In this how-to video, you will teach your dog how to target objects with its front paws. You will need a clicker, treats, and a target such as a yogurt lid or ball on a stick. Take a treat and hide it under the object. Click when the dog does any paw movements towards the object. After ten successful tries, pretend to put a treat. Once the dog paws the object, show that there is no treat but still give the dog a treat. Once this is done, wait until the dog paws the object, and give a treat. I...

A lot goes into making a hunt successful, and most of it happens before you take to the field--like making sure your rifle is properly sighted in. It's not hard to do if you follow a few simple steps: first, and this is the first step when you do anything with a firearm, make sure it's unloaded. Make sure your scope is properly mounted and the mounting screws are tight. Remove the bolt from the rifle and sight through the barrel to make sure you're lined up with a sight-in target placed at 25...

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

Android 6.0 introduced a new feature called Direct Share that allows apps to pin a more specific set of targets to Android's share menu. You've probably seen it already—messaging apps will allow you to share a file directly to a specific contact instead of just to the main app, and there are several other implementations like this.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Five Phases of Hacking:- The five phases of Hacking are as follow:

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

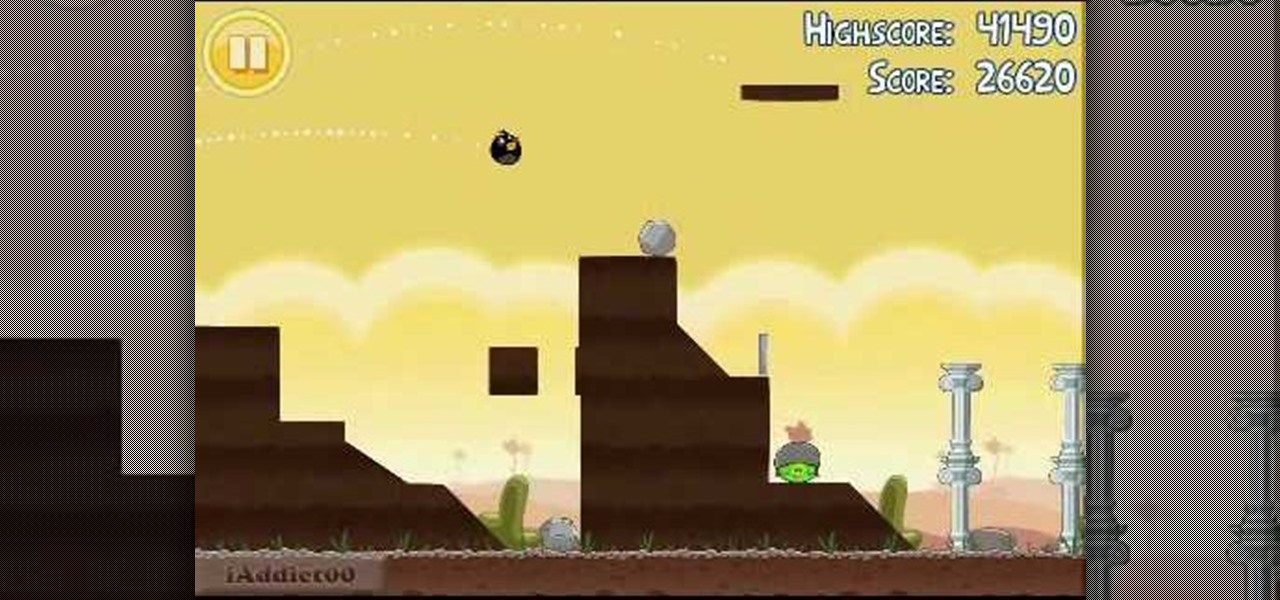
Your target in level 3-13 of Angry Birds is not so much a pig fortress but a series of pig-defended hilltops. Still no problem for a properly trained bird army. Watch the video for a guide to beating level 3-13 with three stars.

