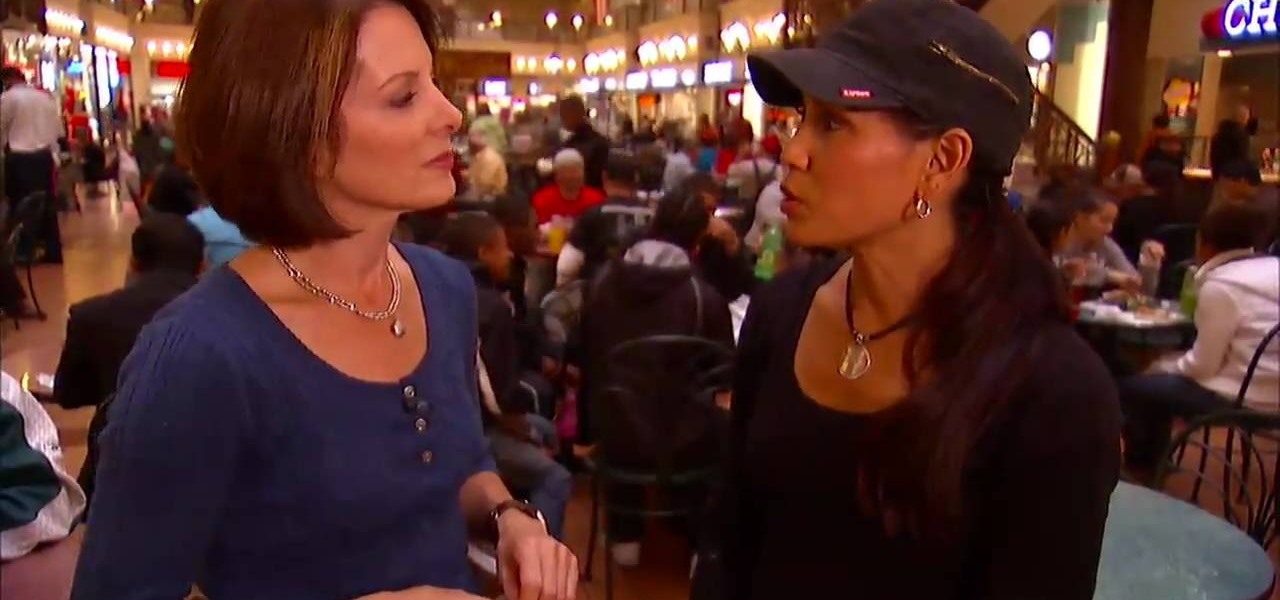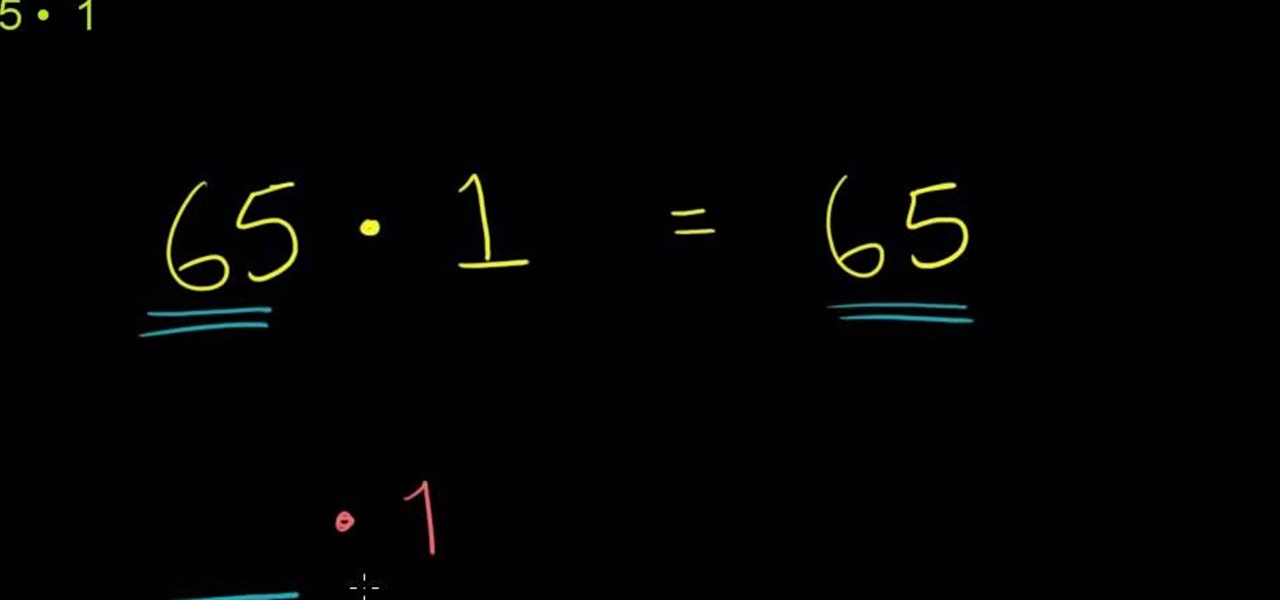