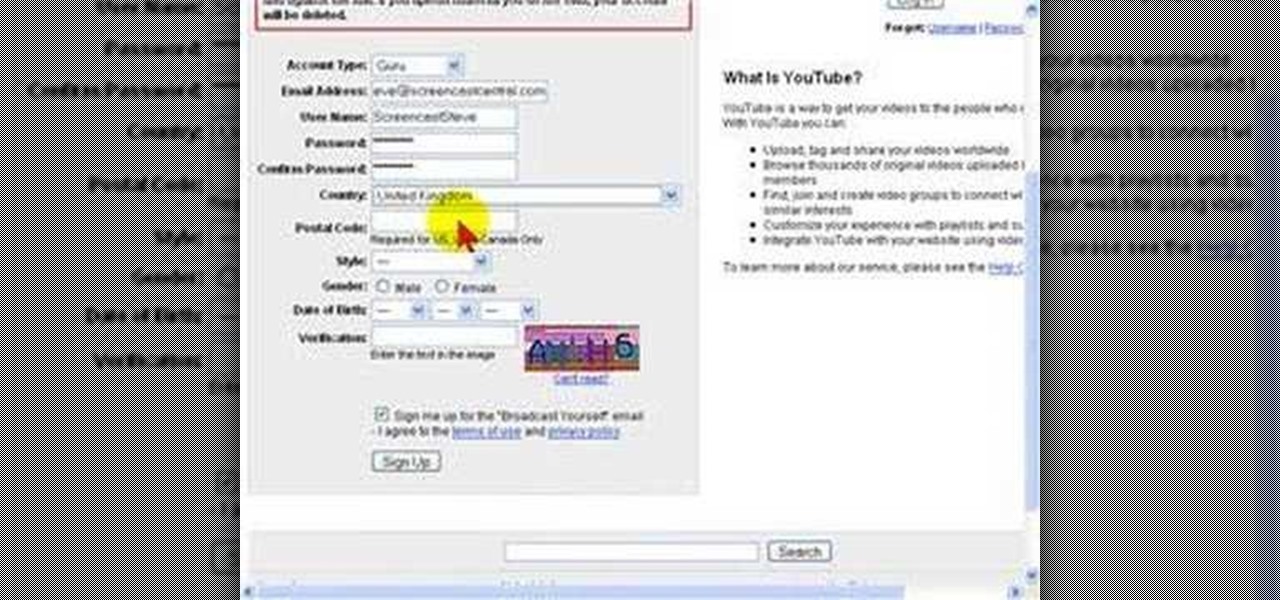
How To: Sign up for an account on YouTube
YouTube is the latest craze to hit the web, allowing users to upload and distribute their own videos. YouTube now boasts more than 100 Million Video Views per day.


YouTube is the latest craze to hit the web, allowing users to upload and distribute their own videos. YouTube now boasts more than 100 Million Video Views per day.
John demonstrates using Google Notebook and Google Apps with web shortcuts and the Mac OS X Dock.
John Hendron shows you how to "subscribe" to free content found on the Web using a (free) "news aggregator" called Vienna. Find out what to do with those orange RSS/XML buttons and more.
http://AskTheTechies.com Brandon Jackson is back with D.Lee Beard to answer "What files are safe to trash on a Mac to free up hard drive space?" What files are the biggest hogs? Have you really trashed all the files you thought you had? Also in this episode: how to sort web browser bookmarks.

Learn how to increase the speed of the Firefox web browser using the FasterFox add-on.
This tutorial demonstrates how to turn on Safari's Debug mode so you can use additional functionality like the JavaScript console, Web Inspector, and spoof Internet Explorer.

A non-geek tutorial for anyone who wants to take advantage of google's free, web-based e-mail program. This tutorial guides you step by step through the process of how to sign up for and delete a G-Mail account.
Why would you want to have an action just for creating a 500px size image? Well, that's the perfect size for posting images on a forum, and if you create an action in Photoshop to do this, you'll never have to manually resize an image for the web again! Learn how to create, and customize this action.

Use a hot glue gun to craft a large spider web to use for Halloween decorations (or to catch giant mutant flies).

