Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

The Pixel 2 debuted a really cool feature that identifies any songs playing nearby and automatically displays the track's name on your lock screen. It's honestly one of the most inventive smartphone features we've seen in a while, especially considering how Google did it — but strangely, it's not enabled by default.

As a part of the already crowded field of diseases transmitted by ticks, you may not know the disease babesiosis, a dangerous infection caused by a parasite that infiltrates blood cells.

Bed bugs are brown and creepy. Could you spot one in your hotel room? A new study reveals most people are freaked out by bed bugs, but only about 35% could identify one.

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

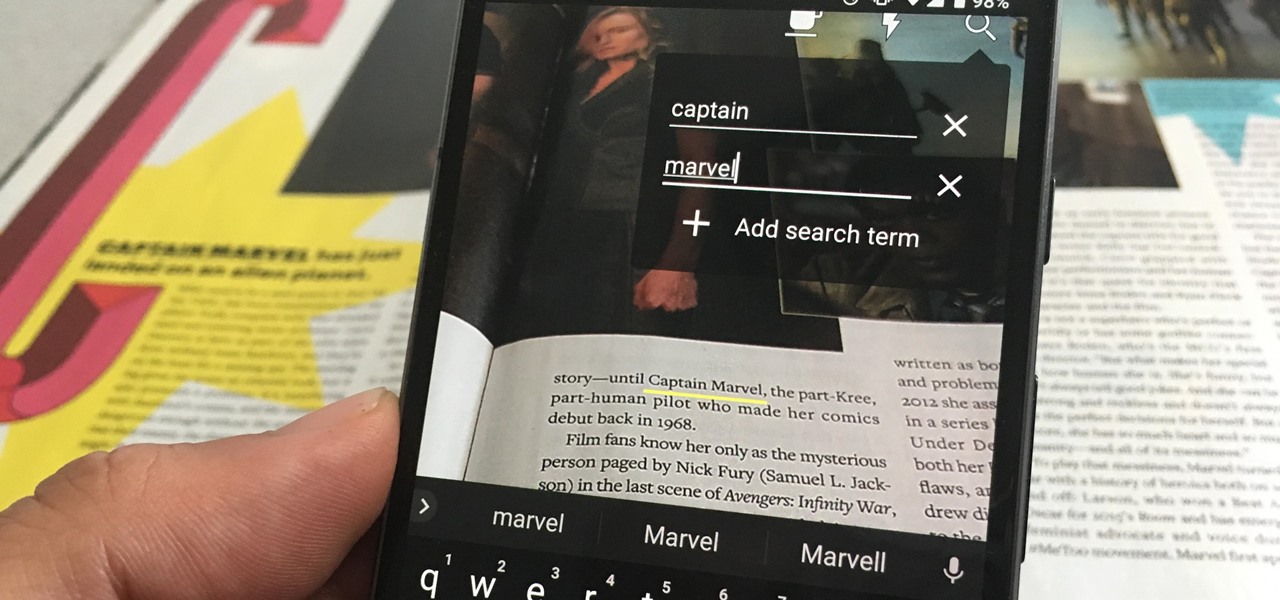
Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

There are a lot of manipulative people out there, but you don't have to let all of them push you around. It's time for the tables to turn.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Songs new and old are given a fresh purpose through the TikTok meme machine, but it can be tricky to figure out where a track originally comes from. Sure, you can tap the name of the song to see the source on TikTok, but if it were a snippet uploaded by someone other than the track's creator, the song title likely wouldn't be listed. Luckily, there is an easy way to figure it out.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