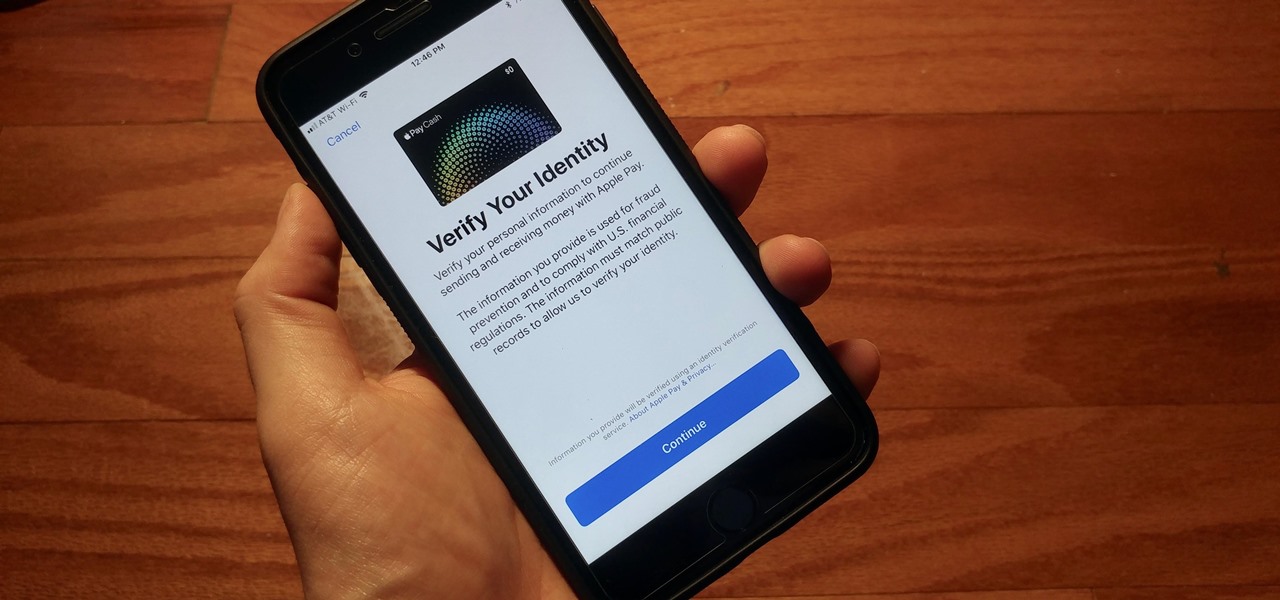
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

