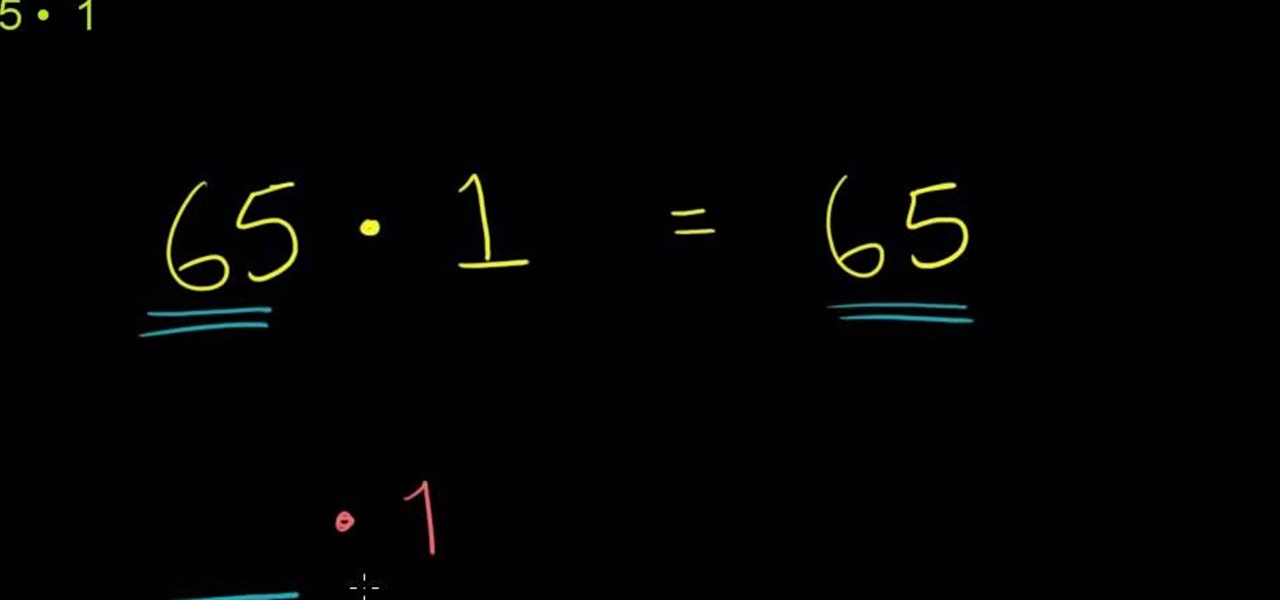T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

In this video from the ID Theft Center, learn exactly what identity theft is and how to prevent it from happening to you. Identity theft can happen to anyone - young, old, living, dead - thieves do not discriminate. This helpful video will tell you exactly what to look out for and how to avoid scams. Your host will explain how identity thieves operate and how to cut them off at the pass.

If you have been a victim of identity theft, you are not alone. This happens to millions of people every year.
Identity theft can happen anywhere, even in social networking. Why are we so careful when using our credit cards online but not when we sign on to Facebook?

There’s only one you, right? WRONG! There’s a lot of bad apples out there, and If you’re not careful, they’ll steal your identity in an artichoke heartbeat. So remember to watch your tail!
Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.

In this video, presented by the experts at the St. Louis Community Credit Union, learn how to prevent thieves from stealing your identity or account information. These days, between paper bills, Internet banking, social networking and all the other ways we interact, there are many ways for crooks to get into our private lives.

