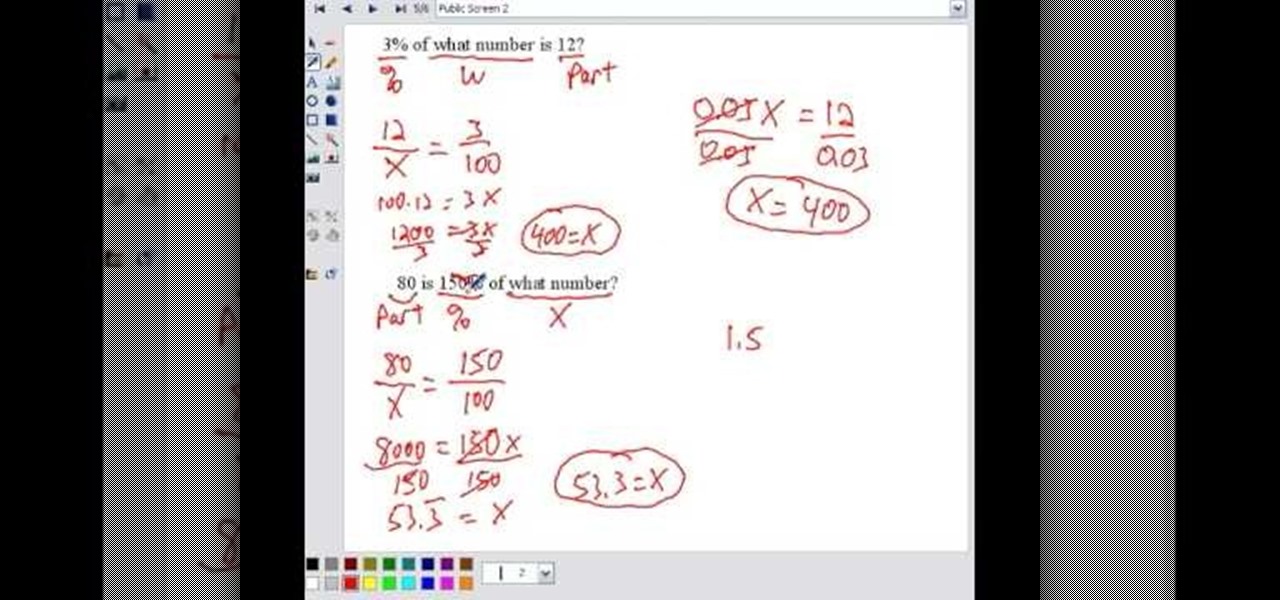There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, but the most visible fungi are mushrooms. Some fungi are delicious, but others can cause disease or, and still others, like Penicillium, can cure it.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

This how to video is very basic introduction to the violin. YOu can learn how to identify the violin and its parts, as well as a little bit of how it works. You will also learn how to count a rhythm. With the tips from this how to video you can start learning the violin.

Whenever I have a new student in the shop, I try to convey what if feels like when something is going wrong on the tablesaw. This may seem like an abstract idea, but knowing how to identify a problem before it goes too far could give you that extra second or two you need to prevent disaster. This woodworking video tutorial reviews common safety items for a table saw and how to use a tablesaw properly.

BPS golf instructor Steve Bishop discusses how to reduce tension in your golf swing and helps you identify where you might be tensing up in your own swing.

In this video golf lesson golf instructor Steve Bishop discusses some key ideas and tips about the finish. This will help you identify some of the errors you may have made during your golf swing.

Learn from Green Deane how to identify and prepare thistles, which are spring time greens from around the world.

Learn from Green Deane how to identify and prepare Rumex (Sorrel) a spring time green around the world.

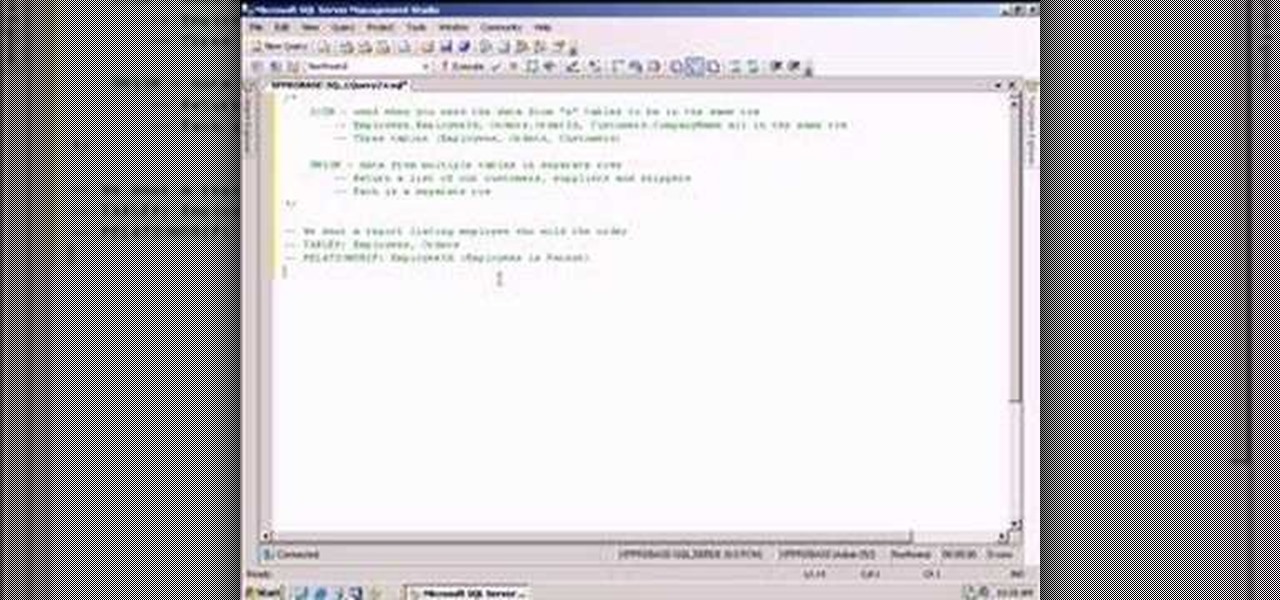
So many newbies to Transact-SQL have difficulties determing when to use a UNION or a JOIN to satisy their query. This video teaches you some guidelines to help you quickly and easily identify whether your query will likely need to become a JOIN or UNION. Disclaimer: these are just guidelines and they will not work in every situation but they are applicable for most SQL developers most of the time.

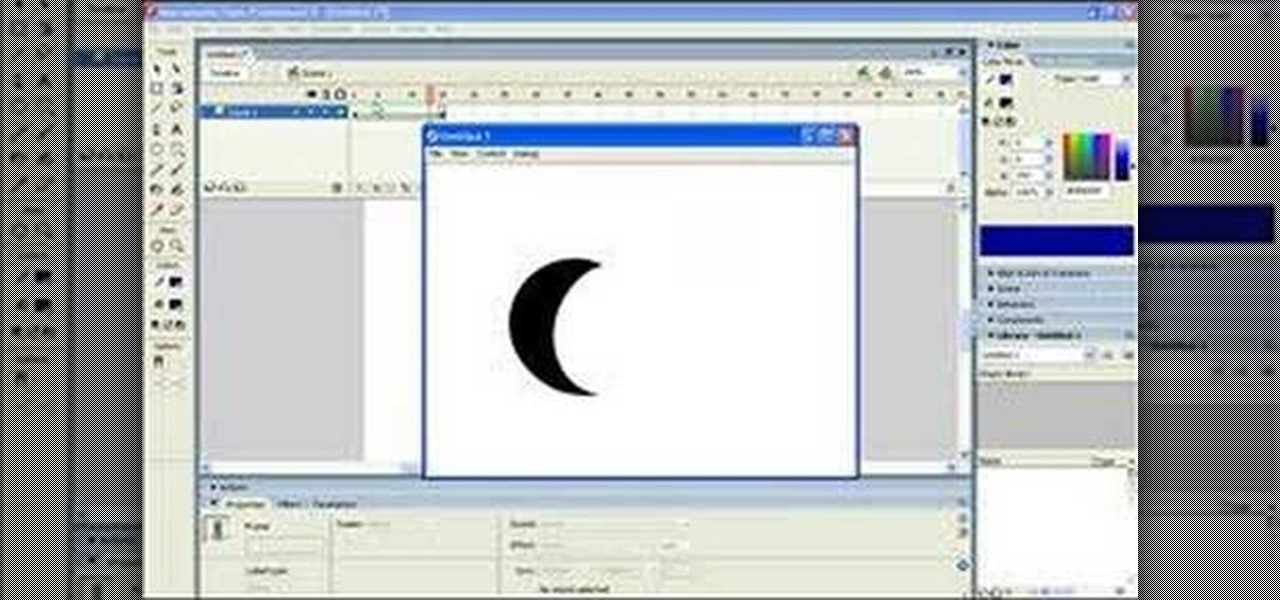
To control more complex or improbable shape changes in Macromedia Flash, you can use shape hints. Shape hints identify points that should correspond in starting and ending shapes. This video tutorial teaches you how to use shape hints to make a cool 3D effect.

Ursa Major is called the Big Dipper in North America. The seven main stars are easy to identify. The big dipper changes positions throughout the night and throughout the year. The change in position is due to the earth's motion rotating the sun.

Hello there, people. Today, I am going to show you how to extract the essence from a useful plant, using either alcohol or olive oil. This is how you take a plant and turn it into a useful (and preservable) medicine. For those of you who know nothing about herbal medicine, let me explain it for you in a nutshell...

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

A peek inside the code of the Snapchat app has revealed that the company is expanding the search capabilities of its augmented reality camera to include visual search that may link to items within Amazon's massive online store.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Augmented reality might not be able to cure cancer (yet), but when combined with a machine learning algorithm, it can help doctors diagnose the disease.

Researchers have developed a new method that harnesses the power of augmented reality to detect a patient's heart rate using a Microsoft HoloLens and computer vision.

At the risk of breaking a few rules, we're going to talk about Fight Club. More specifically, digital artist Mateusz "Marpi" Marcinowski has mimicked a scene from the movie using Apple's ARKit.

Microsoft recently released "Seeing AI," an app aimed to help the blind understand their surroundings. As Microsoft puts it, "the app narrates the world around you by turning the visual world into an audible experience."

While it remains unknown how exactly augmented reality will make its way into the mainstream (the Microsoft HoloLens sitting at $3,000 isn't exactly accessible), many brands have been trying to integrate the tech into their mobile apps, mimicking the success of Snapchat and its popular AR filters. One of those brands going all in on augmented reality is Shazam.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Anyone remember Google Goggles? Well, it's back with a new name: Google Lens. But this time, there's more machine learning and it's integrated into many different Google apps and services. The latest is the Google app for iPhones.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

A recent initiative by the Cherokee Nation American Indian Tribe delivers a success story for knocking out a silent killer — Hepatitis C.

With a death rate of one in five, sepsis is a fast-moving medical nightmare. New testing methods might improve your odds of survival if this infection ever hits you.

The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a compromised immune system.

This is a Q&A video with the question asking if glaze putty can be applied over primer or not. In this short Q&A video I am going to answer this question.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

There's an iOS feature that benefits many users, but it's absolutely vital if you wear AirPods or other headphones models connected to your iPhone. A large number of iPhone users don't even know about it, especially since it's disabled by default and hidden deep in the system settings.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

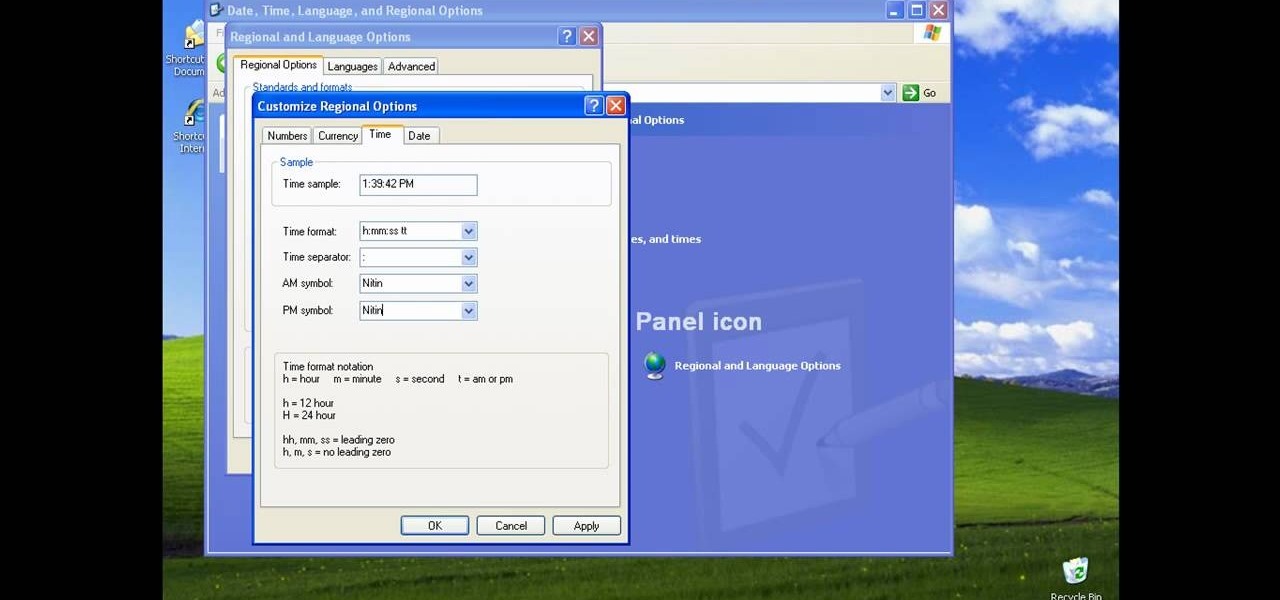
There could be multiple reasons why you would want to input a name in the Windows taskbar on your PC, like when dealing with a network of computers, to help identify workstations, or simply for a customized personal feel. With this tutorial, you'll see how easy it is to put your user name or computer name (or any other name) down in the taskbar, right besides the time in the bottom right.

Percent problems, also called as proportion problems, are simple problems where you deal with percentages. Given a percentage problem you may need to identify the percentage, the part or whole quantity from it. You can use the proportion or percent equation to do this. Proportion equations says that the ratio of part to the whole is equal to the ratio of percentage to one hundred. Percent equation says that the product of the percentage in the decimal form and the whole gives you the quantity...

hcoleman teaches you how to answer interview questions using strategy. When the interviewer asks you to talk about yourself, you should talk about your strengths, abilities, and things that motivate you; things that demotivate you are also important. Your last job question should focus on achievements, leadership, and team skills. Use examples regarding your qualifications. The five years question is about honesty. You should talk about the company you want to work for in 5 years. Identify yo...

d-CON is here to help identify and remedy rodent problems in your dining room. Watch this video tutorial on how to use d-CON Quick Kill Glue Traps to kill mice in the dining room. Signs of a mouse in the dining room include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.