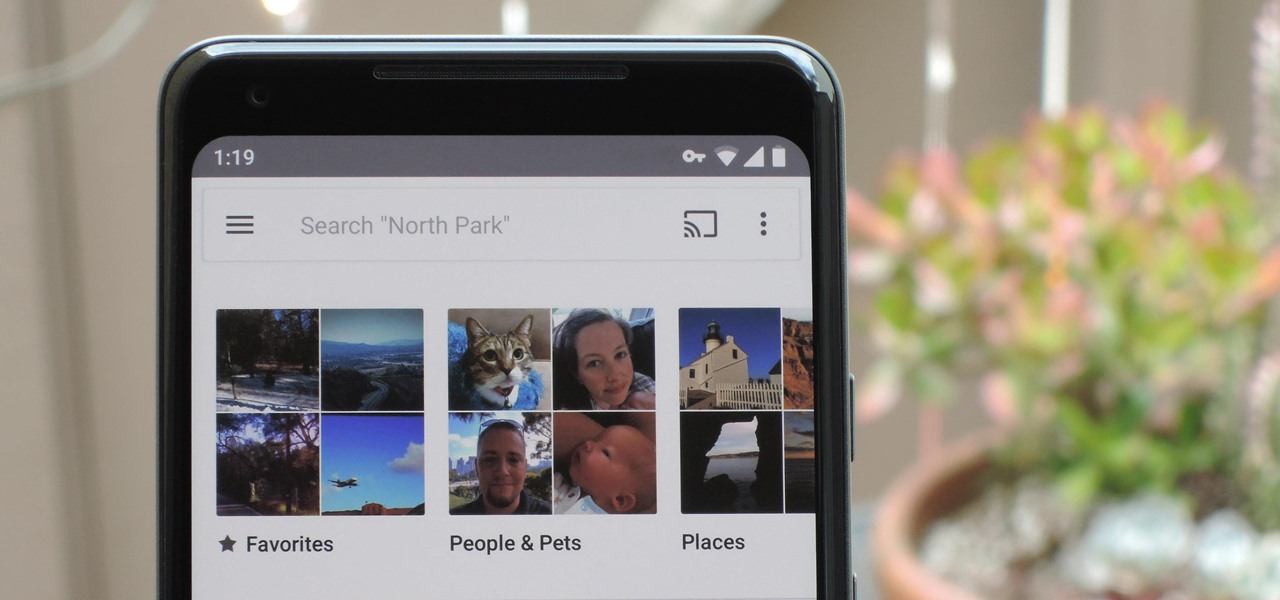
Google Photos is a fantastic service, giving you unlimited storage on either your Android or iPhone. With all this free space, some pictures can get lost in the shuffle. Fortunately, Google will now let users "Favorite" pictures — whereupon they're automatically put in their own standalone album.

Following in the augmented reality footsteps of Pokémon GO, Universal Studios has decided to give us an AR version of Jurassic World.

Facebook may have shamelessly copied Snapchat and its camera effects for faces (as well as its World Lenses), but it might beat its social media competitor to virtual body augmentation.

The same approach to augmented reality that some companies use to improve workforce productivity could also make it easier for car owners to operate and maintain their vehicles.

Do you know when you're going to die? Your iPhone or iPad does. That's the premise behind Death Mask, an experimental app developed by Or Fleisher and Anastasis Germanidis.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

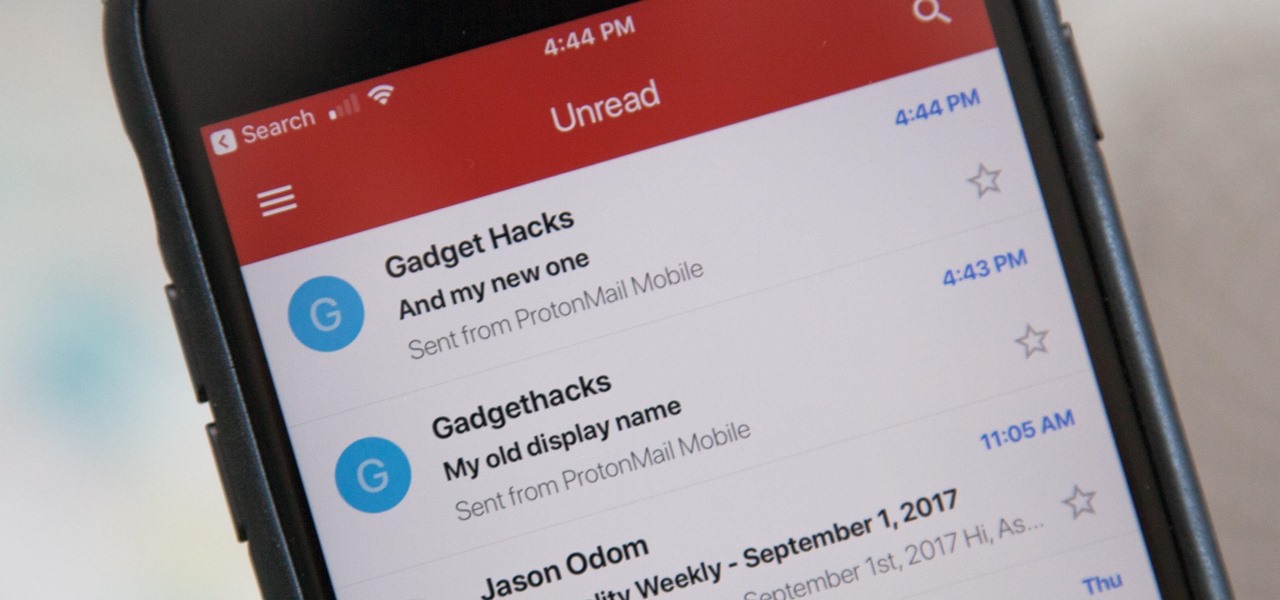
Your display name in ProtonMail is what email recipients will see when they first receive your message in ProtonMail, Gmail, or another email provider. You can choose this name when you first set up your ProtonMail account, but it can also be set up after the fact if you skipped that step.

