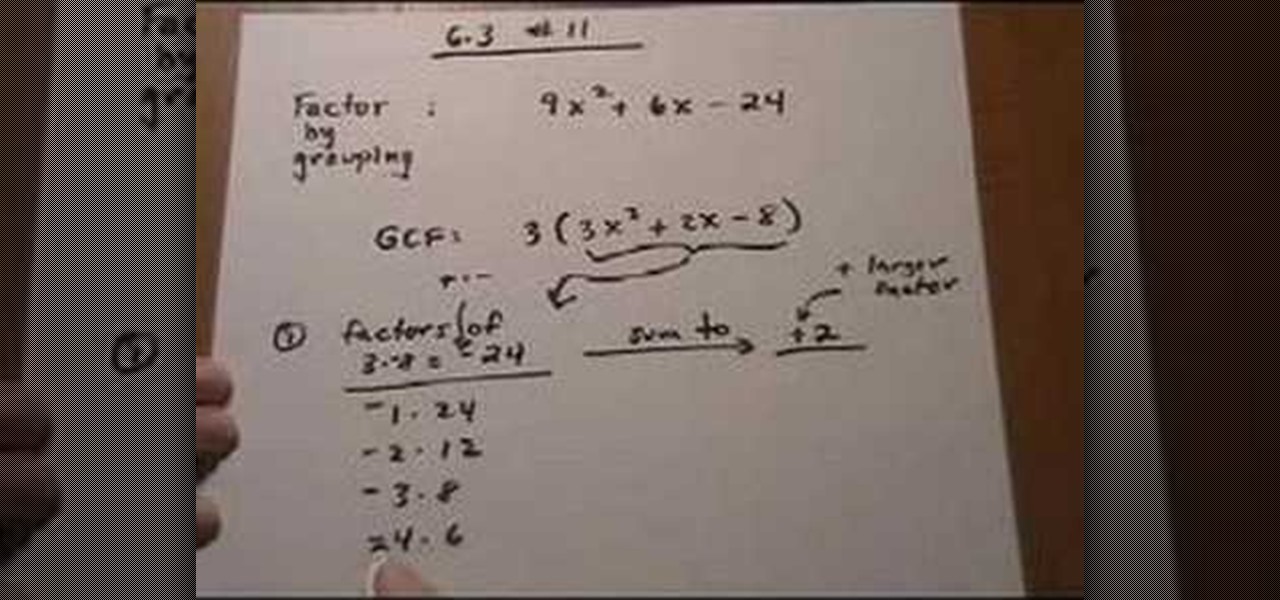A self-contained breathing apparatus allows firefighters to breathe in hostile environments. Identify the different features of a SCBA from a fire captain in this free firefighting video series about SCBA harnesses, gages, regulators, masks and more.
In this video tutorial, Chris Pels will show how to configure an ASP.NET web site to use a specific version of ASP.NET/.NET Framework. First see how to identify what version of the .NET Framework a web site is associated with by viewing the script map in Internet Information Server (IIS). See how a script map is associated with the root in IIS and then with individual web sites. Next learn about the ASP.NET IIS Registration tool (aspnet_regiis.exe) used to configure IIS or an ASP.NET web site...

Check out this video to learn how to find and gather wild edibles and medicinal plants. First, learn how to identify the toothwort plant. If you don't already know how to recognize the wild lettuce plant, keep watching.

