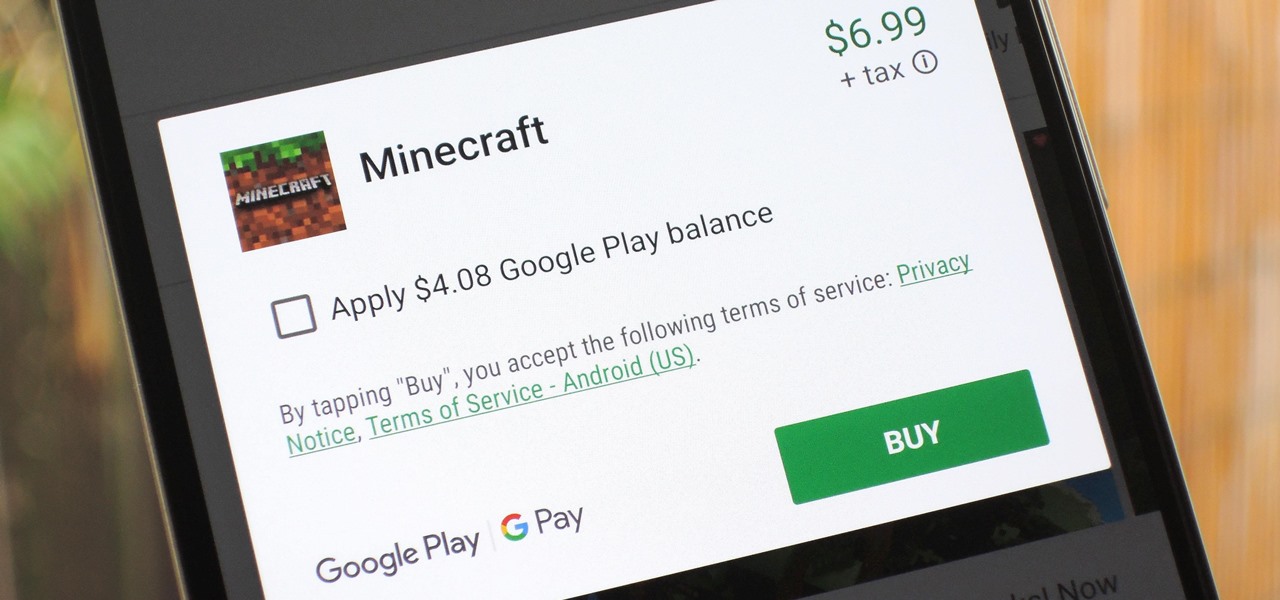
Halloween is this weekend, so if you're looking for a last-minute big batch cocktail that will keep your guests properly hydrated—and might turn them into mutants—look no further! (Note: This will not actually hydrate anyone, just so we're clear. Priorities, people!)

