Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

While new features in Safari, Camera, Photos, Notes, Weather, Messages, and other Apple apps may steal the show on iOS 17, there are some impressive new features you need to know about when it comes to FaceTime audio and video calls.

If you can't access your iCloud data such as emails, contacts, calendars, photos, notes, reminders, files, and other documents via a web browser on untrusted devices, like one at a library or friend's house, there's an easy way to regain access.
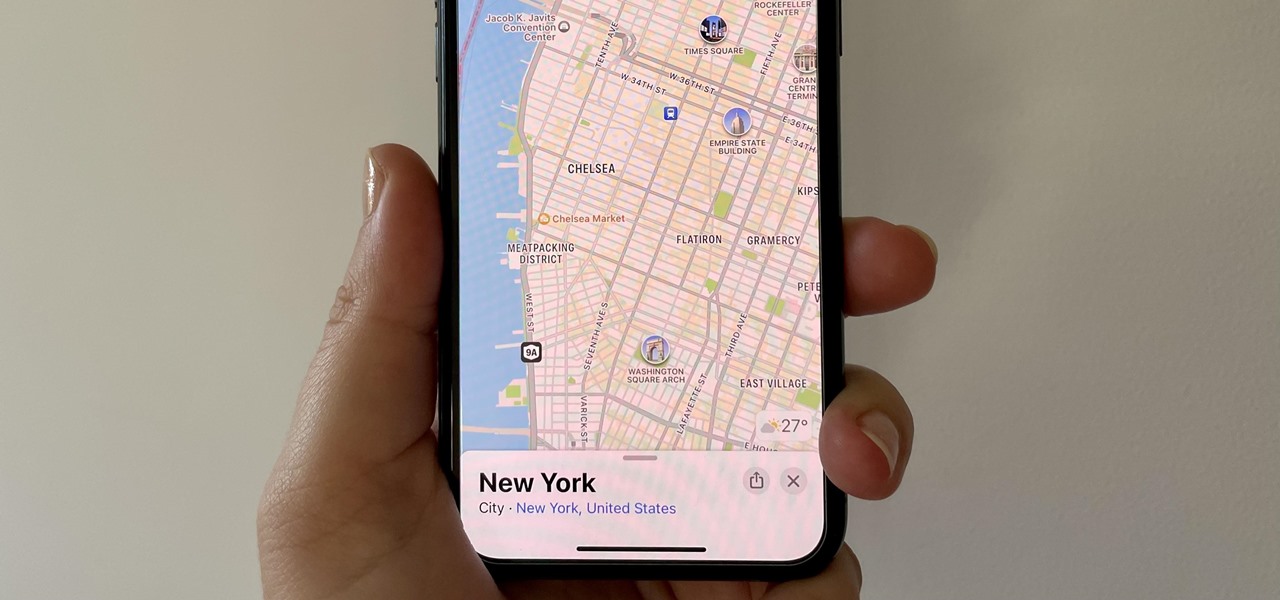
While the Maps app hasn't received as big an update in iOS 16 as Books, Messages, Photos, and Weather did, there are still quite a few exciting new features to enjoy on your iPhone.
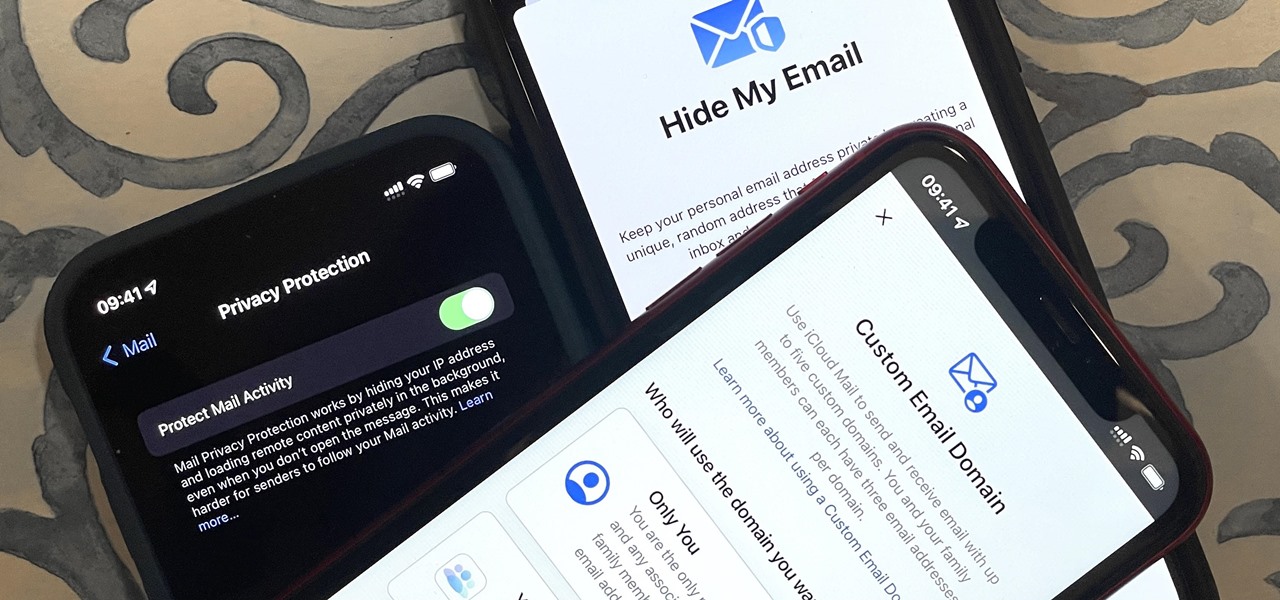
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