So, how does someone keep their hacking life completely secret? What This Is:

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

If you have been a victim of identity theft, you are not alone. This happens to millions of people every year.

Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.

In this video from the ID Theft Center, learn exactly what identity theft is and how to prevent it from happening to you. Identity theft can happen to anyone - young, old, living, dead - thieves do not discriminate. This helpful video will tell you exactly what to look out for and how to avoid scams. Your host will explain how identity thieves operate and how to cut them off at the pass.

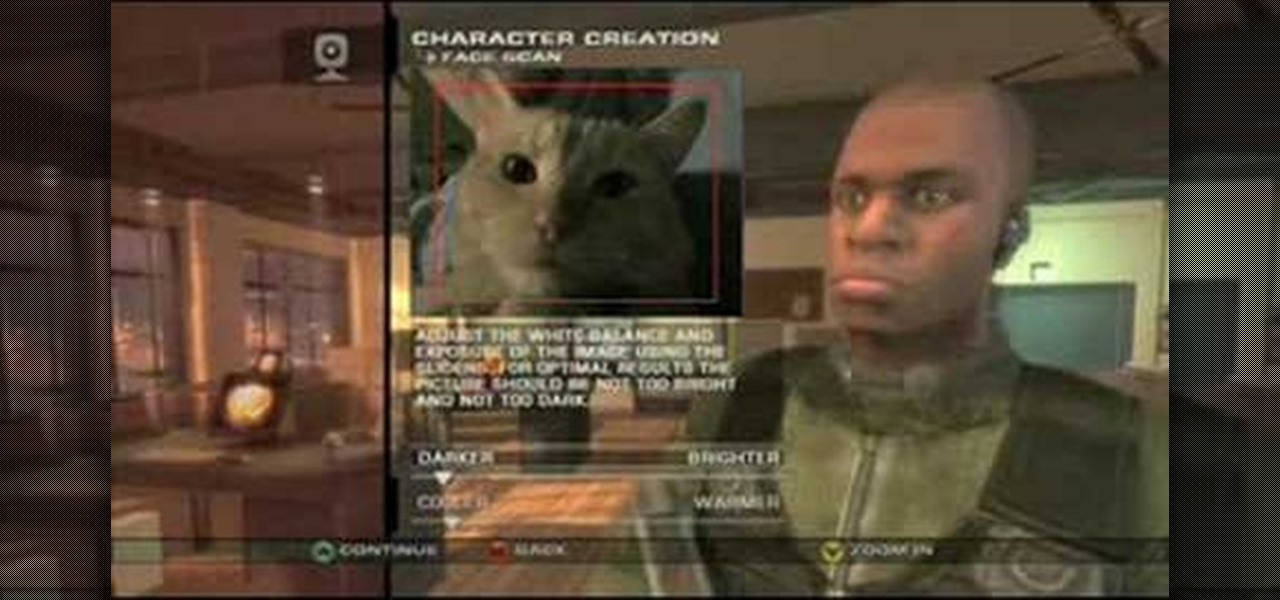
This process requires XBox2 live with vision camera. We are going to create a character. First, you go to multiplayer mode, options and then choose character creation. If you haven't created a character, you will start from scratch here. If you have created a character previously, you will make some adjustments to the character for this presentation. Now, go to player information and then service record. As the program already has a character, we are going to change the appearance of the char...

In this video, presented by the experts at the St. Louis Community Credit Union, learn how to prevent thieves from stealing your identity or account information. These days, between paper bills, Internet banking, social networking and all the other ways we interact, there are many ways for crooks to get into our private lives.

