Magic Leap loves to stoke mystery around its still unreleased product, the Magic Leap One: Creator Edition, and now we've found yet another piece of the puzzle in the form of an Easter egg on the company's website.

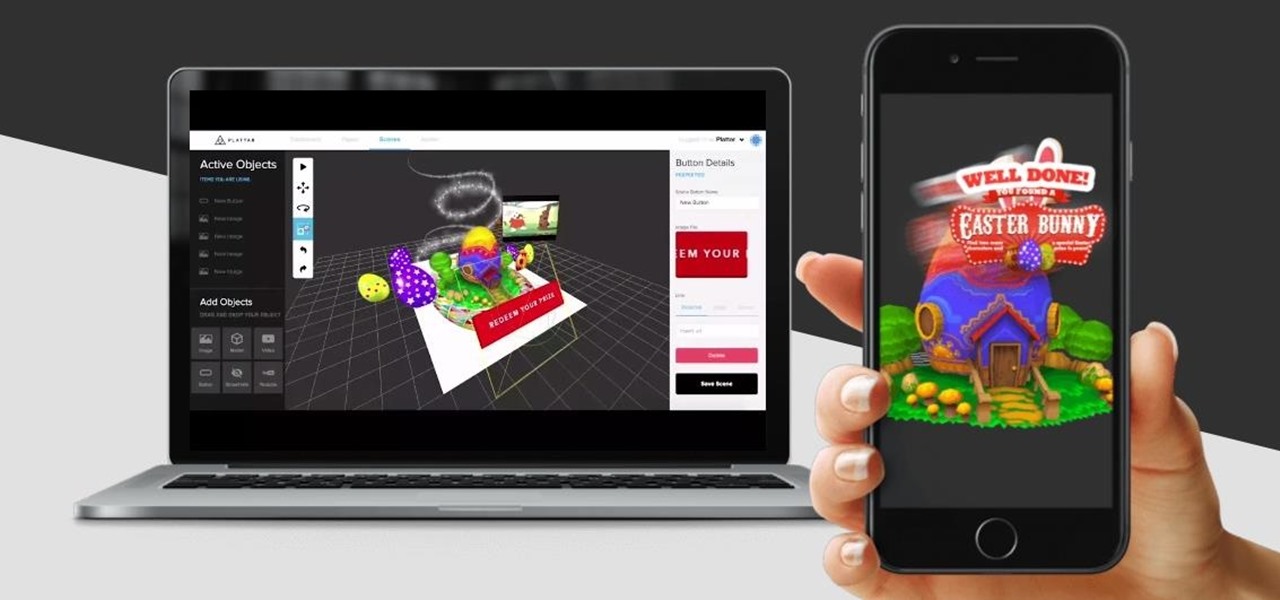
The augmented reality and VR arm of Verizon, Envrmnt, wants to make it really easy for anyone to create AR apps.

The business of enabling the development of augmented reality experiences appears to be as lucrative as AR app development itself.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.
Samsung Internet offers excellent features that enhance the mobile web browsing experience, often through its extensions. A QR code scanner, ad blockers, tracker blockers, and more work directly in the browser, so you can do exactly what you want to do on the web.

Getting an insider view of the goings-on at Magic Leap is hard to come by, but occasionally, the company lets one of its leaders offer a peek at what's happening at the famously secretive augmented reality startup. One of those opportunities came up a few days ago when Magic Leap's chief futurist and science fiction novelist, Neal Stephenson, sat for an extended interview at the MIT Media Lab.

Netflix currently lets parents block content based on maturity rating, but it isn't a perfect system. Not all titles rated PG-13 are equal, for instance. That's why it's good news that Netflix is adding more controls for parents, by allowing account holders to bar individual movies and TV shows they deem inappropriate.

A recent update to Facebook's News Feed could significantly broaden its reach when it comes to delivering augmented reality content.

Master director Steven Spielberg's virtual reality epic Ready Player One is coming to theaters in just a few weeks, but you can get an early look at some of the best parts the latest trailer, "Come With Me," which was revealed on Thursday.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Augmented reality software maker 8th Wall has closed a Series A funding round of $8 million in capital to feed the growth of its development platform.

