time consuming ghillie suit construction.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.