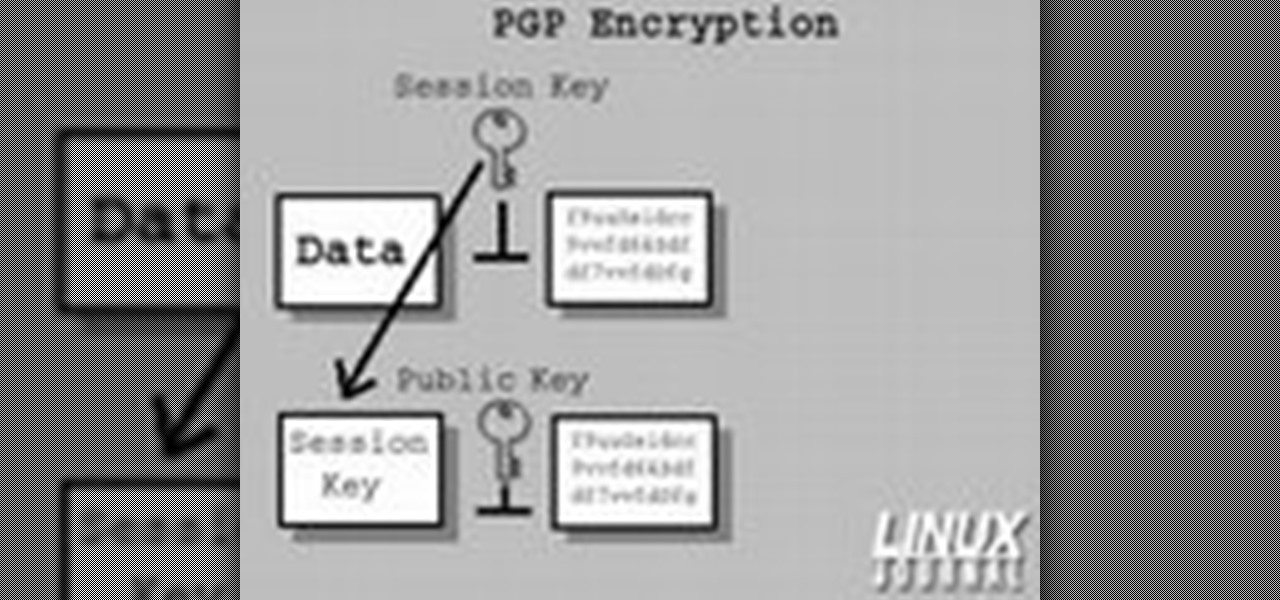
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

Sun, fun, murder, extortion, and all of the top 40 80s hits you can stand! This walkthrough guides you through all of the the 59 main missions of Grand Theft Auto (GTA) Vice City for the Playstation 2 (PS2).

This video walkthrough guides you through the main 61 missions of Grand Theft Auto (GTA) San Andreas for the Playstation 2 (PS2).

Here's a complete video walkthrough guide to Grand Theft Auto 3 (GTA) for computer (PC) from gtamissions.com. This covers the main story mode missions.

This video walkthrough will take you through all 100+ missions of Grand Theft Auto (GTA) San Andreas for the PC.

This walkthrough guides you through the 58 main missions of Grand Theft Auto (GTA) Vice City for the PC.

