
Beat the turismo races in GTA: Vice City Stories
Video walkthrough guide for the tourismo car races in Grand Theft Auto (GTA): Vice City Stories for the Playstation Portable (PSP) from gtamissions.com.


Video walkthrough guide for the tourismo car races in Grand Theft Auto (GTA): Vice City Stories for the Playstation Portable (PSP) from gtamissions.com.

Video walkthrough guide for the side missions in Grand Theft Auto (GTA): Vice City Stories for the Playstation Portable (PSP) from gtamissions.com. Includes the Playground on the Town, Playground on the Point, Playground on the Dock, Beach Patrol - Save the Swimmers, Beach Patrol - Biker Gang, Beach Patrol - Paramedic Driver, Rush, and Swinger's Club missions.
This video series will walk you through beating each of the 10 race tournament side missions for Grand Theft Auto (GTA) San Andreas for the Playstation 2 (PS2).
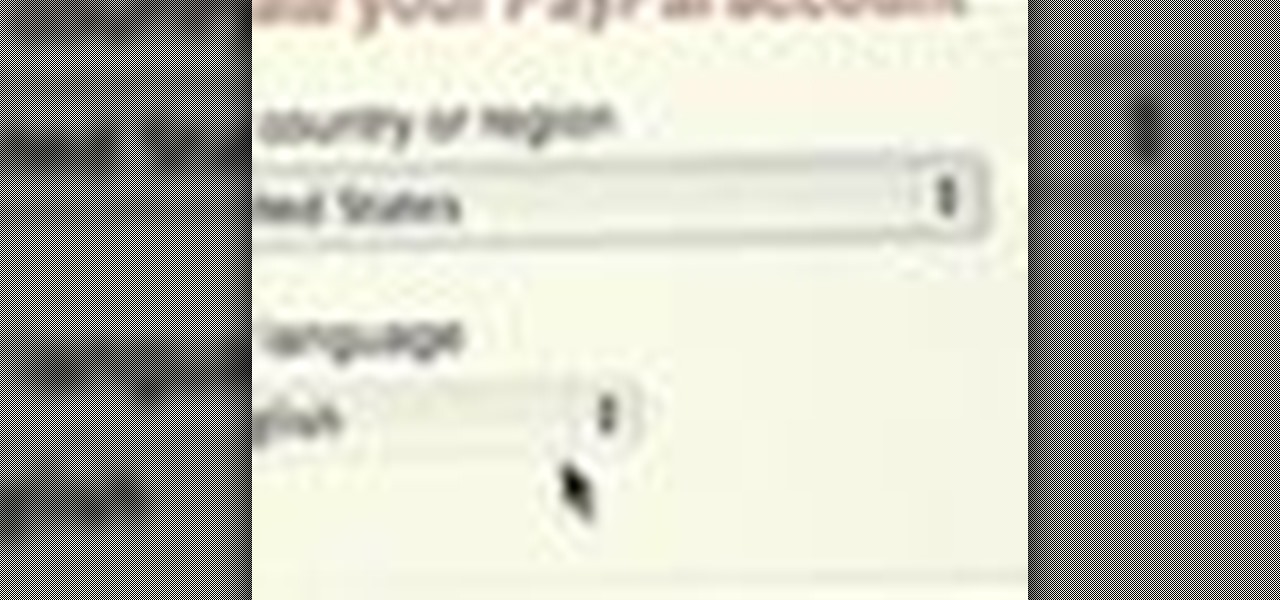
If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved.
With Apple's Photos app, you no longer need a third-party tool on your iPhone, iPad, or Mac to blur or pixelate faces in your photos, helping you safeguard identities when sharing online.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

Imagine walking up to enter a live event — but instead of pulling out a physical or mobile ticket to get admitted — you pull out your smartphone which lets out an ultrasonic sound tailored for you that lets you into the event.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Now that the identity of the Origami Killer has been revealed, it should be easy to find him. In this walkthrough of Heavy Rain (PS3), you'll be in the killer's apartment. See how to beat Chapter 5 - Killer's Place.

Nexus is a pre-approved trusted traveler program that allows approved people expedited travel between Canada and the US. The card is available to US and Canadian citizens or permanent residents who travel by air or land between the two countries. Anyone traveling between the two countries must have their own Nexus card including babies. The Nexus card is considered a privilege by both the US and Canadian governments. You must have a clean record with both the Canadian Border Services and The ...

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

The drama continues! In the latest installment of the feud that has rocked the driverless vehicle industry, Waymo is now accusing Uber of withholding a secret LiDAR device.

Uber's driverless car program lead has quit after just one year working for the ride-hailing company.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.


Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

Cars are expensive to buy, replace or repair. Check out this video and learn how to avoid the most statistically dangerous parking areas. There is no guarantee that no one will touch your vehicle, but by take precautions you are much less likely to be targeted.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Now that it has buried the legal hatchet with Meta Company, augmented reality startup Dreamworld has announced plans to open up pre-orders for its Dream Glass AR headset.
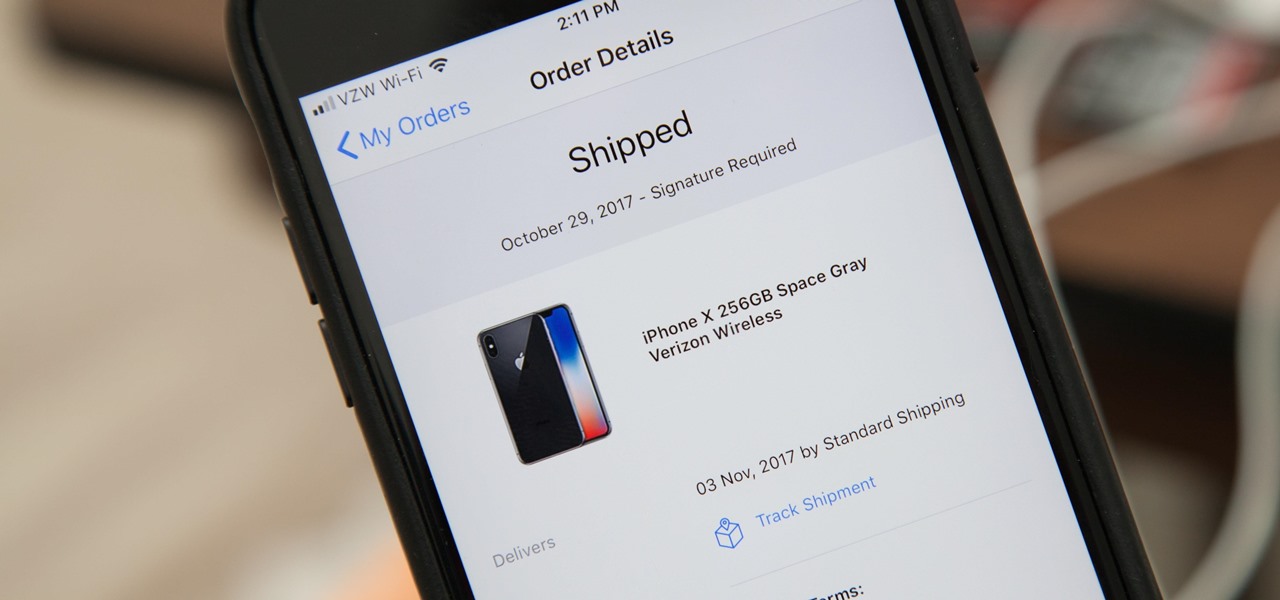
Current shipping estimates for the iPhone X are 5–6 weeks, but is there a chance you'll get yours tomorrow?

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.

It wasn't too long ago that Uber threatened to fire star engineer Anthony Levandowski. Eleven days to be exact. If Levandowski didn't turn over the documentation he allegedly stole from Google's autonomous car division, Uber informed Levandowski that they would take "adverse employment action." Today, The New York Times reported the ride-sharing firm has delivered on that threat. In a memo sent to employees Tuesday morning, Uber announced Lewandowski's official departure from the company "eff...

The best way to spread Christmas cheer is singing loud for all to hear, right? Wrong.

It just got a whole lot easier to decide whether or not saving $50 on Amazon's new ad- and bloatware-subsidized smartphones is worth the headache of having to see an advertisement on the lock screen every time you wake the device.

At the beginning of regular gameplay in Grand Theft Auto 5, you play the role of Michael robbing a bank in North Yankton with his accomplices—shooting police and evading a high-speed train in the process. While you do revisit North Yankton during regular gameplay in Los Santos, it's strangely unavailable for online play.

There are already hundreds of glitches out there for Grand Theft Auto 5 Online, but most of them are useless. Most of them don't do anything to benefit your gameplay, but they're still pretty fun to mess around with. One such glitch, shown off by YouTuber AquibTV below, lets you inside any building in Los Santos. Los Santos is a big ass city and there are tons of buildings that you cannot get into without using a glitch like this one.

Want the best view of Los Santos in Grand Theft Auto 5 without having to purchase a plane or steal a chopper? You can enjoy the sights of the Los Angeles replica by hopping on one of the trains rolling around the city—and forget about riding in one of the cars, we're going straight into the cockpit.

It's easy to forget sometimes that even when you're sitting in the basement playing Grand Theft Auto 5 Online that you're not really alone. Everything you say into the mic can be heard by anyone else in that same session.