Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.
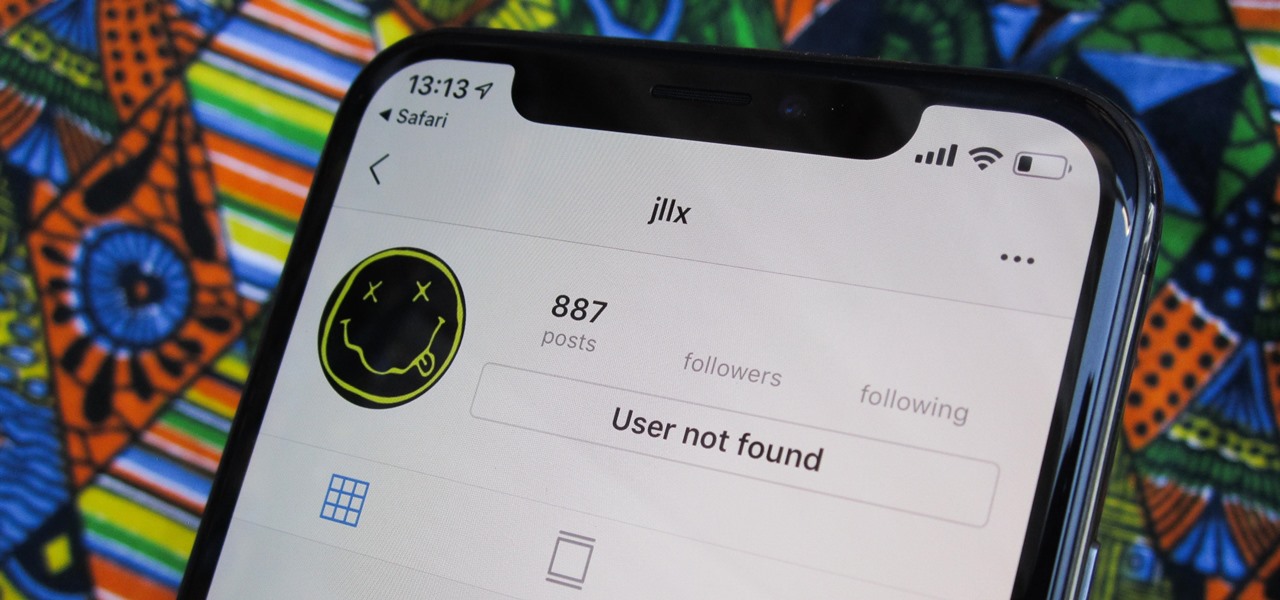
When you don't want certain friends viewing your account or just need to take a break from social media, Instagram lets you do so. While you can completely delete your Instagram account, then start over when you're ready again, it makes much more sense to just disable your account temporarily. Doing so will hide your profile, photos, comments, and likes from everyone, including your friends.

Already a powerhouse for its graphic design tools, Adobe is making a run at the 3D content creation realm dominated by Unity and Epic Games by acquiring software maker Allegorithmic.

The Google Feed is a great source for relevant news articles from your search history, package delivery updates, and much more. Now known as the "Discover" page, many Android users turn to this useful menu on a daily basis. However, as Google recently pointed out, the all-white theme is not ideal for battery life, nor is it easy on the eyes at night.

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

The holidays are here, which means a slew of new smartphones are set to be gifted to loved ones in the spirit of giving. Of course, a great case to compliment and protect that precious flagship is a must, regardless of whether it's a OnePlus 6T, iPhone XS, or Galaxy Note 9. And while quality cases usually come with a hefty price tag, there are plenty of Black Friday deals to keep you from going broke.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

This week, Next Reality published profiles on the leaders in augmented reality hardware industry, with Magic Leap CEO Rony Abovitz topping the list. So, it should be no surprise that two app makers want to align themselves with Magic Leap's flagship product.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

Apple revealed three new iPhone models on Wednesday, Sept. 12, at its "Gather Round" event in Cupertino, as well as announced the official release date of iOS 12, its newest mobile operating system. If you missed it and want to watch the full event, here's how to do it on your computer, smartphone, or Apple TV.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Augmented reality app developer Laan Labs has shared a preview of a beta app that achieves 3D scanning with just an iPhone and produces highly-detailed models for sharing with others.

