IT is a competitive field, and finding success requires more than knowledge of a couple of coding languages or knowing how to google really well. To stand out among your peers and competitors, you should learn everything you can and get as much diverse experience as is available.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.
Earlier this year, NASA reported on findings that might point to water, and microbial life, on moons orbiting Jupiter and Saturn. Named Europa and Enceladus, those moons contain large oceans under their icy surfaces, which many speculate could hold microbial life.

When building anything of a social nature, be it a local roller derby or softball team, a club dance night for chiptune, or building new technology markets, the community around those ideas are an important factor in helping these things not only come into existence but to grow into something that enlightens everyone involved. The community around an idea can actually make or break these new ventures — and this applies to augmented and mixed reality as well.

Bacteria gets a bad rap. Most headlines focus on the danger and discomfort posed by pathogens like bacteria, but many of the bacteria that live on and in us are vital to our health. Many products out there, called probiotics, are sold with the implication that they're supporting these healthy bacteria that share our bodies — but do they actually work?

When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Though many students spend four years of high school learning a foreign language, most of us probably retained very little. Chalk it up to the carelessness of youth, but chances are you've since been in situations or places that left you wishing you paid more attention in class or had continued practicing long after you graduated.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Unless your work clothes require dry cleaning, you probably only go to the cleaner a few times a year. And for those few items in your closet for which you do, you have to then find the time and extra budget to make a trip all the way to the cleaners and back again. In the end, it can be quite the hassle.

Want to play a beautiful version of "Beautiful Day" by U2? See how it's done with this free video guitar lesson, which presents a complete (and we mean complete) breakdown of the song and its constituent parts. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Beautiful Day" on your own guitar, watch this video guit...

Want to play "Until the End of the World" by U2? See how it's done with this free video guitar lesson, which presents a complete (and we mean complete) breakdown of the song and its constituent parts. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Until the End of the World" on your own guitar, watch this video g...

Greg French talks to us about the different ways to reboot a computer to resolve issues in the computer. The first way is by pressing F8 key while startup after rebooting the system. When you insert a wrong driver for video card or something, sometimes when you boot the computer, it gives a black screen. Now he says you can resolve this problem by rebooting the computer and pressing the F8 key while startup. This will take you to a menu selection where you should select 'Safe Mode' and hit en...

I feel like doing a bit of chemistry today, how about you? To my knowledge, thermite is the hottest burning man-made substance. Thermite is a pyrotechnic composition of a metal powder and a metal oxide that produces an exothermic oxidation-reduction reaction known as a thermitereaction.

To assist developers and researchers in their efforts to create apps and services for automobiles, Volvo Cars has launched a new Innovation Portal with useful new tools and assets.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

Suddenly, Magic Leap's lawsuit against Nreal, as well as its barrier to entry in the Chinese market, appears to be as insurmountable as The Great Wall itself.

Augmented objects in the classroom are closer than they appear. Within celebrated the close of summer with Wonderscope's unveiling of a fourth installment in its iOS app, titled Clio's Cosmic Quest.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Augmented reality developers who have exhausted their treasure trove of video tutorials and panels from the recent Magic Leap developer conference can now shift their continuing education attention to Unity.

WaveOptics, makers of diffractive waveguides, has inched closer toward getting products featuring its technology to market through a production partnership with a consumer electronics company whose clients include Google, Microsoft, and Sony.

On Wednesday, in addition to uploading another batch of videos from its L.E.A.P. conference to its YouTube channel, Magic Leap also launched a new video series for developers called Spacebar.

At its annual MAX event kicking off on Monday in Los Angeles, Adobe gave the audience a new preview of its forthcoming Project Aero augmented reality authoring tool during the keynote presentation.

A new augmented reality cloud platform from German startup Visualix is working to give enterprises the capability to scan their own warehouses, factories, and stores and create maps for augmented reality navigation.

I hate folder names, especially the one Apple shoves down our digital throats. On a computer, they make total sense, but on my iPhone, it's just more clutter on the home screen. You can tell what folder is what just by looking at the app icons within it, so why are we forced to label them? Technically, we're not, since there is a workaround in iOS 12 and iOS 13 to make those labels disappear for good.