For some of us, mornings are difficult. But if you can manage to start your morning right, you can trigger a chain reaction that leads to a more productive day. Fortunately, our phones have the tools to help us get off to a good start.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

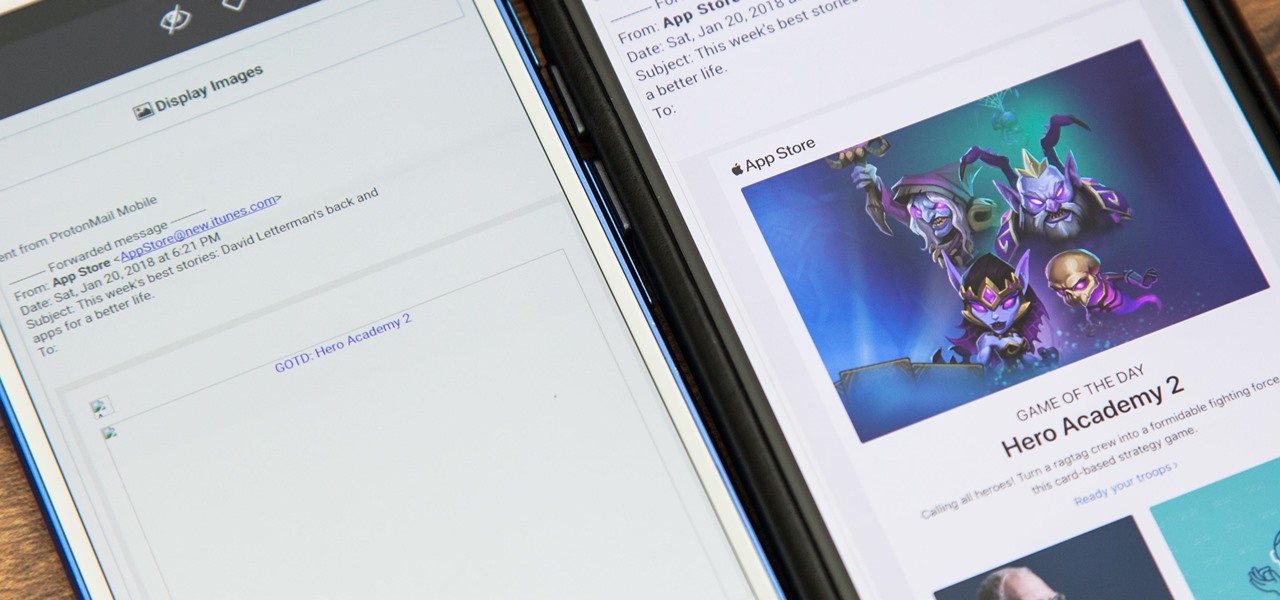
By default, images embedded using external links will not automatically load in any emails that you get with ProtonMail. This is a security mechanism that can prevent malicious code from being executed on your system, but it can also be fairly annoying to have to manually load images in email after email.

Although it sounds like a foodie's take on Facebook, what Calabasas, California-based FaceCake actually offers is more about augmented reality fashion marketing rather than food selfies.

Shanghai-based Realmax is introducing the crowds at CES to the Realmax Qian, an augmented reality headset capable of a field of view (FoV) that topples anything available on the market today.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