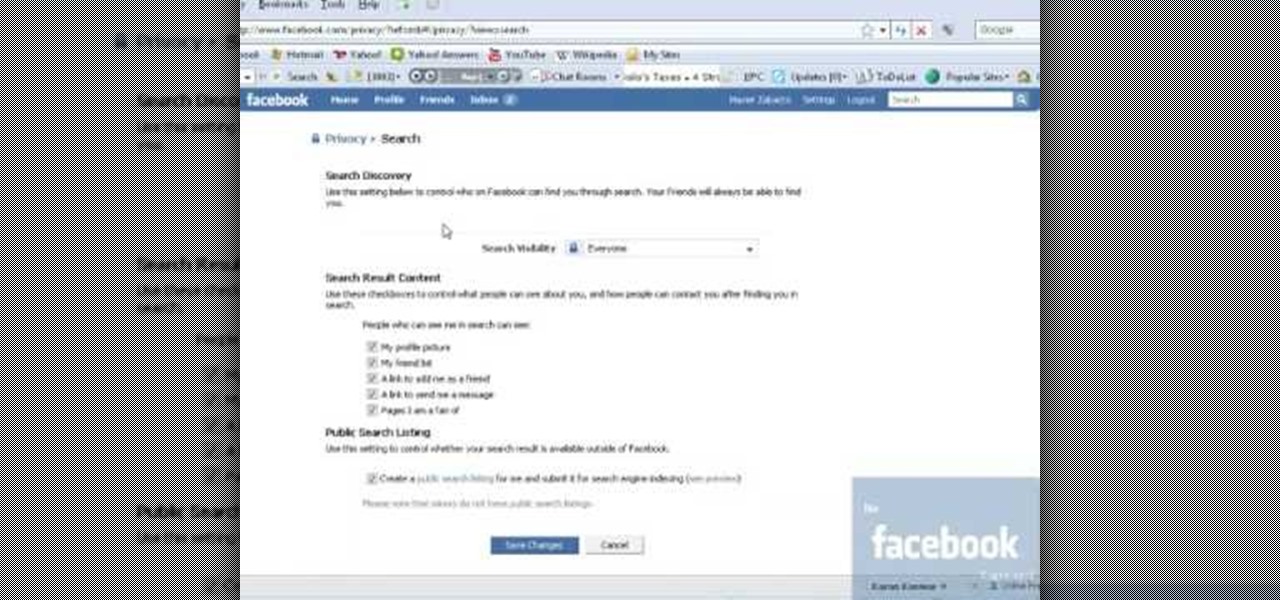
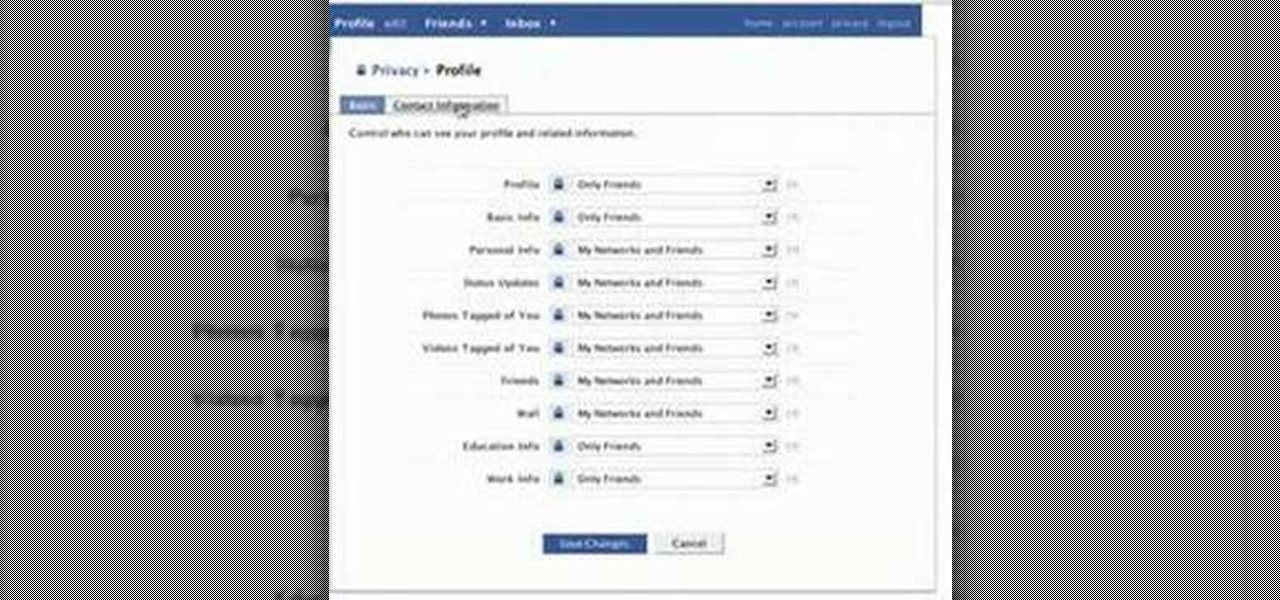
In this video, we learn how to make your Facebook profile less public. First, log onto your Facebook account, then go to your privacy settings. Through there, go to search and choose who you want to allow to search for you on your site. After this, save your settings and move on to the other sections to change more privacy settings. If you do not want people that aren't your friends to see your information or to be able to search for you on Google, this is a great way to go. Making your infor...

In this video, Dan and Jennifer will teach you how to be safe while trying to meet girls or date online. Learn tips and tricks to avoid common scams such as identity theft and fraud, as well as things to look out for and early warning signs that your potential lover may not be all she says she is. Dan and Jennifer will also show you how to watch out for one of the most common scams online: "cam girls". Don't fall for that fake girl that acts like she's totally into you but really just wants y...

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Here's a complete video walkthrough guide for Grand Theft Auto 3 (GTA) for Playstation 2 (PS2) from gtamissions.com. These are all the main story mode missions.

Here's a complete video walkthrough guide for Grand Theft Auto (GTA): Liberty City Stories for Playstation 2 (PS2) from gtamissions.com. This sequence covers the main story mode missions.