Rubber bands are an ordinary, everyday, common household item, right? Their hidden in your desk, wrapped around your bills, holding your pencils together at the office, but what else can you do with rubber bands? What are some extraordinary uses? Woman's Day Magazine tells you how you can repurpose those rubber bands!
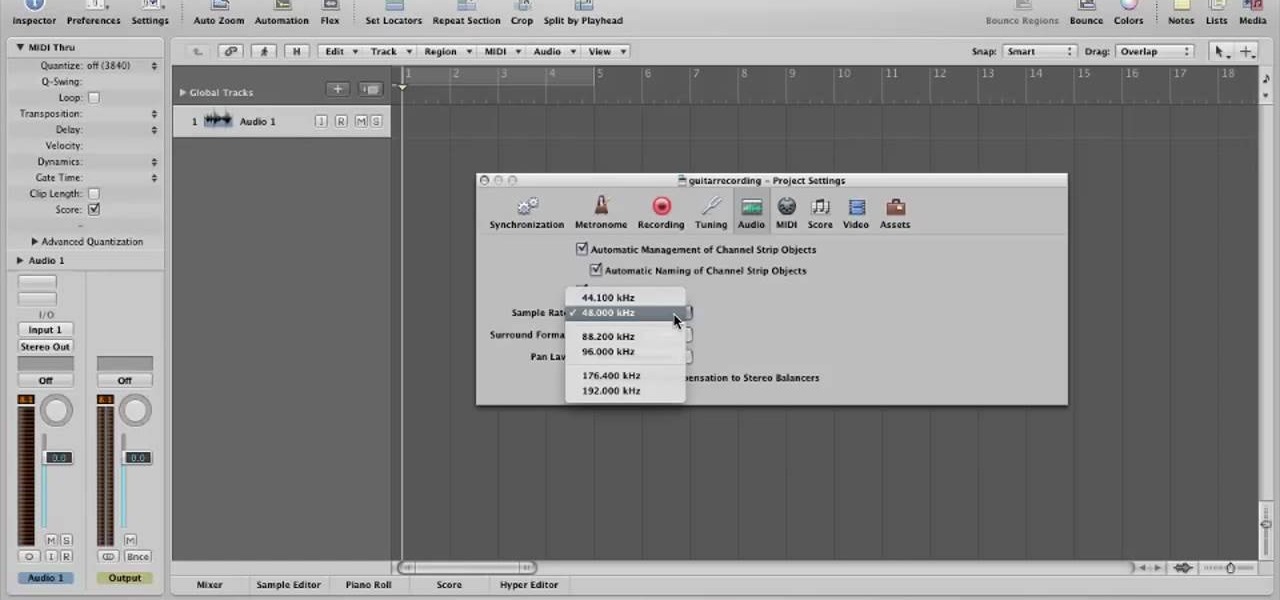
In this video, you will learn how to record using Apple Logic Pro 9. First, open the program and save the session. Make sure your audio interface is set before recording. Go to global settings and navigate to audio. Click on the general tab and change the audio settings. Wave files are the industry standard. Make sure 24-bit recording is checked. Software monitoring will allow you to monitor the audio. Save this and change the project settings. You can adjust the sample rate of your recording...
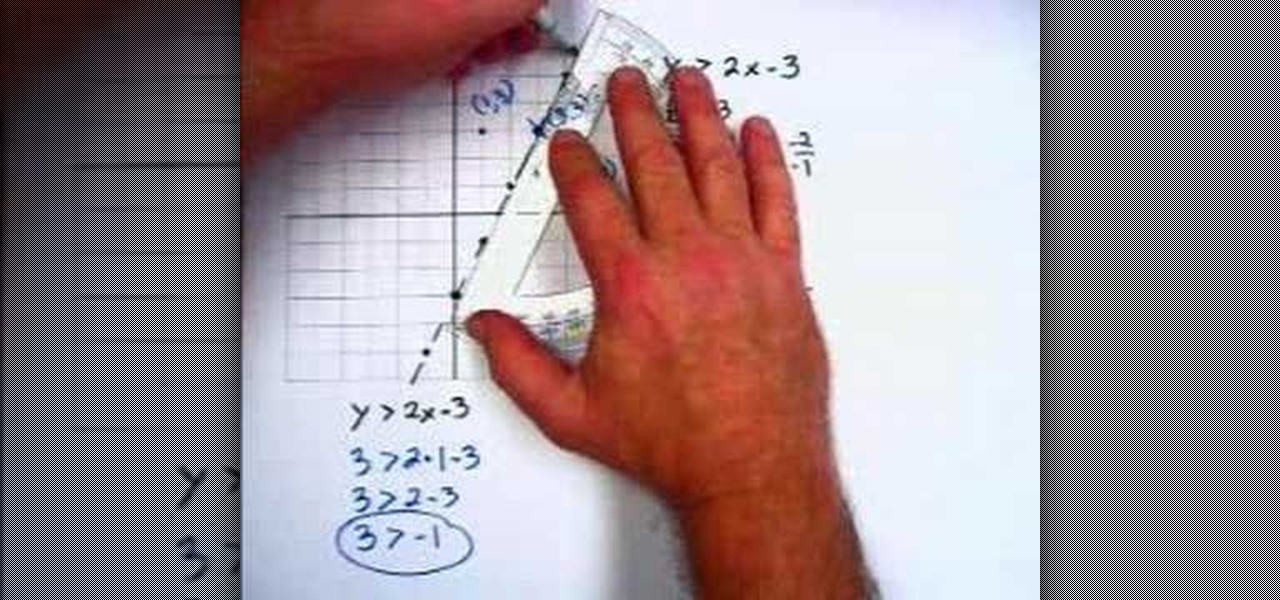
In this video the instructor shows how to graph linear inequalities. A linear in a equation is almost similar to a linear equation except for the sign in the equation. Now treat the in equation as a linear equation and graph the line. So substitute the lesser than or greater than symbol in the liner in equation with the equals to sign and graph the equation. Find the slope of the equation and identify the points that the line passes through. Now take a point on the either side of the pointed ...