Avocados are one of the most universally loved foods, yet a lot of people avoid them because they can be a hassle to cut, especially if you're trying to make cubes.
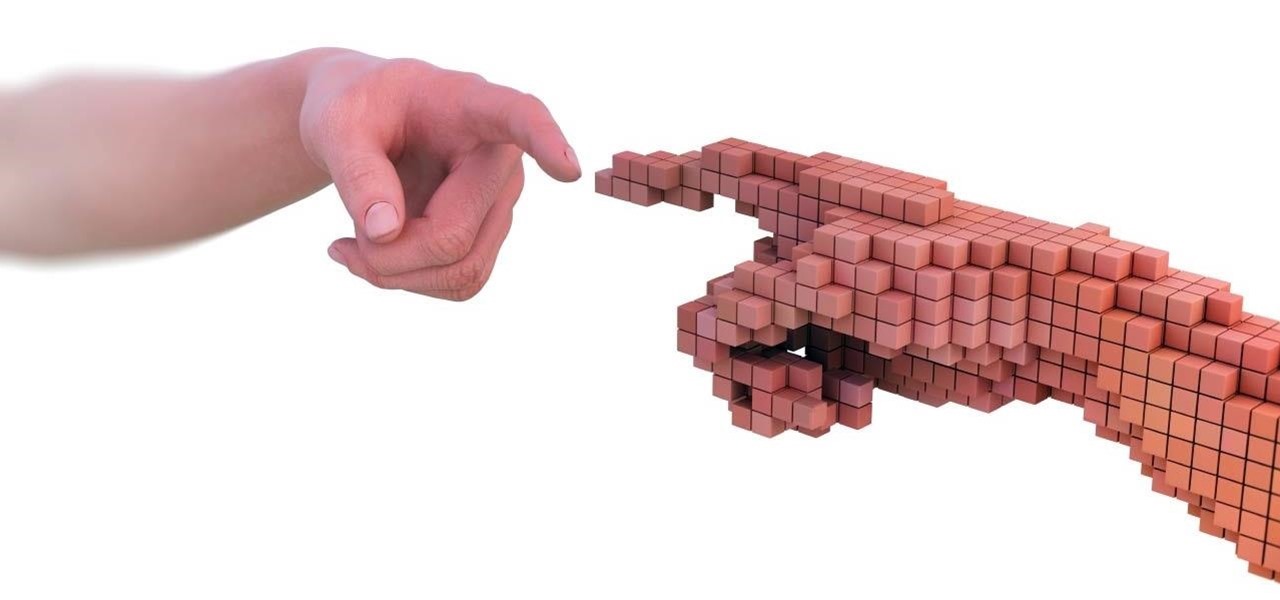
Augmented reality (AR) holds much promise for how we'll interact with technology in the future, but we still have many hurdles to clear before that dream fully comes to fruition.

Chopping veggies is pretty straightforward: grab the right knife and start slicing. Nothing to it! However, the way you cut your food does affect the length of time it takes to cook, as well as how evenly it cooks. So the next time you need to get your vegetable from hard and crunchy to perfectly soft in mere minutes, give the oblique cut a try.

It's no secret that the microwave is a modern-day wonder that, when used correctly, can cook a wide variety of food in a snap.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

I loved the original Star Wars trilogy when I was a kid, but loathe all of the current DVD, Blu-ray, and streaming versions available today. Ever since 1997, every version of A New Hope, The Empire Strikes Back, and Return of the Jedi has had horrendous CGI effects added in that George Lucas deemed necessary to bring his "ideal" version to life.

There are a lot of reasons for wanting to make sure your herbs last a long time. Maybe you know that your grocery store won't have decent parsley in the winter. Maybe you're taking a last-minute trip and don't want to throw away your perfect batch of basil. Or perhaps you're simply like me, and buy a dozen different herbs at the farmer's market, only to remember that you can't make it through all of them before they go bad.

Brought to you by Berocca® Video: .

Based on OTW's encouragement in his post on "How to Find the Exact Location of Any IP Address", I decided to make a gui(graphical user interface) which would hopefully make the process easier. However, because turning a python script into a standalone executable is a right pain in the nether-regions, particularly for linux, I haven't yet completed this step(I will soon and update this). I did however, make an apk for android(you use a .apk file to install an app on your android device), which...

Vacuuming is an easy, almost effortless task. With a few pushes of the vacuum, we can pick up pet hair, loose fluff, and other dirt and debris tracked across our floors. Yet there's one culprit that's harder to beat than all others—long strands of human hair.

I've been lucky enough to never be a victim of street crime, but I have read and seen too many articles and videos to completely rule it out as a possibility. You can do some things to prevent it, but if your life suddenly turns into a scene from Friday the 13th, you'll want to be prepared with some sort of way to let others know you need help. This is where Shake2Safety comes in, a free Android app from Phontonapps.

By now, everybody knows that overcharging a battery will reduce its overall life span. This is why many smartphone manufacturers recommend that you charge your device to 100%, then unplug it immediately. Some even go so far as to automatically stop charging when the device is fully juiced, although not all devices have this functionality.