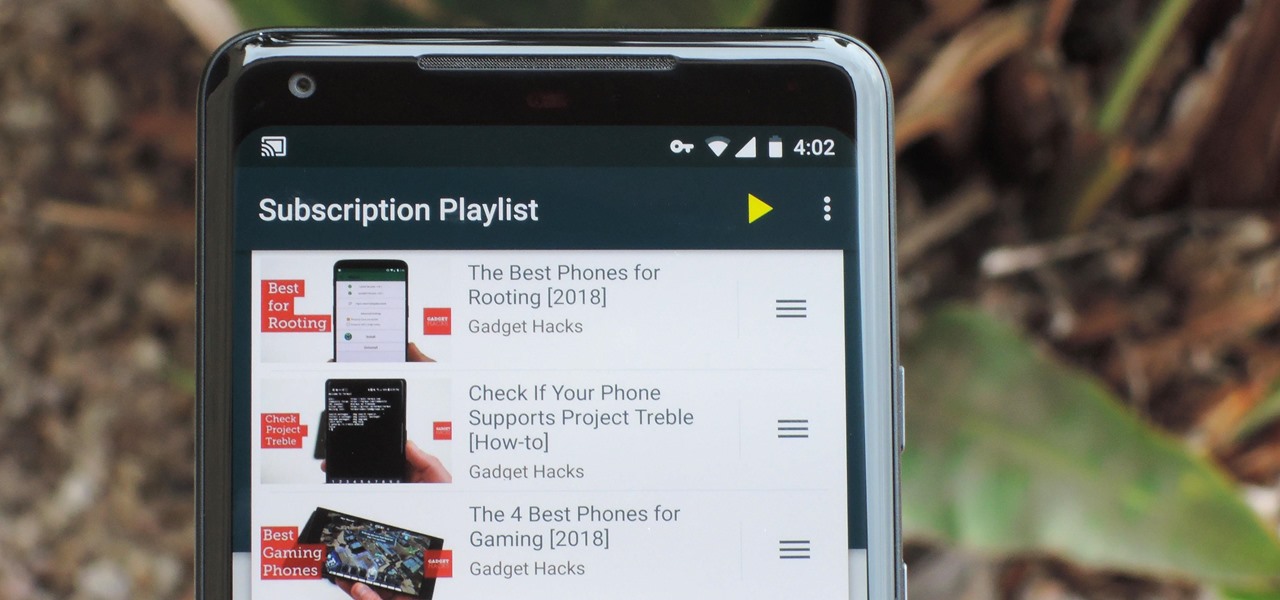
Sometimes I'm convinced Google has ADHD. They'll create a great product, then get distracted by the next moonshot and never put the finishing touches on their last project. Case in point, you can't just cast a playlist of your subscriptions from YouTube to Chromecast, even though that's how many people prefer to use YouTube.

WhatsApp is a great app to keep in touch with friends and family across phone brands and countries, but sharing a post on Instagram hasn't always been as easy as it should have been considering Facebook owns both companies. Now, whether you have Android or iOS, all it takes is a few taps.

It appears that the new AR app from LEGO is inching closer to release.

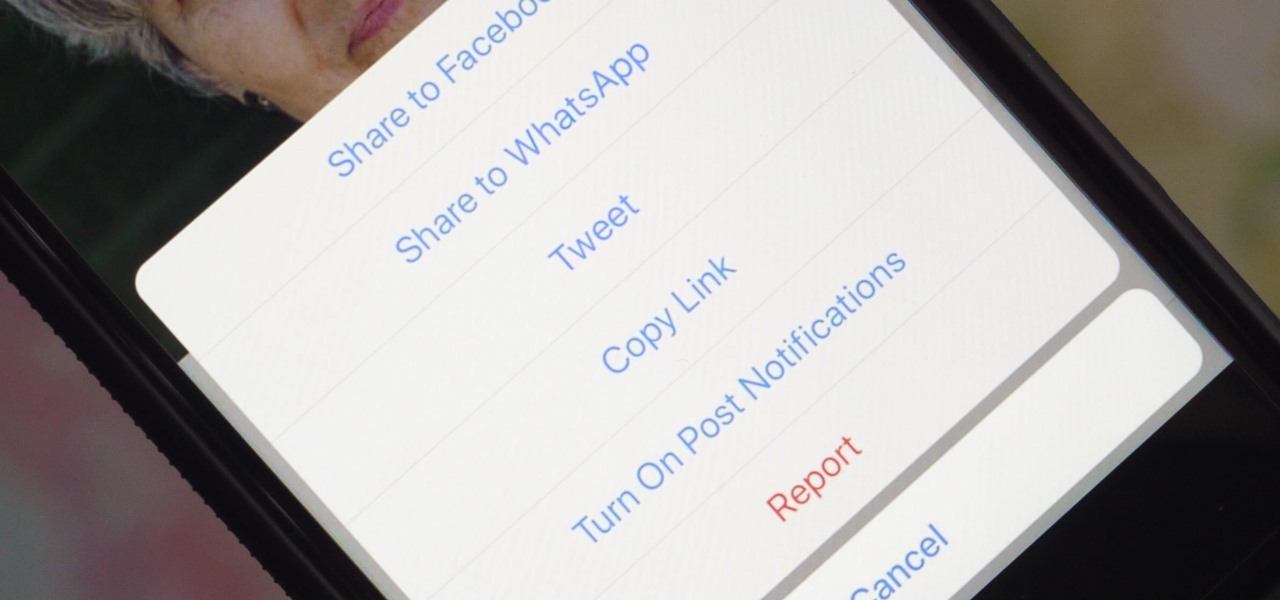
You can retweet on Twitter, and you can reblog on Tumblr, but you cannot regram on Instagram. Until now, that is. For years, third-party apps have made it their business to help Instagram users share content from other users. With some new developments, Instagram looks to render those apps obsolete by adding a native regram button to the official Instagram application.