This video shows the method to change a word problem into algebra and to identify rational numbers among a group of numbers. In the first part of the video we take a word problem namely - The product of 9 and seven, less than a number. 9 multiplied by something can be expressed as 9(). The unknown number can be expressed as 'x'. Seven less than a number can be expressed as x - 7, so that the final equation becomes 9(x - 7). In the second part we are given a list of numbers. A rational number ...

This lesson describes the method to find the factors of a trinomial, which consists of three terms, by grouping. First of all, factor out the greatest common factor (GCF), and write the reduced trinomial in parentheses. Let the terms of the trinomial be written in order of exponent of the variable. For example, 3(3X2+2X-8) trinomial is written in the order of variable, with 3(GCF) factored out. Now identify the coefficient of the first and last terms, for example in this case, it is 3 and 8. ...

Don't throw out your wilting plants! There's a chance you can bring it back from the dead. Your wilting plant can be spared and revitalized with a little help & these easy steps.

Reverse lights are not something to let slide. Having a reverse light out can cause a serious accident. Before you kick your car into reverse, make sure your reverse lights are working properly. Replacing them is easy and takes only a few minutes.

Are you a novice artist looking to up the ante in your drawings? Introduce depth and realism to your drawings with shadows. It all starts with “seeing the light.”

It's not unusual to feel a little down after giving birth. You've been through a major life event, and your mind and body are recovering. Postpartum depression is more serious than the typical “baby blues” that can occur after childbirth. Learn how to identify this condition so you can treat it and spend more time enjoying your baby.

Want to impress some friends? This magic trick requires no sleight of hand, just a bit of setup. Using the Magicard application, you can make your iPhone mysteriously identify the card placed against it.

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

With a torque wrench, you can set a bolt to the proper tightness and cut down on wear and tear. You Will Need

Spread the word: It's easy to reduce energy consumption! By sharing these tips, you'll help friends and family use less energy and save money.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a USB device.

Learn how to write a grant proposal. If your organization has come up with a great idea that needs money to get off the ground, you'll need a great proposal. Here's how to write one.

Try these simple fixes to salvage your specs. Learn how to fix your eyeglasses with this helpful guide.

Identify the proper time to throw a knee kick. If you are grappling with an opponent, look for an opening where you can knee-kick him in the ribs or side of the thigh. If an opponent is trying to tackle you around the waist or take you down by grabbing your legs, introduce his face to your knee. If the opponent is standing in front of you and there is not enough room to throw a fully extended kick, grab him and try a knee.