Most of us know how to make a sandwich, but how many of us know how to make a sandwich correctly—i.e., so that the slippery ingredients like tomatoes and cucumber don't come gushing out the other end when we take a bite?

Most of you probably spread ketchup all over hamburgers and fries. Some of you may even drink it straight. But did you know that tame (and slightly addictive) condiment in your fridge is also a powerful cleaning agent?

Toilet paper isn't the first thing that comes to mind when you want a hot meal, but when you're camping or out in the field (i.e. military training), a little TP is the difference between cold tuna and luxury.

Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks at Facebook are using this technology. Obviously, this brings up some pretty serious privacy concerns amongst most people, because honestly, who wants to be tracked? Right now, there's not a lot we can do about it being ...

This short construction tutorial video shows how to build a small, simple stage from scratch specifically for animating a claymation or stop motion animation project. Construct the ideal world for your claymation characters or stop motion animation armatures and puppets. All you have to do is follow this video then drill holes wherever you want your tie downs to pass through and you're off to the races. Just use the following materials to build your own stage: an armature with foot tie-downs,...

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EXT Backpack Telescope to ogle the universe.

In this gardening tutorial, Martin Fish from Garden News demonstrates how to prick out Foxglove seedlings. "Pricking out" is when seedlings are transplanted into larger pots or trays to give them more room to grow on. The ideal time to do this is when the seedlings are at the two-leaf stage and before the true leaves have developed, or as soon as they are large enough to handle.

Robert Kowalski shares what types of foods to eat to lower blood pressure, without the use of medications.

Ever want to have a friendship bracelet with your own personal saying on? Well, it's going to take a lot of experience to get there. Start off with learning the basics of friendship bracelet making, such as the basic knots and skills. When you think you are ready for a challenge, try to write your name in a bracelet. This video is ideal for learning the letter "i". "I" is a very common letter to be in first names and it is probably found in yours too! After learning how to make the "i" try to...

If you grow your own bedding plants one of the main jobs over the next few weeks is 'pricking out'. This is when seedlings are transplanted into larger pots or trays to give them more room to grow on. The ideal time to do this is when the seedlings are at the two-leaf stage and before the true leaves have developed, or as soon as they are large enough to handle. When done at this stage of growth there is less shock and root disturbance to the seedlings and they will establish and grow on much...

We prune roses for several reasons. Regular pruning helps to keep their size under control, though we must remember that all roses have a predetermined 'ideal' size. We also prune to shape the plant. We take out dead stems to prevent the dead area spreading back into healthy stems. But the main reason we prune is to make the rose more vigorous. This tutorial teaches you how to prune climbing roses for the best results.

Get a new perspective on computing with an HP Tablet PC. HP's Tablet PCs are well-equipped personal notebooks, with a significant twist. The display turns around one hundred and eighty degrees, transforming your notebook into a flat tablet touchscreen PC.

If you have a cat, trying to get all of the little clumps out of the litter probably feels like an impossible task. It pretty much is, but we've found the best cat litter scoop that gets more of those tiny pieces out than any other scoop. Plus, it's sturdy, degradable, and ethically sourced.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.