Video walkthrough guide for the side missions in Grand Theft Auto (GTA): Vice City for Playstation 2 (PS2) from gtamissions.com. Featuring Cone Crazy, Trial by Dirt, Test Track. Hotring, Bloodring, Dirtring, and Pizza Boy Mission.

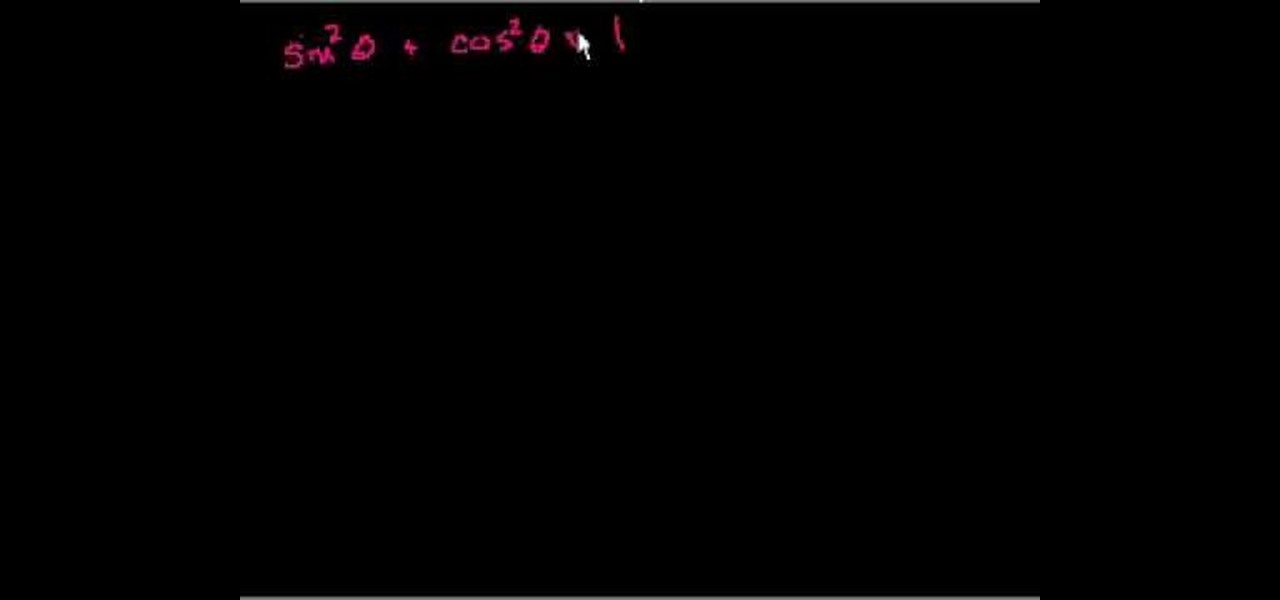
This video shows the method to prove some trigonometric identities. This involves the use of algebra and knowledge of basic trigonometric identities. The video demonstrates three examples to illustrate this problem and its solution. The first problem shows a relatively simple problem involving sines and cosines. The video shows some basic algebra steps to simplify the problem and prove the identities. The second example involves a slightly complicated problem involving square of combination o...

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

The first thing that comes to mind when your car is stolen is: ####!! However, once calm, cover these bases when your car is stolen to notify relevant parties and help ensure vehicle recovery or replacement.

One of the best features of Apple's Final Cut Studio is the graphics interface feature Motion. With its ability to create and edit motion graphics, you can easily create title sequences for your indie film, or maybe even a professional movie, with 2D or 3D visual effects compositing.

From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to unpack and solve word problems requiring use of the identity property of 1.

Need help wrapping your head around trigonometric identities? Watch this free video trig lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll l...