Rabbit ears and dog noses are fun and all, but Kay Jewelers is here to class up Snapchat.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

With a pair of new APIs and low-latency media servers, Twilio's Programmable Video platform could soon help ARKit and ARCore app developers build shared AR experiences between multiple users.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

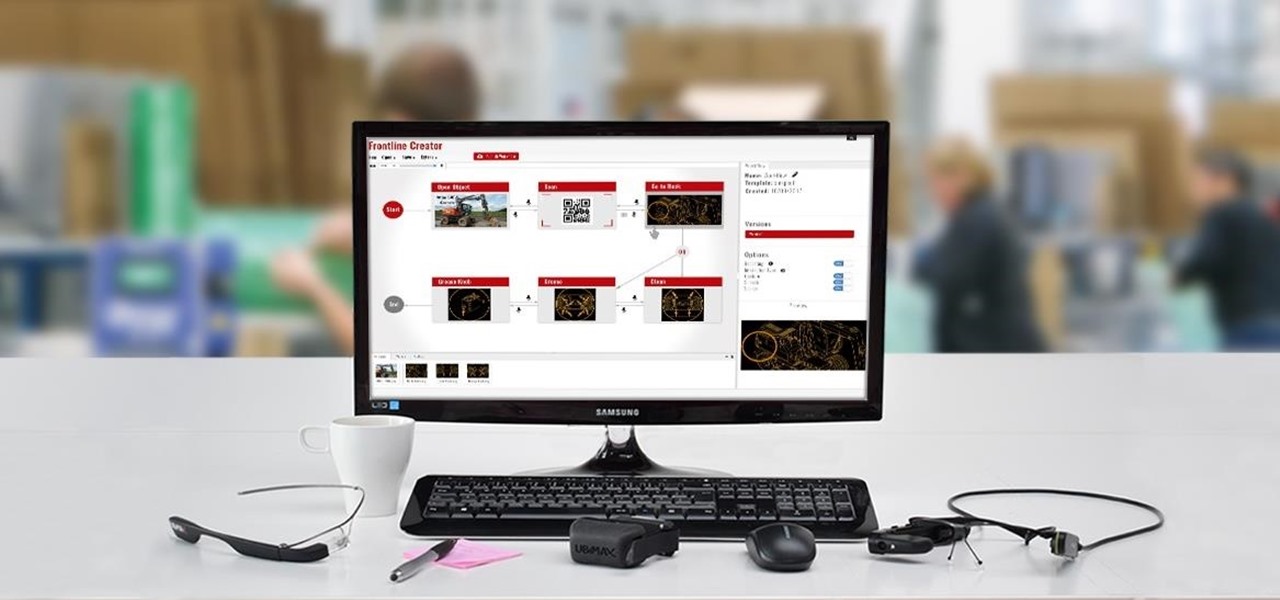
Augmented reality software provider Ubimax unveiled their graphical authoring and publishing tool for their Frontline enterprise platform to attendees at Augmented World Expo Europe today.

Google announced a partnership with Movies Anywhere that allows you to connect your iTunes, Amazon, and Vudu movie library with Google Play Movies. In other words, movies you purchase from any of these online retailers will be available for playback in the Google Play Movies app after a little setup.

Augmented reality software maker Upskill has released the latest version of their Skylight platform, adding a number of new tools to ease implementation and improve functionality for enterprises, including a new application builder.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

The release of iOS 11 and ARKit is probably the biggest event for mobile developers since the advent of the App Store.

During Google Developer Days, taking place now at the ICE Congress Center in Krakow, Poland, an introductory session on ARCore provides some insights on how the platform operates.

A Jedi does not seek adventure or excitement, but Star Wars fans can seek Jedi with the Find the Force augmented reality scavenger hunt promoting the launch of merchandise for Star Wars: The Last Jedi.

