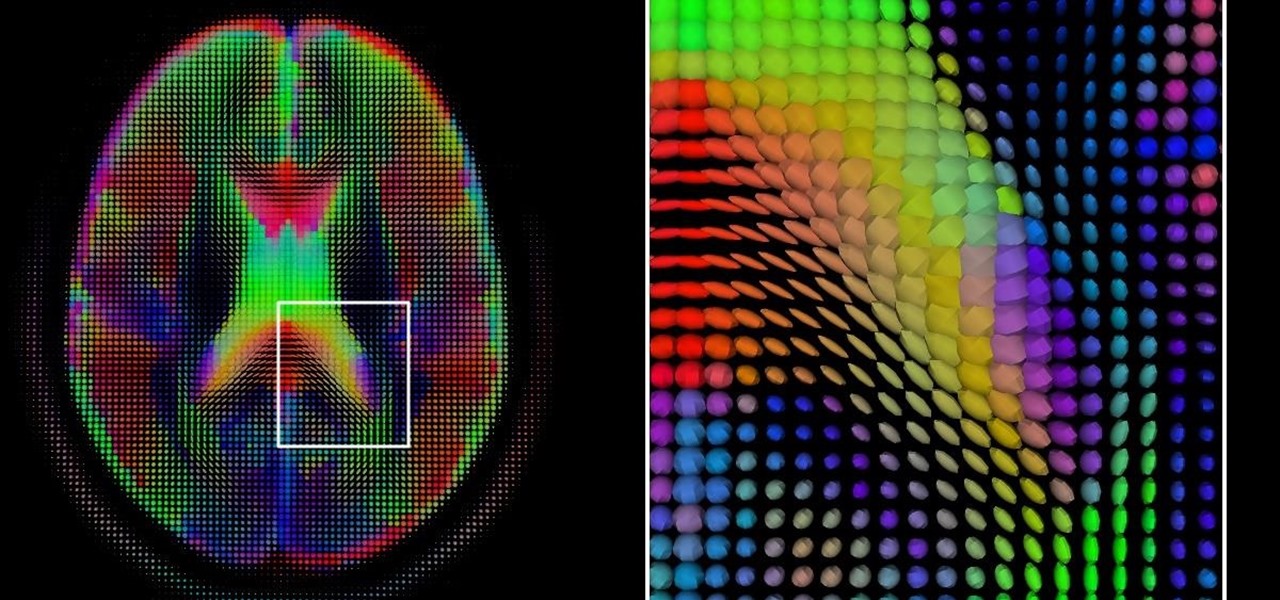
Whether your palate runs to domestic or imported, a piece of cheese can be a real treat for the senses. Its smell, taste, and texture are all parts of its appeal. A big part of what makes that savory wonderfulness comes from the microbes in and on the cheese. Thanks to a team of researchers dedicated to studying those microbes, we have a better understanding of their importance to cheese and us.

Windborne microbes shifting in the snows of the great ice sheet of Greenland may be able to neutralize some of the industrial contaminants oozing out of the melting ice.