A simple method for setting up a slackline with 5 carabiners. This setup should not be used for highlines. Practice this circus trick of balance and skill. You need webbing for this slack lining technique.
How to convert videos to various formats (including web format) with VLC Media Player, free open-source media player
Learn how to Import External Data (i.e data from web pages) dynamically into Excel in Microsoft's Office 2007.
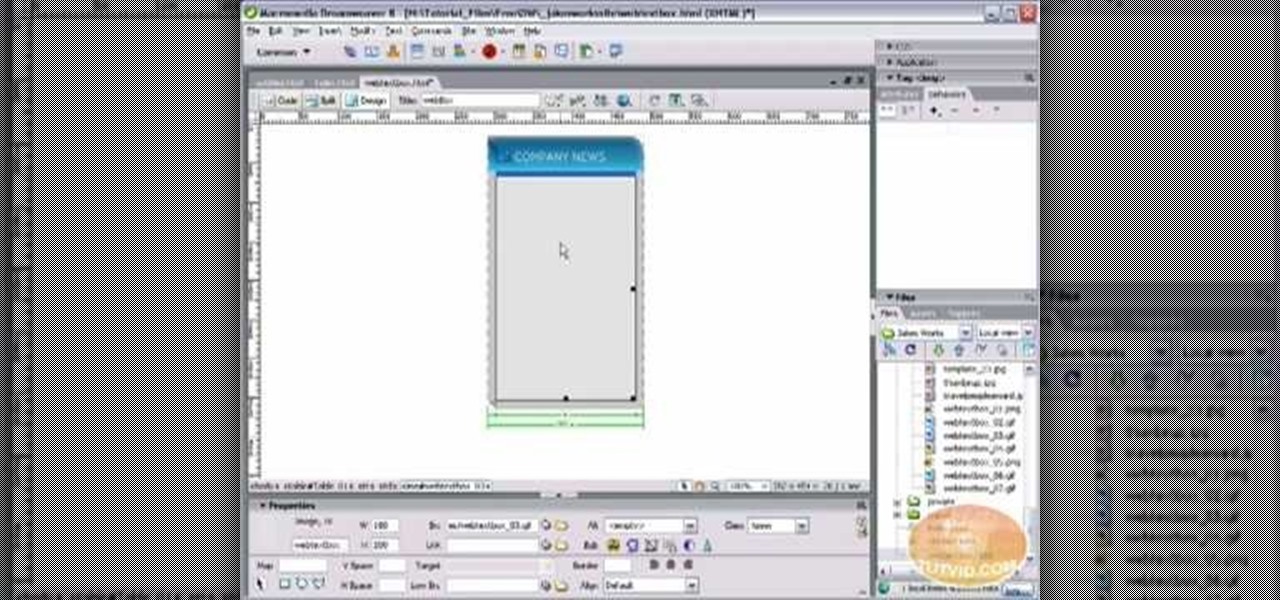
Learn how to create a web text box using Dreamweaver that get bigger or smaller depending on how much text you place in it. Also make a header that spans the users screen not matter what size.

The existing uninstall routine for the Mozilla Firefox web browser may leave profile data and a Program Files folder behind. This is how to remove it.
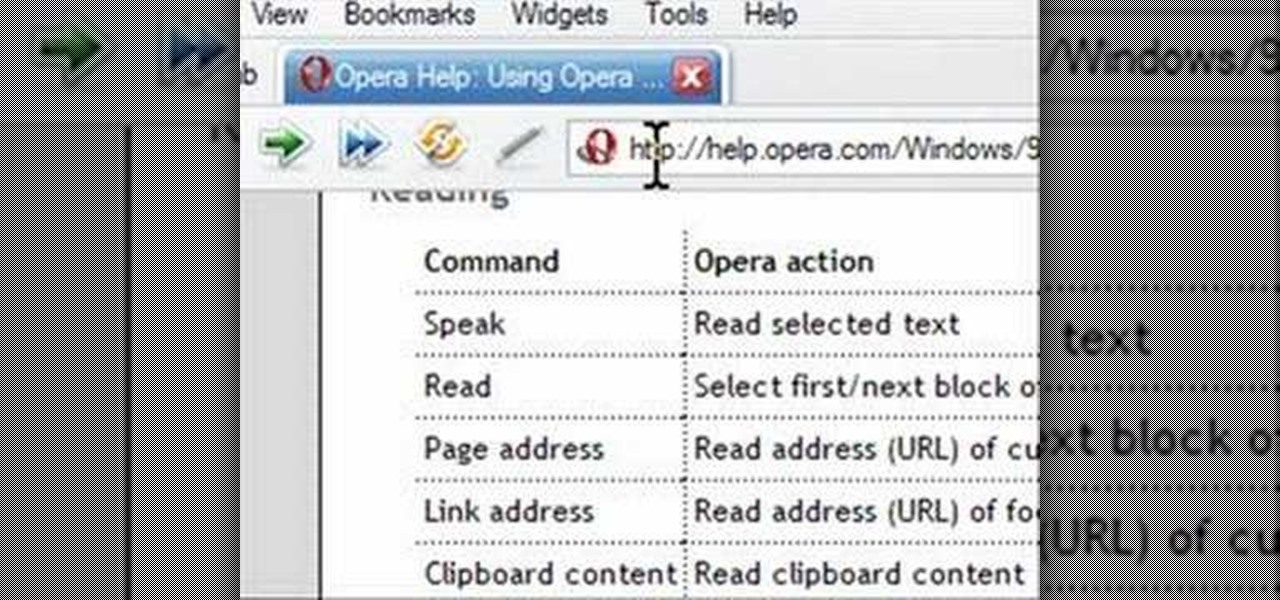
Opera has a feature where you can talk to it and it obeys your commands - and it works! No "voice training" required. Learn how to use Opera Voice.

For all you whos resolution it was to start making your own clothes and DIY'in, this week were taking a look inside the mysteries of the sewing machine plus a look at our 2008 top DIY web picks.

Backpacker magazine shows you how to build a plastic footprint for your tent--a skill taken from the Jan/Feb 2007 issue. Associate editor Jason Stevenson explains the nine steps to create a footprint, including how to cut webbing and punch grommets. Learn more Skills at www.backpacker.com.
Once your video is on the Web you can share it with friends and family in an instant. Learn how to export with Windows Movie Maker so the best possible version of your video is shared.

This video demonstrates how to connect a PSP to a home wireless network. To do this, just turn on your PSP, create a new network connection, and start the web browser on the PSP.

When you want to encode your video for DVD instead of for the web, there are a few extra steps you have to take. You have to split your source media into seperate streams. See how to do it in Compressor 3 in this tutorial.

Rebecca Katz explains how to export your finished project for the web using Apple iMovie. The final menu will allow you to title your film and save it to a location of your choosing.

Watch the Grillmasters at the Barbecue Web prepare some beef chuck burgers so juicy and full of flavor that it will no doubt become one of your favorite quick and easy BBQ recipes. It's quick and easy. All you need is 3-4lbs fresh ground chuck beef, tomatoes, sweet onions, sliced cheese if it's a cheeseburger you want, and any of your favorite condiments.

Trimming spare ribs into St Louis style ribs is demonstrated in this Barbecue Web video.

This video tutorial takes a look at how to create layers in Photoshop CS2 that build up to your signature. Then we'll pop over to Adobe ImageReady to put the finishing touches on animating that signature so that it can be used on the web or in your email application. Check out this Terry White's video now!

Our gardening expert will explain how to set up your perfect perennial plant business. Learn which plants go together, how to position the plants for just the right amount of sun, and how to determine if your adjustment has been successful. Are the flowers, shrubs and grasses happy after all of the work you have put in to meet their needs? Once you have mastered the basic care and maintenance of your garden, then you can concentrate on working toward exactly the look you want. Martha Cycz dis...
The chunin exam. It's one of the hardest parts of Ninja Saga. Can you pass the test? Or do you need a little help on this exam?

Ready to make a statement in your town and get involved? Check out this tutorial and learn how to run for mayor. If you can't beat city hall, why not join it?

There's nothing more disappointing than finding yourself all packed and ready to travel when you find your flight has been canceled. You can make the best of the situation by finding out just what you are entitled to or how to best ameliorate the situation.