The world is a massive place, especially when you consider the field of view of your smartglasses or mobile device. To fulfill the potential promise of augmented reality, we must find a way to fill that view with useful and contextual information. Of course, the job of creating contextual, valuable information, to fill the massive space that is the planet earth, is a daunting task to take on. Machine learning seems to be one solution many are moving toward.

Advertisers must love when their commercials go viral. Take for instance the Esurance commercial where an elderly woman completely misunderstands Facebook jargon.

After laying off 40% of its staff this month to cut costs, SoundCloud appears to be struggling to stay afloat. While blog posts from the company have assured fans that the music platform is not in danger of shutting down, some people aren't so sure this is the truth. Internet Archive — a non-profit dedicated to preserving websites and services — announced today that they will be conducting a partial backup of SoundCloud to safeguard the site's content in case of closure.

With augmented reality making its way into the mainstream, consumers have been expecting a company bloodbath for a while now, one that will have a ton of casualties. Blippar has been expected to be one of those casualties due to the reported loss of millions of dollars earlier this year. Now, their situation might be made worse as the creators of the Layar app, Raimo van der Klein and Martin Lens-Fitzgerald, are rumored to be asking for their company back.

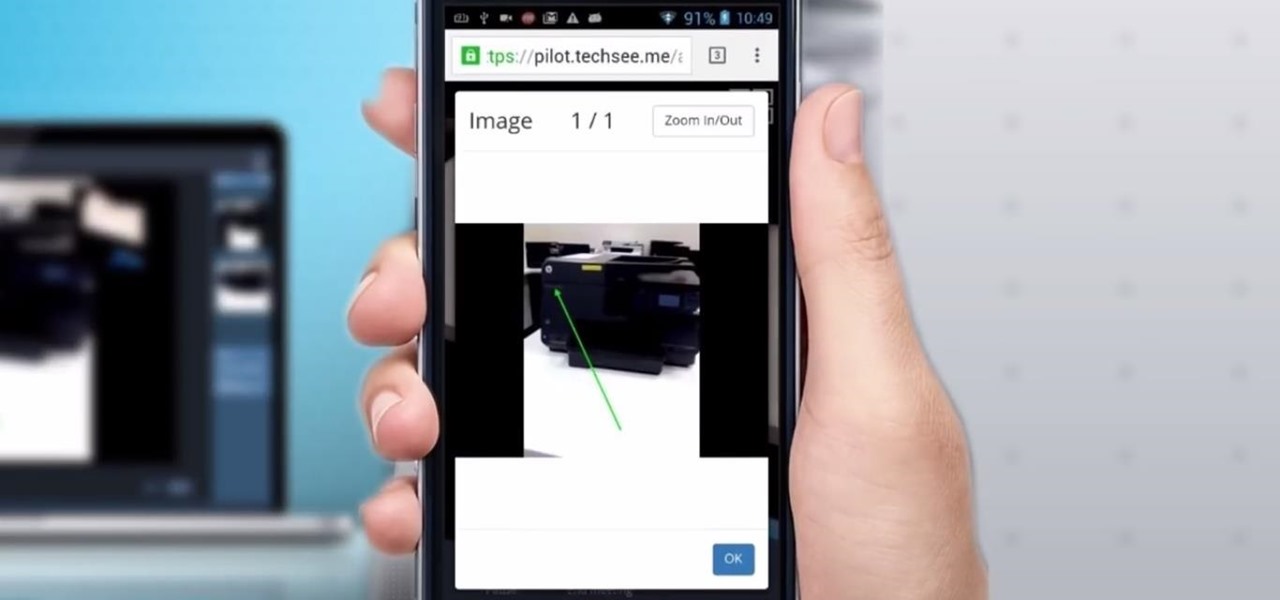
Four augmented reality companies made deals this week to grow their businesses. Two companies, TechSee and Car360, completed funding rounds, while DAQRI signed with a production partner and Decalomania landed a prime spot with a top retailer.

The company that brought us a BB-8 droid controlled with the Force — okay, just a high-tech wristband — is releasing its take on Spider-Man. Toymaker Sphero collaborated with Marvel to release an app-enabled Spider-Man toy equipped with numerous features, as well as games for your smartphone.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.