Nearly every native app on the iPhone received an upgrade or new features in iOS 14 — and Safari is no exception. The web browser now has better password protection, faster performance, privacy reports, and built-in translations, just to name a few. Some of the Safari updates went unnoticed by many, but they're there and ready to use in iOS 14.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

If your current cellular provider costs too much, has poor reception in your area, or doesn't support features you'd like to use, switching to another carrier is the obvious move. But can you bring your current iPhone or Android phone?

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

In these times of identity theft, terrorism, and the TV criminology craze, learn just how genetic fingerprinting occurs.

If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved.

The flame test is used to visually determine the identity of an unknown metal of an ionic salt based on the characteristic color the salt turns the flame of a bunsen burner.

Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

In these Halloween costume videos, learn how to dress up like the man who sold the world a new identity every ten years or so. Whatever music, fashion, or art decade you decide to portray Bowie in, things should all be hunky dory.

Meez is the social entertainment leader combining avatars, web games and virtual worlds. Get help with all of your Meez avatar needs with these Meez tips and tricks! Watch this video tutorial to learn how to cross-dress on Meez.

Do you wanna be that person who stands out in a crowd? Our society dictates our fashion sense. We believe we all must look like who ever is the "most popular" in the media (TV, film, magazines etc.). Our choice to express our self is very limited because of the stigma of what patterns, styles and colors belong to which gender. I have found by adding just a hint of feminine flair to my person that I am able to catch peoples eye's faster than a supermodel walking onto a runway.

Choosing a nanny or au pair for your children is a process that should be organized and performed carefully, to ensure you find someone who can be trusted, will contribute significantly to the development of your child and integrate well into your family.

With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighbors up. These "farmers" are the ones seeking quick hacks and cheats.

One of the object association types in 3ds Max is groups. In this video tutorial we will learn how to create the relationship in 3DS Max. The author compares groups to dating, where each individual has higher commitment yet they still retain their own identity. Whether you're new to Autodesk's popular modeling software or a seasoned 3D artist just looking to better acquaint yourself with the application, you're sure to be well served by this video tutorial. For more information, take a look! ...

Personalization is an important step towards branding. It helps to build your website or blog's identity! This is a detailed tutorial on creating your VERY OWN music player with a volume slider using Macromedia Flash. Create a music player with volume slider in Flash 8.

I've been pretty straight forward with my praise for Batman: Arkham City. But the thing I like most of all are all of the side missions in the game. One of the cooler, and darker, ones is entitled Identity Thief. No, you don't go after some nerd that hacks people's credit card information. You go after a psychopathic serial killer.

Your brave, fearless, and redundant Admin's card collection, in boxes, with further boxes added to protect his grandma's identity.

Last night's Simpsons opening was a sardonic take on the usual gag, directed and storyboarded by the legendary Banksy, the famed renegade British graffiti artist whose real identity is hidden to the public. Below, laborers in Asian countries manufacture Simpsons merch in a dark underworld sweatshop, as an imprisoned dying unicorn impales Simpsons DVDs.

Set during the Great Depression, the music video tells the story of a woman suffering from Dissociative Identity Disorder who is searching for her missing husband

Texas based artist Shawn Smith brings the digital world to reality with his woodcut pixelated sculptures. The combination of a traditional material (wood) with a contemporary concept results in surprisingly fresh work. Plus, the craftsmanship appears to be impeccable. Check out his artist statement below.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.

I've played through Metal Gear Solid 2 at least fifteen times now. Easily. But I have never seen or heard about this Easter egg. So consider my mind blown when I tell you that Vamp (who should be dead three times at this point) is in the final cutscene of the game.

"It seems that artist Iain Heath is quite enamored with her as well, as he’s decided to turn her Tron Legacy character Quorra into an awesome LEGO model. At only 12 inches tall and made of blocky LEGO bits, the model doesn’t exactly capture Olivia Wilde’s character in all her glory, but it’s remarkable nonetheless. Looking almost like pixel art due to its small scale, it still packs a ton of detail, from the black bob haircut to the design of the light cycle suit covering her body. Of course,...

Printers are getting pretty high tech these days. Print a building, print some organs... and now, print your own cement sculptures.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

What causes stress for a teen is a lot of different things. Most of the common ones are: Parents

Holy… Lord, help us all—this isn't CG, it's for real. Meet Geminoid DK, the latest spawn from Osaka University Professor Hiroshi Ishiguro's legion of ultra-realistic Androids.

Pogo is Nick Bertke, originally from New Zealand who has been remixing and DJing since he was 9 years old.