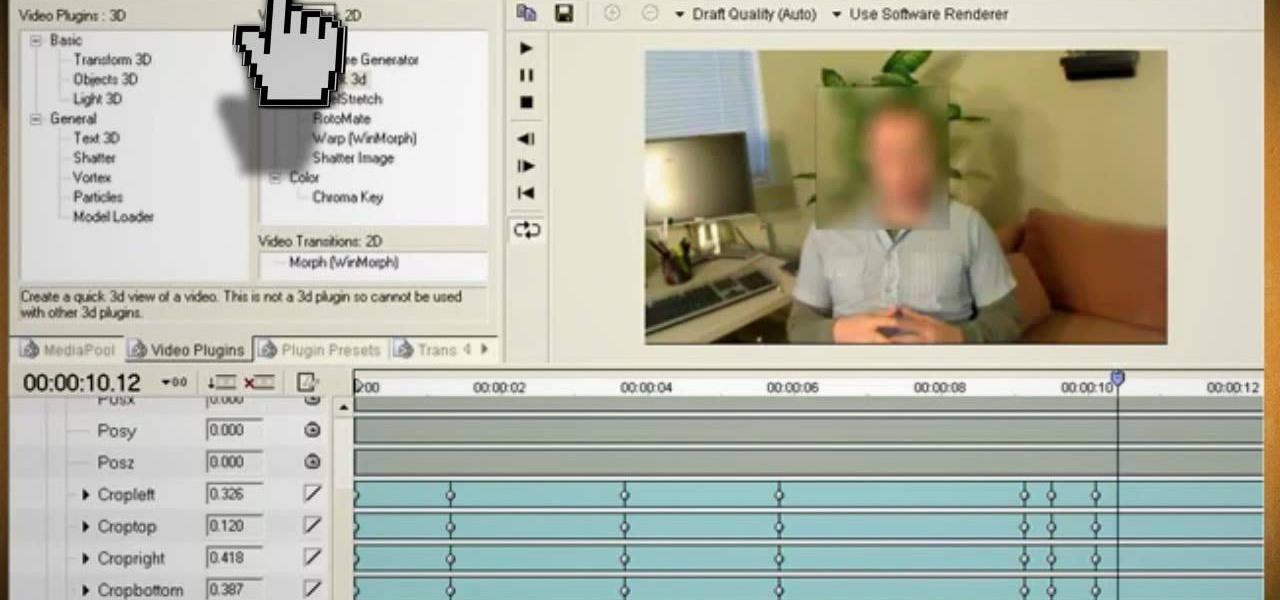
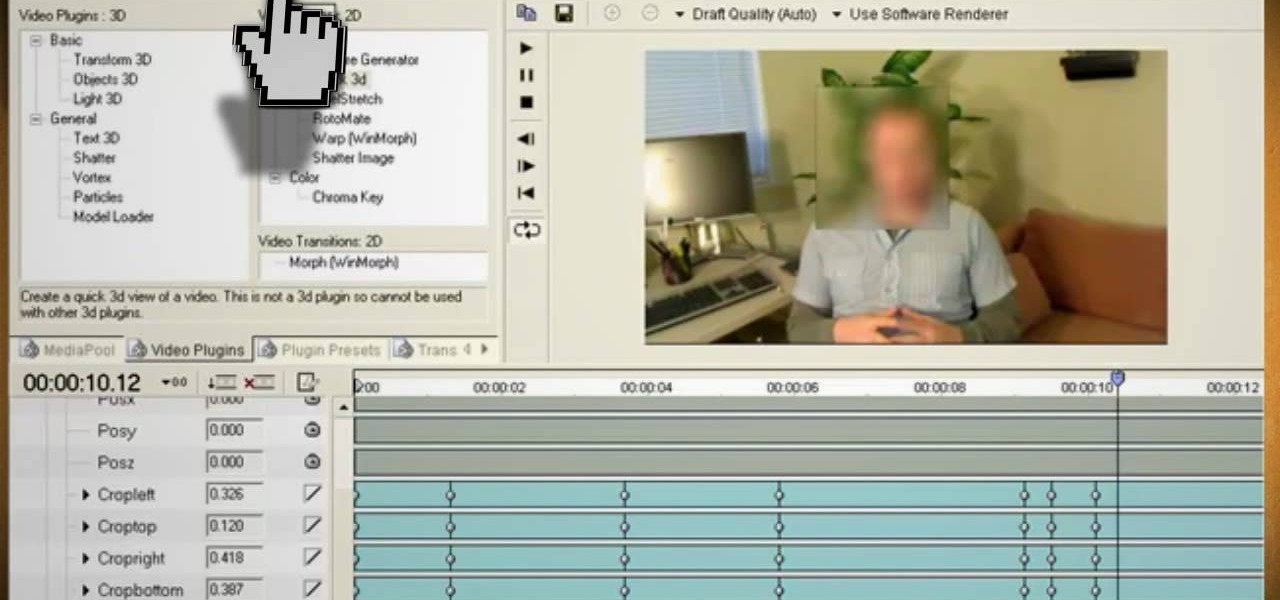
Watch this video and learn how to protect your identity on the internet. This clip will help you learn how to blur out your face and alter your voice when posting videos on the web, where your identity is an important secret. Stay anonymous while portraying your opinions. This software can also be used to avoid release issues with strangers in the backgrounds of your videos. Preventing passers by from having there picture posted with your opinions opening you up for legal action. This can als...