Got school spirit? The cheerleading squad's the perfect place for you. Here's how to make the team. Step 1

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

Have you ever been listening to the radio and a song comes on that you can't identify? But you're driving, so you can't open your phone and use your favorite app to find the song's name. Well, with a feature called "Now Playing" on Pixel phones, Google has solved this problem.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

The use of smart phones is not limited only as a mode of communication now-a-days. There are many things that can be done with the help of a smart phone.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Google Lens is a fantastic addition to Google Photos for Android and iOS that allows your smartphone to identify a number of things in your pictures, like landmarks and contact info. Using this power, you can even find out how to buy almost any product you've taken a photo of — you don't even need the barcode.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

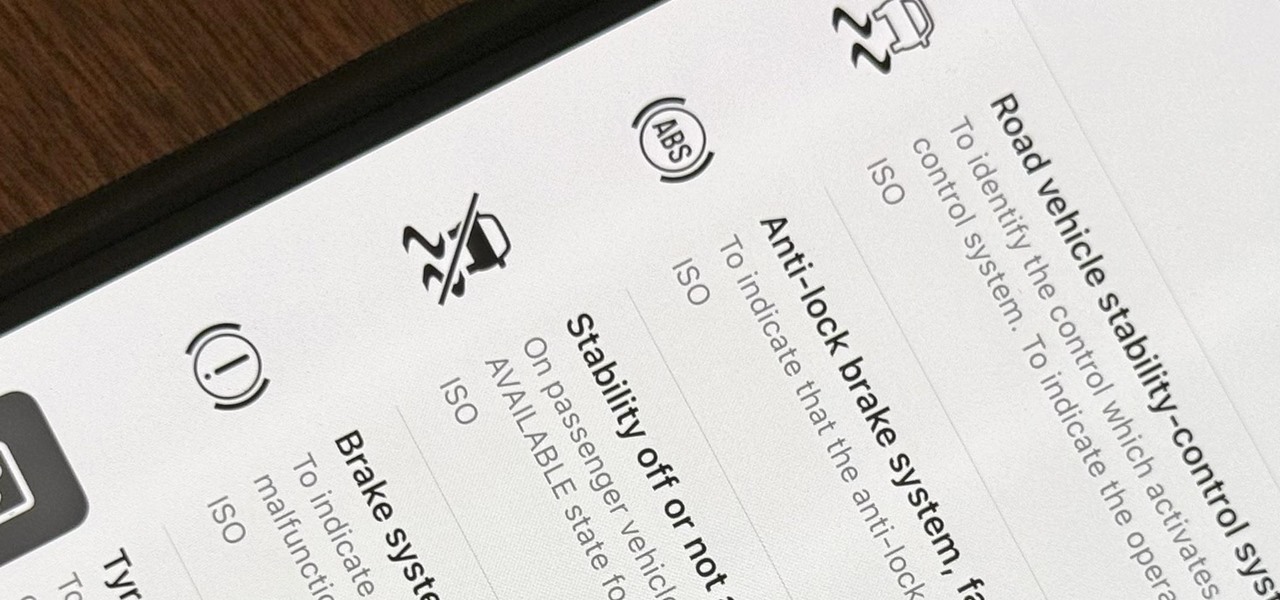
When you encounter a mysterious laundry care symbol or alarming vehicle indicator light, you might just ignore it rather than ask somebody, search online, or open a user manual for the answer. If you have an iPhone, there's an easier way to decipher the meanings behind perplexing symbols and signs—and it only takes a few seconds.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

In this article, I will be showing you how to make a crude form of aspirin from the bark of a willow tree. It is a great remedy for headaches, hangovers, and other minor pain. The use of the willow tree as a mild pain reliever goes back to the Native Americans, who used it in much the same way that I do.

The name of your business will leave an impression on people as this is probably the first information they will receive. Make sure to express yourself and give the impression you intend by choosing the best name for your business.

If you've ever been asked to find the GCF, or Greatest Common Factor, of a series of numbers or algebraic expressions, check out this video to learn how.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.