Food is both a necessity and a joy. Many people enjoy exploring, cooking, eating, and learning about foods from around the world. But the picture isn't always rosy. A new report from the Centers for Disease Control and Prevention (CDC), highlights the ways and whereabouts of food that make us sick.
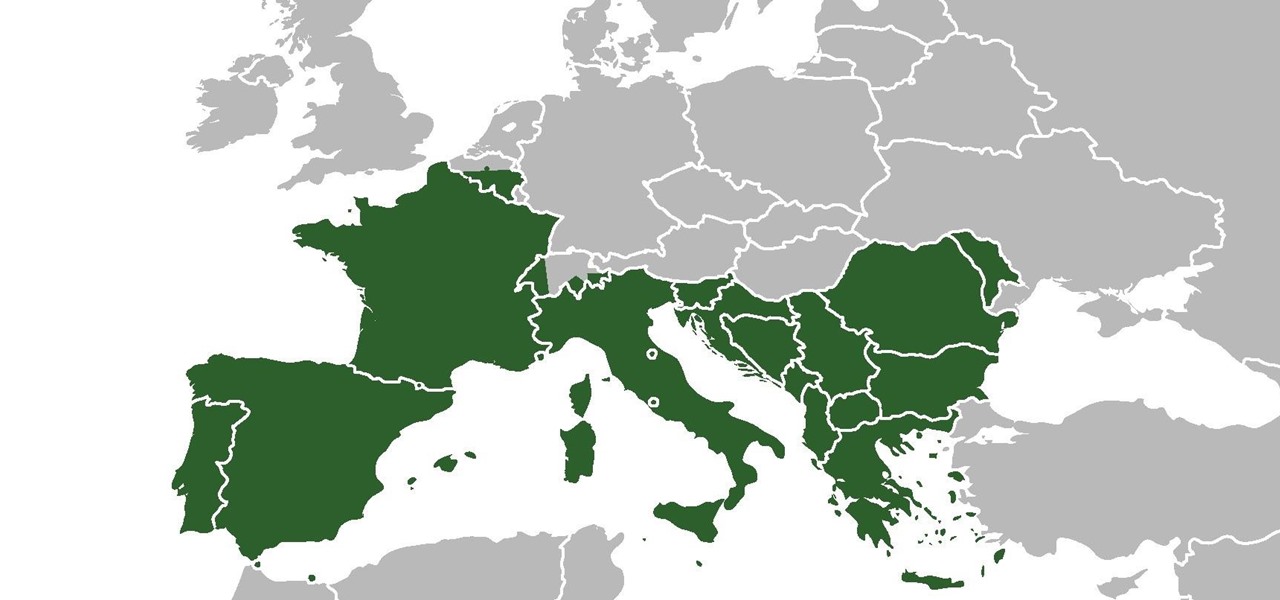
The beauty of southern Europe won't protect it from invasions of disease-carrying ticks and mosquitoes—in fact, the Mediterranean climate and landscape may be part of the reason the bloodsuckers are expanding there, bringing unique and terrifying diseases in their wake.

You can get eggs and high-quality compost from backyard chickens—but you can also get Salmonella.

You just sat down, coffee in hand, and the day is ready to start. Now that you have taken a few sips, let me pose a question: What is living in that coffeemaker of yours? The answer might make you dump that coffee down the drain pronto.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

After jumping to the head of the class of augmented reality journalism in 2019, USA Today is continuing to push the medium forward in 2020.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Although more and more smartphones are introducing portrait modes with their cameras, there are still plenty of devices out there — especially devices older than one or two years — that do not. While your particular smartphone might not offer you that bokeh effect, Instagram can, as it gives all smartphones software-based portrait modes.

While Snap's third quarter financial reports disappointed Wall Street, China's Tencent took the opportunity to expand its investment in the social media company.

For Apple Pay users, the iPhone X, XS, XS Max, or XR will be an adjustment. Gone are the days where you could rest your finger on the Home button and hold your device within range of a contactless reader. Without Touch ID on the iPhone X, this isn't possible. But have no fear, Face ID is here.