Android Oreo may not be the flashiest release, but it's got tons of under-the-hood changes. We recently discovered documentation in the AOSP source code that outlines one of these understated features, which has been dubbed "Rescue Party."

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

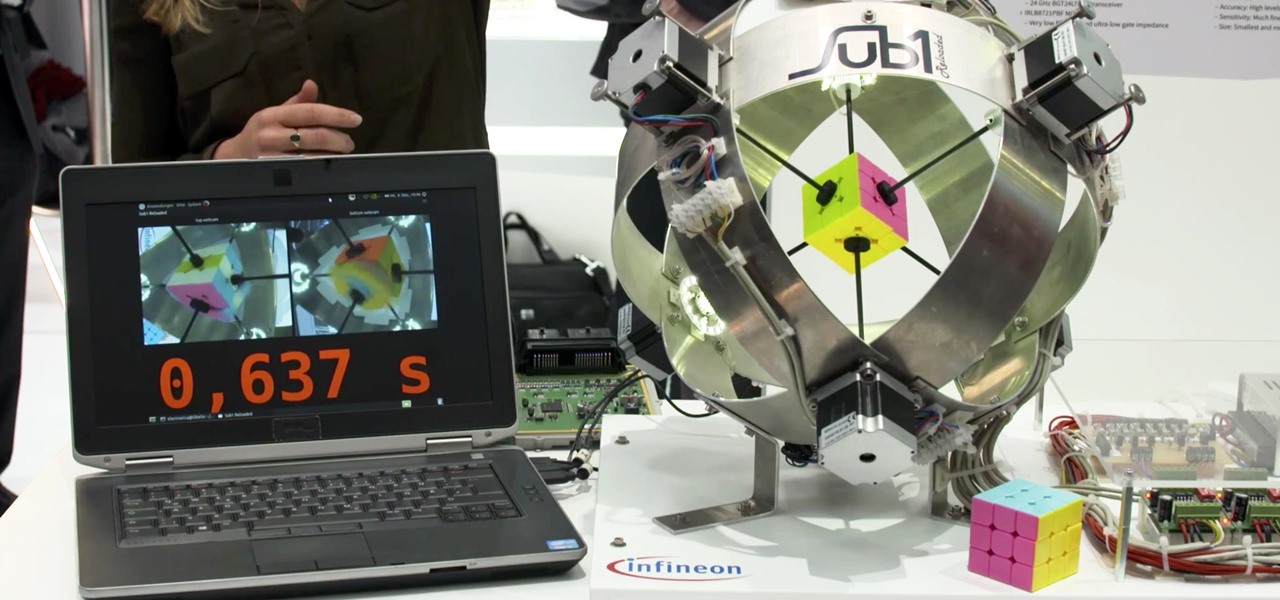
In December of last year, Australian Feliks Zemdegs broke the human world record for solving a Rubik's Cube with a time of 4.737 seconds. Well, this robot did it way, way faster by solving one in under 1 second. Don't tell me a robot takeover isn't real possibility.

If you've been to the doctor enough, you know that the medical staff can make a variety of mistakes from time to time. They're human and that's normal, but errors in the medical field can often have significant negative impacts. At Boston's 2016 HoloHacks event, a team of developers created HoloHealth to mitigate human error in common healthcare tasks.

The headsets of tomorrow offer some amazing possibilities in both gaming and work, but what we've seen so far only begins to scratch the surface. The US Navy saw the potential to use augmented reality in a helmet to provide divers with an incredible amount of information we have so far only seen in Hollywood movies.