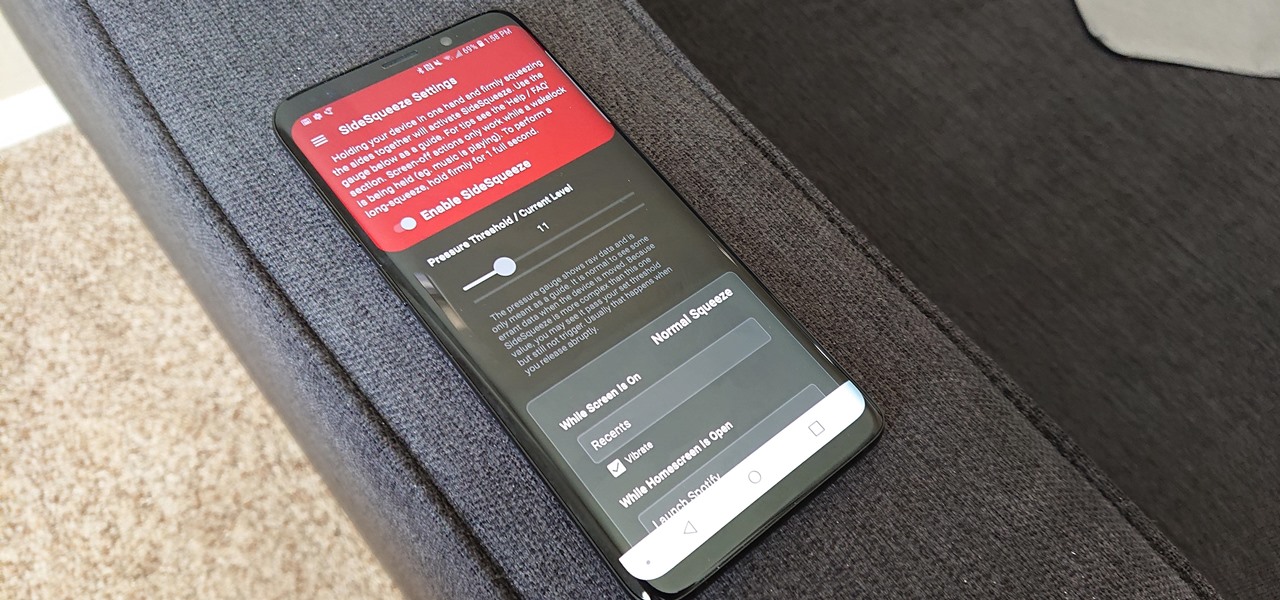
All the Android fans out there undoubtedly remember the squeeze gestures introduced with the HTC U11. Google continued the trend by bringing the gestures to the Pixel 2 and Pixel 2 XL. Thanks to a brand new app, you can now enable similar squeeze actions on your Galaxy S9 or S9+, and even some older Samsung phones.

While not cuddly to most, bats are shy, skilled flyers that fill an important role in their environments. A new study reveals a deadly disease decimating North American bat populations has stepped up its attack on vulnerable bat populations in the summer months.

Montezuma's revenge, the runs, the trots, or just diarrhea — everyone gets it sooner or later. What exactly is diarrhea good for, if anything?

Breastfeeding is the ultimate in farm-to-table dining. It is sustenance prepared just for the baby and delivered with a very personal touch. Along with bonding, breastfeeding provides powerful protection to infants and young children in the form of beneficial bacteria, hormones, vitamins, protein, sugar, and antibodies manufactured on site to support infant health.

As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight.

There's an adage that says "Every plan, no matter how great, goes out the window as soon as you're punched in the face." While our lives are (hopefully) not violent, that saying can easily translate to our daily living. That punch in the face can come in various forms, mainly stress-related. It could be a bad day in the office, rush hour traffic, drama in the family, the list goes on.

The sweet aroma of cooked fruit filling your kitchen is one of the trademark scents of summer. Yet attaining the perfect consistency for homemade jam can be difficult to master. Often it ends up a watery mess or over-solidifies into thick mystery goo that is destined for the trash, not topping your toast.

I've been a fan of potatoes ever since I can remember... but mainly because they weren't a big part of my daily diet (which usually consisted of rice). And because my experience with potatoes was so limited, I only knew of two varieties growing up: big, brown Russets and sinewy sweet potatoes. As for cooking with potatoes—well, I'm embarrassed to admit that the only time I cooked potatoes when I was a kid was with the instant kind.

Having a store-bought cold pack on the ready is the perfect solution for minor bumps, bruises, sprains, and strains, but why spend money on bright blue ice packs when you can make your own right at home?

Just what are probiotics and why are they so good for you? Probiotics are "viable microorganisms" that can confer lots and lots of health benefits if they reach your intestine while they're alive. You may have heard them described as "friendly bacteria."

If you're one of the many professionals transitioning to working from home amidst the current pandemic, there's a good chance you're now realizing how far behind your at-home setup is compared to what you had at the office.