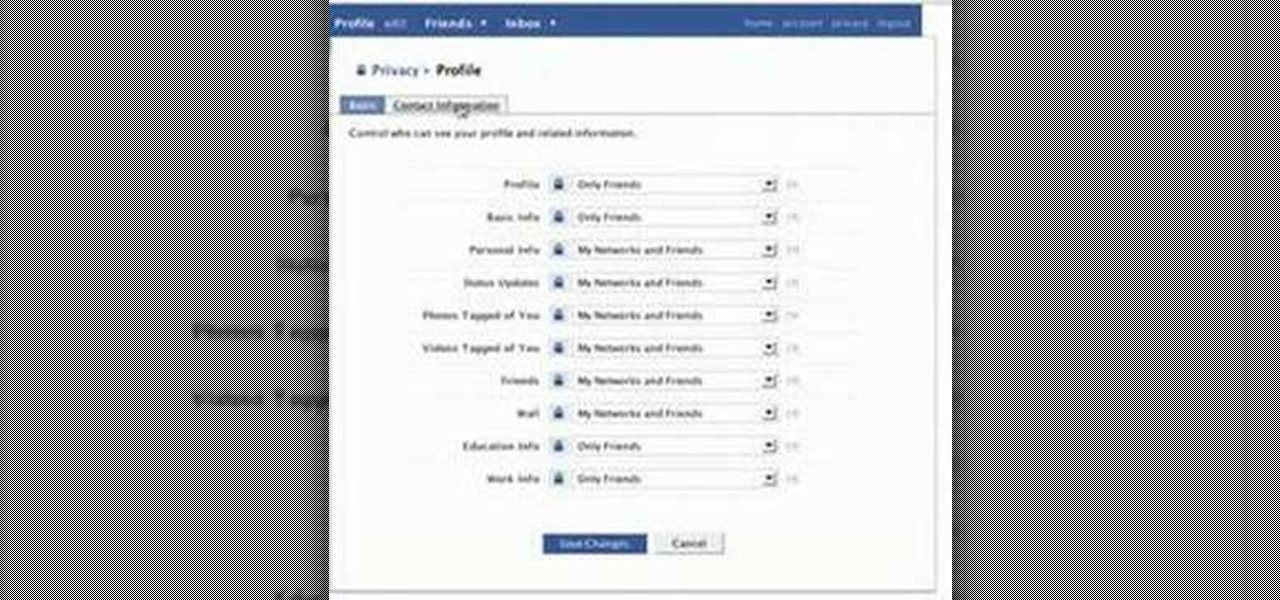
Identity theft can happen anywhere, even in social networking. Why are we so careful when using our credit cards online but not when we sign on to Facebook?

From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to unpack and solve word problems requiring use of the identity property of 1.