When you watch the news or a television show where someone doesn't want to be identified, it is common to see the face blurred out or obscured. In this Adobe Photoshop tutorial you will learn how to blur someone's face in an image and preserve or hide their identity. So if you are producing videos or podcasts or need to hide part of an image, this tutorial will show you how to do it in Photoshop.

There's a cache of weapons hidden in Portland, in the game Grand Theft Auto 3. You don't need to enter any cheats or cheat codes - just follow this video, and it'll show you exactly where to find all of them.

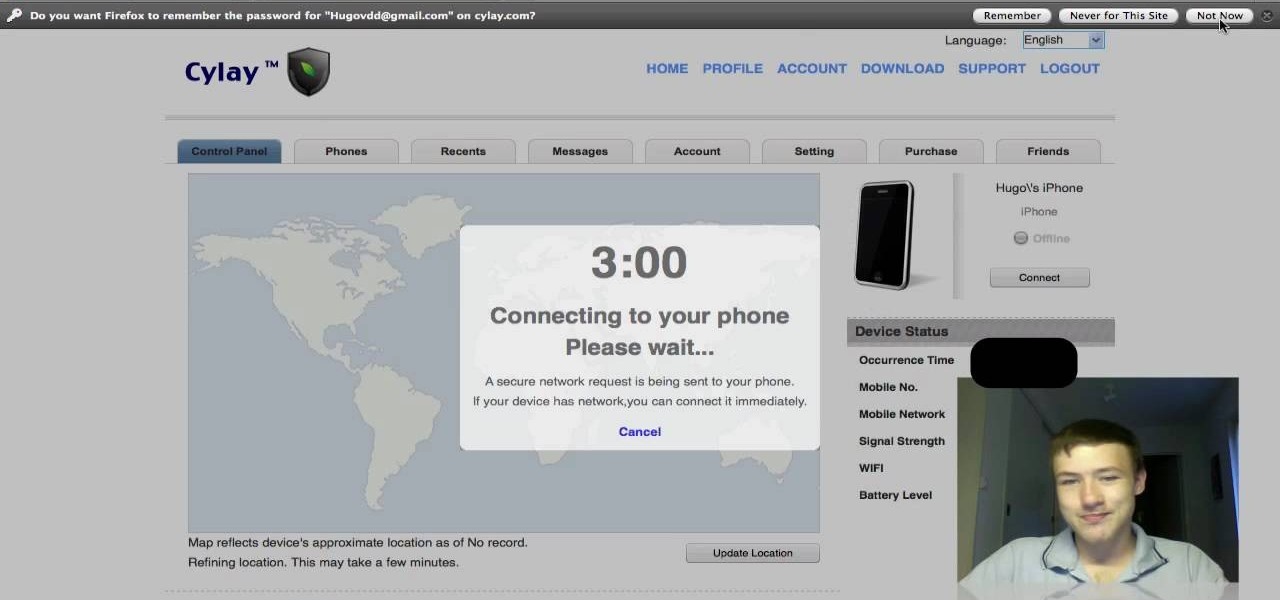
This app will only work on Apple devices that have already been jailbroken. Once you have, you can set up an account with Cylay. And once you have an account with Cylay, you can protect your phone or mp3 player against theft.

Here is a different way to get out/under Liberty City in the new game by Rockstar(registered trademark) Grand Theft Auto 4 (GTA IV).

Kristin Holt from G4TV tells you the right way to get started on the right foot in Grand Theft Auto IV (GTA 4).

