For this project, I sacrificed some of my kids' clothes and a can of tuna to make some high-quality fire starter! Here's how to make a great batch of char cloth to add to your emergency survival kit.

Prepaid phones are becoming more and more popular, and tons of people can see the benefits of switching now that some companies are offering prepaid services that are on par with the big players. For a lot of folks, the only thing keeping them from switching is the huge early termination fees that service providers charge to break a contract early.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

For those of you still using a BlackBerry smartphone, this article will show you the tips and tricks to installing emulators and playing some classic Game Boy Advanced games on your device. You can find a few tutorials and videos out there on getting Game Boy Color or NES games on an Android device, but the most elusive mobile emulator is for Game Boy Advanced (GBA) on a BlackBerry.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

The director of 100 Musicians and Nurse/Fighter/Boy talked with us about old school filmmaking Charles Officer has directed shorts, music videos for K’naan, and the features Nurse/Fighter/Boy and Mighty Jerome, a documentary about Canadian track star Harry Jerome. His new short 100 Musicians, which screens Monday as part of Short Cuts Canada, is a small ode to civic optimism, concerning itself with a lovers’ argument over who exactly misheard a radio DJ reporting the plans of Toronto’s much m...

Welcome to Minecraft World! Check out our full tutorials and make sure to post to the community forum if you have any questions or cool builds you want to share.

Who would have thought that dryer sheets can be a quick remedy for super-staticky flyaway hair? But it's true. It's all about the positive charges in the sheets and their ability to neutralize electron buildup. And that's not the only surprising quick fix for hair problems that you can easily find in your home.

Marinate your pork chops before grilling to really make them tender and flavorful. Your family won’t be disappointed when they sit down to a dinner of hot chops just off the grill, so fire up the grill and get started.

You have your gift and a card and now all you need that special cake for mom on Mother’s Day. You’ve tried other cakes now try a hat cake. This festive and spring inspired hat cake is sure to make this year’s Mother’s Day a memorable one.

SyncVue announced at NAB that they would be offering a new version of their remote collaboration software for editors and producers. Well the long awaited update is finally here and all existing SyncVue users will definitely want to grab it. The functionality is improved and the new features are killer. So check out this quick little video tutorial on setting up and using the new version of the software, This walks you through the newest features and how to basically get around.

Android has not had the best reputation for privacy and security, though Google has made strides in those departments in recent years.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.
Welcome back Hackers\Newbies!

Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

In this video series, watch as screenwriter and producer Chris Cobb teaches you how to turn a script into a production board. learn how to break the pages down, how to transfer the scripts onto the breakdown page, how to color code the script, and how to put together the production board.

In this easy dessert video recipe, learn how to make lemon mousse from expert chef Karen Weisman. Karen will teach what supplies and ingredients you will need to make a delicious lemon mousse. She will also demonstrate how to juice lemons for lemon mousse, how to separate egg whites from egg yolks, how to use dried egg whites as an alternative to fresh egg whites, how to combine gelatin and lemon juice for lemon mousse, how to prepare a trifle dish for lemon mousse, how to prepare lemon souff...

In this series of magic videos, our professional magician demonstrates basic sleight of hand tricks such as the French drop and false transfer in a clear and easy-to-follow manner. He also performs several tricks using cups and balls and explains these routines in detail. He even shows you how to use a magic wand. Now that you know this magician's secret, make it your own.

When Steve Jobs introduced the first iPhone, he pointed out that the biggest problem with physical keyboards on mobile phones is that they're always there, whether you need them or not. Now, 17 years later, a new company is bringing us full circle, giving us the best of both worlds: a physical keyboard for iPhone that can disappear whenever you want.

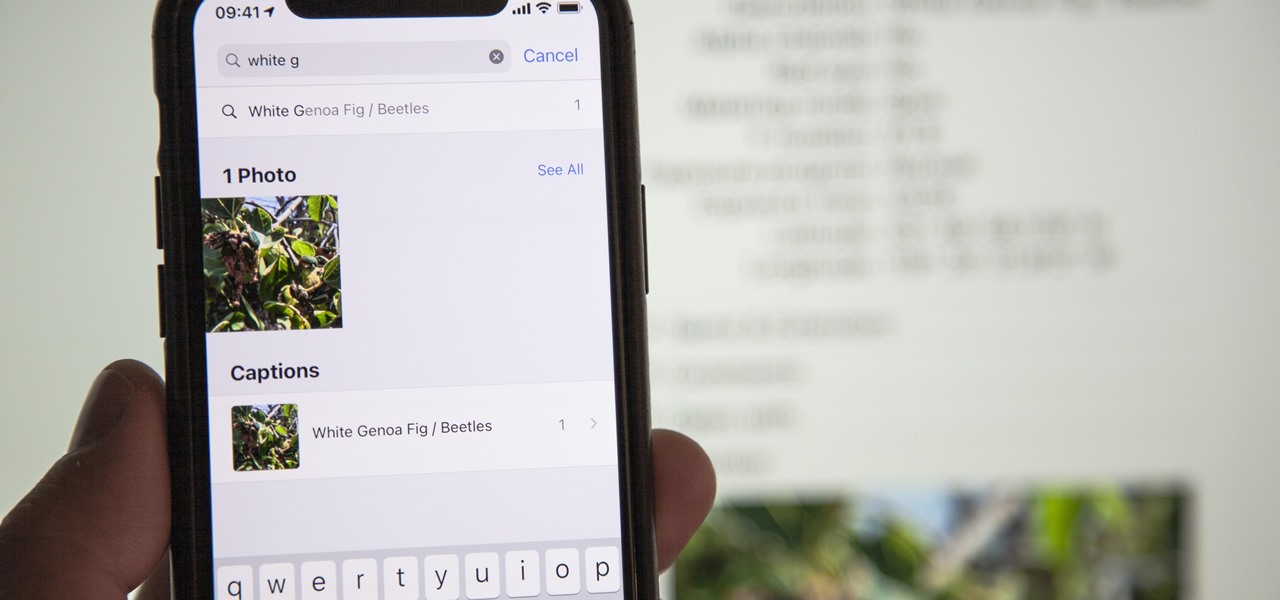
If you've been an iPhone user for quite some time, you probably have quite a bit of photos and videos in iCloud or on your device. Unless you know the date, location, or event, it can be pretty hard to find a specific memory. Even with intelligent search suggestions, AI-created categories, and multi-keyword filters, you still may not be able to find what you want. The new iOS 14 update changes that.

A rather exciting development has recently surfaced in the jailbreaking scene for iPhone. The Checkm8 bootrom exploit was shown off to the public by axi0mX, which made way for the undefeatable Checkra1n jailbreak tool. With it, you can freely jailbreak a variety of older iPhone models without any restrictions. The success rate is quite high, too, when compared to other jailbreak methods.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing up for the new streaming service, let's take you through all the changes and features you should know about before doing so.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

You saw our post on the 18 coolest new features of iOS 7, but now that you've had a chance to play around with your updated iPhone, it's time to lock it down.