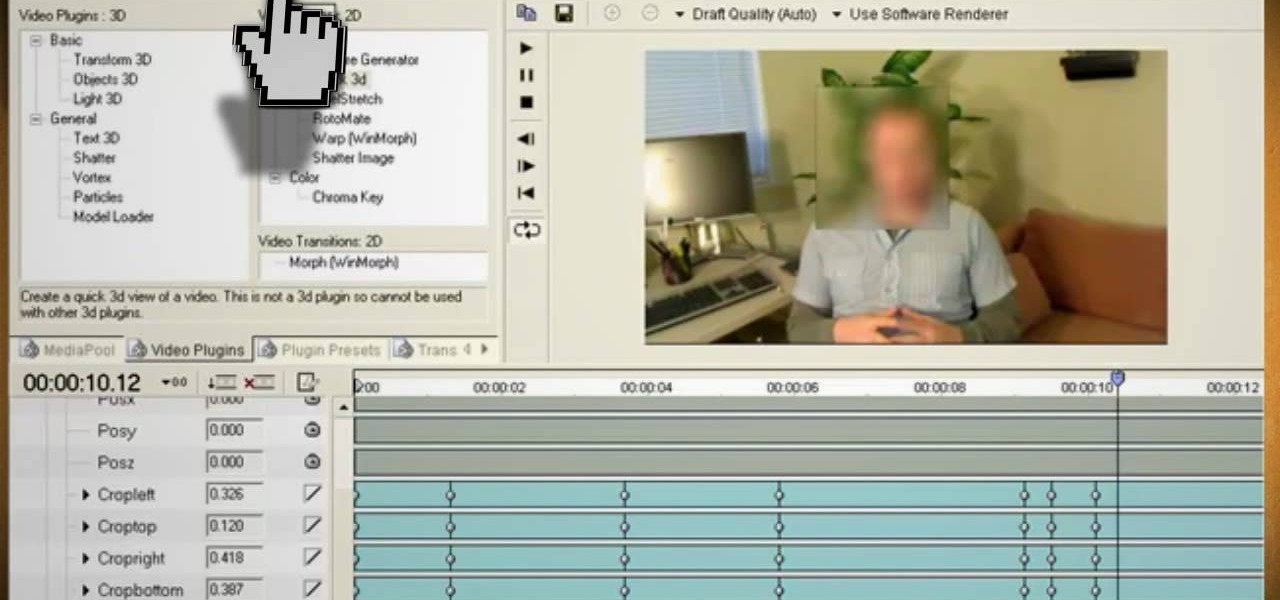
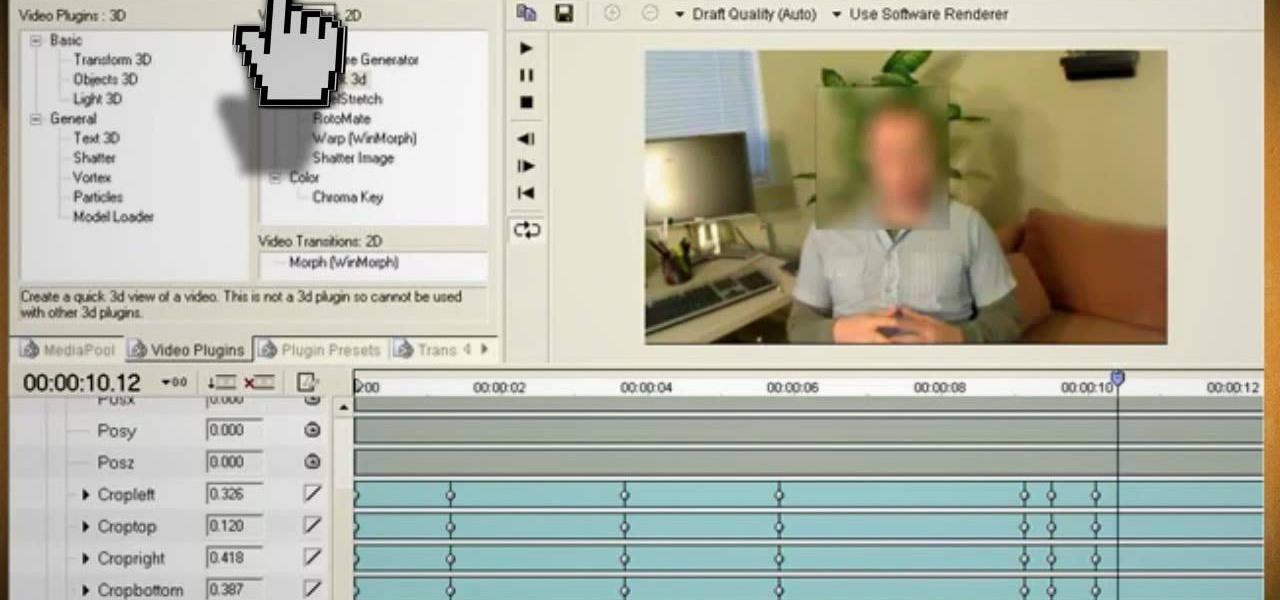
When you watch the news or a television show where someone doesn't want to be identified, it is common to see the face blurred out or obscured. In this Adobe Photoshop tutorial you will learn how to blur someone's face in an image and preserve or hide their identity. So if you are producing videos or podcasts or need to hide part of an image, this tutorial will show you how to do it in Photoshop.

This video will show you how to use video and audio to hide your identity. After you have your audio and video you will need a converter program, for example Format Factory which will convert the audio and video into the necessary formats. You will be encoding your clip as an AVI Video, as well as MP3. To start you will need to change the pitch of the audio track. A good program to use for this is Audacity. Play around by making the pitch either higher or lower. Save it as a Wav file To edit ...

When you really think about it, registering for any website is a little scary. Not only do they now have your name, email address, and a username/password combination you might've used elsewhere, but certain sites and services ask for quite a bit more private information. From phone numbers to addresses to birth dates and more, that company now has all of your information stored.