Augmented reality experiences for consumers, for the most part, are relegated to mobile devices at present, but creation and development of those experiences is still a province of desktop computers.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

While most kids his age are busy playing Fortnite, 11-year-old Yumo Soerianto is developing augmented reality games. Kids like Soerianto are the future of the augmented reality field — they'll likely be coming into their own as professional developers right as AR technologies become lightweight and powerful enough to be contained in a pair of sunglasses.

Using the ARKit 2.0 announcement as its springboard, software maker Adobe is looking leap up to the level of Unity Technologies and Epic Games, the companies making the go-to tools for creating augmented reality experiences.

Consumers are chomping at the bit for augmented reality smartglasses from Cupertino's finest, but one market analyst is saying not so fast, Apple fans. Meanwhile, automotive AR is gaining speed, with the latest milestone coming courtesy of a major investment in waveguides by Continental. And although mobile AR apps have already arrived, retailer Target is taking a different approach. So why is Target tinkering with web-based AR? Answers below...

Noted analyst Gene Munster is predicting that Apple's initial entry into the augmented reality wearables category will be a year later than previous reports have estimated.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

When you accidentally close out of an important tab on your iPhone, Safari's "Recently Closed Tabs" list really comes in handy. However, when it comes time to clear the list, things get a bit complicated. There's no "Delete" or "Erase" button on this page, but don't let that fool you — there are three easy ways to clear your recently closed tabs list.

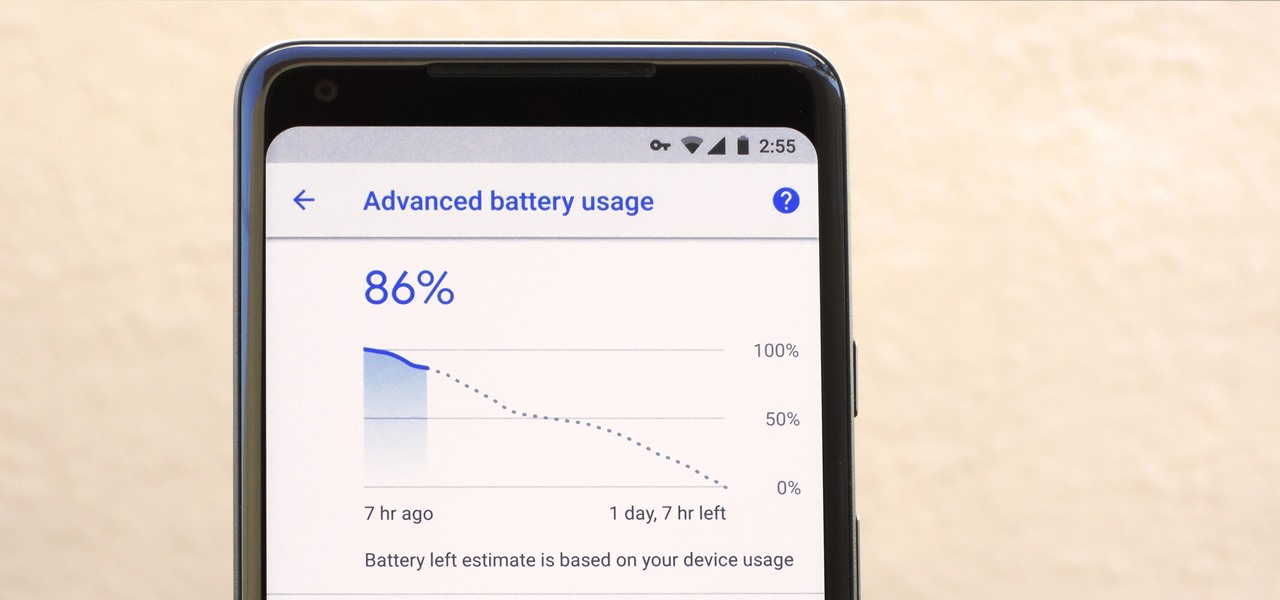
After Apple's recent fiasco, it's now common knowledge that smartphone batteries degrade over time. But aside from causing terrible battery life, a degraded battery can also trick your phone's software into thinking the device has more juice left than it actually does.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

While the public now knows much more about the Magic Leap One: Creator Edition today than it did yesterday, there's still a quite a bit that's unknown. One of the most significant questions — with any mixed reality product — is the field of view. How much of what we see through these glasses will contain the computer's virtual creations?