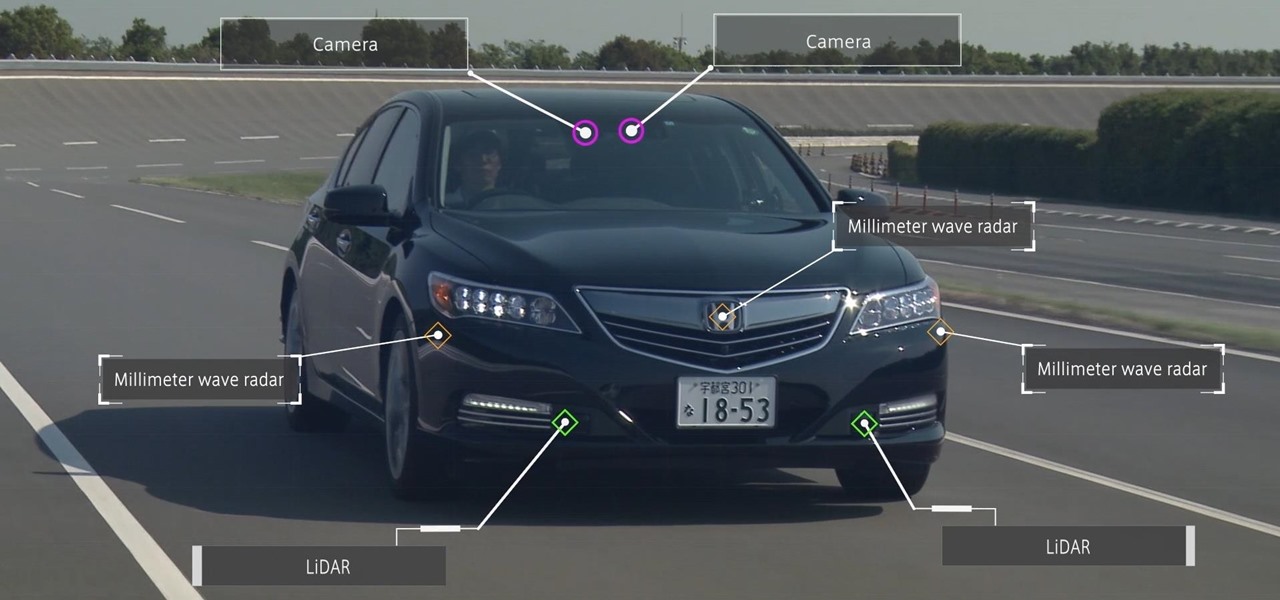
Honda president Takahiro Hachigo has just announced that Honda will complete development of fully self-driving cars by 2025. While the company aims to have level 3 — or conditionally autonomous cars requiring human intervention only in emergencies — on the road in time for the 2020 Tokyo Olympics, these level 4 cars would require no intervention in most environments and thus bring Honda one step closer to producing fully driverless cars.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

After talking up the Magicverse for the past year and adding new capabilities to Lumin OS to accommodate it, Magic Leap appears to be inching ever closer to actually launching its cross-platform flavor of the AR cloud while introducing a new tool for its development community.

"Why do I keep getting popups on my phone when I'm not even doing anything?" I see this question asked all the time. The answer? You have a shady app on your phone and it started showing full screen ads. But people either don't know this (so they don't know they just need to find and uninstall the problematic app), or if they do know it's a bad app, they don't know which app is causing it.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

As the tech world patiently waits for the advent of mainstream consumer smartglasses, Google is content to stick to the business world (for now).

Fresh off of shipping version 2019.1 in April, Unity has already dropped the beta of 2019.2, and it has a bunch of new AR Foundation toys to test.

Alongside its official unveiling of the lower-cost Pixel 3a smartphone at Google I/O, Google took the opportunity to extend its early preview of AR walking navigation in Google Maps to all Pixel devices.

New documents reveal that electric car company Tesla has filed a surprising new patent that has nothing to do with batteries or autonomous driving and everything to do with augmented reality.

The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

Mobile augmented reality developer Blippar's mission is to construct a computer vision map the world, with visual recognition of thousands of notable buildings, bridges, castles, holy places. A major step toward that goal has been taken by the company this month with the announcement of its landmark recognition API.

The advent of ARKit and ARCore has strengthened the demand for development tools to build augmented reality experiences for compatible iPhones, iPads, and Android devices.

The world is a massive place, especially when you consider the field of view of your smartglasses or mobile device. To fulfill the potential promise of augmented reality, we must find a way to fill that view with useful and contextual information. Of course, the job of creating contextual, valuable information, to fill the massive space that is the planet earth, is a daunting task to take on. Machine learning seems to be one solution many are moving toward.

Instagram can be pretty exact when it comes to where you are located. That's why, sometimes, it's best never to geotag your precise location, but a broader area where you are less likely to get, well, um ... stalked?