University video game design programs have been spreading like wildfire around the world over the last ten years. They allow students, researchers and game developers to work on their craft in an academic environment away from the harsh realities of the market, and have led to some interesting products like Fl0w from USC and Ulitsa Dimitrova from Germany. Both games take on topics not often addressed in mainstream games and do so in simple, poignant ways that aim to influence the rest of the ...

The art of disguise is a very important skill to master, no matter if you're a hounded celebrity trying to ditch the paparazzi or just someone who'd like to step out of the house without being recognized. If you think simply throwing on sunglasses and a hat is a good disguise, you are so wrong.

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

There’s only one you, right? WRONG! There’s a lot of bad apples out there, and If you’re not careful, they’ll steal your identity in an artichoke heartbeat. So remember to watch your tail!

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

This video tutorial from iDeviceTutz shows how to change the SSH root password for iPhone or iPod.When iPhone or iPod is jailbroken it sets its password to default - alpine.Thus your device becomes vulnerable from a network attack that could steal your information or identity. So you need to change your password as soon as possible when your device is jailbroken.For this you'll need Mobile Terminal program on your device and SSH client (Cyberduck or WinSCP) on your computer.First download and...

Is your French up to par with Parisians? Can your Aussie tongue mingle with the local Australian natives? What about your old-style New York accent? If you're in need of improving your accents in different languages, then Amy Walker can help you out.

If you loved The Da Vinci Code by Dan Brown, then listen up— there's been a new discovery found hidden within Leonardo da Vinci's most famous painting— the Mona Lisa.

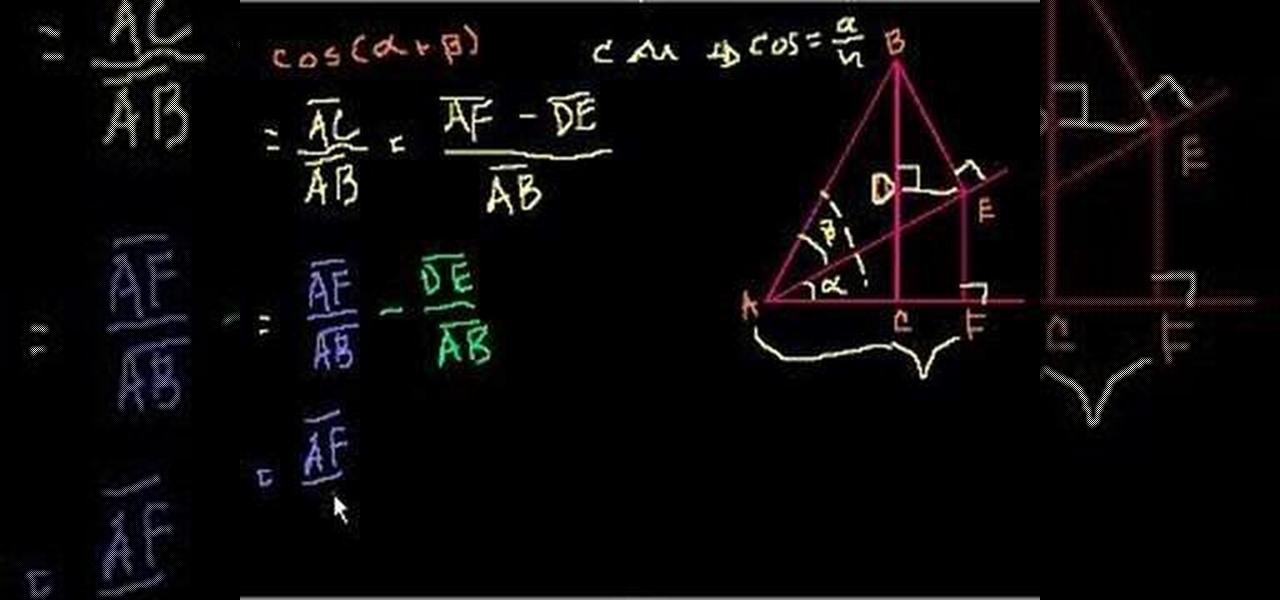
Need help proving the cos(a+b) = (cos a)(cos b)-(sin a)(sin b) trigonometric identity? This free video lesson will show you how. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series ...