As a longtime Android user, one of the changes I was most excited about with Android Pie was the fact that the volume rocker finally controls media volume by default. However, the new way isn't ideal for everyone, but thankfully, there's an app that can change it back.

On Friday, the release date for her new album, Queen, Nicki Minaj is already grabbing headlines for the track "Barbie Dreams," where she disses Drake and a host of other rappers.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

We learned during the LG G7 ThinQ announcement that AT&T would be carrying a new V series device, the V35 ThinQ. In the LG V35 ThinQ's press release, LG revealed its specifications but left out pricing and availability. Thanks to Project Fi, we now know its price tag, and you may not like it.

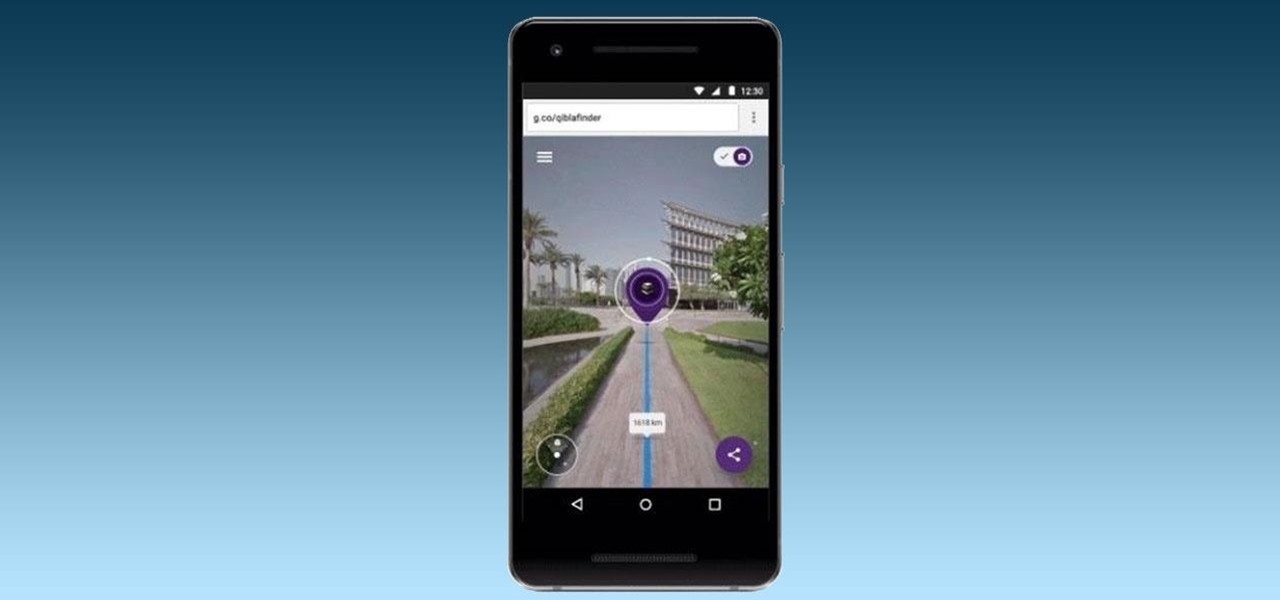
Ramadan, the Islamic holy month of fasting and prayer, is underway, and Google has rolled out several tools to help Muslims commemorate the event, including an augmented reality app.

While it's very easy to enable "Low Power Mode" on your iPhone, since Apple will prompt you to enable it once your battery dips below a certain percentage, it's not as obvious as to how to disable it. If you start charging your iPhone, it won't automatically disable it right away, but there are a few ways you can manually disengage it to get your iPhone running at top speeds again.

When it comes to traveling from one location to another with the aide of your iPhone, ensuring your navigation app works as it should keeps you one step ahead of potential hassles. One feature often overlooked is audio settings, and while having no voice prompts is easy enough to ignore while walking or commuting, having no sound to guide you while driving can spell disaster.