You have a purebred, make it official. With a few simple forms your purebred dog can be a member of the American Kennel Club and carry on the traditions of and gain access to this exclusive organization. Your dog can have an official pedigree.
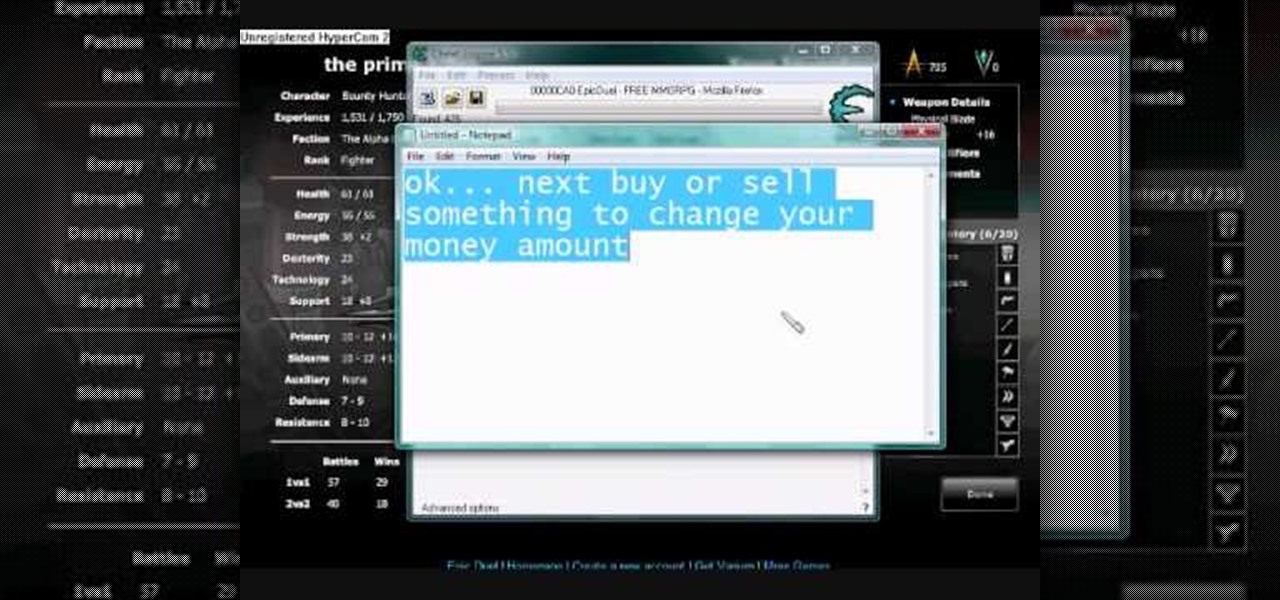
There's a great new web game called Epic Duel out on the internet, and everybody's playing it, but not everybody's hacking it, except you! Outshine them all with this EpicDuel cheat with Cheat Engine 5.5.

If you've been thinking about changing careers and you have just a little bit of time, The Ultimate 2021 Web Developer & Designer Super Bundle may be just what you need. This is also the perfect time to get it because it's on sale for $34.99, which is 98% off the regular price of $1,886. You'll get 14 courses that offer 39 hours of content on HTML, JavaScript, CSS, and more.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.
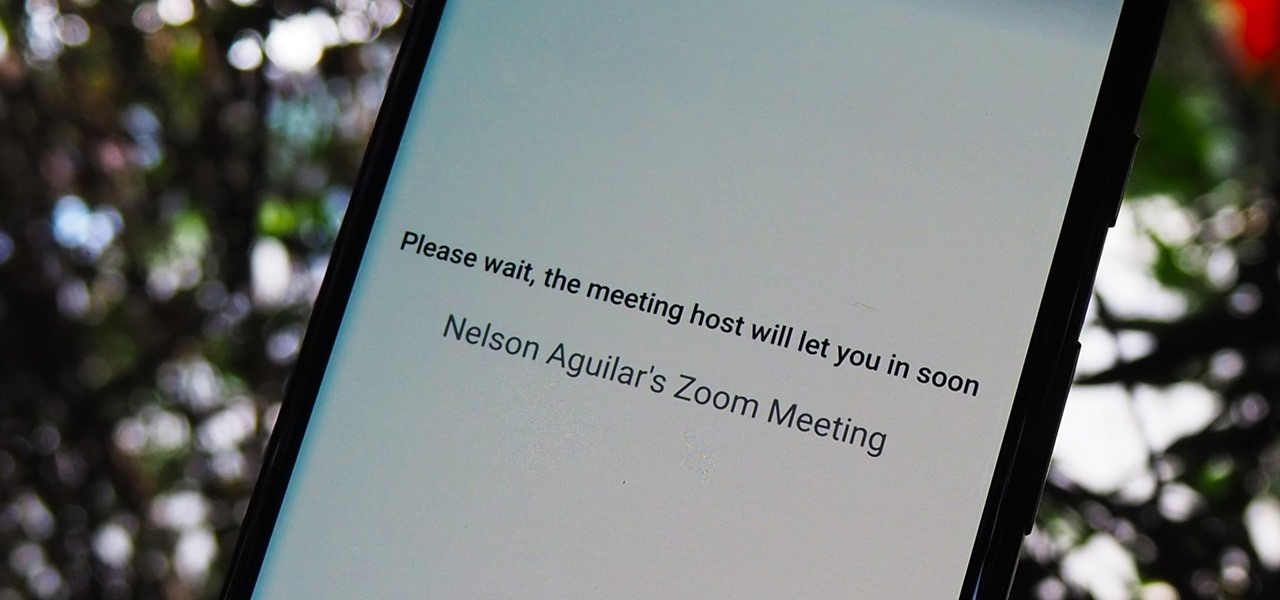
The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Filmed in what appears to be a single continuous shot, war film 1917 is now the front-runner to conquer the Best Picture category of the Academy Awards after bringing home the Golden Globe for Best Motion Picture in the drama category.