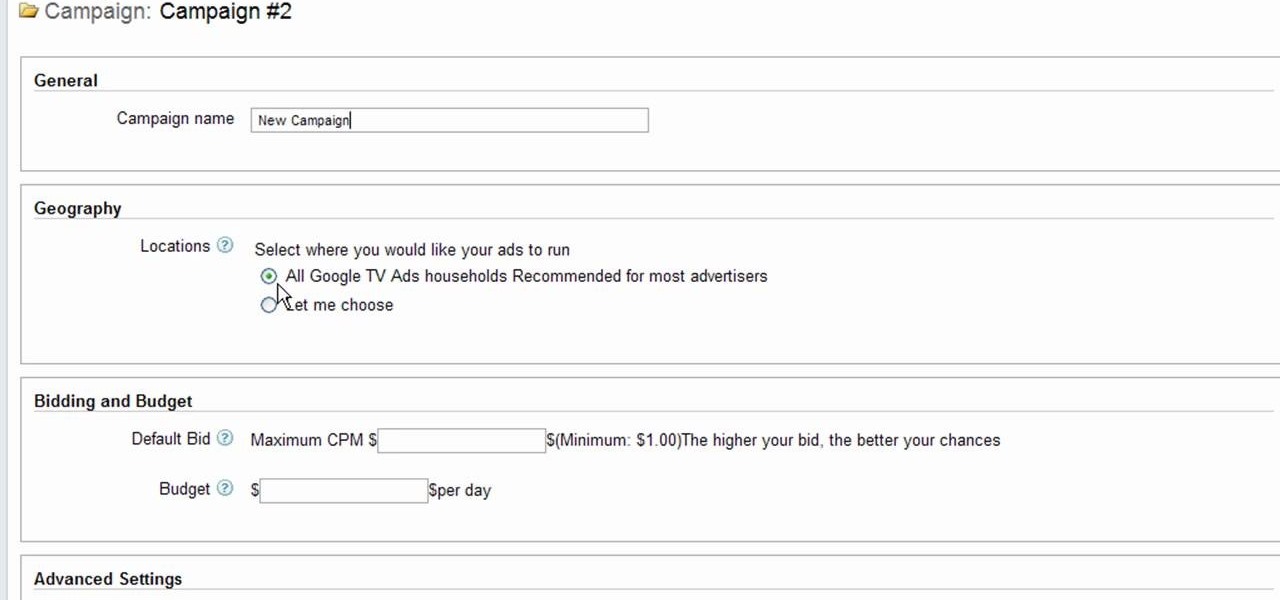
Interested to know how to start a new cable television ad campaign with Google AdWords TV Ads? This official video from Google will teach you how to use the new interface to determine just that. For all of the relevant details, and to get started creating your own televised advertising campaigns, watch this clip.

It's been a few years since Finding Nemo became the highest-grossing animated film of all time, but it's cultural appeal lingers on. If you want to capture some of that Nemo cuteness for your Halloween costume, watch this video to learn how to make a really cute Nemo costume with no sewing required.

The ground and pound is one of the most controversial aspects of MMA fighting, and is a great chance for you to do a lot of damage to your opponent. In this video UFC fighter Joe Lauzon will show you how to use an elbow technique from guard to defend yourself and get a solid elbow shot in at the same time, using Joanne from MMA Girls as his target.