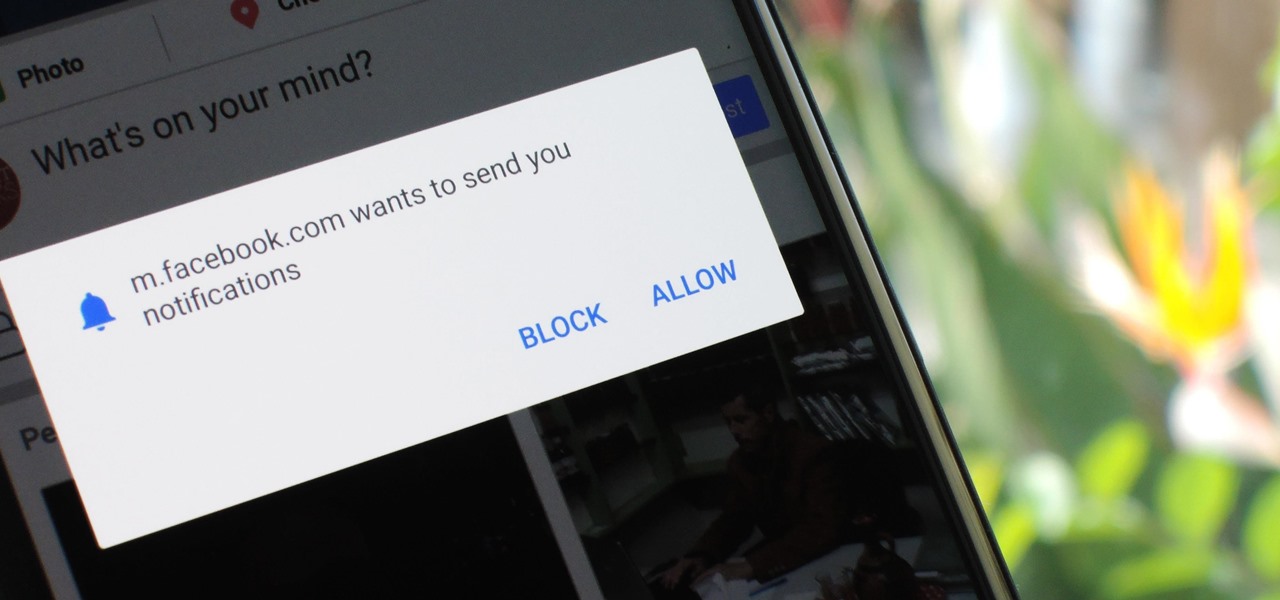
As the go-to browser for millions worldwide, Chrome makes web surfing a breeze with its simple interface and Google integration. But many websites are starting to ask if they can send you notifications, and this can interrupt your browsing. Thankfully, you can completely disable these prompts if you prefer.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

While Instagram users can attach links to images, they can only do so in stories, and only if they meet the special requirements that most users cannot obtain. Snapchat, on the other hand, lets anyone add a link, and it can be done in regular snaps and in your story. This feature has only been around since July 2017, so you may have missed it and not even realized it was a possibility.