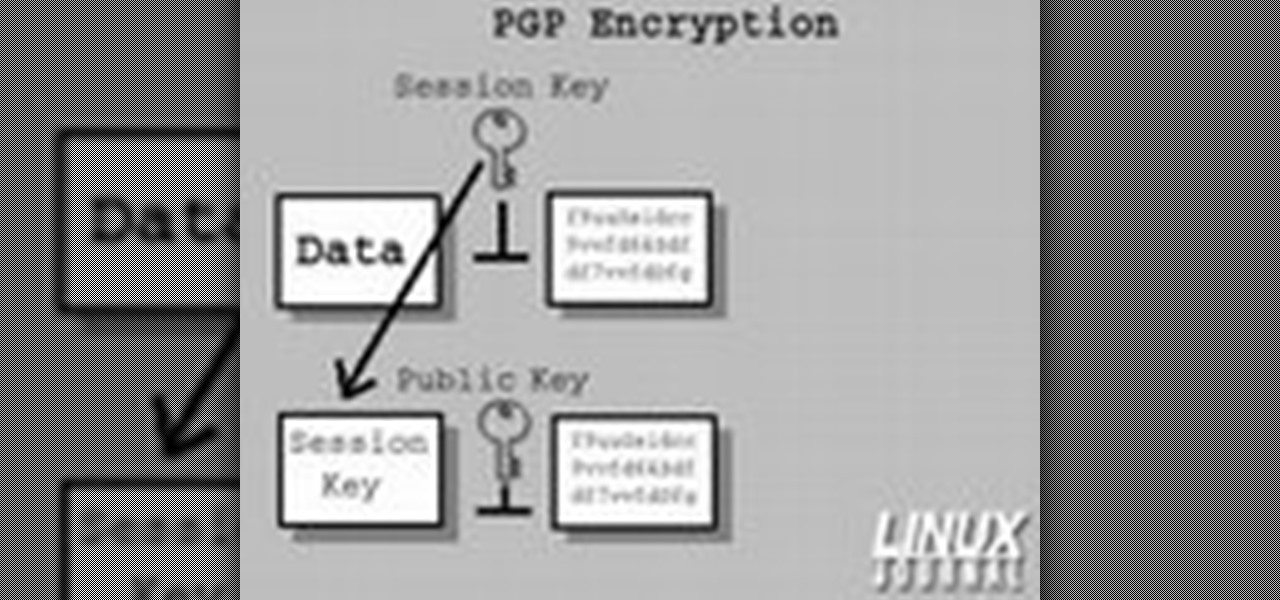
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Focus groups strike fear into the hearts of even the most season marketer, and with good reason. In a world where everything is subject to change based on public opinion, from movie endings, to popcorn flavors, to logo colors, focus groups can make or break a new idea, but it doesn't have to be that way. A focus group is just a way to gather opinions in a vigorous way and can be very useful. Watch this video tutorial to use a focus group to develop and test a new brand name or corporate ident...

Prevent indoor lighting problems with these great tips. -When a window is behind the object, bring lights closer to object or use a reflector using the light from the window to create a 3 point lighting effect.

This software tutorial takes a look at how to design an icon set in both Photoshop and Illustrator. An icon set is a set of icons that you can integrate into a number of different projects, like a website or a company letterhead, logo and identity set up. Having an icon set readily available for all your project needs will make your workflow faster and simpler. So watch and see how to make an icon set first in Photoshop and then in Illustrator.

Meez is the social entertainment leader combining avatars, web games and virtual worlds. Get help with all of your Meez avatar needs with these Meez tips and tricks! Watch this video tutorial to learn how to remove the head off your Meez avatar.

Watch this video and learn how to protect your identity on the internet. This clip will help you learn how to blur out your face and alter your voice when posting videos on the web, where your identity is an important secret. Stay anonymous while portraying your opinions. This software can also be used to avoid release issues with strangers in the backgrounds of your videos. Preventing passers by from having there picture posted with your opinions opening you up for legal action. This can als...

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)