If you're a tech enthusiast, there's no way you're not watching HBO's Silicon Valley. So you surely know the Pied Piper crew's latest shenanigans involve an app that uses a phone's camera to find facts about food items — a sort of Shazaam for food, if you may.

Google's Allo is still a work in progress, but the innovations to the chat and messaging app just keep on coming. The latest update rolling out now includes chat backups and a group incognito feature that we're very excited about.

There's nothing worse than driving up to your destination only to discover that there isn't a parking spot in sight — but thankfully, Google Maps will soon have you covered.

A baby with severe Zika-related birth defects was born in San Diego County this week, prompting officials to urge pregnant women to avoid disease hotspots.

Researchers have been studying the blood meals of flies to understand the flow of infectious pathogens in wild animals.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

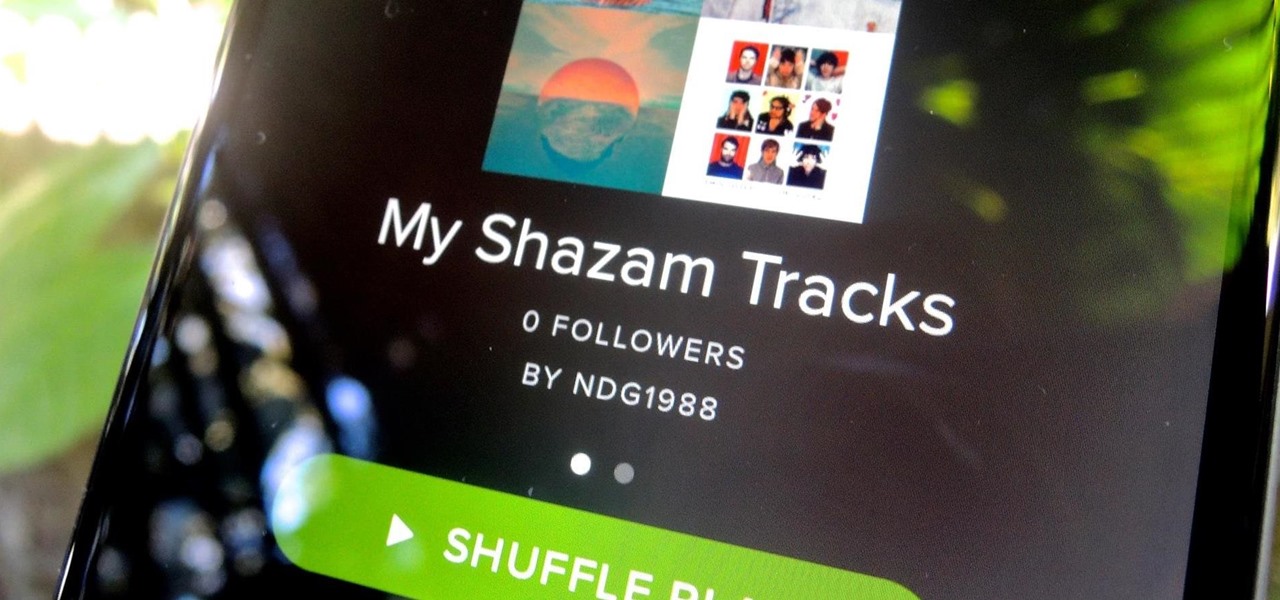
We recently showed you how to recover your Shazam history from Siri, which is a lot less intuitive than finding the songs you've tagged directly in the Shazam app. But with a subscription to Rdio or Spotify, there's no need to even locate your history. You can Shazam songs and have them automatically added to a newly created playlist titled "My Shazam Tracks."

We've previously shown you an app called Floating Lyrics which displayed song lyrics in a, you guessed it, floating window. And while that app was great for any minimalist, it was pretty bare bones overall.

Update January 27, 2014: Samsung has released a statement to address the flip cover issue, claiming it as a bug with a "fix" coming soon: