d-CON is here to help identify and remedy rodent problems in your bedroom. Watch this video tutorial on how to use d-CON Ultra Set Traps to kill mice in the bedroom. Signs of a mouse in the bedroom include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your home. Watch this video tutorial on how to use d-CON Ready Mixed Baitbits to kill mice in the home. Signs of a mouse in the home include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your bathroom. Watch this video tutorial on how to use d-CON Bait Wedges to kill mice in the bathroom. Signs of a mouse in the bathroom include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your living room. Watch this video tutorial on how to use d-CON No View No Touch Traps to kill mice in the living room. Signs of a mouse in the living room include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your kitchen. Watch this video tutorial on how to use d-CON Bait Paste Pouches to kill mice in the kitchen. Signs of a mouse in the kitchen include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.
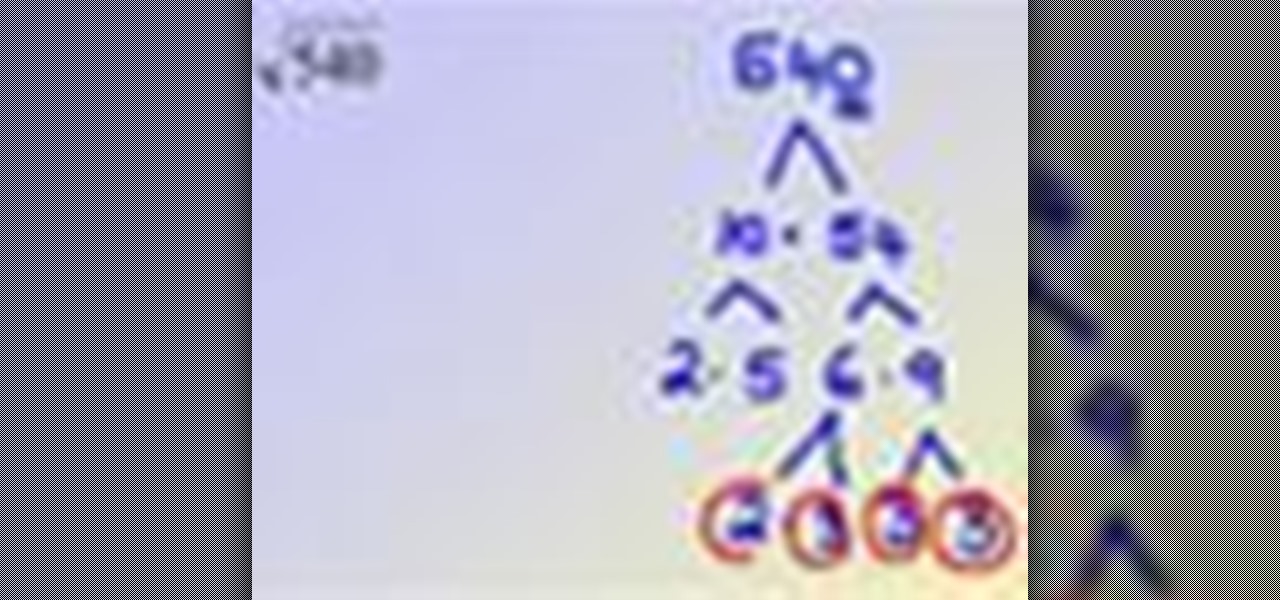
Watch the following video to understand the steps necessary when simplifying square roots. To simplify expressions with radicals, follow these simple steps:

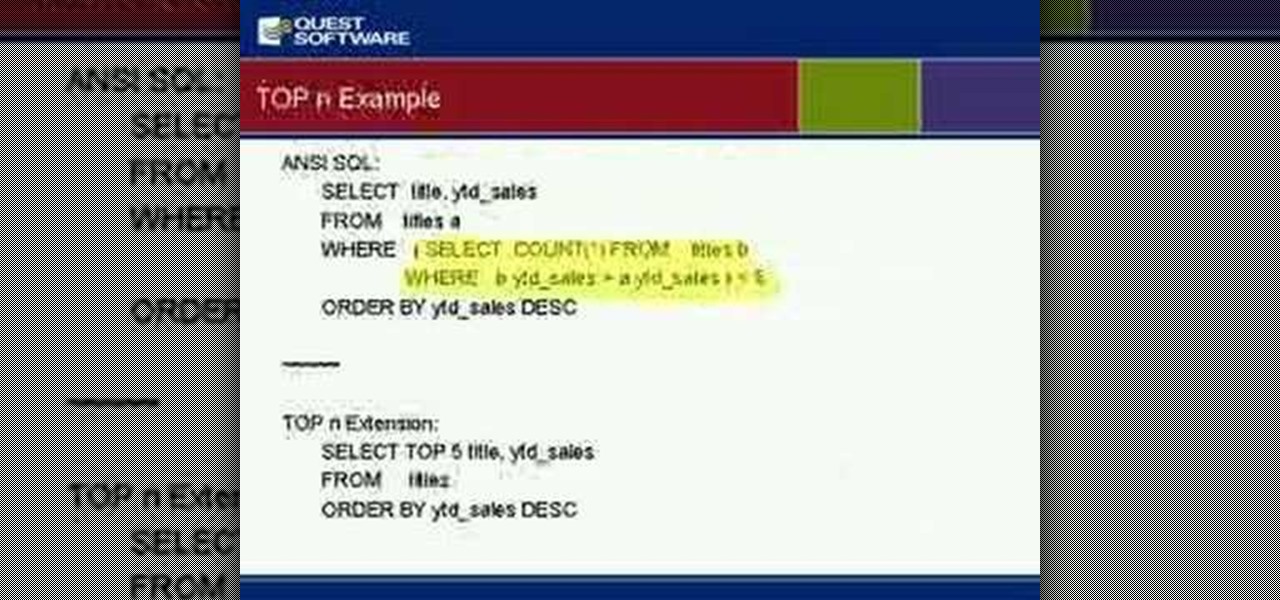
Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

I've covered augmented reality apps for about three years now and the most useful mobile app I've encountered over that time is Google Lens.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

All phones (yes, iPhones too) slow down over time. As your device gets bogged down by various apps and you begin to run out of storage, it's just an inevitability. That doesn't make it any less frustrating ... I mean, is there anything more annoying than a slow phone? My answer: No. Of course not. It's the single most annoying thing ever.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

If you're a tech enthusiast, there's no way you're not watching HBO's Silicon Valley. So you surely know the Pied Piper crew's latest shenanigans involve an app that uses a phone's camera to find facts about food items — a sort of Shazaam for food, if you may.

A sometimes serious disease spread by fleas is making inroads in Texas, quietly doubling case numbers since 2008, and beginning to encroach on larger metropolitan areas.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Revised Version, Gallery pictures of the Ambassabank have been removed since XCL 2.0 has been released.

Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify.

Step 1: Identify an Old Sweater and Get Your Supplies Get an old sweater that you hardly wear or hit up the thrift shop. YOu will also need:

Your Pixel's Now Playing song discovery tool received a few updates in Android 12, and the feature is finally comparable to other music recognition services.

Have you ever had a great meal at your local restaurant and wondered how to make it yourself? Or perhaps you've found yourself stumped at what to make for dinner based on the random provisions in your kitchen? Now, you can discover solutions to these food-based problems via Snapchat's computer vision wizardry.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

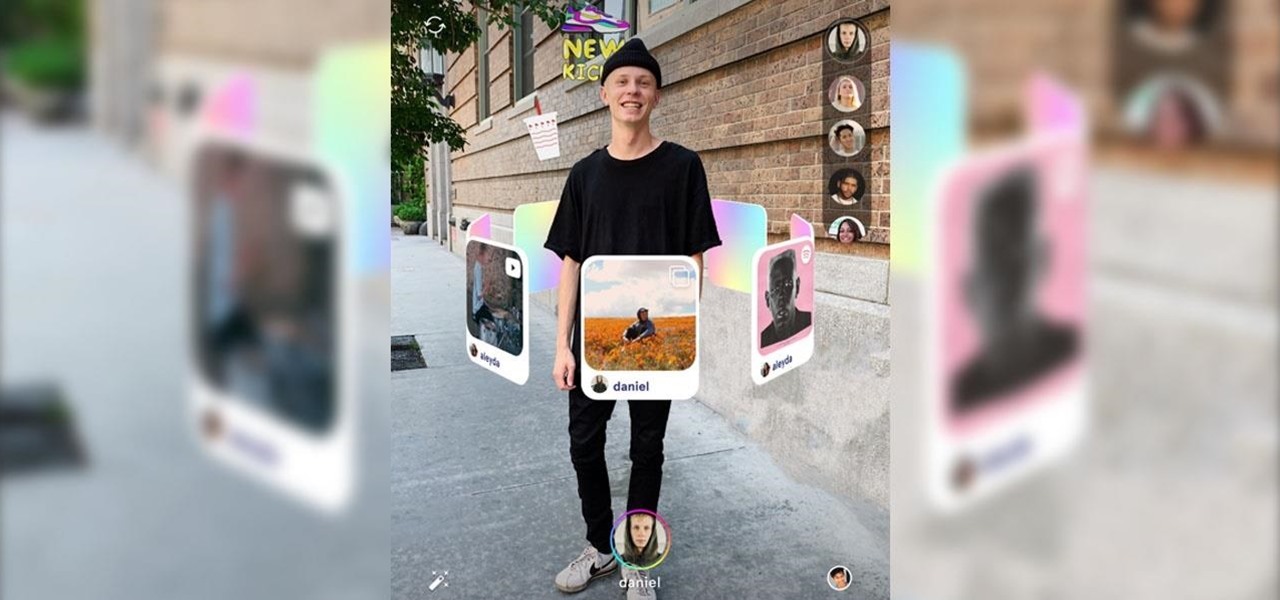
In a world full of augmented reality camera effects apps, one app is going in a more social direction.

With the imminent arrival of the HoloLens 2 expected any day now, Microsoft is preparing new users to take advantage of its software from day one.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

Ben & Jerry's addicts rejoice: Microsoft just won a patent for AR glasses that could help to combat overeating. Physical restraint is still needed to keep me away from that ice-creamy goodness, but a little virtual voice saying 'DON'T DO IT' could definitely help when the cravings come.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.

The rate of preterm birth has been increasing in the United States for unknown reasons, causing increased health risks for infants born too soon. But researchers may have found a signal that could help doctors plan ahead for, or even prevent, early birth with a simple swab of the vagina and cervix during pregnancy.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

I grew up eating Korean, Japanese, and Chinese food, but it wasn't until college that I experienced Thai and Vietnamese cooking. Once I started, I couldn't get enough of these cuisines. The dishes had an incredible richness and savor that I couldn't identify, but whatever it was, it made me want to keep eating.