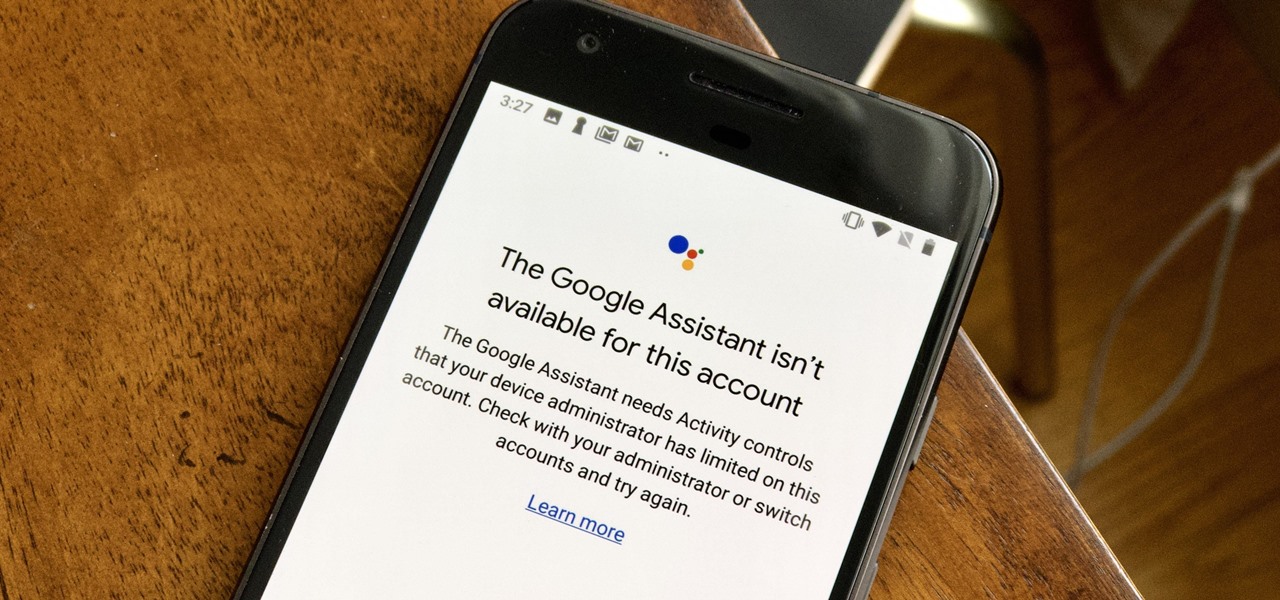
If your virtual assistant can't assist you, what's the point? Anyone who has ever failed to activate Google Assistant knows the frustration that error screen can be. But there are solutions for this problem — "The Google Assistant isn't available for this account" is one message you can actually avoid.

One of Android 8.0's best features is also one of its most subtle — customizable lock screen shortcuts give you more control over the two functions you care about most. Your Galaxy S9 has the Phone and Camera apps in those spots by default, but you can quickly and easily change them if you have other ideas in mind.

Your homepage should be the site you most likely need to check whenever you start a new session with Samsung Internet. However, times change — perhaps the site you're currently browsing is just what you need to see multiple times a day. In that case, you'll want to know a quick and easy way to set it as your default homepage.

The Galaxy S9 and S9+ have a new camera feature that Samsung is calling "Dual Aperture." On the surface, that may sound like your typical techno-jargon, but it actually has some significant implications for the future of smartphone photography.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

Enterprise augmented reality developer Atheer is bringing its AR solution for enterprise businesses to the HoloLens by way of a joint venture with fellow AR developer Design Interactive.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

If you're looking for an alternative iOS keyboard for your iPhone, look no further than Gboard. The Google-made keyboard is bursting with features like web search, Google Maps, GIFs, and more. Now, Gboard is adding a new feature that'll make it easier to find the perfect emoji.

Google's new AI-powered camera, Google Clips, seems to be targeted at parents of young children in its current form, but the idea itself has unique potential. Just set it up somewhere, then you'll never miss a moment trying to capture the moment — you'll have a robot photographer taking care of that stuff for you.

We knew it was coming, it was just a matter of when. Apple has just announced iOS 11.3, a new update for iPad, iPhone, and iPod touch, and it will include a brand-new set of Animoji for the iPhone X.

For the unaware, RED is a company that specializes in high-end cameras and other recording devices. RED's cameras are used to shoot some of Hollywood's biggest films and TV shows. Their modular designs make them ideal for the user who does a lot of mixing and matching — and has a wallet to back their work up (their WEAPON 8K VV starts at $79,500).

A recent TED Talk makes a strong case for the healthcare industry to adopt augmented reality as a means to expanding access to surgical care across the globe.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Augmented reality has given companies worldwide great powers for innovating business practices and engaging customers, but on Monday, Honda demonstrated that with great power, also comes great social responsibility.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Usually paper beats rock. With augmented reality, The Rock beats paper. Using the Life VR app for iOS or Android, Entertainment Weekly readers can point their smartphones at the cover of the Dec. 8 edition to view a holiday greeting from Dwayne "The Rock" Johnson, star of the forthcoming reboot, Jumanji: Welcome to the Jungle.