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

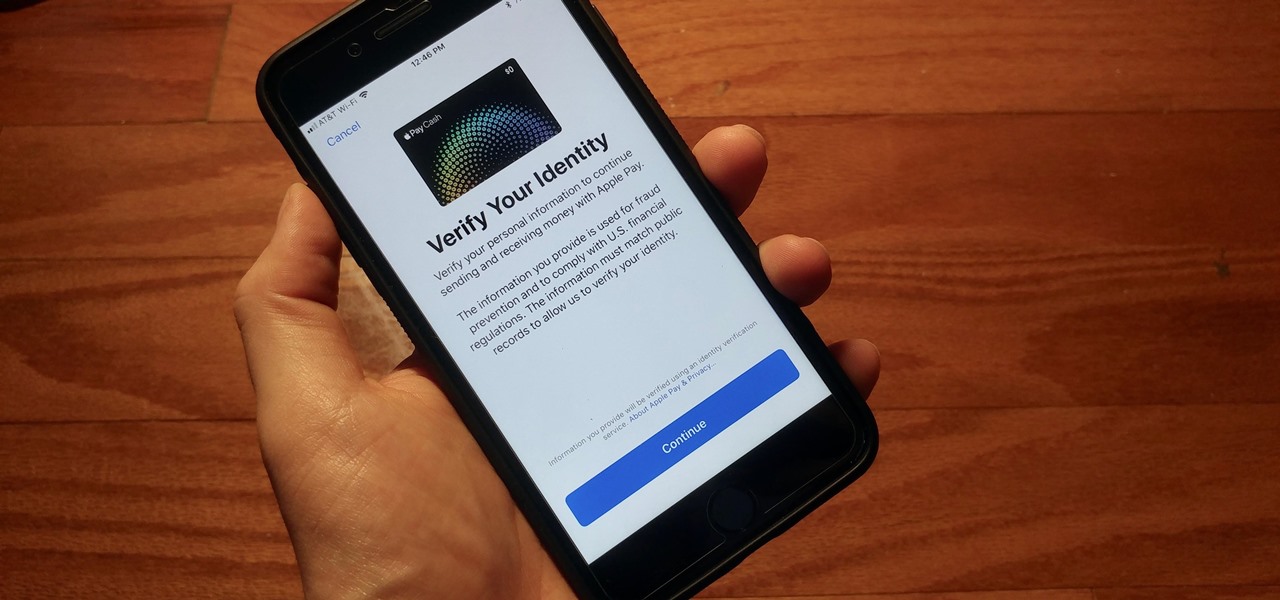
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

Heres a video that teaches you how to mod cars in Grand Theft Auto 3: Vice City for the PC.

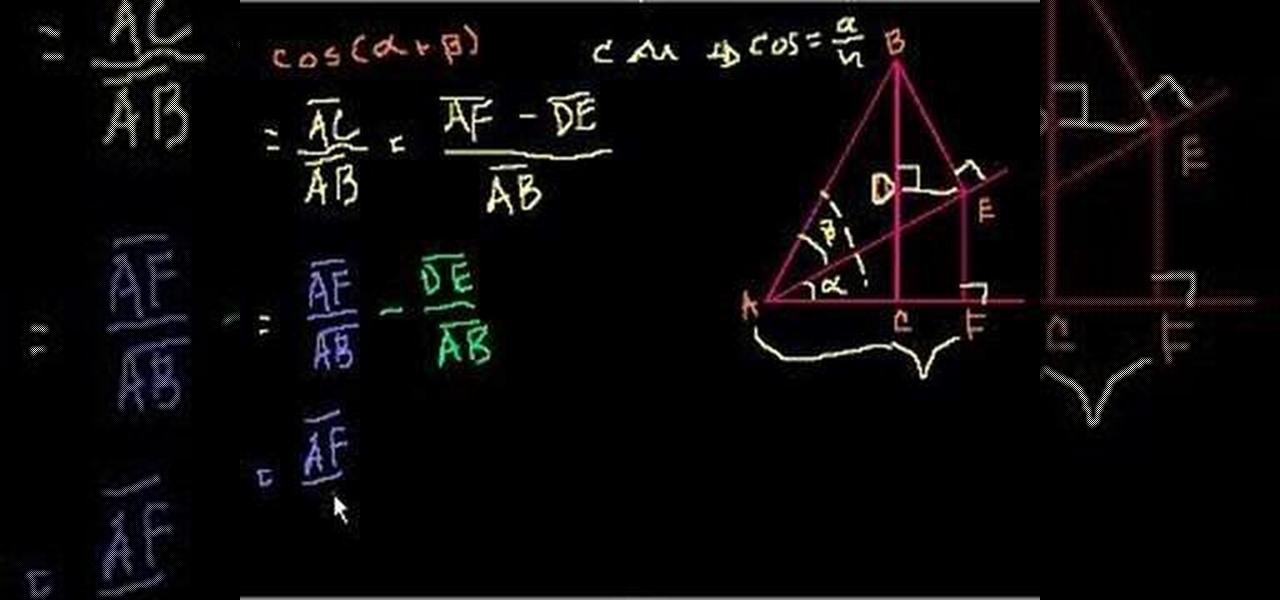
Need help proving the cos(a+b) = (cos a)(cos b)-(sin a)(sin b) trigonometric identity? This free video lesson will show you how. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series ...