What better band than Pink Floyd, the pioneers of psychedelic and progressive rock, to show the music industry how to reinvent album art for the augmented reality age?

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Smartglasses from Apple have become the holy grail of augmented reality, and 2020 has been the rumored time horizon for the product's arrival for the past two years. The latest analyst report sheds more light on its potential debut next year.
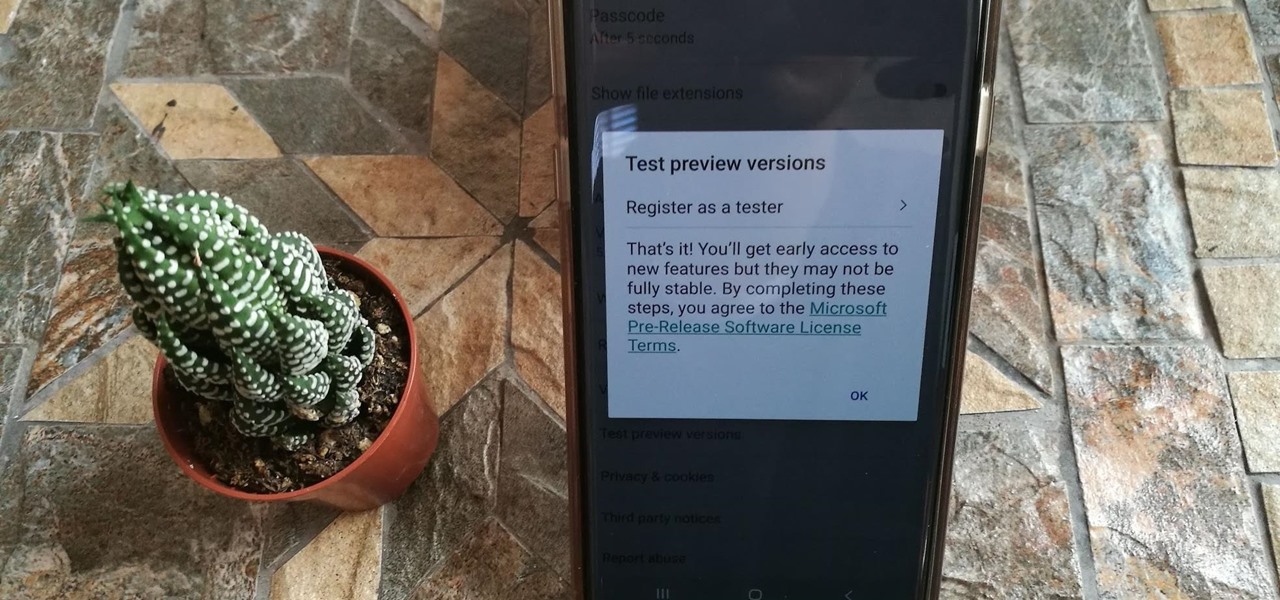
OneDrive has some really cool features, like being able to lock your files with a fingerprint. If you want to be on the forefront of these new features, you can sign up to the OneDrive beta testing program to get new feature before anyone else.