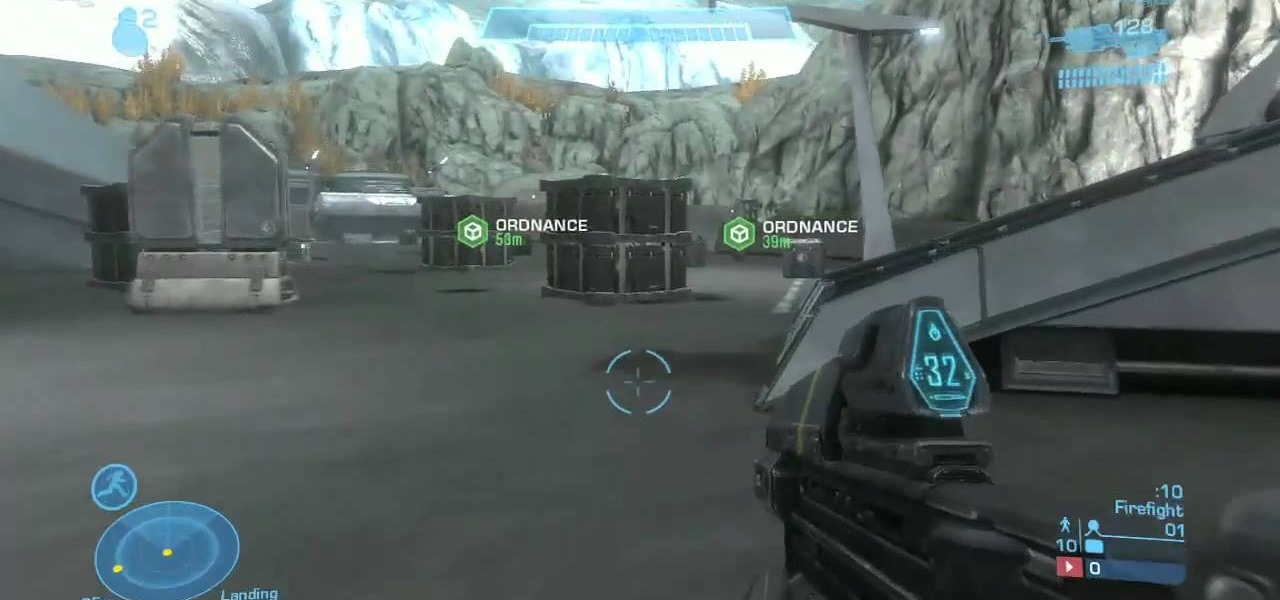
Halo: Reach has so many tough to get achievements, but the easiest one that you can get pretty fast is the "Crowd Control" achievement, and you can get it on Courtyard using the target locator. In this video you will learn how to effectively kill off multiple Covenant drop ships to get the achievement in about five seconds!

Two Corpses in One Grave is a difficult achievement in Halo: Reach if you don't know where to look on mission 3. You will have your chance right after you acquire the Target Locator when two Wraiths show up for the killing! Just be sure to aim straight and true and you will be alright!

Thanks to modern technology, we don't have to visit our nearest Target or Rite Aid to get our pictures professionally retouched and printed. With many printers offering photo-quality ink and paper companies that offer photo-quality paper, you can use your home printer to create professional-grade photos.

If you're planning to become a veteran yogini, you'd better start practicing and loving the up dog pose now, because you'll be spending the greater part of your yoga flow doing up dogs and down dogs.

Sometimes searching Craigslist can be a real hassle if you're looking for something specific. You really have to sort your way through all the clutter in order to find whta you're looking for. If you are looking for email addresses of people who might fit your target market, you can scrape Criaglist for emails. This video will show you how.

In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents for silent archival and email. For detailed instructions on replicating this hack yourself, watch this video hacking tutorial.

The new Splinter Cell video game has a co-op mode now, which means you don't need to play online anymore just to play against a human. You can have your best friend sitting right next to you… playing on the same Xbox 360. Forget the absurdity of playing in separate rooms, play in the same room. Splinter Cell: Conviction for the Xbox 360 is the way to go.

Try out some parkour… or maybe some freerunning… but it's dangerous, so how? By never letting "your" feet touch the ground (because they're resting on your ottoman). With Mirror's Edge, you never have to leave the house to get that free running and parkour feel.

MK vs DC. Sounds like the perfect game, doesn't it. Mortal Kombat vs DC Universe is a great two-player game for the Xbox 360, but what's even better is the fatalities from the Mortal Kombat characters. Maybe even the heroic brutalities from the DC guys.

Unlock the Endangered Species Achievement in GTA IV: Achievement Hunter presents this eight-part video walkthrough of Grand Theft Auto IV for the Xbox 360 or PlayStation 3. Knuckles takes you through a full walkthrough of the Endangered Species Achievement.

If you want a tight, lean stomach and obliques so sculpted you'd make Jillian Michaels jealous, then the only way to get what you want is to complete alternating days of cardio with strength training.

By combining different spells on the same target, or combining spells with other effects, you can do some devastating damage in Dragon Age: Origins. Turn your mage into an archmage by mastering effects like Paralysis Explosion, Grease Fire and more (including the deadliest, Storm of the Century)!

If shield kicking is legal in your game, here's how you can safely and effectively kick your opponents shield (and perhaps even knock them down). Know what's a good target, and a good way to deliver the kick without exposing your leg to be hit in turn.

This next video, is a great blend of woodworking and technology. In the tutorial, you'll be finding out how to create a wooden frame for the small digital picture keychains that can be bought from stores like Target and Best Buy. It's a great gift idea for parents, relatives, or just for you. So check it out, take notes, and good luck!