Super heros' secret identities are their most guarded secrets. Many choose to protect them with masks, but how to make your mask if you're a new superhero or a filmmaker trying to simulate a super hero? This video will show you how to make your own cheap superhero mask at home, which will be a great prop for your next film or Halloween costume.

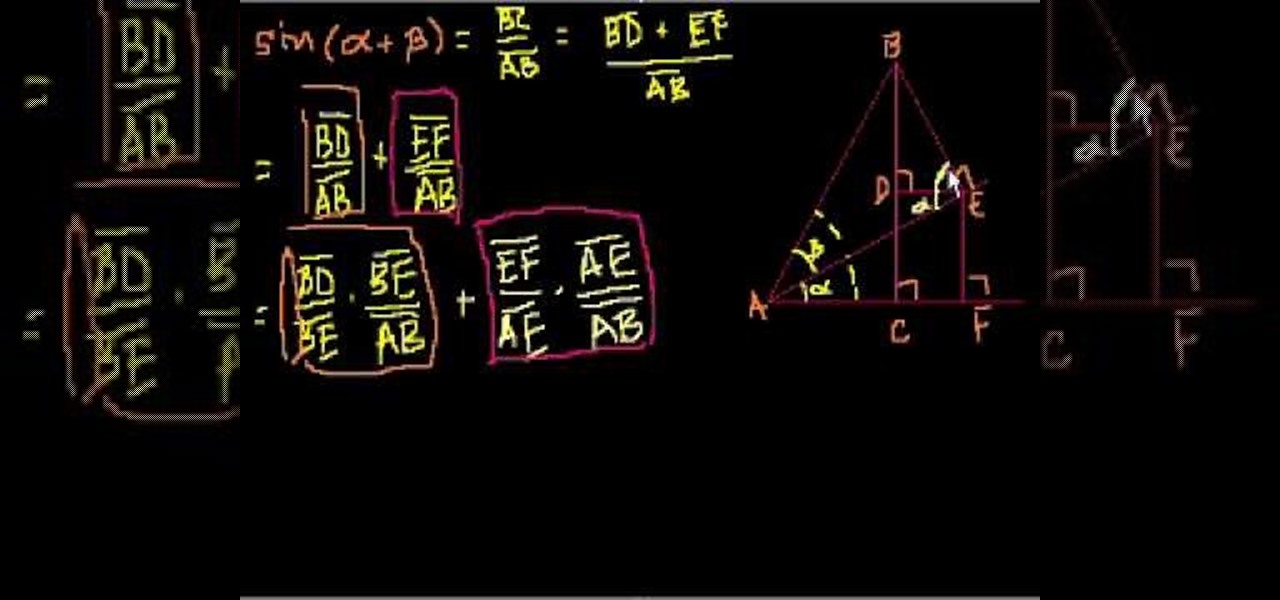
Need help proving the sin(a+b)=(cos a)(sin b)+(sin a)(cos b) trigonometric identity? This free video lesson will show you how. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of...

This video will show you how to use video and audio to hide your identity. After you have your audio and video you will need a converter program, for example Format Factory which will convert the audio and video into the necessary formats. You will be encoding your clip as an AVI Video, as well as MP3. To start you will need to change the pitch of the audio track. A good program to use for this is Audacity. Play around by making the pitch either higher or lower. Save it as a Wav file To edit ...

First you want to find X using the identities given for a 45-45-90 triangle. When comparing the triangles in the video, we find that X must be 6. Next, use the identity to solve for the measurements of the sides of the triangle. In the video example, 6 is the length of the two sides and 6 times the square root of 2 is the length of the hypotenuse. The video is very short and does not explain a lot of things in detail, but that is because the examples are easy to figure out.